Appendix B Audit Record Descriptions
This appendix has two parts. The first part describes each part of an audit record structure and each audit token structure. The second part defines all of the audit records generated in Trusted Solaris 7 software by event description.
Audit Record Structure
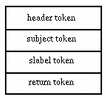
An audit record is a sequence of audit tokens. Each token contains event information such as user ID, time, and date. A header token begins an audit record, and an optional trailer concludes the record. Other audit tokens contain audit-relevant information. The following figure shows a typical audit record.
Figure B-1 Typical Audit Record
Audit Token Structure
Logically, each token has a token type identifier followed by data specific to the token. Each token type has its own format and structure. The audit tokens are shown in the table below. Those marked TS in the TS7 column are in Trusted Solaris 2.5.1 and Trusted Solaris 7 only. Those not marked TS are modified versions of audit tokens from the Solaris Basic Security Module. The token scheme can be extended.
Table B-1 Trusted Solaris Audit Tokens|
Token Name |
Description |
TS7 |
|---|---|---|
|
acl |
Access Control List information |
TS |
|
arbitrary |
Data with format and type information |
|
|
arg |
System call argument value |
|
|
attr |
File attributes |
|
|
clearance |
Clearance information |
TS |
|
exec_args |
Exec system call arguments |
|
|
exec_env |
Exec system call environment variables |
|
|
exit |
Program exit information |
|
|
file |
Audit file information |
|
|
groups |
Process groups information (obsolete) |
|
|
header |
Indicates start of record |
|
|
host |
Indicates the host where the audit record was collected |
TS |
|
ilabel |
Information label information (obsolete in Trusted Solaris 7) |
TS |
|
in_addr |
Internet address |
|
|
ip |
IP header information |
|
|
ipc |
System V IPC information |
|
|
ipc_perm |
System V IPC object tokens |
|
|
iport |
Internet port address |
|
|
liaison |
Liaison information for Trusted Networking |
TS |
|
newgroups |
Process groups information |
|
|
opaque |
Unstructured data (unspecified format) |
|
|
path |
Path information (path) |
|
|
priv |
Use of privilege information |
TS |
|
privilege |
Privilege set information |
TS |
|
process |
Process token information |
|
|
return |
Status of system call |
|
|
seq |
Sequence number token |
|
|
slabel |
sensitivity label information |
TS |
|
socket |
Socket type and addresses |
|
|
socket-inet |
Socket port and address |
|
|
subject |
Subject information (same structure as process token) |
|
|
text |
character string |
|
|
trailer |
Indicates end of record |
|
|
xatom |
X window atom identification |
TS |
|
xclient |
X client identification |
TS |
|
xcolormap |
X window color information |
TS |
|
xcursor |
X window cursor information |
TS |
|
xfont |
X window font information |
TS |
|
xgc |
X window graphical context information |
TS |
|
xpixmap |
Xwindow pixel mapping information |
TS |
|
xproperty |
X window property information |
TS |
|
xselect |
X window data information |
TS |
|
xwindow |
X window window information |
TS |
An audit record always contains a header token and may contain a trailer token. The header token indicates where the audit record begins in the audit trail. The optional trailer token allows backward seeks of the audit trail. Every audit record contains a subject token, except for audit records from some non-attributable events. In the case of attributable events, these two tokens refer to the values of the process that caused the event. In the case of asynchronous events, the process tokens refer to the system. For an example of how to read an audit record, go to "Reading an Audit Record".
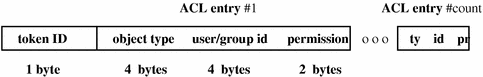
acl Token
The acl token provides information about any access control lists in place on an object. If there is no current acl, this token is not written to the audit record. Also, unless required by an audit record format, this token is normally recorded only when the appropriate auditing policy is set. The fields are:
-
A token ID
-
The object type of an array element
-
The user/group id of an array element
-
The permissions given to the subject
The following figure shows the token format.
Figure B-2 acl Token Format
A list of acl tokens is displayed by praudit(1M) as follows:
acl,user_obj,,rwx acl,user,bin,--- acl,group_obj,,r-x acl,class_obj,,r-- acl,other_obj,,r-x
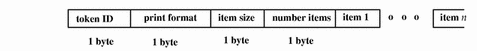
arbitrary Token
The arbitrary token encapsulates data for the audit trail. It consists of four fixed fields and an array of data. The item array may have a number of items. The fields are:
-
A token ID
-
A suggested format, such as decimal
-
A size of encapsulated data, such as int
-
A count of the data array items
-
An item array
The following figure shows the token format.
Figure B-3 arbitrary Token Format
The print format field can take the values shown in Table B-2.
Table B-2 arbitrary Token Print Format Field Values|
Value |
Action |
|---|---|
|
AUP_BINARY |
Print date in binary |
|
AUP_OCTAL |
Print date in octal |
|
AUP_DECIMAL |
Print date in decimal |
|
AUP_HEX |
Print date in hex |
|
AUP_STRING |
Print date as a string |
The item size field can take the values shown in Table B-3.
Table B-3 arbitrary Token Item Size Field Values|
Value |
Action |
|---|---|
|
AUR_BYTE |
Data is in units of bytes (1 byte) |
|
AUR_SHORT |
Data is in units of shorts (2 bytes) |
|
AUR_LONG |
Data is in units of longs (4 bytes) |
|
AUR_LONGLONG |
Data is in units of longlongs (8 bytes) |
An arbitrary token is displayed by praudit as follows:
arbitrary,decimal,int,1 42
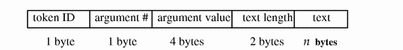
arg Token
The arg token contains system call argument information. A 32-bit integer system call argument is allowed in an audit record. The fields are:
-
A token ID
-
An argument ID of the relevant system call argument
-
The argument value
-
The length of an optional descriptive text string (does not show)
-
An optional text string
The following figure shows the token format.
Figure B-4 arg Token Format
An arg token is displayed by praudit as follows:
argument,2,0x3,cmd
attr Token
The attr token contains file attribute information from the kernel's internal representation of a file or folder. This token usually accompanies a path token and is produced during path searches. In the event of a path-search error, this token is not included as part of the audit record since the file attribute information is not available. The fields are:
-
A token ID
-
The file access mode and type
-
The owner user ID
-
The owner group ID
-
The file system ID
-
The inode ID
-
The device ID that the file might represent
See the statvfs(2) man page for further information about the file system ID and the device ID. The following figure shows the token format.
Figure B-5 attr Token Format

An attr token is displayed by praudit as follows:
attribute,100555,root,root,1805,13871,-4288
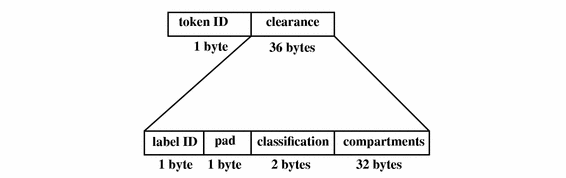
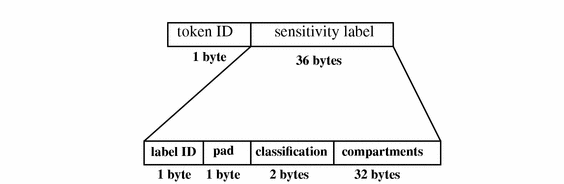
clearance Token
The clearance token contains Trusted Solaris clearance information. The fields are:
-
A token ID
-
The CMW clearance, containing
-
A pad ID identifying the label type
-
The clearance's classifications
-
The clearance's compartments
-
The following figure shows the token format.
Figure B-6 clearance Token Format
A clearance token is displayed by praudit as follows:
clearance,TOP SECRET
exec_args Token
The exec_args token records the arguments to an exec() system call. The fields are:
-
A token ID
-
A count that represents the number of arguments passed to the exec call
-
Zero or more null-terminated strings, the arguments of the exec call
The following figure shows an exec_args token.
Figure B-7 exec_args Token Format
Note -
The exec_args token is output only when the audit policy argv is active. See "Dynamic Procedures" for more information.
An exec_args token is displayed by praudit as follows:
exec_args,
exec_env Token
The exec_env token records the current environment variables to an exec() system call. The fields are:
-
A token ID
-
A count of the current environment variables in the exec call
-
Zero or more null-terminated strings, the variables of the exec call
The following figure shows an exec_env token.
Figure B-8 exec_env Token Format
Note -
The exec_env token is output only when the audit policy arge is active. See "Dynamic Procedures" for more information.
An exec_envtoken is displayed by praudit as follows:
exec_env,
exit Token
The exit token records the exit status of a program and a return value. The fields are:
-
A token ID
-
A program exit status as passed to the exit() system call
-
A return value that describes the exit status or indicates a system error number
The following figure shows an exit token.
Figure B-9 exit Token Format

An exit token is displayed by praudit as follows:
exit,Error 0,0
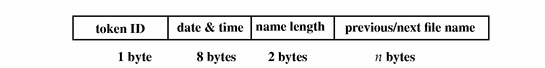
file Token
The file token is a special token generated by the audit daemon to mark the beginning of a new audit trail file and the end of an old file as it is deactivated. The audit daemon builds a special audit record containing this token to link together successive audit files into one audit trail. The fields are:
-
A token ID
-
A time and date stamp that identifies the time the file was created or closed
-
A byte count of the file name including a null terminator (does not show)
-
The file null-terminated name
The following figure shows the token format.
Figure B-10 file Token Format
A file token is displayed by praudit as follows:
file,Fri Jan 23 13:32:42 1997, + 79249 msec, /etc/security/audit/patchwork/files/19920901202558.19920901203241.patchwork
groups Token (Obsolete)
This token has been replaced by the newgroups token, which provides the same type of information but requires less space. A description of the groups token is provided here for completeness, but the application designer should use the newgroups token. Note that praudit does not distinguish between the two tokens as both token IDs are labelled groups when character output is displayed.
The groups token records the groups entries from the process's credential. The fields are:
-
A token ID
-
An array of groups entries of size NGROUPS_MAX (16)
The following figure shows a groups token.
Figure B-11 groups Token Format

A groups token is displayed by praudit as follows:
group,staff,wheel,daemon,kmem,bin,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1,-1
Note -
The groups token is output only when the audit policy group is active. See "The auditconfig Command" for more information.
header Token
The header token is special in that it marks the beginning of an audit record and combines with the trailer token to bracket all the other tokens in the record. The fields are:
-
A token ID
-
The record length in bytes, including the header and trailer tokens
-
An audit record structure version number
-
An event ID identifying the type of audit event
-
An event ID modifier with descriptive information about the event type
-
The time and date the record was created
The following figure shows a header token.
