Chapter 3 Preparing for SSP 3.3 Installation
This chapter covers installing and configuring the Trusted Solaris 8 operating environment on the Sun Enterprise 10000 SSP, and doing other tasks in preparation for installing the Trusted Solaris SSP 3.3 on the SSP.
The procedures in this guide use the conventions shown in the following table for command line prompts.
Table 3–1 Command Line Prompt Conventions| Prompt | User Indicated |
|---|---|
| ssp$ | admin role on the SSP |
| ssp% | ssp user on the SSP |
|
$ |
admin role on a system other than the SSP |
| # | root role or superuser on a system other than the SSP |
Getting Started
This section describes how to begin the installation or upgrade process.
-
If you do not know the current version of your SSP software, determine which version of the SSP software you are running.
For details, see To Determine Your Current SSP Version. You can also use this procedure after installation to verify that SSP 3.3 is running.
-
Obtain the SSP software from the Software Supplement for the Trusted SolarisTM 8 Operating Environment CD-ROM. For details, see Preparing to Install from a CD-ROM.
-
Create a backup file of your SSP environment.
If you are currently running SSP software, you can create a backup file of the SSP environment (the data contained in the /var/opt/SUNWssp directory) using the ssp_backup command. This command creates a backup file named ssp_backup.cpio in a directory that you specify. For dual SSP configurations, you use this backup file to restore the SSP environment on the appropriate SSP. This backup file can also be used to restore the SSP environment if you need to revert from SSP 3.3 to a previous version of SSP.
To Determine Your Current SSP Version
Go to the main SSP.
If you are running a Solaris SSP, log in as superuser. If you are running a Trusted Solaris SSP, log in as a user who can assume the system administrator role (hereafter called the admin role) and assume it.
Type:
ssp$ pkginfo -l SUNWsspr |
Look for the VERSION line, for example:
VERSION: 3.3.0,REV=2000.02.01.19.51
To Create an SSP Backup File
Backing up an existing SSP is required if you want to retain the current SSP environment. The backup file must be created with the ssp_backup command on a Solaris SSP 3.2 or SSP 3.3 system; an SSP 3.0, 3.1, or 3.1.1 backup file can not be restored to Trusted Solaris SSP 3.3. If you have a new system or you do not wish to restore the SSP environment after Trusted Solaris installation, you do not need to create a backup file.
Note –
The size of the SSP backup file can vary depending upon the contents of the subdirectories in the /var/opt/SUNWssp/ directory. You can use the du(1M) command to determine the approximate amount of disk space required for the backup file.
-
Depending on your environment, do one of the following procedures:
-
OPTION 1: If you are on a main Solaris SSP:
-
Log in as superuser.
-
Create a backup directory.
# mkdir target_directory
-
Back up the SSP environment on the Solaris SSP by typing:
# ./ssp_backup target_directory
-
-
OPTION 2: If you are on a main Trusted Solaris SSP:
-
Log in as as a user who can assume the root role and assume it.
-
Create a backup directory.
ssp# mkdir target_directory
-
Back up the SSP environment on the Trusted Solaris SSP by typing:
ssp# /opt/SUNWssp/bin/ssp_backup target_directory
-
A backup file named ssp_backup.cpio is created in target_directory. You may want to rename this file. After you have run ssp_backup, do not make any changes to the Sun Enterprise 10000 environment, such as domain state or power status of boards, until you have completed the installation and restored the SSP environment.
-
SSP 3.3 Hardware and Software Requirements
The following table describes the minimum requirements for running SSP 3.3.
Table 3–2 SSP 3.3 Requirements|
Item |
Description |
|---|---|
|
SSP new installation |
Trusted Solaris 8 operating environment. |
|
|
Configure SSP network files before installing SSP 3.3, as described in Configuring the SSP Network. |
|
Hardware |
SPARCstationTM 5, Sun UltraTM 5, or Sun Enterprise 250 workstation. |
|
|
If you plan to use more than eight domains (SSP 3.3 supports up to 16 domains), the SSP must be a Sun Ultra 5 or Sun Enterprise 250 workstation. The SPARCstation 5 supports up to eight domains only. |
|
Disk space |
Minimum 2.1 Gbytes for the Solaris operating environment and SSP 3.3 software (refer to FIN number I0527-1) |
|
Processor speed |
Minimum 170 MHz |
|
Memory |
Minimum 256 Mbytes |
|
Swap space |
Minimum 512 Mbytes, plus 148 Mbytes for running the Solaris Management Console |
About Main and Spare SSP Configurations
You can set up a dual SSP configuration that consists of a main and spare SSP. The spare SSP serves as a backup if the main SSP fails. For instructions on switching between the main and spare SSP, see the Sun Enterprise 10000 SSP 3.3 User Guide.
