Appendix B Proxy Cache Reference
This chapter contains reference information and advanced procedures for the Netra j proxy cache service.
Advanced Proxy Cache Configuration Examples
This section describes >..the following advanced configuration scenarios:
Domains Inside Firewall and Local Domains Inside the Firewall
See "To View or Modify Proxy Cascade Properties" for a description of the properties described in this section.
If you have a hierarchy of proxy cache servers, you can use the Netra j proxy cache software's "local domain" features, illustrated in the following figure.
Figure B-1 Example of Use of Local Domain Property
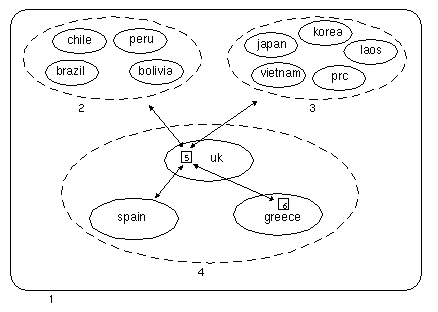
Legend:
-
DNS domain acme.com
-
The following DNS domains are in the geographic region of South America:
-
chile
-
peru
-
brazil
-
bolivia
-
-
The following DNS domains are in the geographic region of Asia:
-
japan
-
korea
-
laos
-
prc
-
vietnam
-
-
The following DNS domains are in the geographic region of Europe:
-
uk
-
greece
-
spain
-
-
Netra j proxy cache server netra_cache.uk
-
Netra j proxy cache server netra_cache.greece
In this example, the configuration for the Netra j proxy cache server netra_cache.greece (6) is as follows:
-
Parent proxy/cache: netra_cache.uk
-
Inside-the-firewall domain: acme.com
-
Local domain inside the firewall: greece.acme.com, spain.acme.com, uk.acme.com
The effect of these configuration options for the machine netra_cache.greece is that, in general, HTTP requests containing acme.com are retrieved from the parent, netra_cache.uk. However, requests for the local domain, greece, are retrieved directly from the local web server.
Limiting Access to the Server
See "To View or Modify Access Control Properties" for a description of the properties you use to limit access to the Netra j proxy cache server.
To limit access to the server, you define a filter in the Access List Definition property, then specify one or more filters for the following properties:
-
Client Access Control
-
Access to Cache via ICP
-
ACLs for Cache Host
-
URL Redirection
When you specify multiple entries for any of the preceding properties, list the lines in the order from the most exclusive (smallest set) toward the most inclusive (largest set). In processing multiple entries, the proxy cache service evaluates entries from top to bottom, stopping at the first entry that matches a URL request.
When you specify multiple access lists for a given property, those lists are ANDed.
Limiting by Source Address
The following are example access lists:
Under Access List Definition: eng src 129.144.118.0/255.255.255.0 sales src 129.144.130.0/255.255.255.0 division src 129.144.0.0/255.255.0.0
The preceding access lists might be used as follows:
Under Client Access Control: allow eng sales deny division
The preceding entries specify that machines on the subnets 129.144.118.0 and 129.144.130.0 are allowed HTTP access to the Netra j proxy cache server, while machines in the division list are excluded.
You might want to restrict Inter Cache Protocol (ICP) access to a server to only those machines. This is illustrated in the following example:
Under Access List Definition: arrayhosts src 129.144.107.1/255.255.255.255 129.144.107.2/255.255.255.255 \ 129.144.107.3/255.255.255.255 127.0.0.1/255.255.255.255 all src 0.0.0.0/0.0.0.0
Limiting by Time
The following are example access lists:
Under Access List Definition: nights time M-F 17:01-07:59 weekends time A-S 00:00-24:00 worktime time M-F 08:00-1700
The preceding access lists might be used as follows:
Under Client Access Control: deny nights weekends allow worktime
Note that A is the abbreviation for Saturday and S for Sunday.
Limiting by Domain in Request
The following are example access lists:
Under Access List Definition: poets domain .poetry .rhyme sports domain .espn .cnnsi cooks domain .culinary .gourmet
The preceding access lists might be used as follows:
Under Client Access Control: deny poets sports cooks
You might want to allow users access to the cache for non-work-hours web access. The following example uses time-based access lists defined in the preceding subsection.
Under Client Access Control: deny worktime poets sports cooks allow nights weekends poets sports cooks
Redirecting Requests
The following are example access lists:
Under Access List Definition: politics domain .rightwing .leftwing pop_culture domain .disney .twarner
The preceding access lists might be used as follows:
Under URL Redirection: politics : HOST www.vatican.net PATH /index.html pop_culture : HOST lcweb.loc.gov PATH /homepage/lchp.html
The effect of the preceding lines is that URL requests that match the politics filter are redirected to http://www.vatican.net/index.html. Requests that match pop_culture are redirected to http://lcweb.loc.gov/homepage/lchp.html.
Technical Information
This section describes the following technical information about the proxy cache software.