Figure B-12 header Token Format
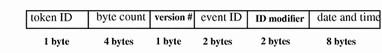
The event modifier field has the following flags defined:
|
Value |
Constant Name |
Description |
|---|---|---|
|
0x0001 |
PAD_MACUSE |
MAC decision was successful |
|
0x0002 |
PAD_MACREAD |
MAC read failure |
|
0x0004 |
PAD_MACWRITE |
MAC write failure |
|
0x0008 |
PAD_MACSEARCH |
MAC search failure |
|
0x0010 |
PAD_MACKILL |
MAC signal failure |
|
0x0020 |
PAD_MACTRACE |
MAC trace failure |
|
0x0040 |
PAD_MACIOCTL |
MAC ioctl failure |
|
0x0080 |
PAD_SPRIVUSE |
Successful use of privilege |
|
0x0100 |
PAD_FPRIVUSE |
Failed use of privilege |
|
0x4000 |
PAD_NONATTR |
Nonattributable event |
|
0x8000 |
PAD_FAILURE |
Failed audit event |
A header token is displayed by praudit as follows:
header,449,3,pfsh(1M),,Mon May
host Token
The host token contains the machine ID for the workstation which generated this audit record. The fields are:
-
A token ID
-
The workstation ID of the host that generated the audit record
The following figure shows the token format.
Figure B-13 host Token Format

A host token is displayed by praudit as follows:
host,patchwork
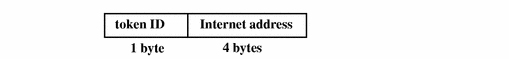
in_addr Token
The in_addr token contains an Internet address. This 4-byte value is an Internet Protocol address. The fields are:
-
A token ID
-
An Internet address
The following figure shows the token format.
Figure B-14 in_addr Token Format
An in_addr token is displayed by praudit as follows:
ip addr,129.150.110.3
ip Token
The ip token contains a copy of an Internet Protocol header but does not include any IP options. The IP options may be added by including more of the IP header in the token. The IP header structure is defined in /usr/include/netinet/ip.h. The fields are:
-
A token ID
-
A 20-byte copy of an IP header (all 20 bytes)
The following figure shows the token format.
Figure B-15 ip Token Format

An ip token is displayed by praudit as follows:
ip,0.0.0.0
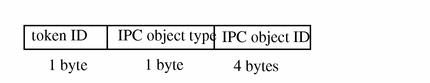
ipc Token
The ipc token contains the System V IPC message/semaphore/shared-memory handle used by the caller to identify a particular IPC object. The fields are:
-
A token ID
-
An IPC object type identifier
-
The IPC object handle
The following figure shows the token format.
Figure B-16 ipc Token Format
An ipc token is displayed by praudit as follows:
IPC,msg,3
Note -
The IPC object identifiers violate the context-free nature of the Solaris CMW audit tokens. No global "name" uniquely identifies IPC objects; instead, they are identified by their handles, which are valid only during the time the IPC objects are active. The identification should not be a problem since the System V IPC mechanisms are seldom used and they all share the same audit class.
The IPC object type field may have the values shown in Table B-4. The values are defined in </usr/include/bsm/audit.h>.
Table B-4 IPC Object Type Field|
Name |
Value |
Description |
|---|---|---|
|
AU_IPC_MSG |
1 |
IPC message object |
|
AU_IPC_SEM |
2 |
IPC semaphore object |
|
AU_IPC_SHM |
3 |
IPC shared memory object |
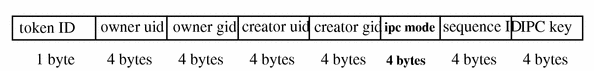
ipc_perm Token
The ipc_perm token contains a copy of the System V IPC access information. Audit records for shared memory, semaphore, and message IPCs have this token added. The fields are:
-
A token ID
-
The IPC owner's user ID
-
The IPC owner's group ID
-
The IPC creator's user ID
-
The IPC creator's group ID
-
The IPC access modes
-
The IPC sequence number
-
The IPC key value
The values are taken from the ipc_perm structure associated with the IPC object. The following figure shows the token format.
Figure B-17 ipc_perm Token Format
An ipc_perm token is displayed by praudit as follows:
IPC perm,root,wheel,root,wheel,0,0,0x00000000
iport Token
The iport token contains the TCP (or UDP) port address. The fields are:
-
A token ID
-
A TCP/UDP address
The following figure shows the token format.
Figure B-18 iport Token Format

An iport token is displayed by praudit as follows:
iport,0xf6d6
liaison Token
The liaison token contains a liaison ID used by the Trusted Networking software. The fields are:
-
A token ID
-
The liaison ID
The following figure shows the token format.
Figure B-19 liaison Token Format

A liaisontoken is displayed by praudit as follows:
liaison,17
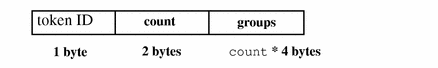
newgroups Token
This token is the replacement for the groups token. Note that praudit does not distinguish between the two tokens as both token IDs are labelled groups when character output is displayed.
The newgroups token records the groups entries from the process's credential. The fields are:
-
A token ID field
-
A count of the number of groups contained in this audit record.
-
Zero or more group entries.
The following figure shows the token format.
Figure B-20 newgroups Token Format
Note -
The newgroups token is output only when the audit policy group is active. See "The auditconfig Command" for more information.
A newgroups token is displayed by praudit as follows:
newgroups,1,analysts
opaque Token
The opaque token contains unformatted data as a sequence of bytes. The fields are:
-
A token ID
-
A byte count of the data array
-
An array of byte data
The following figure shows the token format.
Figure B-21 opaque Token Format

An opaque token is displayed by praudit as follows:
opaque,12,0x4f5041515545204441544100
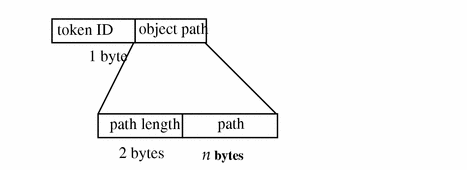
path Token
The path token contains access path information for an object. The fields are:
-
A token ID
-
A byte count of the path length (does not show)
-
An absolute path to the object based on the real root of the system
The following figure shows the token format.
Figure B-22 path Token Format
A path token is displayed by praudit as follows:
path,/etc/security/audit/patchwork
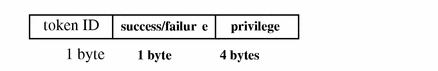
priv Token
The priv token contains use of privilege information. The fields are:
-
A token ID
-
A success/failure field indicating whether the use of privilege was successful (1 success, 0 failure)
-
The privilege being tested
The following figure shows a priv token.
Figure B-23 priv Token Format
A priv token is displayed by praudit as follows:
useofpriv,failed use of priv,win_mac_write
privilege Token
The privilege token contains privilege information for an object or a subject. The fields are:
-
A token ID
-
The type of privilege
-
The privilege set
where type is one of the following:
|
Value |
Type |
|---|---|
|
0 |
Unknown or Undefined |
|
1 |
Forced |
|
2 |
Allowed |
|
3 |
Effective |
|
4 |
Inheritable |
|
5 |
Permitted |
|
6 |
Saved |
The following figure shows the token format.
Figure B-24 privilege Token Format

A privilege token is displayed by praudit as follows:
privilege,1,proc_tcb_audit
process Token
The process token contains information describing a process as an object such as the recipient of a signal. The fields are:
-
A token ID
-
The user audit ID
-
The effective user ID
-
The effective group ID
-
The real user ID
-
The real group ID
-
The process ID
-
The session ID
-
A terminal ID made up of
-
A device ID
-
A workstation ID
-
The following figure shows the token format.
Figure B-25 Format for process and subject Tokens
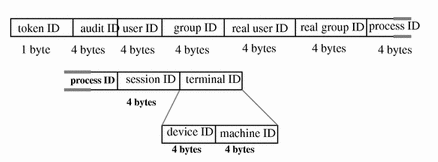
The audit ID, user ID, group ID, process ID, and session ID are long instead of short.
Note -
The process token fields for the session ID, the real user ID, or the real group ID may be unavailable. The entry is then set to -1.
A process token is displayed by praudit as follows:
process,root,root,wheel,root,wheel,0,0,0,0.0.0.0
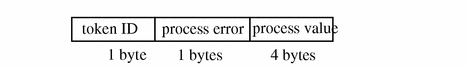
return Token
The return token contains the return status of the system call (u_error) and the process return value (u_rval1). The token indicates exit status and other return values in application auditing. This token is always returned as part of kernel-generated audit records for system calls. The fields are:
-
A token ID
-
The system call error status
-
The system call return value
The following figure shows the token format.
Figure B-26 return Token Format
A return token is displayed by praudit as follows:
return,failure: No such file or directory,-1
seq Token
The seq token (sequence token) is an optional token that contains an increasing sequence number. This token is for debugging. The token is added to each audit record when the AUDIT_SEQ policy is active. The fields are:
-
A token ID
-
A 32-bit unsigned long-sequence number
The sequence number is incremented every time an audit record is generated and put onto the audit trail. The following figure shows the token format.
Figure B-27 seq Token Format
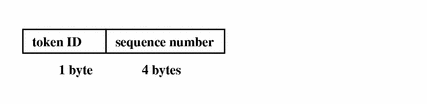
A seq token is displayed by praudit as follows:
sequence,1292
slabel Token
The slabel token contains a sensitivity label. The fields are:
-
A token ID
-
A sensitivity label
The following figure shows the token format.
Figure B-28 slabel Token Format
An slabel token is displayed by praudit as follows:
slabel,ADMIN_LOW
socket Token
The socket token contains information describing an Internet socket. The fields are:
-
A token ID
-
A socket type field (TCP/UDP/UNIX)
-
The local port address
-
The local Internet address
-
The remote port address
-
The remote Internet address
The socket type is taken from the designated socket and the port and Internet addresses are taken from the socket's inpcb control structure. The following figure shows the token format.
Figure B-29 socket Token Format

A socket token is displayed by praudit as follows:
socket,0x0000,0x0000,0.0.0.0,0x0000,0.0.0.0 socket,0x0002,0x8008,patchwork
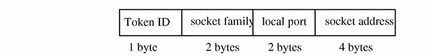
socket-inet Token
The socket-inet token describes a socket connection to a local port, which is used to represent the socket information in the Internet namespace. The fields are:
-
A token ID
-
A socket family field that indicates the Internet family (AF_INET, AF_OSI, and so on)
-
The local port address
-
The socket address
The following figure shows the token format.
Figure B-30 socket-inet Token Format
A socket-inet token is displayed by praudit as follows:
socket,0x0002,0x8008,patchwork
subject Token
The subject token describes a subject (process). The structure is the same as the process token:
-
A token ID
-
The user audit ID
-
The effective user ID
-
The effective group ID
-
The real user ID
-
The real group ID
-
The process ID
-
The session ID
-
A terminal ID made up of
-
A device ID
-
A workstation ID
-
This token is always returned as part of kernel-generated audit records for system calls. The audit ID, user ID, group ID, process ID, and session ID are long instead of short. Figure B-25 shows the token format.
