Network Security Mechanisms
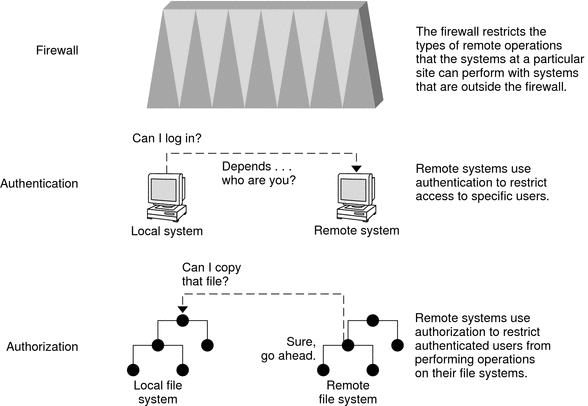
Network security is usually based on limiting or blocking operations from remote systems. The following figure describes the security restrictions that you can impose on remote operations.
Figure 2–1 Security Restrictions for Remote Operations
- © 2010, Oracle Corporation and/or its affiliates
