Chapter 6 Managing Mail
This chapter covers security, multilevel mailers, and trouble-shooting differences when administering mail in the Trusted Solaris environment.
Note -
The Solaris 8 4/01 release contains a number of changes to the sendmail program. See "Mail Services" in Solaris 8 System Administration Supplement for more information. The Solaris 8 4/01 release is the basis of this Trusted Solaris release.
This chapter contains the following procedures:
-
"To Configure Users To Receive Mail Below Their Minimum Labels"
-
"To Create a Multilevel Action for the Alternate Mail Application "
-
"To Substitute an Alternate Mail Application for All Users "
Managing Trusted Solaris Mail Features
In the Trusted Solaris environment, the System Adminstrator role sets up and administers mail servers according to instructions in the Solaris System Administration Guide, Volume 2 and System Administration Guide, Volume 3. In addition, the security administrator determines how Trusted Solaris mail features should be configured. The following sections describe aspects of managing mail that are specific to the Trusted Solaris environment.
.mailrc Is at User's Minimum Label Only
By default, users' .mailrc files are stored only in the SLD at the user's minimum label. Users who work at multiple labels do not have a .mailrc at the higher labels unless they copy or link the .mailrc file to each higher SLD.
The Security Administrator role or the individual user can add the .mailrc file to either .copy_files or .link_files. See updatehome(1M) for a description of .copy_files and .link_files. See "Managing Initialization Files" for more information.
For background about mail aliases, see the Mail Aliases section in "Introduction to Mail Services" in the Solaris System Administration Guide, Volume 3 .
The Solaris Management Console Manages Mail Aliases
Local and name service mail aliases are managed using the Solaris Management Console (SMC) Mailing Lists tool. Depending on the scope of the selected SMC toolbox, an administrator can update the local /etc/aliases file, the mail.aliases NIS map, or the mail_aliases NIS+ table.
Users Cannot Read Email Below Minimum Label
The sendmail.cf file has been extended with Trusted Solaris options to enable the security administrator to customize labeled mail delivery. By default, ADMIN_LOW-labeled mail is upgraded to the recipient's minimum label. Other mail that is labeled below the recipient's minimum label is returned. ADMIN_LOW mail is treated differently from other mail because ADMIN_LOW mail is always sent by a system process to an account (usually an administrative role account) that should see the mail.
The default behavior is shown in the commented-out lines in the sendmail.cf file.
#O LabelAdminLow=upgrade #O LabelTooLow=return |
The Security Administrator role may change the values for the Trusted Solaris-specific options in the sendmail(1M) configuration file sendmail.cf to be consistent with the site's security policy. A user who is cleared to a particular label, such as CONFIDENTIAL or INTERNAL USE ONLY, should probably not be able to send mail to a user whose minimum label dominates the first user's label, such as SECRET or NEED TO KNOW.
Users Cannot List the Mail Queue
By default, a user is not able to list queued mail sent by other users. The restrictmailq privacy option is set by default in the sendmail.cf file.
Listing of the mail queue is done either by entering the mailq command or the equivalent command, sendmail with the -bp option. These commands are in the Mail Management profile, and show mail only at labels dominated by the calling process.
See "To Permit Users to See the Mail Queue" for how to enable a user on a particular system to list the queue.
dtmail is the Default Mail Application
By default, dtmail is the mail application that is launched from the Mailer subpanel on the Trusted Solaris Front Panel. Trusted Solaris software enables the System Administrator role to substitute an alternate mail application that provides full multilevel mail capabilities.
Without administrative intervention, any user can drag and drop an action for an alternate mail application into the Front Panel and then access the newly-installed mailer at the label of the current workspace. However, since mail monitoring at multiple labels does not occur when an action is installed this way, dragging and dropping by individual accounts of alternate mail actions into the Front Panel is only appropriate at a site using a single label.
Before an alternate mail action can be installed in the front panel, an application must first be defined for the mail application. The example in "To Create a Multilevel Action for the Alternate Mail Application " shows the substitution of the OpenWindows mailtool for Dtmail, even
though it is unlikely that this substitution would be made. The example relies on a predefined OpenWindows mailtool action in the /usr/dt/appconfig/types/C/sunOW.dt file as shown below.