Note -
The subject token fields for the session ID, the real user ID, or the real group ID may be unavailable. The entry is then set to -1.
A subject token is displayed by praudit as follows:
subject,root,root,staff,root,staff,552,552,24 3 patchwork
text Token
The text token contains a text string. The fields are:
-
A token ID
-
The length of the text string (does not show)
-
A text string
The following figure shows the token format.
Figure B-31 text Token Format
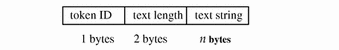
A text token is displayed by praudit as follows:
text,emily
trailer Token
A trailer token it marks the end of an audit record to support backward seeks of the audit trail. It is an optional token that is added as the last token of each record only when the AUDIT_TRAIL audit policy has been set. The fields are:
-
A token ID
-
A pad number that marks the end of the record (does not show)
-
The total number of audit record characters including the header and trailer tokens
The following figure shows the token format.
Figure B-32 trailer Token Format
A trailer token is displayed by praudit as follows:
trailer,136
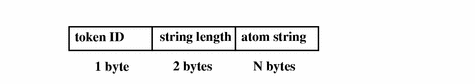
xatom Token
The xatom token contains information concerning an X atom. The fields are:
-
A token ID
-
The string length
-
A text string identifying the atom
The following figure shows the token format.
Figure B-33 xatom Token Format
An xatom token is displayed by praudit as follows:
xatom,_DT_SAVE_MODE
xclient Token
The xclient token contains information concerning the X client. The fields are:
-
A token ID
-
The client ID
The following figure shows the token format.
Figure B-34 xclient Token Format

An xclient token is displayed by praudit as follows:
xclient,15
xcolormap Token
The xcolormap token contains information about the colormaps. The fields are:
-
A token ID
-
The X server identifier
-
The creator's user ID
The following figure shows the token format.
Figure B-35 Format for xcolormap, xcursor, xfont, xgc, xpixmap, and xwindow Tokens
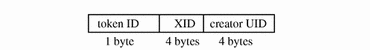
An xcolormap token is displayed by praudit as follows:
xcolormap,0x08c00005,srv
xcursor Token
The xcursor token contains information about the cursors. The fields are:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure B-35 shows the token format.
An xcursor token is displayed by praudit as follows:
xcursor,0x0f400006,srv
xfont Token
The xfont token contains information about the fonts. The fields are:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure B-35 shows the token format.
An xfont token is displayed by praudit as follows:
xfont,0x08c00001,srv
xgc Token
The xgc token contains information about the xgc. The fields are:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure B-35 shows the token format.
An xgc token is displayed by praudit as follows:
xgc,0x002f2ca0,srv
xpixmap Token
The xpixmap token contains information about the pixel mappings. The fields are:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure B-35 shows the token format.
An xpixmap token is displayed by praudit as follows:
xpixmap,0x08c00005,srv
xproperty Token
The xproperty token contains information about various properties of a window. The fields are:
-
A token ID
-
The X server identifier
-
The creator's user ID
-
A string length
-
A string (atom name)
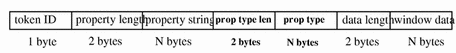
The following figure shows an xproperty token format.
Figure B-36 xproperty Token Format
An xproperty token is displayed by praudit as follows:
xproperty,0x000075d5,root,_MOTIF_DEFAULT_BINDINGS
xselect Token
The xselect token contains the data moved between windows. This data is a byte stream with no assumed internal structure, and a property string. The fields are:
-
A token ID
-
The length of the property string
-
The property string
-
A length for the property type
-
The property type string
-
A length field that gives the number of bytes of data
-
A byte string containing the data
The following figure shows the token format.
Figure B-37 xselect Token Format
An xselect token is displayed by praudit as follows:
xselect,
xwindow Token
The xwindow token contains information about a window. The fields are:
-
A token ID
-
The X server identifier
-
The creator's user ID
Figure B-35 shows the token format.
An xwindow token is displayed by praudit as follows:
xwindow,0x07400001,gww
Audit Records
General Audit Record Structure
The audit records produced by Trusted Solaris 7 have a sequence of tokens. Certain tokens are optional within an audit record, according to the current audit policy. The group, sequence, and trailer tokens fall into this category. The administrator can determine if these are included in an audit record with the auditconfig command -getpolicy option.
Kernel-Level Generated Audit Records
These audit records are created by system calls which are used by the kernel. The records are sorted alphabetically by system call. The description of each record includes:
-
The name of the system call
-
A man page reference (if appropriate)
-
The audit event number
-
The audit event name
-
The audit event class
-
The mask for the event class
-
The audit record structure
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_ACCESS |
14 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-6 acct(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_ACCT |
18 |
as |
0x00020000 |
|
Format (zero path): header-token argument-token (1, "accounting off", 0) [priv-token] (if privilege used or required) subject-token return-token Format (non-zero path): header-token path-token [attr-token] subject-token return-token |
|||
Table B-7 adjtime(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_ADJTIME |
50 |
as |
0x00000800 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-8 audit(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDIT |
211 |
no |
0x00000000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-9 auditon(2) -- get current active root
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GETCAR |
224 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-10 auditon(2) -- get event class
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GETCLASS |
231 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-11 auditon(2) -- get audit state
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GETCOND |
229 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token
|
|||
Table B-12 auditon(2) -- get current working directory
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GETCWD |
223 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-13 auditon(2) -- get kernel mask
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GETKMASK |
221 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token
|
|||
Table B-14 auditon(2) -- get audit statistics
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GETSTAT |
225 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-15 auditon(2) -- GETPOLICY command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GPOLICY |
114 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-16 auditon(2) -- get audit queue control parameters
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_GQCTRL |
145 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-17 auditon(2) -- set event class
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SETCLASS |
232 |
aa |
0x00040000 |
|
Format: header-token [argument-token] (2, "setclass:ec_event", event number) [argument-token] (3, "setclass:ec_class", class mask) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-18 auditon(2) -- set audit state
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SETCOND |
230 |
aa |
0x00040000 |
|
Format: header-token [argument-token] (3, "setcond", audit state) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-19 auditon(2) -- set kernel mask
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SETKMASK |
222 |
aa |
0x00040000 |
|
Format: header-token [argument-token] (2, "setkmask:as_success", kernel mask) [argument-token] (2, "setkmask:as_failure", kernel mask) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-20 auditon(2) -- set mask per session ID
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SETSMASK |
228 |
aa |
0x00040000 |
|
Format: header-token [argument-token] (3, "setsmask:as_success", session ID mask) [argument-token] (3, "setsmask:as_failure", session ID mask) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-21 auditon(2) -- reset audit statistics
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SETSTAT |
226 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-22 auditon(2) -- set mask per uid
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SETUMASK |
227 |
aa |
0x00040000 |
|
Format: header-token [argument-token] (3, "setumask:as_success", audit ID mask) [argument-token] (3, "setumask:as_failure", audit ID mask) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-23 auditon(2) -- SETPOLICY command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SPOLICY |
147 |
aa |
0x00040000 |
|
Format: header-token [argument-token] (1, "policy", audit policy flags) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-24 auditon(2) -- set audit queue control parameters
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITON_SQCTRL |
146 |
aa |
0x00040000 |
|
Format: header-token [argument-token] (3,"setqctrl:aq_hiwater",queue control param.) [argument-token] (3,"setqctrl:aq_lowater",queue control param.) [argument-token] (3,"setqctrl:aq_bufsz",queue control param.) [argument-token] (3,"setqctrl:aq_delay",queue control param.) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-25 auditpsa(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITPSA |
529 |
aa |
0x00040000 |
|
Format (valid file descriptor): header-token argument-token (1, "op", state) in_addr-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-26 auditstat(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITSTAT |
150 |
aa |
0x00040000 |
|
Format: header-token [argument-token] [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-27 auditsvc(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_AUDITSVC |
136 |
aa |
0x00040000 |
|
Format (valid file descriptor): header-token [path-token] [attr-token] [priv-token] (if privilege used or required) subject-token return-token Format (invalid file descriptor): header-token argument-token (1, "no path: fd", file descriptor) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-28 chdir(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CHDIR |
8 |
pc |
0x00300000 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-29 chmod(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CHMOD |
10 |
fm |
0x00000008 |
|
Format: header-token argument-token (2, "new file mode", mode) path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-30 chown(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CHOWN |
11 |
fm |
0x00000008 |
|
Format: header-token argument-token (2, "new file uid", uid) argument-token (3, "new file gid", gid) path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-31 chroot(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CHROOT |
24 |
pm |
0x00200000 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-32 chstate(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CHSTATE |
538 |
as |
0x00000800 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-33 clock_settime(3R)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CLOCK_SETTIME |
513 |
as |
0x00000800 |
|
Format: header-token slabel-token return-token |
|||
Table B-34 close(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CLOSE |
112 |
cl |
0x00000040 |
|
Format: <file system object> header-token argument-token (1, "fd", file descriptor) [path-token] [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Also for files closed on process termination. The argument-token is only present with the close() system call. It may be removed in future releases. The path-token is present only with valid file descriptors. |
|||
Table B-35 creat(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CREAT |
4 |
fc |
0x00000010 |
|
Format header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-36 devpolicy(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_DRVPOLICY |
531 |
as |
0x00000800 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-37 enter prom, exit prom
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_ENTERPROM |
153 |
na |
0x00000400 |
|
AUE_EXITPROM |
154 |
na |
0x00000400 |
|
Format: header-token text-token (addr, "monitor PROM"|"kadb") [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-38 exec(2), execve(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_EXEC |