If you plan to use the new features offered in SSP 3.3, it is recommended that both the main and spare be version 3.3 in order to maintain failover compatibility. If you plan to install only one SSP for verification purposes, install the main SSP but do not implement the new features introduced in SSP 3.3. This will allow the spare SSP to continue to serve as a backup to the main SSP. When you are satisfied with the base release of SSP 3.3, upgrade the spare SSP, then begin using the new SSP 3.3 features.
Installing Trusted Solaris 8
Trusted Solaris SSP 3.3 installs on a Trusted Solaris 8 operating environment.
To Install Trusted Solaris 8 on the SSP
Install the Trusted Solaris 8 operating environment on the SSP as you would on a name service (NIS+ or NIS) client.
See Trusted Solaris Installation and Configuration Guide for details.
To Enable the System Administrator to Install SSP 3.3 and AP 2.3
-
Log in as a user who can assume the role secadmin and assume it.
-
Add the rights profile “SSP Installation” to the admin role. Optionally, add the “Host Alternate Pathing” profile.
-
Invoke the Solaris Management Console toolbox where the admin role is defined for your site.
See “To Select a Toolbox of the Appropriate Scope” in Trusted Solaris Installation and Configuration if you need help in choosing the correct toolbox.
-
Double-click the Trusted Solaris Management node in the Navigation pane.
-
Double-click the Users tool and enter the secadmin role password.
-
Double-click the Administrative Roles tool.
-
Double-click the admin role.
-
Click the Rights tab.
-
Follow the online help to add the existing profile, “SSP Installation”, to the role's rights before the System Administrator profile.
-
If you are going to install Alternate Pathing, add the “Host Alternate Pathing” profile after the SSP Installation profile and before the System Administrator profile.
-
-
Save your changes.
Configuring the SSP Network
After installing the Trusted Solaris operating environment on the SSP, you need to configure its SSP network files before installing the Trusted Solaris SSP 3.3 software.
Note –
Configuring the network is very important. Complete it before installing the SSP 3.3 software.
This section describes the following SSP network configurations:
Two Subnets
The following table and figure describe the two-subnet network configuration.
Table 3–3 Two-Subnet Network Configuration| Subnet | Name | Description |
|---|---|---|
| Primary | Domain Subnet or dom_subnet | SSP and the domains |
| Second | Control Board Subnet or cb0_subnet | SSP and the control board |
Figure 3–1 Two-Subnet Network Configuration
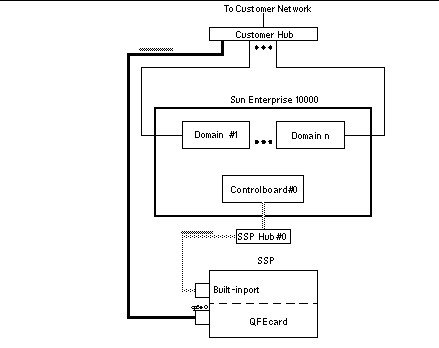
In Figure 3–1, the Built-in port is le0 for a SparcstationTM 5 and hme0 for a Sun UltraTM 5 and a Sun Enterprise 250 system.
Three Subnets
The following table and figure describe the three-subnet network configuration.
Table 3–4 Three-Subnet Network Configuration| Subnet | Name | Description |
|---|---|---|
| Primary | Domain Subnet or dom_subnet | SSP and the domains |
| Second | Control Board Subnet 0 or cb0_subnet | SSP and the first control board |
| Third | Control Board Subnet 1 or cb1_subnet | SSP and the second control board |
Figure 3–2 Three-Subnet Network Configuration
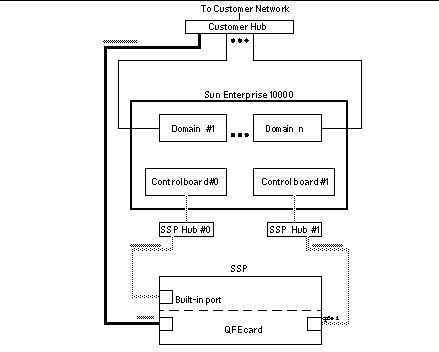
In Figure 3–2, the Built-in port is le0 for a Sparcstation 5 and hme0 for a Sun Ultra 5 and a Sun Enterprise 250 system.
Spare SSP
The following table and figure describe the spare SSP network configuration.
