Chapter 2 Accessing and Leaving the Trusted Solaris Environment
This chapter presents procedures necessary for accessing and leaving the Trusted Solaris environment.
The Login Process
Before you can get access to the environment, your Trusted Solaris 8 system administrator and security administrator must set up a user account for you. The account gives you permission to use some of the computer facilities and contains identifying information, such as the username assigned to you and your user ID (UID). The username in conjunction with your password lets you log into the system. The user ID identifies all of your transactions as well as the files and directories that you own.
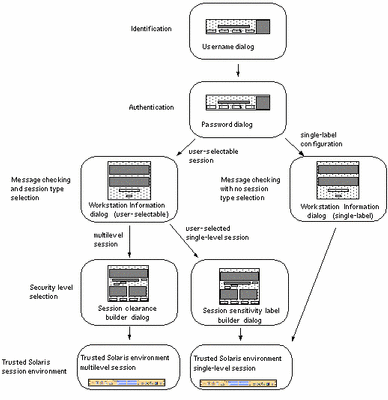
An overview of the login process is shown in Figure 2-1. The process is described in more detail in the material following the overview figure. The steps in the process include:
-
Identification - entering your username in the Username dialog box
-
Authentication - entering your password in the Password dialog box. A password is a private combination of keystrokes that validates your identity to the system. Since it is stored in an encrypted form, your password is not accessible by other users on the system. It is your responsibility to protect your password so that other users cannot use it to gain unauthorized access. Never write your password down or disclose it to anyone else, because a person with your password has access to all your data without being identifiable or accountable. Your initial password is supplied by your Trusted Solaris 8 administrator.
Successful completion of identification and authentication confirms your right to use the system.
-
Message checking and session type selection -The Workstation Information dialog box displays the message of the day, provides account access information (so that you can check for any possible security breaches), and lets you specify the type of session: single-level or multilevel.
Note -Your account may be configured such that you always operate at the same label (a single-label configuration). If this is the case, you will not be able to select the type of session in the Workstation Information dialog box or set a security level.
-
Security level selection - setting the highest security level at which you intend to operate while in your session.
Figure 2-1 The Trusted Solaris Environment Login Process
Identification
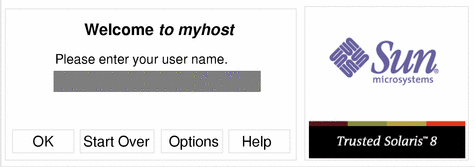
When a Trusted Solaris 8 workstation is not in a work session, it displays the login screen. The login screen initially contains the username dialog box, which enables the next user to enter his or her username (see Figure 2-2). This is the identification part of the login process.
To Identify Yourself to the System
-
You can log in remotely by selecting Remote Login from the Options menu in the username dialog box (see following figure) and selecting Enter Host Name or Choose Host From List; otherwise, go to the following step to log in locally.
A dialog box for direct host entry or a list dialog box is displayed. The host you specify must be running a compatible version of the Trusted Solaris environment. In either case, after host selection, another username dialog is displayed with the name of the remote host.
Figure 2-2 Username Dialog Box
-
Type your username in the text field in the username dialog box.
Be sure to type it exactly as your administrator assigned it to you with regard to spelling and upper and lower case.
-
Click the OK button (or press Enter) to confirm your entry of the username or select one of the other options if you are not ready to log in.
If you are not ready to log in, you can choose one of these options:
-
Click the Start Over button to re-enter your username.
-
Click Reset login in the Options menu to restart the windowing system.
-
Click Help to get information on using the login username dialog box.
 Caution -
Caution - You should never see the Trusted Stripe when the login screen appears. If you ever see the screen stripe while attempting to log in or unlock the screen, do not type your password because there's a chance you are being spoofed, that is, an intruder's program is masquerading as a login program to capture passwords.
-
Authentication
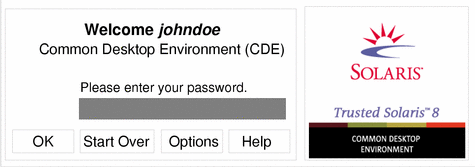
After you have entered the username, the username dialog box is replaced in the login screen by the password dialog box (see Figure 2-3). This part of the process is referred to as authentication, that is, authenticating that you are indeed the user authorized to use that username.