7 |
ps |
0x00100000 |
|
AUE_EXECVE |
23 |
ps |
0x00100000 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-39 exit(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_EXIT |
1 |
pm |
0x00200000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-40 fauditpsa(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FAUDITPSA |
530 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-41 fchdir(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FCHDIR |
68 |
pc |
0x00300000 |
|
Format: header-token [path-token] [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-42 fchmod(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FCHMOD |
39 |
fm |
0x00000008 |
|
Format (valid file descriptor): header-token argument-token (2, "new file mode", mode) [path-token] [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Format (invalid file descriptor): header-token argument-token (2, "new file mode", mode) argument-token (1, "no path: fd", file descriptor) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-43 fchown(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FCHOWN |
38 |
fm |
0x00000008 |
|
Format (valid file descriptor): header-token argument-token (2, "new file uid", uid) argument-token (3, "new file gid", gid) [path-token] [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Format (non-file descriptor): header-token argument-token (2, "new file uid", uid) argument-token (3, "new file gid", gid) argument-token (1, "no path: fd", file descriptor) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-44 fchroot(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FCHROOT |
69 |
pm |
0x00200000 |
|
Format: header-token [path-token] [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-45 fcntl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FCNTL (cmd=F_GETLK, F_SETLK,F_SETLKW) |
30 |
fn |
0x40000000 |
|
Format (file descriptor): header-token argument-token (2, "cmd", cmd) path-token attr-token [priv-token] (if privilege used or required) subject-token return-token Format (bad file descriptor): header-token argument-token (2, "cmd", cmd) argument-token (1, "no path: fd", file descriptor) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-46 fgetsldname(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FGETSLDNAME |
532 |
fc |
0x00000010 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-47 fork(2), fork1(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FORK |
2 |
ps |
0x00100000 |
|
AUE_FORK1 |
241 |
ps |
0x00100000 |
|
Format: header-token [argument-token] (0, "child PID", pid) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token The fork() and fork1() return values are undefined since each audit record is produced at the point that the child process is spawned. |
|||
Table B-48 fsetcmwlabel(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FSETCMWLABEL |
544 |
fm |
0x00000008 |
|
Format: header-token argument-token (3, "flag", which parts of label to set) [slabel-token] (if slabel is being set) path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-49 fsetfattrflag(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FSETFATTRFLAG |
523 |
fm |
0x00000008 |
|
Format: header-token argument-token (2, "which", which flags to set) argument-token (3, "attrs", flag values) path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-50 fstatfs(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FSTATFS |
55 |
fa |
0x00000004 |
|
Format (file descriptor): header-token [path-token] [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Format (non-file descriptor): header-token argument-token (1, "no path: fd", file descriptor) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-51 getaudit(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETAUDIT |
132 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-52 getauid(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETAUID |
130 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-53 getcmwfsrange(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETCMWFSRANGE |
545 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-54 getcmwlabel(2), fgetcmwlabel(2), lgetcmwlabel(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETCMWLABEL |
546 |
fa |
0x00000004 |
|
AUE_FGETCMWLABEL |
118 |
fa |
0x00000004 |
|
AUE_LGETCMWLABEL |
548 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-55 getdents(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETDENTS |
193 |
no |
0x00000000 |
|
Format: header-token path-token [attr-token] [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-56 getfpriv(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETFILEPRIV |
547 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-57 getmldadorn(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETMLDADORN |
554 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-58 getmsg(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETMSG |
217 |
nt |
0x00000100 |
|
Format: header-token argument-token (1, "fd", file descriptor) argument-token (4, "pri", priority) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-59 getmsg(2) -- accept, receive
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SOCKACCEPT |
247 |
nt |
0x00000100 |
|
AUE_SOCKRECEIVE |
250 |
nt |
0x00000100 |
|
Format: header-token socket-inet-token argument-token (1, "fd", file descriptor) argument-token (4, "pri", priority) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-60 getmsgqcmwlabel(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETMSGQCMWLABEL |
514 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg ID", message ID) [argument-token] [ipc_perm-token] (of the IPC) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid. |
|||
Table B-61 getpmsg(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETPMSG |
219 |
nt |
0x00000100 |
|
Format: header-token argument-token (1, "fd", file descriptor) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-62 getportaudit(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETPORTAUDIT |
149 |
aa |
0x00040000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-63 getsemcmwlabel(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETSEMCMWLABEL |
515 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] (of the IPC) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the sem ID is invalid. |
|||
Table B-64 getshmcmwlabel(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETSHMCMWLABEL |
516 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm ID", semaphore ID) [argument-token] [ipc_perm-token] (of the IPC) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the shm ID is invalid. |
|||
Table B-65 getsldname(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_GETSLDNAME |
555 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-66 ioctl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_IOCTL |
158 |
io |
0x20000000 |
|
Format (good file descriptor): header-token path-token [attr-token] argument-token (2, "cmd" ioctl cmd) argument-token (3, "arg" ioctl arg) [priv-token] (if privilege used or required) subject-token return-token Format (socket): header-token [socket-token] argument-token (2, "cmd" ioctl cmd) argument-token (3, "arg" ioctl arg) [priv-token] (if privilege used or required) subject-token return-token Format (non-file file descriptor): header-token argument-token (1, "fd", file descriptor) argument-token (2, "cmd" ioctl cmd) argument-token (3, "arg" ioctl arg) [priv-token] (if privilege used or required) subject-token return-token Format (bad file name): header-token argument-token (1, "no path: fd", file descriptor) argument-token (2, "cmd" ioctl cmd) argument-token (3, "arg" ioctl arg) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-67 kill(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_KILL |
15 |
pm |
0x00200000 |
|
Format (valid process): header-token argument-token (2, "signal", signo) [process-token] [slabel-token] (process) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Format (zero or negative process): header-token argument-token (2, "signal", signo) argument-token (1, "process", pid) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-68 lchown(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_LCHOWN |
237 |
fm |
0x00000008 |
|
Format: header-token argument-token (2, "new file uid", uid) argument-token (3, "new file gid", gid) path-token [attr-token] [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-69 link(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_LINK |
5 |
fc |
0x00000010 |
|
Format: header-token path-token (from path) [attr-token] (from path) [slabel-token] (from path) path-token (to path) [attr-token] (to path) [slabel-token] (to path) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-70 lstat(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_LSTAT |
17 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-71 lxstat(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_LXSTAT |
236 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-72 memcntl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MEMCNTL |
238 |
ot |
0x80000000 |
|
Format: header-token argument-token (1, "base", base address) argument-token (2, "len", length) argument-token (3, "cmd", command) argument-token (4, "arg", command args) argument-token (5, "attr", command attributes) argument-token (6, "mask", 0) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-73 mkdir(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MKDIR |
47 |
fc |
0x00000010 |
|
Format: header-token argument-token (2, "mode", mode) path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-74 mknod(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MKNOD |
9 |
fc |
0x00000010 |
|
Format: header-token argument-token (2, "mode", mode) argument-token (3, "dev", dev) path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-75 mldsetfattrflag(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MLDSETFATTRFLAG |
524 |
fm |
0x00000008 |
|
Format: header-token argument-token (2, "which", which flags to set) argument-token (3, "attrs", flag values) [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-76 mmap(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MMAP |
210 |
no |
0x00000000 |
|
Format (valid file descriptor): header-token argument-token (1, "addr", segment address) argument-token (2, "len", segment length) [path-token] [attr-token] [priv-token] (if privilege used or required) subject-token return-token Format (invalid file descriptor): header-token argument-token (1, "addr", segment address) argument-token (2, "len", segment length) argument-token (1, "no path: fd", file descriptor) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-77 modctl(2) -- bind module
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MODADDMAJ |
246 |
as |
0x00000800 |
|
Format: header-token [text-token] (driver major number) [text-token] (driver name) text-token (root dir.|"no rootdir") text-token (driver major number|"no drvname") argument-token (5, "", number of aliases) (0..n)[text-token] (aliases) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-78 modctl(2) -- configure module
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MODCONFIG |
245 |
as |
0x00000800 |
|
Format: header-token text-token (root dir.|"no rootdir") text-token (driver major number|"no drvname") [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-79 modctl(2) -- load module
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MODLOAD |
243 |
as |
0x00020000 |
|
Format: header-token [text-token] (default path) text-token (filename path) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-80 modctl(2) -- unload module
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MODUNLOAD |
244 |
as |
0x00020000 |
|
Format: header-token argument-token (1, "id", module ID) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-81 mount(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MOUNT |
62 |
ao |
0x00080000 |
|
Format (UNIX file system): header-token argument-token (3, "flags", flags) text-token (filesystem type) path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Format (NFS file system): header-token argument-token (3, "flags", flags) text-token (filesystem type) text-token (host name) argument-token (3, "internal flags", flags) path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-82 msgctl(2) -- IPC_RMID command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MSGCTL_RMID |
85 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg ID", message ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid.