Table 3–5 Spare SSP Network Configuration| Subnet | Name | Description |
|---|---|---|
| Primary | Domain Subnet or dom_subnet | Both SSPs and the domains |
| Second | Control Board Subnet 0 or cb0_subnet | Both SSPs and the first control board |
| Third | Control Board Subnet 1 or cb1_subnet | Both SSPs and the second control board |
Figure 3–3 Spare SSP Network Configuration
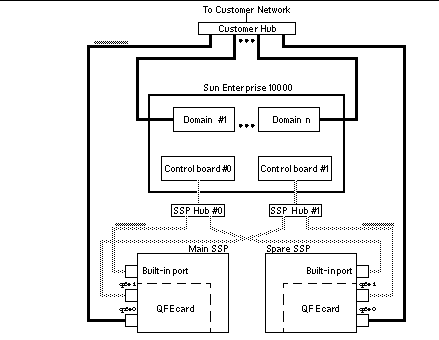
In Figure 3–3, the Built-in port on the main SSP and the spare SSP is le0 for a Sparcstation 5 and hme0 for a Sun Ultra 5 and a Sun Enterprise 250 system.
To Configure Your SSP Network
This procedure provides instructions for configuring your SSP network in one of the three configurations discussed earlier in this chapter.
-
Log in to the SSP as a user who can assume the root role and assume it.
Do the following steps in the role root at label
admin_low. -
Using the Admin Editor action from the System_Admin folder in the Application Manager, create the /etc/hostname.* configuration files.
If you need to view your network controllers, use ifconfig -a.
For example, if you are using a QuadFastEthernetTM (QFE) card, model 1049A, in the two-subnet, three-subnet, or spare SSP network configuration on a Sun Ultra 5, you need the following files:
-
/etc/hostname.qfe0 — contains the current SSP host name; it configures the primary subnet, dom_subnet.
-
/etc/hostname.hme0 — contains ssp_hostname-hme0; it configures the second subnet, cb0_subnet.
-
/etc/hostname.qfe1 — contains ssp_hostname-qfe1; it configures the third subnet, cb1_subnet.
Example 3–1 SSP with hostname xf4–ssp
File Name File Contents /etc/hostname.qfe0 xf4-ssp /etc/hostname.hme0 xf4-ssp-hme0 /etc/hostname.qfe1 xfe-ssp-qfe1
-
-
Set the contents of the defaultrouter file to the IP address of the primary network interface:
ssp# echo primary_network_IP_address > /etc/defaultrouter
-
Manually update your name service hosts registry to include the host names and IP addresses of your control board(s) and other hosts, such as domains and the SSP.
This can involve updating the Network Information Service (NIS or NIS+), or the /etc/hosts file, or the Domain Name Service (DNS).
The following example shows the typical modifications for an /etc/hosts file:
# Internet host table 127.0.0.1 localhost 0.0.0.0 tsol_default # Entries for dom_subnet. www.xxx.yyy.zzz domain1_hostname www.xxx.yyy.zzz domain2_hostname ... www.xxx.yyy.zzz domainn_hostnname(n is the number of domains) # # Entries on both ssp's. # NOTE : On the spare SSP, make sure “loghost” # belongs to the spare. # www.xxx.yyy.zzz main_ssp_hostname loghost www.xxx.yyy.zzz spare_ssp_hostname # # The next three entries need to be on cb0_subnet. # www.xxx.yyy.zzz main_ssp_hostname-hme0 www.xxx.yyy.zzz spare_ssp_hostname-hme0 www.xxx.yyy.zzz cb0_hostname # # The next three entries need to be on cb1_subnet. # www.xxx.yyy.zzz main_ssp_hostname-qfe1 www.xxx.yyy.zzz spare_ssp_hostname-qfe1 www.xxx.yyy.zzz cb1_hostname
Here is an example of a main SSP's /etc/hosts file. In this example, the SSP is configured as follows:
-
xf4 and xf4-b3 are host domains.
-
xf4-ssp is the main SSP and xf4-ssp1 is the spare SSP.
-
xf4-cb0 and xf4-cb1 are the host names for the two control boards.
#/etc/hosts # 127.0.0.1 localhost 0.0.0.0 tsol_default #dom_subnet (www.xxx.49.zzz). The 49 subnet # 129.153.49.8 xf4 129.153.49.9 xf4-b3 129.153.49.113 xf4-ssp loghost 129.153.49.114 xf4-ssp1 # #cb0_subnet (www.xxx.151.zzz). The 151 subnet # 129.153.3.113 xf4-ssp-hme0 129.153.3.114 xf4-ssp1-hme0 129.153.3.123 xf4-cb0 # #cb1_subnet (www.xxx.152.zzz). The 152 subnet # 129.153.152.113 xf4-ssp-qfe1 129.153.152.114 xf4-ssp1-qfe1 129.153.152.127 xf4-cb1
The /etc/hosts file is a link to the /etc/inet/hosts file.
