Chapter 6 Configuring Web Proxies and Firewalls
This chapter explains how Sun Update Connection – Enterprise works through web proxies and firewalls, and what you need to do to configure Sun Update Connection – Enterprise to work in such an environment.
The Sun Update Connection – Enterprise agent, console, CLI, and API communicatesimilarly. Generally, tThe terms console, CLI, or API can replace agent when discussing proxies and firewalls..
Between the Sun Update Connection – Enterprise components, communications are secured. Between the agents and the dependency manager (DM), communications are encrypted with an RSA private/public key pair. Messages between the Sun Update Connection – Enterprise Apache-based server and the agents are in the secure HTTPS protocol.
Local security measures might include:
-
Firewall and web proxy between the Sun Update Connection – Enterprise server and the Sun server over the Internet.
-
Routers between agents on one side, and the DM and Sun Update Connection – Enterprise server on an other, over different local networks.
This chapter covers the following topics::
Defining the Components
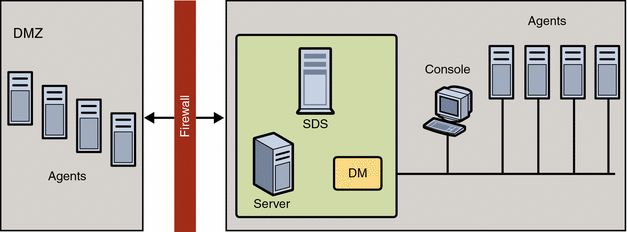
The Sun Update Connection – Enterprise architecture includes the server, DM, agents, consoles, CLI, and API on the local side; and the Sun Update Connection – Enterprise public servers over the Internet. This section describes the architecture components.
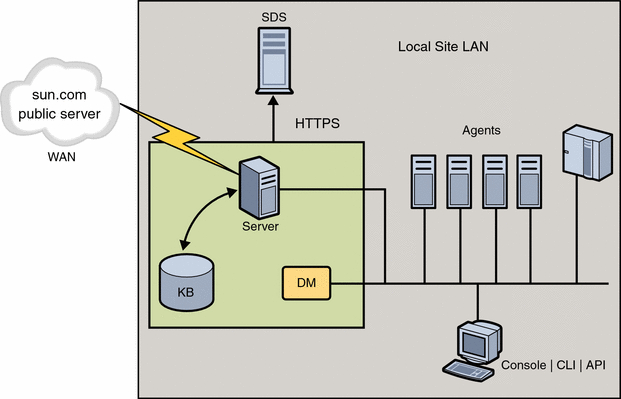
-
The public server is an Apache-based cache of Sun Update Connection – Enterprise certified components and their deployment rules, along with signature files and other security measures.
-
The Sun Update Connection – Enterprise server pulls data, in the form of Apache pages, from the public server and pushes on-demand to agents, consoles, CLI, and API.
-
The DM is the Sun Update Connection – Enterprise application that manages jobs. It manages communications between agents, consoles, CLI, and API.
-
The knowledge base (KB) is a repository of downloadable packages and their deployment rules.
-
The agent is the Sun Update Connection – Enterprise application that is installed on each host to be managed.
-
The console is a graphical user interface.
-
The CLI is a command-line interface.
-
The API is an optional, customer-built interface.
Defining Component Communications Details
This section explains how the Sun Update Connection – Enterprise components communicate with each other to fulfill Sun Update Connection – Enterprise functionality. In the following table, wherever agent is mentioned, it is true also of the console, CLI, and API.
Table 6–1 Component Communication Details|
Components |
Initiator |
Data Flow |
Connection Timing |
Port & Protocol |
|---|---|---|---|---|
|
Sun Update Connection – Enterprise server - public server |
Sun Update Connection – Enterprise server |
pull from public server |
scheduled check for new updates; on demand for agent needs; closed when task done. |
443 and HTTPS (443 is saved for HTTPS only) |
|
Sun Update Connection – Enterprise server - agents |
agents |
pull from KB via server |
on demand; closed when done |
HTTPS 8002 (8000-8100) |
|
DM - agents |
agent - login DM - alive pings both - messages |
bi-directional |
constant |
TCP/TP 8100 (8100-8200) DM listening port 8200 (8200 - 8300) agent listening for reconnect |
|
Sun Update Connection – Enterprise server - DM |
none |
none |
none |
none |
|
Sun Update Connection – Enterprise server - KB |
server |
pull from KB to fulfill jobs push of local to KB |
on demand; closed when done |
cache-type pull |
|
server.cgi - LRL |
server.cgi |
execute LRL |
on schedule |
application execution |
Editing the Configuration File
The Sun Update Connection – Enterprise server and the DM are installed with the ezInstaller program.
You can change the configuration of each Sun Update Connection – Enterprise component by editing the .uce.rc file.
Do not change the uce.rc file. If you want to make a change, make it in the override .uce.rc file (notice the dot in the override filename). Sun cannot accept responsibility for results if you change the default uce.rc file.
Configure the Sun Update Connection – Enterprise Server to the Public Server
The Sun Update Connection – Enterprise server is directed to the public server with parameters seen in /usr/local/uce/server/cgi-bin/.uce.rc file:
( server_name , "knowledge.aduva.com" ) ( server_port , 443 )
Do not change the values of these parameters in either of the rc files. The default value of server_name is the name of the public server, other values do not work. Likewise, server_port 443 is the only value that allows Sun Update Connection – Enterprise to operate correctly.
The Sun Update Connection – Enterprise server is the only Sun Update Connection – Enterprise component that communicates over the Internet (to the public server). The server uses secure HTTPS on port 443.
Web Proxy and Firewall Connection Parameters
A standard architecture on the local site contains a firewall and, in some cases, a web proxy.