ACTION OWmailtool
{
LABEL OW Mail Tool
ICON OWmailtool
TYPE COMMAND
WINDOW_TYPE NO_STDIO
EXEC_STRING /usr/openwin/bin/mailtool
}
|
See "To Create a Multilevel Action for the Alternate Mail Application " for creating an alternate Front Panel mail application, and "To Substitute an Alternate Mail Application for All Users " and "To Install an Alternate Mailer in the Front Panel" for different distribution methods.
Troubleshooting Mail Problems
Tracing Mail Delivery Difficulties
Trusted Solaris 8 4/01 software checks host and user labels before sending or forwarding mail.
-
The software checks that the mail is within the accreditation range of that host, as described in the following list and in Chapter 8, Specifying Routing and Security for Remote Computers.
-
The software checks that the mail is between the account's clearance and minimum label.
See "To Troubleshoot Mail Delivery Difficulties" for specific guidelines in debugging label difficulties.
Tracing sendmail's Activities
Multiple instances of sendmail are involved in local and remote mail delivery. To aid in debugging any problems with sendmail, Figure 6-1 shows how data flows through the sendmail processes.
Any mailer that is used to send mail (the default is dtmail) starts an instance of sendmail. This instance of sendmail attempts to deliver any mail that originates on the host, storing it in the local /var/spool/mqueue MLD until it is delivered [1 in Figure 6-1 shows this instance of sendmail]. Normally the message is delivered right away so its stay in the queue is only a matter of seconds. However, if the remote host is down, mail can stay in the queue indefinitely.
An instance of the sendmail program also starts when the system is booted. This instance of sendmail listens at port 25 and attempts to deliver any mail that it receives from a remote host, also storing each message in the mail queue MLD until it is delivered [3 and 5 in the example].
Yet another instance of sendmail periodically scans the mail queue and attempts to deliver any mail in the queue [2 and 4 in the example]. The following figure shows some of the sendmail processes on three hosts: cascade, trustworthy, and juggle. Host trustworthy is the mail relay host for juggle.
Figure 6-1 Sendmail Data Flow Example
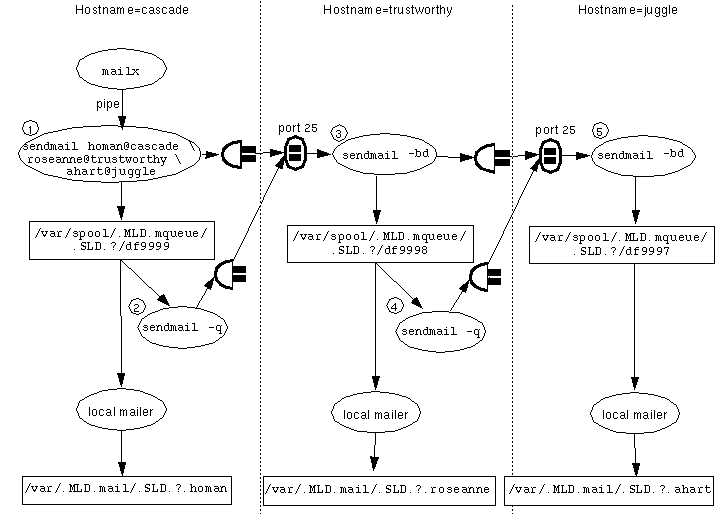
When mail is sent to username@hostname and hostname is a remote host, sendmail forwards the message to port 25 of hostname. In the example, when mail addressed to homan@cascade is sent from another account on host cascade, sendmail #1 puts the mail into an SLD within the /var/spool/.MLD.mqueue on cascade, where it is delivered by a local mailer. sendmail #2 on cascade periodically polls the queue and delivers mail that could not get delivered right away. sendmail #3 and #5 on hosts trustworthy and juggle listen on port 25 for incoming mail. The messages originating on cascade that are addressed to hosts trustworthy and juggle are both put into the local /var/spool/.MLD.mqueue and sent to port 25 of trusted, which is acting as a mail relay host in this example. The sendmail #3 on trusted also puts both messages into an SLD within the local /var/spool/mqueue, where the message to roseanne@trustworthy is delivered by the local mailer and the message to ahart@juggle is forwarded to sendmail #5, which is listening at port 25 of juggle.
