Chapter 4 Elements of Trusted Extensions (Reference)
This chapter explains the key elements of Solaris Trusted Extensions. This chapter covers the following topics:
Visible Features of Trusted Extensions
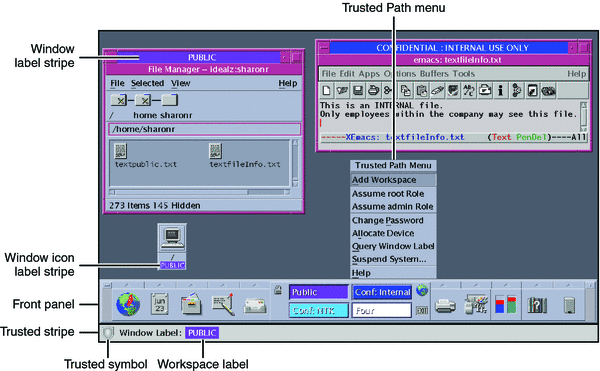
After you have successfully completed the login process, as explained in Chapter 2, Logging In to Trusted Extensions (Tasks), you can work within Trusted Extensions. Your work is subject to security restrictions. Restrictions that are specific to Trusted Extensions include the label range of the system, your clearance, and your choice of a single-level or multilevel session. As the following figure illustrates, four features distinguish a system that is configured with Trusted Extensions from a Solaris system.
Figure 4–1 Multilevel Trusted CDE Desktop
-
Label displays – All windows, workspaces, files, and applications have a label. The desktop provides stripes and other indicators for viewing an entity's label.
-
Trusted stripe – This stripe is a special graphical security mechanism. In Solaris Trusted Extensions (CDE), the trusted stripe is always displayed at the bottom of the screen. In Solaris Trusted Extensions (GNOME), the stripe is displayed at the top of the screen.
-
Limited access to applications from the workspace – The workspace provides access only to those applications that are permitted in your user account.
-
Trusted Path menu – In Trusted CDE, the switch area in the Front Panel provides access to the Trusted Path menu, which is used to perform security-related tasks. In Trusted GNOME, the trusted symbol provides access to the menu.
Labels on Trusted Extensions Desktops
As discussed in Mandatory Access Control, all applications and files in Trusted Extensions have labels. Trusted Extensions displays labels in the following locations:
-
Window label stripes above the window title bar
-
Window icon label stripes under the minimized window
-
Window label indicator in the trusted stripe
-
Query window label indicator from the Trusted Path menu that displays the label of the window or icon that is specified by the pointer location
Figure 4–1 shows how labels display on a system that is configured to display labels. The system is using Trusted CDE as its desktop. A site can also be configured to hide labels. Even if your administrator has configured the system to hide labels, labeling is still in effect. The Query Window Label menu item can be used to display the label of a window. For an illustration, see Figure 3–4.
Trusted Stripe
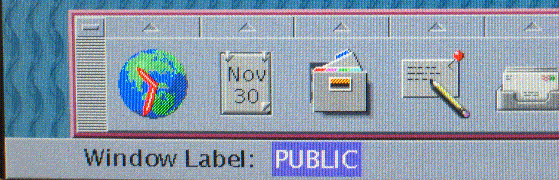
In Trusted CDE, the trusted stripe appears in a reserved area at the bottom of the screen in all Trusted Extensions sessions. In Trusted GNOME, the trusted stripe appears at the top of the screen.
The purpose of the trusted stripe is to give you a visual confirmation that you are in a legitimate Trusted Extensions session. The stripe indicates when you are interacting with the trusted computing base (TCB). The stripe also displays the labels of your current workspace and current window. The trusted stripe cannot be moved or obscured by other windows or dialog boxes.
In Trusted CDE, the trusted stripe has two elements:
-
The trusted symbol – Displays when the screen focus is security-related.
-
The window label – Optional. Displays the label of the active window.
In Trusted GNOME, the trusted stripe has two additional elements:
-
The current user name or role name – At the right of the trusted symbol, displays the name of the owner of new processes in the workspace.
-
Labeled windows – Displays the labels of all windows in the workspace.
Figure 4–2 PUBLIC Window Label in the Trusted Stripe
Trusted Symbol
Whenever you access any portion of the TCB, the trusted symbol appears at the left of the trusted stripe area. If your configuration suppresses labels, then the trusted symbol appears with the trusted stripe. In Trusted CDE, the symbol appears to the left of the Front Panel. In Trusted GNOME, the symbol appears at the left of the trusted stripe.

The trusted symbol is not displayed when the pointer is focused in a window or area of the screen that does not affect security. The trusted symbol cannot be forged. If you see the symbol, you can be sure that you are safely interacting with the TCB.
If the trusted stripe is missing from your workspace, contact the security administrator. The problem with your system could be serious.
The trusted stripe should not appear during login, or when you lock your screen. If the trusted stripe shows, contact the administrator immediately.
