System Accreditation Range
The system accreditation range always includes administrative labels ADMIN_HIGH and ADMIN_LOW. The system accreditation range also includes all the well-formed labels that can be made up out of all label components
defined in the label_encodings file.
Administrative role accounts are usually the only accounts configured to be able to work at all of the labels within the system accreditation range. An organization may also set up normal user (non-role accounts) to be able to perform a task that can only be done at one of the administrative labels ADMIN_HIGH or ADMIN_LOW. A good example in the default Trusted Solaris system is the install user account that is used for configuring the system after installation. The install account needs to log in at ADMIN_LOW because the site's label_encodings file is not yet installed, and therefore the site's non-administrative labels are not yet defined.
The following figure presents an example of how rules can constrain the labels permitted in a system accreditation range.
Figure 1-2 How System Accreditation Range Is Constrained By Rules
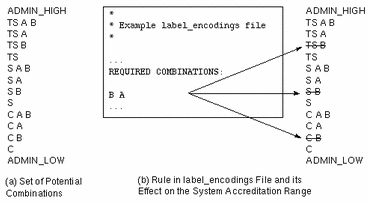
Figure 1-2 (a) shows all potential combinations given the classifications, TS (TOP SECRET), S (SECRET), and C (CONFIDENTIAL), and the compartments, A and B.
Figure 1-2 (b) shows a typical rule from the REQUIRED COMBINATIONS subsection of the SENSITIVITY LABELS section and its effects. The arrows point to the labels disqualified by the rule, which appear with lines through them. The REQUIRED COMBINATIONS syntax B A means that any label that has B as a compartment must also contain A. (Note that the converse is not true; compartment A is not required to be combined with any other compartments.) Since compartment B is only permitted when A is also present, the labels TS B, S B, and C B are not well-formed and hence are not in the system accreditation range.
- © 2010, Oracle Corporation and/or its affiliates
