How the Trusted Solaris Environment Controls Device Access
Since devices provide a means for the import and export of data to and from a Trusted Solaris system, they must be controlled to properly protect the data. (A device is either a physical peripheral that is connected to a Trusted Solaris system or a software-simulated device called a pseudo-device.) The Trusted Solaris environment lets you control data flowing through devices through device allocation and device label ranges.
Device Allocation
Device allocation provides a way to control data when it is imported and exported and prevents unauthorized users from access to the information. In a Trusted Solaris system the administrator decides which devices, if any, each user can use to import and export data and sets those devices to be allocatable. The administrator then assigns to selected users the Allocate Device authorization . The Configure Device Attributes, Delegate Device Administration, and Revoke or Claim Device authorizations are used to adminstrate devices. Users authorized to use a device must allocate the device before using it and deallocate the device when finished. Between the allocation and deallocation of a device, the user has exclusive use of it.
The device allocation applications are provided by the Solaris SunSHIELD Basic Security Module (BSM); refer to Chapter 4, "Device Allocation," in the SunSHIELD Basic Security Module Guide. The Trusted Solaris environment provides a graphical user interface on top of these commands called the Device Allocation Manager that enables device label ranges.
Device allocation provides a way to control the import and export of data. In the Trusted Solaris environment, the administrator decides which devices, if any, can be used to import and export data and includes the devices in the device_maps(4) file.
Users allocate devices through the Device Allocation Manager. The Device Allocation Manager mounts the device, runs a clean script to prepare the device and performs the allocation. When finished, the user deallocates the device through the Device Allocation Manager, which runs another clean script and unmounts and deallocates the device.
Device Label Ranges
To prevent users from copying off sensitive information, each allocatable device has an associated label range that is assigned by an administrator. To use an allocatable device, the user must be currently operating at a label within the device's label range; if not, allocation is denied. The user's current label is applied to data imported or exported while the device is allocated to the user. The label of exported data is displayed when the device is deallocated so that the user can physically label the medium containing the exported data.
Examples of devices that have label ranges are frame buffers, tape drives, diskette and CD-ROM drives, printers, and network interfaces.
Administering Devices through the Device Allocation Manager
The Device Allocation Manager is accessed from the Tools subpanel above the Style Manager in the Front Panel. The Device Allocation Manager is available to users with the Allocate Device authorization for allocation and deallocation only. Normal users cannot see if a device is currently allocated to another user and cannot perform maintenance through the Device Administration button in the Device Allocation Manager, which is available to authorized users and administrators only. The Device Allocation Manager is shown in the following figure.
Figure 1-7 Device Allocation Administration Dialog Boxes
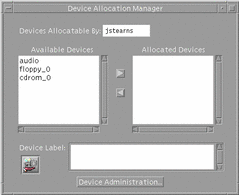
Device Administration Dialog Box
Clicking the Device Administration button in the Device Allocation Manager main window causes the Device Administration dialog box to be displayed (see following figure). The Device Administration dialog box lets you select a device. Its state is then displayed. The buttons in the upper right of the dialog box let you perform operations on the selected device. Clicking the Revoke button moves the selected device from a busy (allocated) state to an available (deallocated) state. Clicking the Reclaim button lets you make available a device that is currently in an error state. The revoke or reclaim device authorization is required to use these buttons. Clicking the Delete button makes a device unavailable. Clicking the New or Configure buttons displays the Device Allocation Configuration dialog box.
Figure 1-8 Device Administration Dialog Box
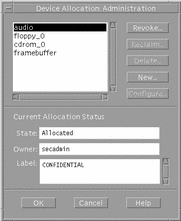
Device Allocation Configuration Dialog Box
To use the Device Allocation Configuration dialog box requires the configure device attributes authorization. Clicking the Configuration button in the Device Allocation Maintenance dialog box causes the Device Allocation Configuration dialog box to be displayed (see following figure).
Figure 1-9 Device Allocation Configuration Dialog Box
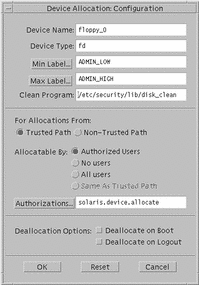
The Device Allocation Configuration dialog box is divided into three parts:
-
Device security attributes--includes device name and type, minimum and maximum labels, clean program, and device map.
-
Allocation specifications--from Trusted Path or non-Trusted Path (for command line users), authorized users (with the authorizations specified in the Authorizations field), no users (if device is not allocatable), all users (if no authorizations required), and which authorizations to require for device allocation
-
Deallocation options--deallocate any allocated devices on reboot and deallocate any allocated devices on logout
Device Allocation Authorizations Dialog Box
If you click the Authorizations button in the Device Allocation Configuration dialog box, the Device Allocation Authorizations dialog box is displayed (see following figure). It lets you specify the authorizations required for using the device.
Figure 1-10 Device Allocation Authorizations Dialog Box
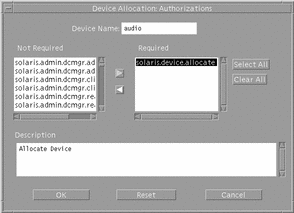
Device Allocation Databases and Commands
If you do not have access to the Device Allocation Manager, you can use the commands below to administer allocatable devices. The commands use the device databases: device_allocate(4), device_deallocate(4), and device_maps(4) . Note that the commands are not intended for non-administrative users.
-
add_allocatable(1M)--adds devices to the allocation databases.
-
allocate(1M)--manages the ownership of devices through its allocation mechanism. It ensures that each device is used by only one qualified user at a time.
-
deallocate(1M)--deallocates a device allocated to the evoking user.
-
list_devices(1M)--lists the allocatable devices in the system according to specified qualifications.
-
dminfo(1M)--displays information about device entries in the device maps file.
Device Clean Scripts
Device clean scripts are special scripts that are run when a device is first allocated. Clean scripts address two security concerns:
-
Object reuse - the requirement that a device is clean of previous data before being allocated or reallocated
-
Media labeling - the requirement that removable information storage media have a physical label indicating its label. While the ultimate responsibility for putting the labels on the removable media rests with the user, the device clean scripts can prompt the user to do so.
The name of a device clean script for a specific device is stored with that device's entry in the device_allocate(4), file. The operations of each device clean program are specific to each device. The following is a list of tasks that a device clean program performs:
-
Eject media - Devices that store information on removable media must be forced to eject that media upon deallocation or reallocation of the device, to prevent passing information to the next user of the device who may be at a different label.
-
Reset device state - Devices that keep state information can potentially be used as a covert channel by the users. Thus driver status information must be reset to default values during deallocation of the device.
-
Remind user about media labeling - It is a requirement that removable information storage media be labeled with appropriate external media labels. The device user's label is passed to the device clean program when it is invoked (Seedevice_clean(1M) man page for interface detail.)
Not all allocatable devices require a device clean program. Devices that do not keep states and do not use removable media do not need a device clean program.
Device clean programs for tape, floppy disk, CD-ROM, and audio devices are provided by the Trusted Solaris environment. The configurable nature of the user device allocation mechanism lets an administrator install new devices and configure device clean programs accordingly.
Device Allocation Security Policy
For more information on device allocation, see Chapter 15, "Managing Devices," in Trusted Solaris Administrator's Procedures.
- © 2010, Oracle Corporation and/or its affiliates