Window Label Indicator
The Window Label indicator displays the label of the active window. In a multilevel session, the indicator can help identify windows with different labels in the same workspace. The indicator can also show that you are interacting with the TCB. For example, when you change your password, the Trusted Path indicator displays in the trusted stripe.
Figure 4–3 Trusted Path Indicator in the Trusted Stripe

Files and Applications in Trusted Extensions
All applications in Trusted Extensions have a level of sensitivity that is indicated by their label. Applications are subjects in any data transactions. Subjects must dominate the objects that the subjects try to access. Objects can be files and sometimes other processes can be objects. The label information for an application is displayed in the window label stripe. The label is visible when a window is open and when a window is minimized. An application's label also appears in the trusted stripe when the pointer is in the application's window.
In Trusted Extensions, files are objects in data transactions. Files can be accessed only by applications whose labels dominate the files' labels. A file can be viewed from windows that have the same label as the file.
Some applications use initialization files to configure the environment for the user. Two special files in your home directory help you access initialization files at every label. These files enable an application at one label to use an initialization file that originates in a directory at a different label. The two special files are .copy_files and .link_files.
.copy_files File
The .copy_files file stores file names to be copied when you first change to a workspace with a higher label. .copy_files is stored in your home directory at your minimum label. This file is useful when you have an application that always writes to a file in your home directory with a specific name. .copy_files enables you to specify that the application update the file at every label.
.link_files File
The .link_files file stores file names to be linked when you first change to a workspace with a higher label. .link_files is stored in your home directory at your minimum label. This file is useful when a specific file needs to be available at multiple labels, but the content must be identical at every label.
Password Security in the Solaris OS
Users who change passwords on a frequent basis shorten the window of opportunity for intruders to use illegally obtained passwords. Therefore, your site's security policy can require you to change your password regularly. The Solaris OS can set content requirements for passwords and enforce password resetting requirements. The following are possible resetting requirements:
-
Minimum number of days between changes – Prevents you or anyone else from changing your password for a set number of days.
-
Maximum number of days between changes – Requires you to change your password after a set number of days.
-
Maximum number of inactive days – Locks your account after the set number of days of inactivity if the password has not been changed.
-
Expiration date – Requires you to change your password by a specific date.
If your administrator has implemented one of the preceding options, you are sent an email message that warns you to change your password prior to the cutoff date.
Passwords can have content criteria. At minimum, passwords in the Solaris OS must meet the following criteria:
-
The password must be at least eight characters long.
-
The password must contain at least two alphabetic characters and at least one numeric character or one special character.
-
The new password must differ from your previous password. You cannot use a reverse or circular shift of the previous password. For this comparison, uppercase letters and lowercase letters are considered to be equal.
-
The new password must have at least three characters that are different from the old password. For this comparison, uppercase letters and lowercase letters are considered to be equal.
-
The password must be difficult to guess. Do not use a common word or a proper name. Programs and individuals who try to break into an account can use lists to try to guess users' passwords.
You can change your password by using the Change Password menu item from the Trusted Path menu. For the steps, see Performing Trusted Actions.
Front Panel Security (Trusted CDE)
The Front Panel in Solaris Trusted Extensions (CDE) is very similar to the Front Panel that is used in the standard CDE. The Trusted Extensions Front Panel restricts access to only those applications, files, and utilities that you are allowed to use. By clicking mouse button 3 anywhere in the workspace switch area, the Trusted Path menu is displayed.
Before you can access a device through the Removable Media Manager, that device must be allocated by using the Device Allocation Manager. The Device Allocation Manager is accessed from the Tools subpanel, which is above the Style Manager icon in the Front Panel.
Tip –
If you minimize the Front Panel, you can restore the panel by clicking anywhere in the trusted stripe.
In Trusted Extensions, Install Icon drop sites are limited to the applications and files that you are permitted to use at the label of the current workspace.
For more information about the standard CDE, see the Common Desktop Environment User's Guide.
Workspace Switch Area
In Trusted Extensions, the workspace buttons not only define separate workspaces, but they also require you to work at particular labels. When you begin a multilevel session, each workspace is set to the lowest label that you can use. If your administrator has color-coded the labels at your site, the workspace buttons display the color of the label. The Trusted Path menu is available from the workspace switch area.
Trusted Path Menu
The Trusted Path menu contains menu items that affect security, as the following figure shows.
Figure 4–4 Trusted Path Menu – Basic
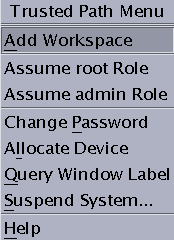
For example, you change your password or allocate devices with this menu. For details, see Performing Trusted Actions.
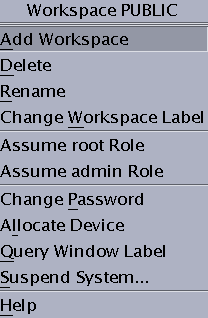
In Trusted CDE, the Trusted Path menu has a second version. The Workspace Name version includes additional workspace options. The selections that appear in your menu depend on how the administrator configured your account.
Figure 4–5 Trusted Path Menu – Workspace Name Version
Clock Security
In Trusted Extensions, only an administrator can change the date and time that is set for your workstation.