Debugging sendmail
Debugging sendmail using the -d option is described in the sendmail Nutshell Handbook published by O'Reilly & Associates, Inc. To review briefly, you can get debugging information by specifying sendmail with the -d option followed by X. To limit the output of sendmail -d to a specific aspect of sendmail's behavior, you can specify a category optionally followed by a dot (.) followed by a level from 0-9, with 9 meaning the most information. Category 75, which is unique to the Trusted Solaris version of sendmail, selects Trusted Solaris debugging information.
Managing Mail (Tasks)
To Enable the IMAP Server to Authenticate Users
This procedure enables the mail server in a NIS+ domain to authenticate users, while protecting the NIS+ password table from being read.
-
On the NIS+ master, assume the System Administrator role and go to an
ADMIN_LOWworkspace. -
Open the System_Admin folder in the Application Manager.
-
Double-click the Add to NIS+ Administrative Group action and enter the IMAP server in its full principal name.
The principal name has the format hostname.subdomain.domain.suffix.. For example:
Group Name: admin Principal Name: pigeon.aviary.eco.org.
Note -Remember to type a period (.) at the end of the the domain name.
To Configure Users To Receive Mail Below Their Minimum Labels
The value upgrade means to upgrade a low-labeled message to the recipient's minimum label, and deliver it.
The value accept means to leave the message at the low label and deliver it.
The value return means to return the message to the sender (the default).
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Use the Set Mail Options action in the System_Admin folder in the Application Manager to open the sendmail.cf file for editing.
-
Search for TSOL, and change the default settings to reflect site security policy.
# TSOL: Incoming mail below recipient's minimum label # Possible values are return, upgrade, or accept #O LabelTooLow=return # Special case for mail labeled admin_low #O LabelAdminLow=upgrade
To Modify a Mail Alias
-
Assume the System Administrator role and go to an
ADMIN_LOWworkspace. -
Launch the SMC, open the Trusted Solaris Configuration toolbox, and choose the appropriate name service scope for your site (NIS or NIS+).
-
Double-click the Users tool and enter the role password when prompted.
-
Double-click the Mailing Lists tool, and follow the online help for creating and modifying mailing lists.
To Permit Users to See the Mail Queue
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace on the system where you want a user to be able to list the mail queue. -
Use the Set Mail Options action in the System_Admin folder in the Application Manager to open the sendmail.cf file for editing.
-
Search for the restrictmailq option in the file.
# Privacy flags O PrivacyOptions=authwarnings,restrictmailq
-
Remove the restrictmailq option.
# Privacy flags O PrivacyOptions=authwarnings
-
Save and quit the file.
-
Open the SMC at the appropriate scope and assign the Mail Management rights profile to the user.
The user can now use the mailq and sendmail -bp commands show the mail queue at labels dominated by the user's process.
To Troubleshoot Mail Delivery Difficulties
-
Check that there is a properly configured network connection between the sending and receiving hosts, as detailed in "To Check Network Connections for Sending Mail".
-
Check the nsswitch.conf file and the mail aliases repositories.
sendmail consults the local /aliases file, the NIS map mail.aliases, or the NIS+ mail_aliases table when determining where to deliver mail. Which alias file it consults depends on the nsswitch.conf(4) entry for aliases.
For example, mail to janez from a process on her Trusted Solaris desktop tern would not go to janez@tern if sendmail consults the NIS+ mail_aliases table and finds an alias of janez@egret in that table for user janez.
To Trace sendmail for Trusted Solaris Information
-
Assume the System Administrator role and go to an
ADMIN_LOWworkspace. -
Go to the /etc/init.d directory and stop sendmail.
$ cd /etc/rc2.d $ sendmail stop
-
Debug sendmail using the sendmail -d command followed by the category 75 optionally followed by a dot (.) and a level, followed by a space and the address, followed by a message.
A message can be included either by redirecting the contents of a file to the address, as shown below, or by entering return at the end of the line. In the latter case, a Subject: prompt comes up; after entering the subject, you can create a message from the command line, using the syntax of the mail(1) command.
$ /usr/lib/sendmail -d75.9 janez@tern < /etc/motd
-
Review the error messages.