Note –The SSP and the host domains must be on the same subnet so you can boot domains from the network.
-
-
Manually update your name service ethers registry to include the Ethernet addresses for the domain(s), SSP(s), and control board(s).
You need to update a NIS+ table, a NIS map, or the /etc/ethers file. For example:
08:00:20:ac:5b:ba xf4-ssp 08:00:20:b0:64:78 xf4-ssp1 00:00:be:a6:55:88 xf4 00:00:be:a6:6f:89 xf4-b3 00.00.be.01.00.1e xf4-cb0 00.00.be.01.00.57 xf4-cb1
Note –The Ethernet address of the control board(s) is located on the front of each control board.
-
Update the tnrhdb(4) file to indicate the template for the SSP(s), domain(s), control board(s) and interface(s).
Follow the procedure outlined in Trusted Solaris Installation and Configuration Guide. For example, if the E10000 is configured as follows:
Example 3–2 Tnrhdb Information for SSP xf4-ssp (129.153.49.113)
Main SSP
xf4-ssp (129.153.49.113)Is running the Trusted Solaris 8 operating environment.
Interfaces xf4-ssp-hme0 (129.153.3.113)
xf4-ssp-qfe1 (129.153.152.113)
Spare SSP
xf4-ssp1 (129.153.49.114)Is running the Trusted Solaris 8 operating environment.
Interfaces
xf4-ssp1-hme0 (129.153.3.114)
xf4-ssp1-qfe1 (129.153.152.114)
Domain1
xf4 (129.153.49.8)Is running the Trusted Solaris 8 operating environment.
Domain2
xf4-b3 (129.153.49.9)Is running the Solaris 8 operating environment.
Control boards
xf4-cb0 (129.153.3.123)
xf4-cb1 (129.153.152.127)
-
The tnrhdb entries for SSP xf4–ssp (129.153.49.113) are:
# /etc/security/tsol/tnrhdb # # Assume that templates confidential and tsol are defined in the tnrhtp database. # 127.0.0.1:tsol 0.0.0.0:confidential 129.153.49.113:tsol 129.153.3.113:tsol 129.153.152.113:tsol 129.153.49.114:tsol 129.153.3.114:tsol 129.153.152.114:tsol 129.153.49.8:tsol 129.153.49.9:confidential 129.153.3.123:confidential 129.153.152.127:confidential
-
If there are other Solaris or Trusted Solaris machines that the SSP needs to communicate with, they also need to be viewed by the SSP using the correct template. This would require additional entries in this /etc/security/tsol/tnrhdb file.
-
Depending on the site's configuration, you might also need to update tnrhdb files on other Trusted Solaris machines so that they can communicate with the freshly installed SSP using the correct template.
-
-
Using the Admin Editor, update the /etc/inet/netmasks file.
If the netmasks file does not contain the netmask for all the network numbers used in the /etc/inet file.
For example, if the /etc/hosts file defines the control boards to be:
10.100.100.100 ctrl_brd_0 10.100.101.100 ctrl_brd_1
The /etc/inet/netmasks file would need to have two entries:10.100.100.0 255.255.255.0 10.100.101.0 255.255.255.0
-
Using the Admin Editor, update the /etc/default/login file to allow remote login to the root role from any workstation.
Comment out the CONSOLE=/dev/console line in the /etc/default/login file, as in:
#CONSOLE=/dev/console
Requirements for remote login are discussed in greater detail in “Remote Administration Options” in Trusted Solaris Administrator's Procedures.
-
Using the Name Service Switch action, edit the /etc/nsswitch.conf file on the main SSP and the spare SSP.
If you are using local configuration files, the lines in the /etc/nsswitch.conf files are similar to the following example:
hosts: files ethers: files netmasks: files bootparams: files tnrhtp: files tnrhdb: files auth_attr: files prof_attr: files
For NIS+, the lines in the file should look like the following:
hosts: files nisplus ethers: files nisplus netmasks: files nisplus bootparams: files nisplus tnrhtp: nisplus files tnrhdb: nisplus files auth_attr: files nisplus prof_attr: files nisplus
For NIS, the lines in the file should look like the following:
hosts: files nis ethers: files nis netmasks: files nis bootparams: files nis tnrhtp: nis files tnrhdb: nis files auth_attr: files nis prof_attr: files nis
Note –The name service information (NIS+ and NIS) is dependent on your network configuration.
-
Reboot the SSP.
- © 2010, Oracle Corporation and/or its affiliates