To Authenticate Yourself
-
Type your password in the password entry field.
For security purposes, the characters do not actually display in the field.
Figure 2-3 Password Dialog Box
-
Click the OK button (or press Enter) to confirm your entry of the password or select one of the other options if you are not ready to log in.
If you are ready to log in, click OK or press Enter. Otherwise. you have these options:
-
Click the Start Over button to re-enter your username.
-
Click Reset login in the Options menu to restart the windowing system.
-
Click Help to get information on using the login username dialog box
The system compares the entered login name and password against a list of authorized users. If you have entered your password incorrectly, a message dialog box appears displaying the message:
Login incorrect; please try again.
Click OK to dismiss the error dialog box and return to Step 1.
-
Message Checking and Session Type Selection
After you successfully enter your username and password, the Workstation Information dialog box is displayed. It provides status information and, if your account is configured for user-specified sessions, lets you a select a single- or multilevel session. If your account is set up for a single-label configuration, then there will be no option for selecting a session level.
Single-level Versus Multilevel Sessions
In a multilevel session, you can operate at different labels. The range in which you operate is bounded at the upper end by the session clearance you specify and at the lower end by the minimum label assigned to you by your administrator.
In a single-level session, you specify a session label at which you operate for the entire session. In a single-level session, you can access and write to files at that label only. You cannot change the label of workspaces in the session. Note that you can assume a role within a single-level session and then operate at any label available to that role.
Session Selection Example
Table 2-1 provides an example of the difference between a single- and multilevel session. It contrasts a user choosing to operate in a single-level session at SECRET A against the user selecting a multilevel session, also at SECRET A. Note that labels are shown in their long form inside square brackets ([]).
The three columns on the left show the user's session selections at login. Note that users set session labels for single-level sessions and session clearances for multilevel sessions. (This is a minor distinction that is taken care of by the system; the correct label builder dialog box is always displayed with the choices permitted.)
The two columns on the right show the label values available in the session. The Initial Workspace label column represents the label when the user first enters the Trusted Solaris environment. The Available Labels column lists the labels that the user is permitted to switch to in the session.
Table 2-1 How Session Selections Affect Session Values|
User Selections |
Session Label Values |
|||
|---|---|---|---|---|
|
Session Type |
Session Label |
Session Clearance |
Initial Workspace Label |
Available Labels |
|
single-level |
[S A] |
-- |
[S A] |
[S A] |
|
multilevel |
-- |
[S A] |
[C] |
[C], [C A], [S], [S A] |
In the first row of the table, the user has selected a single-level session with a session label of [S A]. In the Trusted Solaris environment, the user has an initial workspace label of [S A] which is also the only label at which the user can operate.
In the second row of the table, the user has selected a multilevel session with a session clearance of [S A]. The user's initial workspace label is set to [U], that is, a label of [UNCLASSIFIED], because that is the lowest possible label in the user's account label range. The user can switch to any label between [U], the minimum, and [S A], the session clearance.
To Check Messages and Select Session Type
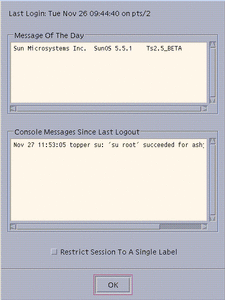
A typical Workstation Information dialog box appears in the following figure. Note that because this account is configured for multilevel operation, there is a toggle for restricting the session to a single level; single-level accounts do not get this option.
Figure 2-4 Workstation Information Dialog Box
-
Check the date and time of the last login.
This field indicates when your system was last used. You should always check that there is nothing suspicious about the last login, such as an unusual time of day, and report such occurrences to your security administrator.
-
Read any messages in the Message of the Day field.
This field contains messages from your administrator. Since this message may contain warnings about scheduled maintenance or security problems, you should always read it.
-
Read any console messages since last logout.
Typically, these system messages contain messages concerning cron (batch) jobs, but you should check that there are no messages indicating suspicious activity or other problems.