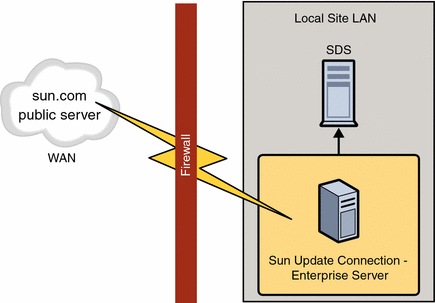
If the Sun Update Connection – Enterprise server is separated from the Internet by a web proxy, configure the connection parameters of the /usr/local/uce/server/cgi-bin/.uce.rc file.
Use one of the following methods to configure the connection parameters:
-
If your Internet security is in place before you install Sun Update Connection – Enterprise with the ezInstaller command, the following message is displayed:
Failed to connect to Universal Server. If you have a web proxy, configuring it might solve this problem. Would you like to setup proxy settings?
To setup your proxy settings, type Y and answer the questions to configure your web proxy. When completed, your web proxy parameters are automatically copied to the .uce.rc file and the local values are inserted.
-
If your Internet security was set up or changed after installation, copy the parameters from the Sun Update Connection – Enterprise server uce.rc file to the .uce.rc file and change the values for the local environment.
If you require Web proxy authentication, you might have to create the /etc/server/.proxyauth. The .proxyauth file contains the following line:
username:password
The following are the web proxy parameters:
( all ) ( proxy_server_name , "your_proxy" ); - hostname of web proxy ( all ) ( proxy_server_port , 8080 ); - open port of web proxy ( all ) ( proxy_user_name , "your_authentication_username" ); - username for authentication ( all ) ( proxy_user_password , "your_authentication_password" ); - password for authentication
Verify that the proxy.conf file is in the /etc/server/ directory. Web proxy authentication is optional. If you use authentication, the .proxyauth file must also be in the /etc/server/ directory.
Reconfiguring Agent, Console, CLI, and APIParameters
Agents, consoles, CLI, and APIs are each installed with a separate Install program. During automatic installation, the .uce.rc file for each is created and in it are placed local values for these parameters:
( server_name , "<server_hostname>" ); ( server_port , 8002 ); ( distrizor_host , "<engine_hostname>"); ( distizor_port , 8100); ( agent.__general.agent_port , 8200 );
The parameter files are:
-
/opt/local/uce/agent/bin/.uce.rc file – on every managed host
-
/~/.uce_console/bin/.uce.rc file – on /home directory of every console user
-
/usr/local/uce/cli/bin/.uce.rc file – on system with CLI
-
/~/.uce_python/bin/.uce.rc file – on /home directory of the uce-python API user
Agent Connections to Sun Update Connection – Enterprise Server
The default port between agents (including consoles, CLI, and API) and the Sun Update Connection – Enterprise server is 8002. This is the server_port parameter. If this port is not available on the local site, the range from 8000 to 8100 is searched. Agents call to the Sun Update Connection – Enterprise server using HTTPS.
If you want a different default port, open the UCE-<version>-<release>/scripts/defs file and change the value of DEFAULT_START_PORT before installing.
Agents to DM
Agents, consoles, CLI, and API do not communicate with each other; all their inter-connections are through the DM.
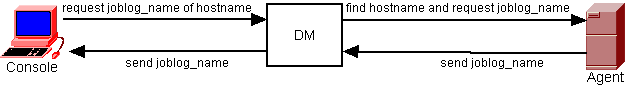
Agents (including consoles, CLI, and API) and the DM communicate over TCP/IP. The default listening port for the DM from the agents is 8100. However, when the agent and the DM first communicate, any open port between 8100 and 8200 can become their regular communication port. This port is configured in the distrizor_port parameter.
The agent might be released from this connection if traffic to the DM reaches the threshold. The DM maintains a pinging schedule and renew the connection when traffic opens. Agents listen to the DM for reconnection on the agent listening port: 8200. This is the agent_port parameter. If the local environment does not allow for 8200 to be used, the scanned range (during installation) is 8200 to 8300.
Agents on Different Networks
A standard site configuration separates agents by network segments (for example, Development might be a separate segment from Testing), and the agents might be on different networks than the Sun Update Connection – Enterprise server and the DM.
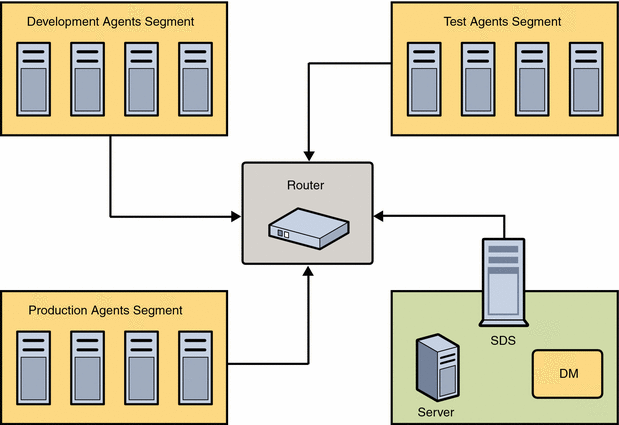
If this is the case, make sure that the ports for distrizor_port, agent_port, and server_port are open.
Agents With DMZ
If agents are separated from the Sun Update Connection – Enterprise server and DM by a DMZ setup, the agent's uce.rc file contains the proxy parameters (as shown in Agent Connections to Sun Update Connection – Enterprise Server) and can be configured in the .uce.rc file to reach the Sun Update Connection – Enterprise server.
It is recommended that the Sun Update Connection – Enterprise server and the DM be on the secured LAN, not on the DMZ.
- © 2010, Oracle Corporation and/or its affiliates
