Understanding Rights Profiles
Trusted applications and authorizations can be grouped into packages called rights profiles for assignment to user or role accounts. The main purpose of a rights profile is to provide limited override power to a user or role who needs this capability.
The potential contents of a rights profile are:
-
CDE actions with or without real and effective UIDs and GIDs, privileges, process labels, and clearances
-
Commands with or without real and effective UIDs and GIDs, privileges, process labels, and clearances
Assigning Rights Profiles to Users or Roles
To assign rights profiles to users, you open the User Properties dialog box from the User Tool in the Solaris Management Console and select the Rights tab, as shown in the following figure. The rights profiles not assigned to the current user or role are displayed in the Excluded column on the left and must be moved to the right column for assignment to the current account. For more information, see the online help. In similar fashion, you can make changes to roles through the Administrative Roles dialog box in the User Tool.
Figure 1-2 Assigning Rights Profiles to Users

Predefined Trusted Solaris Rights Profiles
The Trusted Solaris environment provides a set of predefined rights profiles (see the following table). Before you assign any of these rights profiles, you should familiarize yourself with their contents. To view the contents of predefined rights profiles, use the -list option in the smprofile command (see next section) or the Rights dialog box. The profiles can be modified according to the needs of your organization.
Table 1-2 Rights Profile Descriptions|
Rights Profile |
Purpose |
|---|---|
|
Provides access to all executables but without privileges. |
|
|
All Actions |
Provides access to all actions but without privileges. |
|
Provides all authorizations. For testing. |
|
|
All Commands |
Provides access to all commands but without privileges. |
|
For managing the audit subsystem but without ability to read files. |
|
|
For reading the audit trail. |
|
|
Provides access to the applications on the Front Panel with the necessary privileges. |
|
|
Provides access to rudimentary commands necessary for all roles. |
|
|
Basic Solaris User |
Assigned to all users of the Solaris Management Console. Provides Read permissions and lets users add con jobs to their crontab files. Contains All rights profile. |
|
Provides authorizations for normal users. |
|
|
For managing cron and at jobs. |
|
|
This is an empty right for adding security attributes to the default Admin role. |
|
|
This is an empty right for adding security attributes to the default Oper role. |
|
|
This is an empty right for adding security attributes to the default Root role. |
|
|
This is an empty right for adding security attributes to the default Secadmin role. |
|
|
Custom SSP |
This is an empty right for adding security attributes to the default SSP role for Sun Enterprose 10000 administration. |
|
Device Management |
For allocating and deallocating devices, and correcting error conditions. |
|
For managing and configuring devices. |
|
|
Provides the authorization for allowing yourself and other users to log in after boot. |
|
|
For managing file systems. |
|
|
For managing file system labels and other security attributes. |
|
|
Information Security |
For setting access control policy. |
|
For configuring sendmail, modifying aliases, and checking mail queues. |
|
|
Provides commands needed to maintain or repair a system. |
|
|
Backup files. |
|
|
Restore files from backup. |
|
|
Name Service Management |
Grants right to control the name service daemon. |
|
Name Service Security |
Grants right to control the name service properties and table data. |
|
For managing the host and network configuration. |
|
|
Network Security |
For managing network and host security, with authorizations for modifying trusted network databases. |
|
For changing ownership and permissions on files. |
|
|
For changing labels of files and setting up system-wide labels. |
|
|
For changing privileges on executable files. |
|
|
Operate outside system accreditation range. |
|
|
Primary Adminstrator |
Contains subordinate rights profiles for primary administrator role. |
|
For developers to run Bourne, Korn, and C shells with all privileges. NOT intended for secure environments. |
|
|
For managing current processes, including cron and at jobs. |
|
| Remote Administration | Remote administration of headless systems. |
|
Rights Delegation |
Lets user or role assign rights assigned to that user or role to other users or roles. Lets user assign roles assigned to that user to other users. |
|
Rights Security |
For managing assignment of rights profiles, labels, and privileges, and for setting account security. |
|
Software Installation |
For adding application software to the system. |
| SSP Administration | Tools for administering the SSP. |
| SSP Installation | Tools for installing the SSP. |
|
System Administrator |
Contains subordinate rights profiles for system administrator role. |
|
For creating and modifying users but without the ability to modify self (as a security measure). |
|
|
For creating and modifying users' security attributes but without the ability to modify self (as a security measure). |
Displaying Rights Profile Information
Use the -list option in the smprofile command to obtain various rights profile information. This command lets you display the contents of any profile for all users or specified user(s) and optionally the contents of the profiles. Another option for displaying rights profile information is profiles(1).
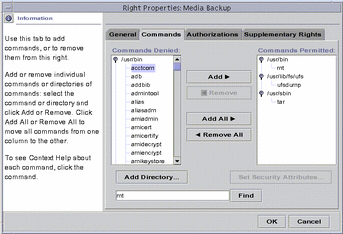
Customizing Rights Profiles
If the predefined rights profiles as they are shipped are not appropriate for your organization, they can be modified by the security administrator (or other role with equivalent powers). The Rights dialog box is used to edit the contents of rights profiles (see figure below). The Rights dialog box is accessed from the User Tool in the Solaris Management Console. For more information, see the online help.
Figure 1-3 Rights Dialog Box
- © 2010, Oracle Corporation and/or its affiliates
