How Trusted Solaris Keeps Labeled Information Separate
Trusted Solaris helps keep information at different sensitivity labels separate by
-
Letting users select single- or multilevel sessions
-
Providing labeled workspaces
-
Storing files in separate directories according to sensitivity label
-
Enforcing MAC for email transactions
-
Clearing objects prior to reuse
Letting Users Select Single- or Multilevel Sessions
When you first log into a Trusted Solaris session, you specify whether you will be operating at a single sensitivity label or at multiple sensitivity labels (if you are permitted to). You then set your session clearance or session sensitivity label, that is, the security level at which you intend to operate.
In a single-level session, you can access only those objects at or dominated by your session sensitivity label.
In a multilevel session, you can access information at different sensitivity levels, as long as they are at or lower than your session clearance. In the Trusted Solaris environment, you can specify different sensitivity labels for different workspaces.
Providing Labeled Workspaces
The workspaces in Trusted Solaris are accessed through buttons in the front panel, just as in the standard Solaris operating environment. However, in Trusted Solaris, you can devote a workspace entirely to a single sensitivity label. This is very convenient when you are in a multilevel session and do not wish to move information between files at different sensitivity labels.
Storing Files in Separate Directories by Sensitivity Labels
The Trusted Solaris environment provides two special types of directories for storing files and subdirectories with different sensitivity labels and keeping them separate:
-
multilevel directory (MLD) - is a special type of directory that transparently stores information by sensitivity label in separate subdirectories called single-level directories. Your administrator typically creates your home directory as multilevel directory.
-
single-level directory (SLD) - is a hidden subdirectory within a multilevel directory containing files and optionally subdirectories at a single sensitivity label only.
When you attempt to view or access files in a multilevel directory, (either through an application such as the File Manager or through a shell using standard commands), only those files that are at your current sensitivity label are visible and accessible. If you keep files at different sensitivity labels in your home directory, for example, you cannot normally view files at sensitivity labels other than your current sensitivity label.
The following figure illustrates the concept of hidden single-level directories within a multilevel directory. The top part of the figure shows the contents of a multilevel home directory called /myHomeDir from the user's view while working at Confidential A B; the lower part of the figure shows the user at Secret A B. Hidden directories and files are indicated with dashed lines and unbolded text; the solid lines and bolded text indicate visible ones. (Note that the sensitivity labels associated with the single-level directories are shown in their short form inside parentheses; the sensitivity labels do not actually appear in the directory names.)
Figure 1-4 Visible and Hidden Files and Directories
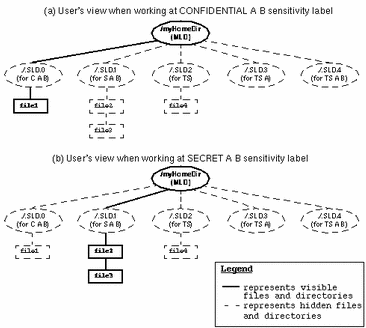
While working at Confidential A B, the user has the following results when trying to list the contents of the /myHomeDir directory:
% pwd /myhomedir % ls file1 |
At Secret A B, the user sees these results:
% pwd /myhomedir % ls file2 file3 |
Enforcing MAC for Email Transactions
Trusted Solaris enforces mandatory access control whenever you use email. When you send email, Trusted Solaris prevents users with insufficiently high clearance from receiving it. On the receiving end, email is sorted by the sensitivity labels within your account range. Your current sensitivity label must be at the same level as the email message you intend to read; otherwise you must change your current sensitivity label.
Clearing Objects Prior to Reuse
Trusted Solaris prevents inadvertent exposure of sensitive information by automatically clearing (erasing) user-accessible objects, such as memory and disk space, prior to reuse. Processes on the system continuously allocate, deallocate, and reuse objects, such as memory and disk space. Failure to erase sensitive data prior to reuse of the object risks exposing the data to inappropriate users. Through device deallocation, Trusted Solaris clears all user-accessible objects prior to allocating them to processes. Note, however, you must clear any removable storage medium (floppy disk, magnetic tape, etc.) before another user can have access to it.
- © 2010, Oracle Corporation and/or its affiliates