-
Click the session level toggle if you intend to work at only one label in your session (not available in single-label configurations).
In a single-level session, you operate at a single discrete label. You can only access and write to files at the same label. If you do not click the toggle, you are implicitly selecting a multilevel session and can view data at different labels. The range in which you can operate is bounded at the upper end by the session clearance that you select in the session clearance dialog box and at the lower end by the minimum label assigned to you by your administrator.
-
Click OK (or press Enter) to close the Workstation Information dialog box.
If your account is configured for single-label operation, the Trusted Solaris environment is displayed after the Workstation Information dialog box is closed; otherwise you will set the session level next.
Setting the Session Level
Note -
If your account is set up for a single-label configuration, the Trusted Solaris environment will be displayed after you close the Workstation Information dialog box and you have no need to read further in this section.
If you do not select Restrict Session to a Single Level, the Clearance Builder version of the Label Builder dialog box is displayed so that you can specify the session clearance (see Figure 2-5).
If you select Restrict Session to a Single Level, the user session label version of the Label Builder dialog box is displayed and you select the label for your entire session.
Note -
Workstations can be restricted to a limited range of session clearances and labels. For example, a workstation in a lobby might be limited to UNCLASSIFIED labels only. If the session clearance or label you enter is not accepted, check with an administrator to see if the workstation is restricted.
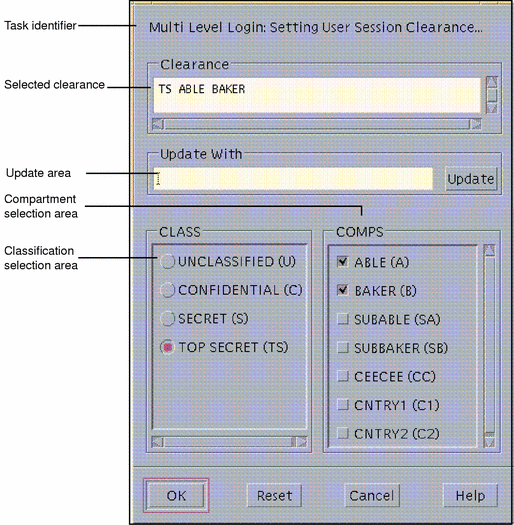
To Select a Clearance for a Multilevel Session
The session clearance sets the top boundary for labels of files that you will be able to access in the session. To set the clearance, you use the Clearance Builder dialog box (see Figure 2-5).
-
To use the default clearance in the Clearance field, click OK (or press Enter) and wait for the Trusted Solaris environment to be displayed.
For a different clearance, go to step 2 to build a new clearance.
-
Click the desired classification in the classification selection area.
-
Click the desired compartments (if any) in the compartments selection area.
-
Check the clearance you have built in the selected clearance field. Click OK or press Enter if it is correct or go back to step 2 to build a different clearance.
Figure 2-5 Session Clearance Builder Dialog Box
To Select a Label for a Single-level Session
The session label sets the label at which you intend to operate in this single-level session. To set the session label, you use the Single-Level Session Label Builder dialog box, which is similar to dialog box shown in Figure 2-5 except that the task identifier indicates a single-level session.
-
To use the default label in the Label field, click OK (or press Enter) and wait for the Trusted Solaris environment to be displayed.
For a different label, go to step 2 to build a new label.
-
Click the desired classification in the classification selection area.
-
Click the desired compartments (if any) in the compartments selection area.
-
Check the label you have built in the selected label field. Click OK or press Enter if it is correct or go back to step 2 to build a different label.
Related Access Procedures
This section provides other procedures related to accessing the Trusted Solaris environment, concerning:
-
Leaving the Trusted Solaris environment
-
Changing passwords
-
Enabling logins when logins are disabled
Leaving the Trusted Solaris Environment
If you leave your logged-on terminal unattended, you create a security risk. Make a habit of securing your terminal before leaving it; either lock the screen or log out. If you plan to return shortly, lock your screen. In most facilities, the screen times out after a specified period of idleness and automatically locks. If you expect to be gone for a while or you expect someone else to use your terminal, log out.
