Routing through Non-Trusted Solaris Gateway Clusters
It is possible to route secure data through clusters containing non-Trusted Solaris gateways. This procedure is called tunneling. For our purposes, a cluster is a contiguous set of either Trusted Solaris hosts and gateways only, or non-Trusted Solaris hosts and gateways only. An edge gateway is a gateway (Trusted Solaris or non-Trusted Solaris) that connects a cluster to a cluster of the other type.
The following figure shows an example of tunneling. The shaded rectangles represent non-Trusted Solaris gateways. The loops with thick lines indicate clusters. Cluster #1 is a non-Trusted Solaris cluster; cluster #2 is a Trusted Solaris cluster.
Figure 3-5 Tunneling Example
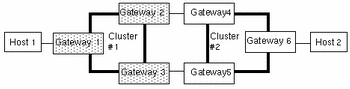
To transmit data from host #1 to host #2 requires a route through cluster #1, a non-Trusted Solaris cluster, and cluster #2, a Trusted Solaris cluster. This is permitted under these two conditions only:
-
All the gateways in the non-Trusted Solaris cluster (in the example, gateways #1, #2, and #3) must have the same security attributes. At start-up, each gateway must have a local file called /etc/security/tsol/tunnel containing the addresses of target hosts with which it can connect.
-
If there is more than one possible route and the routes enter the non-Trusted Solaris cluster through the same edge gateway and can exit from the cluster through different edge gateways, then the emetrics for these routes must be the same. For example, assume that gateway #4 has an SL range of CONFIDENTIAL to SECRET and gateway #5 has a broader range of ADMIN_LOW to ADMIN_HIGH. Because gateway #1 is a non-Trusted Solaris host, it uses a standard routing table without security attributes and would be unable to distinguish between the route through gateway #4 and the route through gateway #5.
- © 2010, Oracle Corporation and/or its affiliates