System Administrator and Proxy Webmaster Aliases
Netra j proxy cache software enables you to establish email recipients for mail that is addressed to root@netra_host_name or Postmaster@netra_host_name. When entering email addresses, make sure you specify addresses in a form compatible with your sendmail configuration. For example, if your mail system expects an address of a form login@nis_domain_name, mail sent to login@host_name is undeliverable.
Proxy Cache Connect Timeout and Parent Failover
The Netra j proxy cache server supports parent failover, in which, if the server's parent fails, the server switches to the next parent on its list. (See "To View or Modify Proxy Cascade Properties" for a description of the table of parent proxies.) Failover occurs if the Netra j proxy cache server's TCP connect call fails, not if the proxy cache service's connect timeout (2 minutes, by default) is exceeded. (See "To View or Modify Timeouts" for a description of the Timeout for Server Connections property.)
A TCP connect call might fail because the operating system's timeout (3 minutes, by default) is exceeded or from some other cause. If the proxy cache service's timeout is shorter than the operating system's (as is true for the default case), the connect attempt is terminated before an error is returned, with the result that parent failover does not occur.
If your server experiences frequent connection timeouts when attempting to connect to a parent, you can set the proxy cache service's connect timeout to be at least 10 seconds greater than the operating system's TCP connect timeout. Alternatively, (if you have a serial connection to your server) you can reduce the operating system's timeout. To change the operating system's timeout, use the ndd command, which takes arguments in milliseconds. For example:
# ndd -set /dev/tcp tcp_ip_abort_cinterval 30000
The preceding command sets the TCP connect timeout to 30 seconds. To view the current TCP connect timeout, enter:
# ndd /dev/tcp tcp_ip_abort_cinterval
Rules for Pattern Matching for TTL Selection Property
Listed below are the rules for pattern matching used for the reg_expression component of the TTL Selection Based on URL property, described in "URL Policy". These rules are taken from Section 3C of the Solaris regexec man page.
-
If subexpression i in a regular expression is not contained within another subexpression, and it participated in the match several times, then the byte offsets in pmatch[i] will delimit the last such match.
-
If subexpression i is not contained within another subexpression, and it did not participate in an otherwise successful match, the byte offsets in pmatch[i] will be -1. A subexpression does not participate in the match when:
-
* or \{ \} appears immediately after the subexpression in a basic regular expression, or *, ?, or {} appears immediately after the subexpression in an extended regular expression, and the subexpression did not match (matched zero times)
or
-
| is used in an extended regular expression to select this subexpression or another, and the other subexpression matched.
-
-
If subexpression i is contained within another subexpression j, and i is not contained within any other subexpression that is contained within j, and a match of subexpression j is reported in pmatch[j], then the match or non-match of subexpression i reported in pmatch[i] will be as described in 1. and 2. above, but within the substring reported in pmatch[j] rather than the whole string.
-
If subexpression i is contained in subexpression j, and the byte offsets in pmatch[j] are -1, then the pointers in pmatch[i] also will be -1.
-
If subexpression i matched a zero-length string, then both byte offsets in pmatch[i] will be the byte offset of the character or NULL terminator immediately following the zero-length string.
Adding a SCSI Disk
Depending on the hit rate experienced by your server, the size of cached objects, and client usage patterns, adding disk space can improve the performance of your server. Such an improvement would be manifested in reduced response time for users and decreased network traffic between the proxy server and its parents.
Adding a SCSI Disk includes three procedures:
-
Installing the new SCSI disk
-
Formatting the disk
-
Configuring new file systems
For these procedures, you must have a serial connection to the Netra j proxy cache server.
To Install a SCSI Disk
In the procedure specified below, for purposes of this example, assume the following:
-
You are adding a six-disk Sun StorEdge(TM) MultiPack enclosure to the existing SCSI controller (controller 0, or c0).
-
You will use all of the space on all of the disks in the enclosure for caching.
-
You will use slice (partition) 0 for all of the available space on a disk.
-
The disks in the MultiPack enclosure are formatted at the factory.
-
Set the address switch on the back of the MultiPack enclosure to 9-14.
The two internal disks are c0t0 and c0t1. For controller 0, you can use target numbers other than 0, 1, and 6, which is used by the CD-ROM drive.
-
Halt your machine.
In the Netra j Main Administration page, click Restart and Shutdown. In the Restart and Shutdown Administration page, click the Shutdown and power off operation and leave the check box for "Check for new devices upon restart" set to Yes. Click OK.
-
Ensure that the server is powered off (after about 90 seconds).
The green indicator light on the front of your machine is off when the machine is powered off.
-
Connect the MultiPack enclosure to the SCSI port on the back of the server.
-
Power on the enclosure.
To Format the New Disk
-
Power on the Netra j machine and log in as root.
-
# format
-
In the available-disk menu, select 2, for the first available disk after the two internal disks.
In this menu, there are eight disks: 0 and 1 for the internal disks and 2 through 7 for the disks in the MultiPack enclosure.
-
If the disk is new, you are asked whether to label the disk. Enter y to label the disk now.