To Lock and Unlock Your Screen
-
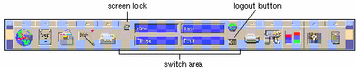
To lock your screen, click on the screen lock icon in the switch area of the front panel (see Figure 2-6).
Figure 2-6 Front Panel Switch Area
The screen turns black and the dialog box shown in Figure 2-7 is displayed.
Figure 2-7 Lock Screen Dialog Box
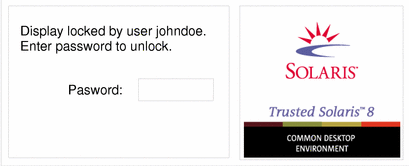
Note -The Trusted Stripe should not be displayed when the screen is locked. If it does appear, notify your security administrator immediately.
-
To unlock your screen, type your password in the password entry field and press Enter.
To Log Out of the Trusted Solaris Environment
-
Click on the EXIT icon in the switch area of the front panel (see Figure 2-6).
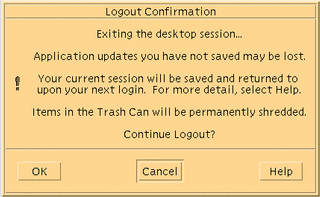
The confirmation dialog box shown in Figure 2-8 is displayed. It tells you to save application updates, reminds you that the current session will be saved, and warns you that any items in the Trash Can will be permanently shredded.
-
Click OK to continue the logout process.
Figure 2-8 Logout Confirmation Dialog Box
To Shut Down Your System (for authorized users only)
Logging out is the normal way to end a Trusted Solaris session. If you need to turn off your machine (and you are authorized for shutting down your system), you should use the Shut Down command and then turn off your power. If you do shut down your machine, it may require rebooting by an user with additional authorization depending on your security policy.
-
Select Shut Down from the Trusted Path menu.
This causes a confirmation dialog box to be displayed.
-
Select OK if you definitely want to shut down your system or Cancel if you want to reconsider.
Note -The keyboard combination Stop-A (L1-A) is not available in the Trusted Solaris environment unless specially configured by your security administrator.
Enabling Logins When Logins Are Disabled
As a security measure, your administrator can configure your site so that all logins are disabled after a reboot. If a reboot has occurred and you are not authorized to enable logins, the dialog box shown in Figure 2-9 appears; you must notify your Trusted Solaris 8 administrator to help you log in. If you are authorized to enable logins, the dialog box shown in Figure 2-10 appears.
Figure 2-9 Disabled Logins Dialog Box for Users Unauthorized to Enable Logins
Figure 2-10 Disabled Logins Dialog Box for Users Authorized to Enable Logins
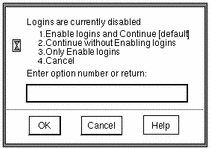
To Enable Logins After a Reboot
-
Enter the appropriate Enable logins option (see Figure 2-10):
-
Enter 1 to enable logins for all users and then log in, or 3 to enable logins for all users without logging in.
You should first check your site's security policy to ensure that enabling logins does not cause a security breach.
-
Enter 2 to leave other logins disabled and then log in, or 4 to leave other logins disabled and not log in.
Do this if you are not ready to enable logins.
-
-
Click OK to enable or leave disabled the logins as specified or click Cancel to leave logins in their current state.
Both options dismiss the dialog box and reset logins as specified.
Fixing a Bad Desktop Profile
If you have customized your shell initialization files (.cshrc, .login, etc.) and cannot log in, you can use the failsafe login feature to log in and correct the situation. In a standard login, the shell initialization files are sourced at startup to provide features customized for your environment. In a failsafe login, the default values are applied to your environment and no shell initialization files are sourced. This guarantees your ability to log in and permits you to fix any problems in shell initialization files.
To Perform a Failsafe Login
-
Type your username in the text field in the username dialog box (see Figure 2-2).
-
Click the Options button and choose Failsafe Session from the Session submenu.
-
Click the OK button (or press Enter) and perform the rest of the steps in a standard login.
-
Edit the shell initialization file(s) where you think the problem may be occurring.
- © 2010, Oracle Corporation and/or its affiliates