Calendar Security
The calendar shows the appointments for you at the label of your current workspace only. To view appointments at a different label, you need to open the calendar at that label.
File Manager Security
In Trusted Extensions, the File Manager displays files at the label of the current workspace. To view files at more than one label at a time, you run the File Manager from workspaces at different labels. You then use the Occupy Workspace command to display the different File Manager windows in the same workspace.
The File Manager enables you to change a file or folder's basic permissions and access control list (ACL). If you are authorized, you can also move or link files between File Managers at different labels. For details about File Manager use, see How to View Your Files in a Labeled Workspace and Performing Trusted Actions.
Text Editor Security
A text editor can be used to edit files at the label of the current workspace only. If you are authorized, you can copy information between text editors at different labels.
Personal Applications Subpanel
The default applications in the Personal Applications subpanel operate similarly to the standard CDE environment. The Terminal icon opens the default shell that is assigned to you by your administrator. To access a web server, the label of your browser must be the same as the label of the web server.
Mailer Security
In Trusted Extensions, all mail messages are labeled. When you send a message, it is sent at the label of your mail application. Only hosts and users that are cleared for that label receive the message. Only users who are working at that label can view the message.
If you need to use the vacation message option in your mail application, you must explicitly enable vacation message replies for each label at which you typically receive mail. Check with your security administrator for your site's security policy on vacation messages.
Printer Security
The Print Manager in the Personal Printers subpanel displays icons for all printers that are accredited up to your clearance. However, you can use only those printers that are accredited to print documents at the label of the current workspace.
A typical print job in Trusted Extensions includes labels and extra pages, as follows:
-
A banner page at the beginning of the print job identifies the print job, handling instructions, and labels that are appropriate to the site.
-
Body pages are labeled at the header and the footer.
-
A trailer page at the end of the print job signals the end of the job.
A typical banner page appears in the following figure. The words JOB START indicate the banner page.
Figure 4–6 Typical Banner Page of a Labeled Print Job
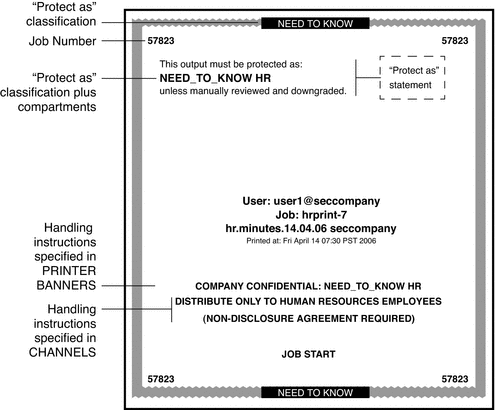
For the exact security information regarding printing at your site, see your administrator.
Style Manager Security
With three exceptions, the Style Manager operates in the same manner as on a Solaris system.
-
The Style Manager cannot be run from the Application Manager when Trusted Extensions is configured because the Style Manager requires the trusted path. Run the Style Manager from the Front Panel and the Workspace menu, where the Style Manager has the trusted path.
-
The Screen Saver and Screen Lock options are limited. Your administrator specifies the maximum amount of time that your system can be idle prior to being locked. You can reduce the idle time. You cannot increase the idle time beyond the maximum. You can still choose a pattern for when the screen is locked. See your administrator if you are not familiar with the policy at your site.
-
The Startup control sets your startup session settings according to the label or clearance that you specify at login. Thus, you can save a different workspace configuration for each label in your account label range.
Application Manager Security
The Application Manager provides access to only those applications and utilities that your administrator has assigned to you. In a role, you have access to a different set of applications and capabilities. Remember that the ability of a function to operate on a file depends on the label of the current workspace.
Similarly, although you can add applications to the Personal Application subpanel by dropping icons onto the Install Icon drop site, you can only run an application if your administrator has assigned the application to you.
Trash Can Security
In Trusted Extensions, the trash can stores files to be deleted by label. Although you can drop files at any label in the trash can, the trash can displays files at the current label only. You must delete sensitive information as soon as the information is in the trash can.
Workspace Security (Trusted GNOME)
In Trusted Extensions, Trusted GNOME provides equivalent security to Trusted CDE, but the look and feel is different. As in Trusted CDE, desktop applications are label-aware. Applications run at the label of the current workspace, and display information only at the label of the process that opened the application.
The location of security features differs in Trusted GNOME from their location in Trusted CDE. The behavior can also be different.
-
In Trusted GNOME, the Trusted Path menu is available from the trusted stripe.
-
The label name of a window in the task list on the panel appears in a tooltip when the mouse hovers over the window. Similarly, the label name of a workspace in the switch area appears in the tooltip.
-
To change a role, you click the user or role name in the trusted stripe and choose the role.
-
To add a workspace at a particular label, you select an existing workspace and change its label.
-
The desktop can be configured so that each workspace reflects the color of the label at which you are working in that workspace.
- © 2010, Oracle Corporation and/or its affiliates