|
|||
Table B-83 msgctl(2) -- IPC_SET command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MSGCTL_SET |
86 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg ID", message ID) [argument-token] [ipc_perm-token] (of the IPC's old values) [slabel-token] [ipc_perm-token] (of the IPC's new values) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token subject-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid. |
|||
Table B-84 msgctl(2) -- IPC_STAT command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MSGCTL_STAT |
87 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg ID", message ID) [argument-token] [ipc_perm-token] (of the IPC) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid. |
|||
Table B-85 msgget(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MSGGET |
88 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg key", message key) argument-token (2, "msg flag", message flags) [ipc_perm-token] (of the IPC object) [slabel-token] [argument-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid. |
|||
Table B-86 msggetl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MSGGETL |
174 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg key", message key) argument-token (2, "msg flag", message flags) slabel-token (desired SL) [ipc_perm-token] (of the IPC object) [slabel-token] [argument-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid. |
|||
Table B-87 msgrcv(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MSGRCV |
89 |
ip |
0x00000200 |
|
AUE_MSGRCVL |
175 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg ID", message ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid. |
|||
Table B-88 msgsnd(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MSGSND |
90 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "msg ID", message ID) [argument-token] [ipc_perm-token] (of the IPC's new values) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the msg ID is invalid. |
|||
Table B-89 munmap(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_MUNMAP |
214 |
cl |
0x00000040 |
|
Format: header-token argument-token (1, "addr", address of memory) argument-token (2, "len", memory segment size) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-90 old nice(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_NICE |
203 |
pc |
0x00300000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-91 open(2) -- read
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_R |
72 |
fr |
0x00000001 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-92 open(2) -- read,creat
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_RC |
73 |
fc,fr |
0x00000011 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-93 open(2) -- read,trunc,creat
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_RTC |
75 |
fc,fd,fr |
0x00000031 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-94 open(2) -- read,trunc
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_RT |
74 |
fd,fr |
0x00000021 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-95 open(2) -- read,write
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_RW |
80 |
fr,fw |
0x00000003 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-96 open(2) -- read,write,creat
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_RWC |
81 |
fr,fw,fc |
0x00000013 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-97 open(2) -- read,write,trunc,creat
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_RWTC |
83 |
fr,fw,fc,fd |
0x00000033 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-98 open(2) -- read,write,trunc
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_RWT |
82 |
fr,fw,fd |
0x00000023 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-99 open(2) -- write
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_W |
76 |
fw |
0x00000002 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-100 open(2) -- write,creat
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_WC |
77 |
fw,fc |
0x00000012 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-101 open(2) -- write,trunc,creat
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_WTC |
79 |
fw,fc,fd |
0x00000032 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-102 open(2) -- write,trunc
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OPEN_WT |
78 |
fw,fd |
0x00000022 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-103 pathconf(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PATHCONF |
71 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-104 pipe(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PIPE |
185 |
no |
0x00000000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-105 preadl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PREADL |
527 |
no |
0x00000000 |
|
Format: header-token path-token [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-106 priocntl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PRIOCNTLSYS |
212 |
pm |
0x00200000 |
|
Format: header-token argument-token (1, "pc_version", priocntl version num.) argument-token (3,"cmd", command) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-107 privilege enable
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PRIVENABLE |
533 |
as |
0x00020000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-108 process dumped core
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_CORE |
111 |
fc |
0x0000010 |
|
Format: header-token path-token [attr-token] argument-token (1, "signal", signal) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-109 putmsg(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PUTMSG |
216 |
nt |
0x00000100 |
|
Format: header-token argument-token (1, "fd", file descriptor) argument-token (4, "pri", priority) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-110 putmsg(2) - connect, send
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SOCKCONNECT |
248 |
nt |
0x00000100 |
|
AUE_SOCKSEND |
249 |
nt |
0x00000100 |
|
Format: header-token socket-inet-token argument-token (1, "fd", file descriptor) argument-token (4, "pri", priority) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-111 putpmsg(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PUTPMSG |
218 |
nt |
0x00000100 |
|
Format: header-token argument-token (1, "fd", file descriptor) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-112 read(2), readl(2), readvl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_READ |
192 |
no |
0x00000000 |
|
AUE_READL |
558 |
|
|
|
AUE_READVL |
559 |
|
|
|
Format: header-token path-token) [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-113 readlink(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_READLINK |
22 |
fr |
0x00000001 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-114 rename(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_RENAME |
42 |
fc,fd |
0x00000030 |
|
Format: header-token path-token (from name) [attr-token] (from name) [slabel-token] (from name) [path-token] (to name) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-115 rmdir(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_RMDIR |
48 |
fd |
0x00000020 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-116 semctl(2) -- getall
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_GETALL |
105 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-117 semctl(2) -- GETNCNT command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_GETNCNT |
102 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-118 semctl(2) -- GETPID command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_GETPID |
103 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-119 semctl(2) -- GETVAL command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_GETVAL |
104 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-120 semctl(2) -- GETZCNT command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_GETZCNT |
106 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-121 semctl(2) -- IPC_RMID command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_RMID |
99 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-122 semctl(2) -- IPC_SET command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_SET |
100 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] (of the IPC's old values) [slabel-token] [ipc_perm-token] (of the IPC's new values) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-123 semctl(2) -- SETALL command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_SETALL |
108 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-124 semctl(2) -- SETVAL command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_SETVAL |
107 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-125 semctl(2) -- IPC_STAT command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMCTL_STAT |
101 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-126 semget(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMGET |
109 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem key", semaphore key) argument-token (3, "sem flags", semaphore flags) [ipc_perm-token] [slabel-token] [argument-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-127 semgetl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMGETL |
177 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem key", semaphore key) argument-token (3, "sem flags", semaphore flags) slabel-token [ipc_perm-token] [slabel-token] [argument-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the system call failed. |
|||
Table B-128 semop(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SEMOP |
110 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "sem ID", semaphore ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and the slabel of the ipc tokens are not included if the semaphore ID is invalid. |
|||
Table B-129 setacl(1), setfacl(1)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_ACLSET |
251 |
fm |
0x00000008 |
|
AUE_FACLSET |
252 |
fm |
0x00000008 |
|
Format: header-token argument-token (2,"cmd", command) argument-token (3,"n_entries", number of acl entries) acl-token ... (token repeated "n_entries" times) path-token [attr-token] [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-130 setaudit(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETAUDIT |
133 |
aa |
0x00040000 |
|
Format (valid program stack address): header-token argument-token (1, "setaudit:auid", audit user ID) argument-token (1, "setaudit:port", terminal ID) argument-token (1, "setaudit:machine", terminal ID) argument-token (1, "setaudit:as_success", preselection mask) argument-token (1, "setaudit:as_failure", preselection mask) argument-token (1, "setaudit:asid", audit session ID) [priv-token] (if privilege used or required) subject-token return-token Format (invalid program stack address): header-token subject-token return-token |
|||
Table B-131 setauid(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETAUID |
131 |
aa |
0x00040000 |
|
Format: header-token argument-token (2, "setauid", audit user ID) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-132 setclearance(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETCLEARANCE |
542 |
fm |
0x00000008 |
|
Format: header-token clearance-token (specified) clearance-token (old) clearance-token (new) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-133 setcmwlabel(2), lsetcmwlabel(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETCMWLABEL |
549 |
fm |
0x00000008 |
|
AUE_LSETCMWLABEL |
525 |
fm |
0x00000008 |
|
Format: header-token argument-token (3, "flag", which parts of label to set) [slabel-token] (if slabel is being set) [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-134 setcmwplabel(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETCMWPLABEL |
541 |
fm |
0x00000008 |
|
Format (setting flag == SETCL_ALL): header-token slabel-token (SL from input argument) slabel-token (original SL) argument-token (2, "flag", value) slabel-token (new SL) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Format (setting flag == SETCL_SL): header-token slabel-token (SL from input argument) slabel-token (SL of subject before) argument-token (2, "flag", value) slabel-token (SL of subject after) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Format (setting flag == SETCL_IL): header-token argument-token (2, "flag", value) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-135 setegid(2), old setgid(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETEGID |
214 |
pm |
0x00200000 |
|
AUE_SETGID |
205 |
pm |
0x00200000 |
|
Format: header-token argument-token (1, "gid", group ID) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-136 seteuid(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETEUID |
215 |
pm |
0x00200000 |
|
Format: header-token argument-token (1, "gid", user ID) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-137 setfattrflag(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETFATTRFLAG |
522 |
fm |
0x00000008 |
|
Format: header-token argument-token (2, "which", which flags to set) argument-token (3, "attrs", flag values) [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-138 setfpriv(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETFILEPRIV |
550 |
fm |
0x00000008 |
|
Format: header-token argument-token (4, "privilege type", privilege set type) privilege-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-139 setgroups(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETGROUPS |
26 |
pm |
0x00200000 |
|
Format: header-token [argument-token] (1, "setgroups", group ID) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token One argument-token for each group set. |
|||
Table B-140 setpattr(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETPATTR |
526 |
ps |
0x00100000 |
|
Format: header-token argument-token (1, "type", type of attribute to set) argument-token (2, "value", value of attribute) [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-141 setpgrp(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETPGRP |
27 |
pm |
0x00200000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-142 setppriv(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETPROCPRIV |
127 |
fm |
0x00000008 |
|
Format: header-token argument-token (3, "type", privilege set type) argument-token (4, "op", operation to perform) privilege-token (specified) privilege-token (old) [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-143 setregid(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETREGID |
41 |
pm |
0x00200000 |
|
Format: header-token argument-token (1, "rgid", real group ID) argument-token (1, "egid", effective group ID) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-144 setreuid(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETREUID |
40 |
pm |
0x00200000 |
|
Format: header-token argument-token (1, "ruid", real user ID) argument-token (1, "euid", effective user ID) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-145 setrlimit(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SETRLIMIT |
51 |
as |
0x00020000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-146 old setuid(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_OSETUID |
200 |
pm |
0x00200000 |
|
Format: header-token argument-token (1, "uid", user ID) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token Due to a current bug in the audit software, this token is reported as AUE_OSETUID. |
|||
Table B-147 shmat(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SHMAT |
96 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm ID", shared memory ID) argument-token (2, "shm adr", shared mem addr) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and slabel tokens are not included if the shared memory segment ID is invalid. |
|||
Table B-148 shmctl(2) -- IPC_RMID command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SHMCTL_RMID |
92 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm ID", shared memory ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and slabel tokens are not included if the shared memory segment ID is invalid. |
|||
Table B-149 shmctl(2) -- IPC_SET command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SHMCTL_SET |
93 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm ID", shared memory ID) [argument-token] [ipc_perm-token] (of the IPC's old values) [slabel-token] [ipc_perm-token] (of the IPC's new values) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and slabel tokens are not included if the shared memory segment ID is invalid. |
|||
Table B-150 shmctl(2) -- IPC_STAT command
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SHMCTL_STAT |
94 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm ID", shared memory ID) [argument-token] [ipc_perm-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token The ipc, ipc_perm, and slabel tokens are not included if the shared memory segment ID is invalid. |
|||
Table B-151 shmdt(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SHMDT |
97 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm adr", shared mem addr) [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-152 shmget(2)
|
Event Name |
Event ID |
EventClass |
Mask |
|---|---|---|---|
|
AUE_SHMGET |
95 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm ID", shared memory ID) argument-token (3, "shm flag", shared memory flags) [argument-token] [slabel-token] [ipc_perm-token] (of the IPC's old values) [slabel-token] [ipc_perm-token] (of the IPC's new values) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token subject-token The ipc, ipc_perm, and slabel tokens are not included for failed events. |
|||
Table B-153 shmgetl(2)
|
Event Name |
Event ID |
EventClass |
Mask |
|---|---|---|---|
|
AUE_SHMGETL |
178 |
ip |
0x00000200 |
|
Format: header-token argument-token (1, "shm ID", shared memory ID) argument-token (3, "shm flag", shared memory flags) slabel-token [ipc_perm-token] (of the IPC's old values) [slabel-token] [ipc_perm-token] (of the IPC's new values) [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token subject-token The ipc, ipc_perm, and slabel tokens are not included for failed events. |
|||
Table B-154 stat(2), statfs(2), statvfs(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_STAT |
16 |
fa |
0x00000004 |
|
AUE_STATFS |
54 |
fa |
0x00000004 |
|
AUE_STATVFS |
234 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-155 stime(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_STIME |
201 |
as |
0x00020000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-156 symlink(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SYMLINK |
21 |
fc |
0x00000010 |
|
Format: header-token text-token (symbolic link string) path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-157 sysinfo(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SYSINFO |
39 |
as |
0x00020000 |
|
Format: header-token argument-token (1, "cmd", command) text-token (name) [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-158 system booted
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SYSTEMBOOT |
113 |
na |
0x00000400 |
|
Format:
header-token
text-token ("booting kernel")
return-token
|
|||
Table B-159 tnif(2), tnrh(2), tnrhtp(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_TNIF |
534 |
nt |
0x00000100 |
|
AUE_TNRH |
535 |
|
|
|
AUE_TNRHTP |
536 |
|
|
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-160 tokmapper(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_TOKMAPPER |
537 |
nt |
0x00000100 |
|
Format: header-token argument-token (1, "op", state) in_addr-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-161 uadmin(2) - system freeze
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_FREEZE |
539 |
ss |
0x00010000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-162 uadmin(2) - system reboot
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_REBOOT |
561 |
ss |
0x00010000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-163 uadmin(2) - system remount
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_REMOUNT |
540 |
as |
0x00020000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-164 uadmin(2) - system shutdown
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_SHUTDOWN |
560 |
ss |
0x00010000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-165 umount(2) -- old version
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_UMOUNT |
12 |
ao |
0x00080000 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-166 unlink(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_UNLINK |
6 |
fd |
0x00000020 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-167 old utime(2), utimes(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_UTIME |
202 |
fm |
0x00000008 |
|
AUE_UTIMES |
49 |
fm |
0x00000008 |
|
Format: header-token path-token [attr-token] [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-168 utssys(2) -- fusers
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_UTSSYS |
233 |
ao |
0x00080000 |
|
Format: header-token path-token [attr-token] [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-169 vfork(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_VFORK |
25 |
ps |
0x00100000 |
|
Format: header-token argument-token (0, "child PID", pid) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token The fork return values are undefined since the audit record is produced at the point that the child process is spawned. |
|||
Table B-170 vtrace(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_VTRACE |
36 |
pm |
0x00200000 |
|
Format: header-token [priv-token] (if privilege used or required) subject-token return-token |
|||
Table B-171 write(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_WRITE |
195 |
no |
0x00000000 |
|
Format: header-token slabel-token (from label specified in syscall args) path-token) [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-172 writel(2), pwritel(2), writevl(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_PWRITEL |
528 |
no |
0x00000000 |
|
AUE_WRITEL |
552 |
fm |
0x00000008 |
|
AUE_WRITEVL |
553 |
fm |
0x00000008 |
|
Format: header-token slabel-token (from label specified in syscall args) path-token) [attr-token] [slabel-token] [priv-token] (if privilege used or required) subject-token slabel-token return-token |
|||
Table B-173 xmknod(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_XMKNOD |
240 |
fc |
0x00000010 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Table B-174 xstat(2)
|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_XSTAT |
235 |
fa |
0x00000004 |
|
Format: header-token path-token [attr-token] [slabel-token] (object) [priv-token] (if privilege used or required) subject-token slabel-token (subject) return-token |
|||
Kernel-Level Pseudo-Events
Pseudo-events do have their own audit record structure. They create audit records for the event that uses privilege. When the pseudo-event AUE_UPRIV is in a class that is being audited, any use of privilege will be audited, including uses of privilege for events that are otherwise not being audited.