-
In the format menu, enter p for partition.
-
In the partition menu, enter m to modify a partition table.
-
In response to the Select partitioning base menu, enter the number to select "modify the current partition table."
The current partition table is displayed.
-
In the displayed partition table, make a note of the number of cylinders for slice (partition) 2.
-
Press Return to indicate that, yes, you want to create a new partition table.
-
Press Return to accept the default partition number (for example, 6) for the free hog partition.
-
Enter the number of cylinders noted in Step 8 for the size of partition 0.
For example, 4101c, to indicate 4101 cylinders.
-
Except for the partition number for the free hog partition, enter a size of 0 for the remaining partitions. For the free hog partition, press Return to accept the default.
After making or accepting an entry for each partition, the partition table is displayed.
-
Press Return to OK the current partition table or enter n to make changes.
-
After confirming your partition table, you are prompted to enter a table name. Enter a name enclosed in quotes.
For example, "added_cache1", for the first disk in a MultiPack enclosure.
-
If the disk is not a new disk, you are asked whether you are ready to label the disk. Enter y to label the disk.
-
Enter q at the partition> prompt.
-
Enter disk at the format> prompt, to return to the available-disk menu.
-
Repeat Step 3 through Step 16 for each disk in the MultiPack enclosure.
For Step 3, enter the number that corresponds to the disk whose partition map you are modifying.
-
After you modify the partition map for the last disk in your MultiPack enclosure, enter q at the format> prompt (see Step 17), to exit format.
To Configure New File Systems
-
For each disk in the MultiPack enclosure, enter a newfs command of the following form:
# newfs /dev/rdsk/c0tnumd0s0 where num is, in succession, 9, 10, 11, 12, 13, and 14.
Each instance of the newfs command takes a few minutes.
-
Edit /etc/vfstab to add the new partitions.
# cat /etc/vfstab.orig #device device mount FS fsck mount mount #to mount to fsck point type pass at boot options # #/dev/dsk/c1d0s2 /dev/rdsk/c1d0s2 /usr ufs 1 yes - fd - /dev/fd fd - no - /proc - /proc proc - no - /dev/dsk/c0t0d0s1 - - swap - no - /dev/dsk/c0t1d0s1 - - swap - no - /dev/dsk/c0t0d0s0 /dev/rdsk/c0t0d0s0 / ufs 1 no - /dev/dsk/c0t1d0s0 /dev/rdsk/c0t1d0s0 /var ufs 1 no - this line continued from previous line ufs 2 yes - this line continued from previous line ufs 2 yes - swap - /tmp tmpfs - yes -
Using the disks in our example MultiPack enclosure, add lines such as the following to vfstab:
# The following disks were added to extend the cache /dev/dsk/c0t9d0s0 /dev/rdsk/c0t9d0s0 /var/opt/SUNWcache/cache3 this line continued from previous line ufs 2 yes - /dev/dsk/c0t10d0s0 /dev/rdsk/c0t10d0s0 /var/opt/SUNWcache/cache4 this line continued from previous line ufs 2 yes - /dev/dsk/c0t11d0s0 /dev/rdsk/c0t11d0s0 /var/opt/SUNWcache/cache5 this line continued from previous line ufs 2 yes - /dev/dsk/c0t12d0s0 /dev/rdsk/c0t12d0s0 /var/opt/SUNWcache/cache6 this line continued from previous line ufs 2 yes - /dev/dsk/c0t13d0s0 /dev/rdsk/c0t13d0s0 /var/opt/SUNWcache/cache7 this line continued from previous line ufs 2 yes - /dev/dsk/c0t14d0s0 /dev/rdsk/c0t14d0s0 /var/opt/SUNWcache/cache8 this line continued from previous line ufs 2 yes -
Note that the mount points, /var/opt/SUNWcache/cachenum, are present in the Netra j proxy cache software distribution.
-
Reboot.
In the Netra j Main Administration page, click Restart and Shutdown. In the Restart and Shutdown Administration page, click the Restart operation and leave the check box for "Check for new devices upon restart" set to Yes. Click OK.
Upon rebooting, in the console window, you receive output such as the following:
Disk configuration has changed. New filesystem detected: /var/opt/SUNWcache/cache3 New filesystem detected: /var/opt/SUNWcache/cache4 New filesystem detected: /var/opt/SUNWcache/cache5 New filesystem detected: /var/opt/SUNWcache/cache6 New filesystem detected: /var/opt/SUNWcache/cache7 New filesystem detected: /var/opt/SUNWcache/cache8 Disk configuration has changed. Reconfiguring the cache. Please wait. This operation should take no more than 5 minutes. Current time is: Fri Dec 5 11:06:04 PST 1997 0 1 2 3 4 5 (min) |_____|_____|_____|_____|_____|_____|_____|_____|_____|_____| DONE The cache has been reconfigured. oamserver in stop state The system is ready. host_name console login:
At this point, the proxy cache service can begin to use the additional disks for caching web objects.
- © 2010, Oracle Corporation and/or its affiliates