Table B-175 Use of privilege|
Event Name |
Event ID |
Event Class |
Mask |
|---|---|---|---|
|
AUE_UPRIV |
521 |
no |
0x00000000 |
X Server Protocol Audit Records
These audit records are created by X windows calls and use of the X server. The records are sorted alphabetically by protocol; where possible, records with identical structure are listed together. The description of each record includes:
-
The name of the protocol
-
The audit event number
-
The audit event name
-
The audit record structure
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ClientConnect |
Client connection to Xserver |
9101 |
xl |
0x08000000 |
|
Format: header-token subject-token newgroups-token slabel-token xclient-token inaddr-token (IP address of client) iport-token (port on server) return-token |
||||
Table B-177 XClientDisconnect
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ClientDisconnect |
Client logout from Xserver |
9102 |
xl |
0x08000000 |
|
Format: header-token subject-token newgroups-token slabel-token xclient-token return-token |
||||
Table B-178 X Server Protocols - window operations
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ChangeSaveSet |
Change the saved set |
9108 |
xp |
0x10000000 |
|
AUE_ChangeWindowAttributes |
Change window attributes |
9104 |
|
|
|
AUE_CirculateWindow |
Circulate the window |
9115 |
|
|
|
AUE_ConfigureWindow |
Configure the window |
9114 |
|
|
|
AUE_CreateWindow |
Create window |
9103 |
|
|
|
AUE_DestroySubwindows |
Destroy subwindows |
9107 |
|
|
|
AUE_DestroyWindow |
Destroy window |
9106 |
|
|
|
AUE_GetGeometry |
Get window geometry |
9116 |
|
|
|
AUE_GetWindowAttributes |
Get window attributes |
9105 |
|
|
|
AUE_MapSubwindows |
Map the subwindows |
9111 |
|
|
|
AUE_MapWindow |
Map the window |
9110 |
|
|
|
AUE_QueryTree |
Query window tree |
9117 |
|
|
|
AUE_ReparentWindow |
Reparent the window |
9109 |
|
|
|
AUE_UnmapSubwindows |
Unmap the subwindows |
9113 |
|
|
|
AUE_UnmapWindow |
Unmap the window |
9112 |
|
|
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token return-token |
||||
Table B-179 X Server Protocols - window properties
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ChangeProperty |
Change window property |
9120 |
xc |
0x20000000 |
|
AUE_DeleteProperty |
Delete window property |
9121 |
xc |
0x20000000 |
|
AUE_GetProperty |
Get window property |
9122 |
xp |
0x10000000 |
|
AUE_ListProperties |
List window properties |
9123 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token xproperty-token return-token |
||||
Table B-180 XGetAtomName, XInternAtom
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GetAtomName |
Get atom name |
9119 |
xs |
0x80000000 |
|
AUE_InternAtom |
Fetch atom |
9118 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xatom-token (atom string) return-token |
||||
Table B-181 XConvertSelection, XGetSelectionOwner, XSetSelectionOwner
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ConvertSelection |
Convert selection |
9126 |
xs |
0x80000000 |
|
AUE_GetSelectionOwner |
Get selection owner |
9125 |
xs |
0x80000000 |
|
AUE_SetSelectionOwner |
Set selection owner |
9124 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-182 XGrabButton
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GrabButton |
Grab window button |
9130 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token (grabbing window id) xwindow-token (current device focus) xcursor-token return-token |
||||
Table B-183 XGrabPointer, XUngrabPointer, XUngrabButton
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GrabPointer |
Grab pointer |
9128 |
xs |
0x80000000 |
|
AUE_UngrabButton |
Release window button |
9131 |
xs |
0x80000000 |
|
AUE_UngrabPointer |
Release pointer |
9129 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token (grabbing window id) xwindow-token (current device focus) xcursor-token return-token |
||||
Table B-184 XChangeActivePointerGrab
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ChangeActivePointerGrab |
Change active pointer grab |
9132 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xcursor-token return-token |
||||
Table B-185 XGrabKey, XUngrabKeyboard
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GrabKey |
Grab key |
9135 |
xs |
0x80000000 |
|
AUE_UngrabKeyboard |
Release keyboard |
9134 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token return-token |
||||
Table B-186 XGrabKeyboard, XUngrabKey
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GrabKeyboard |
Grab keyboard |
9133 |
xp |
0x10000000 |
|
AUE_UngrabKey |
Release key |
9135 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token return-token |
||||
Table B-187 XGrabServer, XUngrabServer
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GrabServer |
Grab the server |
9137 |
xa |
0x40000000 |
|
AUE_UngrabServer |
Release the server |
9138 |
xa |
0x40000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-188 XQueryPointer
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_QueryPointer |
Query pointer |
9139 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token (querying window id) xwindow-token (pointer's window id) return-token |
||||
Table B-189 XGetMotionEvents, XSendEvent
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GetMotionEvents |
Get motion events |
9140 |
xp |
0x10000000 |
|
AUE_SendEvent |
Send window event |
9127 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token return-token |
||||
Table B-190 XTranslateCoords, XWarpPointer
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_TranslateCoords |
Translate coordinates |
9141 |
xp |
0x10000000 |
|
AUE_WarpPointer |
Warp the pointer |
9142 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token (source window id) xwindow-token (destination window id) return-token |
||||
Table B-191 XGetInputFocus, XSetInputFocus
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GetInputFocus |
Get input focus |
9144 |
xs |
0x80000000 |
|
AUE_SetInputFocus |
Set input focus |
9143 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token return-token |
||||
Table B-192 XQueryKeymap
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_QueryKeymap |
Query keymap |
9145 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-193 XSetFontPath
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_SetFontPath |
Set font path |
9146 |
xa |
0x40000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token xfont-token return-token |
||||
Table B-194 XChangeGC
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ChangeGC |
Change graphical context |
9148 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xfont-token xpixmap-token xgc-token return-token |
||||
Table B-195 XCopyGC
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_CopyGC |
Copy graphical context |
9149 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xgc-token (source gc ID) xgc-token (destination gc ID) return-token |
||||
Table B-196 XFreeGC, XSetClipRectangles, XSetDashes
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_FreeGC |
Free graphical context |
9152 |
xc |
0x20000000 |
|
AUE_SetClipRectangles |
Set clip rectangles |
9151 |
xp |
0x10000000 |
|
AUE_SetDashes |
Set dashes |
9150 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xgc-token return-token |
||||
Table B-197 XClearArea
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ClearArea |
Clear area |
9153 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token return-token |
||||
Table B-198 XCopyArea, XCopyPlane
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_CopyArea |
Copy area |
9154 |
xs |
0x80000000 |
|
AUE_CopyPlane |
Copy plane |
9155 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xpixmap-token (source pixmap ID) xpixmap-token (destination pixmap ID) xgc-token return-token |
||||
Table B-199 XFillPolygon, XPolyArc, XPolyFillArc, XPolyFillRectangle, XPolyLine, XPolyPoint, XPolyRectangle, XPolySegment
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_FillPolygon |
Fill polygon |
9161 |
xp |
0x10000000 |
|
AUE_PolyArc |
Polyarc |
9160 |
xp |
0x10000000 |
|
AUE_PolyFillArc |
Fill polyarc |
9163 |
xp |
0x10000000 |
|
AUE_PolyFillRectangle |
Fill polyrectangle |
9162 |
xp |
0x10000000 |
|
AUE_PolyLine |
Polyline |
9157 |
xp |
0x10000000 |
|
AUE_PolyPoint |
Polypoint |
9156 |
xp |
0x10000000 |
|
AUE_PolyRectangle |
Polyrectangle |
9159 |
xs |
0x80000000 |
|
AUE_PolySegment |
Polysegment |
9158 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token xpixmap-token xgc-token return-token |
||||
Table B-200 XGetImage, XImageText8, XImageText16, XPolyText8, XPolyText16, XPutImage
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_GetImage |
Get image |
9165 |
xs |
0x80000000 |
|
AUE_ImageText8 |
Imagetext (8-bit) |
9168 |
xp |
0x10000000 |
|
AUE_ImageText16 |
Imagetext (16-bit) |
9169 |
xp |
0x10000000 |
|
AUE_PolyText8 |
Polytext (8-bit) |
9166 |
xp |
0x10000000 |
|
AUE_PolyText16 |
Polytext (16-bit) |
9167 |
xp |
0x10000000 |
|
AUE_PutImage |
Put image |
9164 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token xpixmap-token xgc-token return-token |
||||
Table B-201 XCreateColormap
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_CreateColormap |
Create colormap |
9170 |
xc |
0x20000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token return-token |
||||
Table B-202 XAllocColor, XAllocColorCells, XAllocColorPlanes, XAllocNamedColor, XFreeColors
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_AllocColor |
Allocate color |
9176 |
xc |
0x20000000 |
|
AUE_AllocColorCells |
Allocate color cells |
9178 |
|
|
|
AUE_AllocColorPlanes |
Allocate color planes |
9179 |
|
|
|
AUE_AllocNamedColor |
Allocate named color |
9177 |
|
|
|
AUE_FreeColors |
Free colors |
9180 |
|
|
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xcolormap-token return-token |
||||
Table B-203 XCopyColormapAndFree, XFreeColormap, XInstallColormap, XListInstalledColormap, XUninstallColormap
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_CopyColormapAndFree |
Copy and free colormap |
9172 |
xp |
0x10000000 |
|
AUE_FreeColormap |
Free colormap |
9171 |
xp |
0x10000000 |
|
AUE_InstallColormap |
Install colormap |
9173 |
xa |
0x40000000 |
|
AUE_ListInstalledColormap |
List installed colormap |
9175 |
xs |
0x80000000 |
|
AUE_UninstallColormap |
Uninstall colormap |
9174 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xcolormap-token return-token |
||||
Table B-204 XLookupColor, XQueryColors, XStoreColors, XStoreNamedColor
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_LookupColor |
Look up colors |
9184 |
xp |
0x10000000 |
|
AUE_QueryColors |
Query colors |
9183 |
xp |
0x10000000 |
|
AUE_StoreColors |
Store colors |
9181 |
xp |
0x10000000 |
|
AUE_StoreNamedColor |
Store named colors |
9182 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xcolormap-token return-token |
||||
Table B-205 XCreateCursor
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_CreateCursor |
Create cursor |
9185 |
xc |
0x20000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xpixmap-token (source pixmap ID) xpixmap-token (mask pixmap ID) xcursor-token return-token |
||||
Table B-206 XCreateGlyphCursor
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_CreateGlyphCursor |
Create glyph cursor |
9186 |
xc |
0x20000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xfont-token (source font ID) xfont-token (mask font ID) xcursor-token return-token |
||||
Table B-207 XFreeCursor, XRecolorCursor
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_FreeCursor |
Free cursor |
9187 |
xc |
0x20000000 |
|
AUE_RecolorCursor |
Recolor cursor |
9188 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xcursor-token return-token |
||||
Table B-208 XFreePixmap
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_FreePixmap |
Free pixmap |
9147 |
xc |
0x20000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xpixmap-token return-token |
||||
Table B-209 XBell, XChangeKeyboardControl, XChangeKeyboardMapping, XChangePointerControl
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_Bell |
Bell |
9193 |
xs |
0x80000000 |
|
AUE_ChangeKeyboardControl |
Change keyboard control |
9190 |
|
|
|
AUE_ChangeKeyboardMapping |
Change keyboard mapping |
9189 |
|
|
|
AUE_ChangePointerControl |
Change pointer control |
9192 |
|
|
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-210 XForceScreenSaver, XSetScreenSaver
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ForceScreenSaver |
Cover screen |
9199 |
xp |
0x10000000 |
|
AUE_SetScreenSaver |
Set screensaver |
9193 |
|
|
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-211 XSetCloseDownMode
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_SetCloseDownMode |
Set closedown mode |
9196 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-212 XChangeHosts, XKillClient, XSetAccessControl
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ChangeHosts |
Change hosts |
9194 |
xa |
0x40000000 |
|
AUE_KillClient |
Kill client |
9197 |
xc |
0x20000000 |
|
AUE_SetAccessControl |
Set access control |
9195 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-213 XRotateProperties
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_RotateProperties |
Rotate properties |
9198 |
xp |
0x10000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xwindow-token xproperty-token return-token |
||||
Table B-214 XSetModifierMapping, XSetPointerMapping
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_SetModifierMapping |
Set modifier mapping |
9201 |
xs |
0x80000000 |
|
AUE_SetPointerMapping |
Set pointer mapping |
9200 |
xs |
0x80000000 |
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
Table B-215 X Server Extensions
|
Event Name |
Message |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_XExtensions |
X extension protocols |
9202 |
xp |
|
|
Format: header-token subject-token newgroups-token slabel-token [priv-token] (if privilege used or required) xclient-token return-token |
||||
The AUE_XExtensions audit record format is used when auditing extensions to the X11 library, such as XTSOLMakeTPWindow.
User-Level Generated Audit Records
These audit records are created by programs that operate outside the kernel. The records are sorted alphabetically by program. The description of each record includes:
-
The name of the program
-
A man page reference (if appropriate)
-
The audit event number
-
The audit event name
-
The audit record structure
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_add_drv |
/usr/sbin/add_drv |
9018 |
as |
0x00020000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) text-token (driver name) text-token (base directory) text-token (class name) text-token (aliases) |
||||
Table B-217 Admin Editor Action - Modify System Files
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_te_modsysfiles |
trusted editor |
9322 |
ao |
0x00080000 |
|
Format:
header-token
path-token (filename)
text-token (changes)
host-token
return-token
subject-token
slabel-token
|
||||
Table B-218 allocate(1M) - device success
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_allocate_succ |
/usr/sbin/allocate |
6200 |
ao |
0x00080000 |
|
Format: header-token subject-token [slabel-token] (subject) newgroups-token exit-token |
||||
Table B-219 allocate(1M) - device failure
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_allocate_fail |
/usr/sbin/allocate |
6201 |
ao |
0x00080000 |
|
Format: header-token subject-token [slabel-token] (subject) newgroups-token exit-token |
||||
Table B-220 allocate(1M) - list devices success
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_listdevice_succ |
/usr/sbin/allocate |
6205 |
ao |
0x00080000 |
|
Format: header-token subject-token [slabel-token] (subject) newgroups-token exit-token |
||||
Table B-221 allocate(1M) - list devices failure
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_listdevice_fail |
/usr/sbin/allocate |
6206 |
ao |
0x00080000 |
|
Format: header-token subject-token [slabel-token] (subject) newgroups-token exit-token |
||||
Table B-222 at(1) - create atjob
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_at_create |
/usr/bin/at |
6144 |
ao |
0x00080000 |
|
Format: header-token subject-token return-token exec_args-token text-token (user name) text-token (job queue) |
||||
Table B-223 at(1) - delete atjob file (at or atrm)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_at_delete |
/usr/bin/at /usr/bin/atrm |
6145 |
ao |
0x00080000 |
|
Format: header-token subject-token return-token exec_args-token text-token (user name) text-token (job queue) |
||||
Table B-224 at(1) - permission
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_at_perm |
/usr/bin/at |
6146 |
ao |
0x00080000 |
|
Format: header-token subject-token [group-token] exit-token |
||||
Table B-225 auditd(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_audit |
/usr/sbin/audit |
9016 |
aa |
0x00040000 |
|
Format:
header-token
text-token ("new audit file" | "reread audit_control" | "terminate auditd" | "unknown option" >
return-token
subject-token
slabel-token
|
||||
Table B-226 auditwrite(3)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_auditwrite |
auditwrite() |
9015 |
aa |
0x00040000 |
|
Format: header-token text-token (error description) subject-token return-token |
||||
Table B-227 automountd(1M) - mismatch
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_automountd_mismatch |
/usr/lib/fs/autofs/automount |
9034 |
ao |
0x00080000 |
|
Format: header-token path-token (mount dir) slabel-token (auto* file slabel) slabel-token (remote host template slabel) text-token (remote host server) return-token |
||||
Table B-228 automountd(1M) - mount
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_automountd_mount |
/usr/lib/fs/autofs/automount |
9033 |
ao |
0x00080000 |
|
Format: header-token subject-token slabel-token (subject slabel) path-token (mount dir) return-token host-token (machine name) |
||||
Table B-229 chroot(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_chroot |
/usr/sbin/chroot |
9029 |
ao |
0x00080000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) path-token (new root directory) path-token (command to execute) |
||||
Table B-230 crontab(1) - crontab created
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_crontab_create |
/usr/bin/crontab |
6148 |
ao |
0x00080000 |
|
Format: header-token subject-token return-token exec_args-token text-token (user name) |
||||
Table B-231 crontab(1) - crontab deleted
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_crontab_delete |
/usr/bin/crontab |
6149 |
ao |
0x00080000 |
|
Format: header-token subject-token return-token exec_args-token text-token (user name) |
||||
Table B-232 crontab(1) - invoke atjob or crontab
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_cron_invoke |
/usr/bin/crontab |
6147 |
ao |
0x00080000 |
|
Format: header-token subject-token return-token exec_args-token text-token (user name) text-token (job type: cron or at) text-token (cron command or at job name) |
||||
Table B-233 crontab(1) - permission
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_crontab_perm |
/usr/bin/crontab |
6150 |
ao |
0x00080000 |
|
Format: header-token subject-token [group-token] exit-token |
||||
Table B-234 dbmgr
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_dm_add |
/opt/SUNWadm/2.3/bin/dbmgr |
9319 |
ao |
0x00080000 |
|
AUE_dm_del |
9320 |
|
|
|
|
AUE_dm_mod |
|
9321 |
|
|
|
Format:
header-token
text-token (database info)
text-token (database type)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-235 deallocate(1M) - device success
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_deallocate_succ |
/usr/sbin/deallocate |
6202 |
ao |
0x00080000 |
|
Format: header-token subject-token [slabel-token] (subject) newgroups-token exit-token |
||||
Table B-236 deallocate(1M) -- device failure
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_deallocate_fail |
/usr/sbin/deallocate |
6203 |
ao |
0x00080000 |
|
Format: header-token subject-token [slabel-token] (subject) newgroups-token exit-token |
||||
Table B-237 dispadmin(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_dispadmin |
/usr/sbin/dispadmin |
9025 |
as |
0x00020000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) text-token (scheduler class) path-token (input file) |
||||
Table B-238 dtfile(1) - copy and move
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_dtfile_copy |
/usr/dt/bin/dtfile |
9037 |
fm |
0x00000008 |
|
AUE_dtfile_move |
|
9038 |
|
|
|
Format: header-token return-token path-token (target path) slabel-token (slabel of target) path-token (source path) slabel-token (slabel of source) host-token |
||||
Table B-239 eeprom(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_eeprom |
/usr/sbin/eeprom |
9032 |
as |
0x00020000 |
|
Format: header-token return-token path-token (prom device) text-token (variable=old value) text-token (variable=new value) |
||||
Table B-240 fuser(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_fuser |
/usr/sbin/fuser |
9031 |
ao |
0x00080000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) path-token (file name) arg-token (1, "PID", process-id) |
||||
Table B-241 groupmgr
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_gm_add_grp |
/opt/SUNWadm/2.3/bin/groupmgr |
9307 |
ao |
0x00080000 |
|
AUE_gm_del_grp |
9308 |
ao |
0x00080000 |
|
|
AUE_gm_mod_grp |
|
9309 |
ao |
0x00080000 |
|
Format:
header-token
text-token (group info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-242 halt(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_halt_solaris |
/usr/sbin/halt |
6160 |
ss |
0x00010000 |
|
Format: header-token subject-token return-token |
||||
Table B-243 hostmgr
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_hm_add_host |
/opt/SUNWadm/2.3/bin/hostmgr |
9310 |
ao |
0x00080000 |
|
AUE_hm_del_host |
9311 |
|
|
|
|
AUE_hm_mod_host |
|
9312 |
|
|
|
AUE_hm_set_def |
|
9313 |
|
|
|
Format:
header-token
text-token (host info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-244 inetd(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_inetd_connect |
/usr/sbin/inetd |
6151 |
na |
0x00000400 |
|
Format: header-token subject-token text-token (service name) ip-address-token ip-port-token return-token |
||||
Table B-245 in.ftpd(1M) - ftp access
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_ftpd |
/usr/sbin/in.ftpd |
6165 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (error message, failure only) return-token |
||||
Table B-246 installf(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_installf |
/usr/sbin/installf |
9042 |
as |
0x00020000 |
|
Format: header-token return-token argument-token (package name) subject-token slabel-token |
||||
Table B-247 login(1) -- local
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_login |
/usr/bin/login |
6152 |
lo |
0x00001000 |
|
Format: header-token text-token text-token (message - success or failure) subject-token return-token |
||||
Table B-248 login(1) -- rlogin
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_rlogin |
/usr/bin/login |
6155 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (error message) return-token |
||||
Table B-249 login(1) -- telnet
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_telnet |
/usr/bin/login |
6154 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (error message) return-token |
||||
Table B-250 logout(1)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_logout |
/usr/bin/login |
6153 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token return-token |
||||
Table B-251 lpadmin(1M) - authorization
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_uauth |
/usr/lib/lpadmin |
9017 |
ao |
0x00080000 |
|
Format: header-token text-token (authorization used) return-token text-token (lpadmin command line) subject-token slabel-token host-token |
||||
Table B-252 lpsched(1M) - authorization
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_uauth |
/usr/lib/lpsched |
9017 |
ao |
0x00080000 |
|
Format:
header-token
text-token (" print without banners | print without labels |print a PostScript file")
return-token
text-token (hostname/jobnumber-filenumber)
slabel-token (label of print job)
subject-token
slabel-token
host-token
|
||||
Table B-253 lpsched(1M) - privilege
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_lp_cancel |
/usr/lib/lpsched |
9044 |
ao |
0x00080000 |
|
AUE_lp_status |
9045 |
|
|
|
|
Format: header-token return-token privilege-token text-token (hostname/jobnumber-filenumber) slabel-token (print job label) subject-token slabel-token host-token (error message) |
||||
Table B-254 modload(1M), modunload(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_modload |
/usr/sbin/modload |
9020 |
as |
0x00020000 |
|
AUE_modunload |
/usr/sbin/modunload |
9021 |
|
|
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) text-token (module pathname) |
||||
Table B-255 mountd(1M) - NFS mount
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_mountd_mount |
/usr/lib/nfs/mountd |
6156 |
na |
0x00000400 |
|
Format: header-token argument-token slabel-token (subject slabel) text-token (remote client hostname) path-token (mount dir) slabel-token (slabel of the directory) text-token (error message, failure only) attribute-token subject-token return-token |
||||
Table B-256 mountd(1M) - NFS unmount
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_mountd_umount |
/usr/lib/nfs/mountd |
6157 |
na |
0x00000400 |
|
Format: header-token slabel-token (subject slabel) text-token (remote client hostname) path-token (mount dir) slabel-token (slabel of the directory) text-token (error message, failure only) attribute-token subject-token return-token |
||||
Table B-257 passwd(1)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_passwoeoed |
/usr/bin/passwd |
6163 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (error message) return-token |
||||
Table B-258 pbind(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pbind |
/usr/sbin/pbind |
9026 |
as |
0x00020000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) text-token (action: "BIND" | "UNBIND") arg-token (1, "CPU", processor id) arg-token (2, "PID", process-id) |
||||
Table B-259 pfsh(1M)
|
Event Names |
Program |
Event IDs |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pfsh_trusted_priv AUE_pfsh_trusted_nopriv AUE_pfsh_priv |
/usr/bin/pfsh |
9007 9008 9009 |
ao |
0x00080000 |
|
AUE_pfsh_nopriv |
/usr/bin/pfsh |
9010 |
ap |
0x00004000 |
|
Format: header-token path-token (of the executable) exec_args-token path-token (of current directory) privilege-token return-token exec_env-token (if AUDIT_ARGE is on) subject-token slabel-token |
||||
Table B-260 pkgadd(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pkginstall |
/usr/sbin/pkgadd |
9040 |
as |
0x00020000 |
|
Format: header-token return-token argument-token (package name) subject-token slabel-token |
||||
Table B-261 pkgrm(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pkgremove |
/usr/sbin/pkgrm |
9041 |
as |
0x00020000 |
|
Format: header-token return-token argument-token (package name) subject-token slabel-token |
||||
Table B-262 printmgr
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pm_add_prn |
/opt/SUNWadm/2.3/bin/printmgr |
9316 |
ao |
0x00080000 |
|
AUE_pm_del_prn |
9318 |
ao |
0x00080000 |
|
|
AUE_pm_mod_prn |
|
9317 |
ao |
0x00080000 |
|
Format:
header-token
text-token (printer info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-263 profmgr - add profile
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pm_add_prof |
/opt/SUNWadm/2.3/bin/profmgr |
9306 |
ao |
0x00080000 |
|
Format:
header-token
text-token (new profile info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-264 profmgr - delete profile
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pm_del_prof |
/opt/SUNWadm/2.3/bin/profmgr |
9304 |
ao |
0x00080000 |
|
Format:
header-token
text-token (profile info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-265 profmgr - modify profile
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_pm_mod_prof |
/opt/SUNWadm/2.3/bin/profmgr |
9305 |
ao |
0x00080000 |
|
Format:
header-token
text-token (old profile info)
text-token (new profile info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-266 psradm(1m)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_psradm |
/usr/sbin/psradm |
9027 |
ps |
0x00100000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) text-token (action: "ON" | "OFF") arg-token (1, "PID", processor id) |
||||
Table B-267 reboot(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_reboot_solaris |
/usr/sbin/reboot |
6161 |
ss |
0x00010000 |
|
Format: header-token subject-token return-token |
||||
Table B-268 removef(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_removef |
/usr/sbin/removef |
9043 |
as |
0x00020000 |
|
Format: header-token return-token argument-token (package name) subject-token slabel-token |
||||
Table B-269 rpc.rexd(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_rexd |
/usr/sbin/rpc.rexd |
6164 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (error message, failure only) text-token (hostname) text-token (username) text-token (command to be executed) exit-token |
||||
Table B-270 in.rexecd(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_rexecd |
/usr/sbin/in.rexecd |
6162 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (error message, failure only) text-token (hostname) text-token (username) text-token (command to be executed) exit-token |
||||
Table B-271 in.rshd(1M) - rsh access
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_rshd |
/usr/sbin/in.rshd |
6158 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (command string) text-token (local user) text-token (remote user) return-token |
||||
Table B-272 rem_drv(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_rem_drv |
/usr/sbin/rem_drv |
9019 |
as |
0x00020000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) text-token (driver name) [text-token] (base directory) |
||||
Table B-273 init(1M) - run level change
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_run_level_change |
/usr/sbin/init |
9024 |
ss |
0x00010000 |
|
Format: header-token text-token (new run level) subject-token slabel-token (if slabel policy on) return-token |
||||
Table B-274 Selection Manager Transfer
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_sel_mgr_xfer |
|
9039 |
ax |
0x00002000 |
|
Format: header-token subject-token slabel-token return-token |
||||
Table B-275 sendmail(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_sendmail_deliver AUE_sendmail_defer |
/usr/lib/sendmail |
9013 9014 |
ao |
0x00080000 |
|
Format: header-token text-token (message about status) text-token (to) text-token (message ID) text-token (from) text-token (from host) text-token (to user) text-token (to host) return-token slabel-token |
||||
Table B-276 sendmail(1M) - upgrade
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_sendmail_upgrade |
/usr/lib/sendmail |
9012 |
ao |
0x00080000 |
|
Format: header-token text-token (message ID) slabel-token (old label) slabel-token (new label) subject-token slabel-token |
||||
Table B-277 serialmgr
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_sm_del_ser |
/opt/SUNWadm/2.3/bin/serialmgr |
9315 |
ao |
0x00080000 |
|
AUE_sm_mod_ser |
9314 |
|
|
|
|
Format:
header-token
text-token (port info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-278 setuname(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_setuname |
/usr/bin/setuname |
9022 |
as |
0x00020000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token(command-line arguments) text-token (action: "ADD" | "DELETE") path-token (swapname) |
||||
Table B-279 share(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_EXPORTFS |
/usr/lib/fs.d/nfs/share |
61 |
ao |
0x00080000 |
|
Format: header-token subject-token slabel-token (subject slabel) path-token (export directory) slabel-token (slabel of the directory) text-token (export options) return-token |
||||
Table B-280 Workspace SL Change
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_sl_change |
|
9035 |
ap |
0x00004000 |
|
Format: header-token subject-token slabel-token (original SL) slabel-token (new SL) return-token host-token |
||||
Table B-281 su(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_su |
/usr/bin/su |
6159 |
lo |
0x00001000 |
|
Format: header-token subject-token text-token (error message) return-token |
||||
Table B-282 swap(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_swap |
/usr/sbin/swap |
9030 |
as |
0x00020000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token text-token (new node name | "*none*") text-token (new systemname | "*none*") |
||||
Table B-283 uadmin(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_uadmin_cmd |
/usr/sbin/uadmin |
9023 |
ss |
0x00010000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) argument-token (1, "cmd", command code) argument-token (2, "fcn", function code) |
||||
Table B-284 uauth
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_uauth |
use of authorization |
9017 |
ao |
0x00080000 |
|
(See Table B-252 for use of authorization with printing) Format: header-token text-token (user name) text-token (authorization) subject-token return-token |
||||
Table B-285 usermgr
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_um_add_user |
/opt/SUNWadm/2.3/bin/usermgr |
9302 |
ao |
0x00080000 |
|
AUE_um_del_user |
9301 |
|
|
|
|
AUE_um_mod_user |
|
9300 |
|
|
|
AUE_um_set_def |
|
9303 |
|
|
|
Format:
header-token
text-token (user info)
text-token (error message)
return-token
subject-token
slabel-token
|
||||
Table B-286 uname(1)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_uname_set |
/usr/bin/uname |
9024 |
as |
0x00020000 |
|
Format: header-token subject-token groups-token slabel-token return-token exec_args-token (command-line arguments) text-token (new node name) |
||||
Table B-287 unshare(1M)
|
Event Name |
Program |
Event ID |
Event Class |
Mask |
|---|---|---|---|---|
|
AUE_exportfs |
/usr/lib/fs.d/nfs/share |
|
na |
0x00000400 |
|
Format: header-token subject-token slabel-token (subject slabel) path-token (export directory) return-token |
||||
- © 2010, Oracle Corporation and/or its affiliates