-
Restart sendmail when you are through.
$ cd /etc/init.d $ sendmail start
-
Return to Step 7 in "To Check Network Connections for Sending Mail" if the user still has trouble sending or receiving mail.
To Check Network Connections for Sending Mail
-
As a user, send mail using the mailx command.
tern% mailx -v somebody@somehost Subject: test1 testl .
Review the messages from mailx.
-
Log in to the sending host or, if the mail server is not the same as the sending host, log in to the mail server at the label at which the user sends mail.
-
Use the telnet command to connect to port 25 of the receiving host.
egret% telnet hostname 25
If the connection is properly set up. that is, the trusted networking databases for the sending and the receiving hosts have the correct labels, the sendmail on the destination host prints a message like:
220 hostname Sendmail version ready at date
End the connection by typing quit.
quit
-
If the connection seems to be set up properly, go to the following step.
-
If telnet sends an error message, then the connection is not properly set up. Use the following table to determine the next step.
Type of host
Go to ...
Trusted Solaris host
label-cognizant non-Trusted Solaris host
unlabeled host (such as Solaris)
-
-
Assume a role with the Mail Management right.
-
At the label of the outgoing mail, list the mail queue on the sending host or, if the mail server is not the same as the sending host, list the mail queue on the mail server.
$ mailq | more
Check the list to see if the mail is stuck on the mail server.
-
Try the procedure under "To Trace sendmail for Trusted Solaris Information".
-
If the destination host is running a Trusted Solaris 2.5.1 or later release, do these steps to make sure the destined user is able to receive mail within Trusted Solaris security policy:
-
Check that the recipient has a valid user account.
In the Trusted Solaris 8 and Trusted Solaris 8 4/01 releases, use the SMC User Accounts tool. In Trusted Solaris 2.5.1 and Trusted Solaris 7, use the Solstice User Manager.
-
Note the account's minimum label and clearance.
-
Check that the label of the mail is within the System Accreditation range of the destination host as specified in the label_encodings(4) file.
sendmail does not deliver mail if the label of the mail is outside the System Accreditation Range.
-
Check that the label of the mail is within the User Accreditation Range of the destination host as specified in the label_encodings(4) file.
If the label of the mail is inside the System Accreditation Range but outside the User Accreditation Range, such as mail sent at
ADMIN_LOWandADMIN_HIGH, go to Step 8. -
Suggested fix:
-
If the label of the mail being sent is not in the recipient's label range, try to find a mutually-acceptable label for the sender and the recipient. If one is found, change the label and try again.
-
If the mail goes through, instruct the sender to send mail to that recipient at the mutually-acceptable label.
-
-
If the mail is below the minimum label of the recipient, change the default Trusted Solaris options in the sendmail.cf file, if doing so is consistent with your site's security policy.
See "Users Cannot Read Email Below Minimum Label" and "To Configure Users To Receive Mail Below Their Minimum Labels".
-
To enable anyone to receive mail from system processes outside the User Accreditation Range if the tsoladminlowaccept or tsolotherlowreturn option are used, use the Rights tool to give the user the
solaris.label.rangeauthorization.The default administrative roles have the needed authorization in their profiles.
-
-
For a destination host running the Trusted Solaris operating environment, check that the sending host has properly configured tnrhdb and tnrhtp entries for the receiving host.
Note -You can use the tninfo(1M) command to check the tnrhdb(4)/tnrhtp(4) configuration. The -h hostname option lists the name of the template assigned to the specified host, while the -t template_name option lists the entries specified in the template, including the host type.
-
Check that the destination host has the correct template name assigned to it in the tnrhdb database, and that the template in the tnrhtp file correctly specifies
sun_tsolas the host type. -
Check that the minimum and maximum label set in the assigned template in tnrhtp allow communications at the label of the mail that is not being delivered.
-
Once these checks are passed, try Step 3 in "To Check Network Connections for Sending Mail" to confirm that the network connection works.
-
-
For a labeled destination host that is not a Trusted Solaris system, check that the sending host has properly configured tnrhdb/tnrhtp entries for the receiving host.
Read the tnrhtp(4) man page if necessary to find out the correct host type and other options to specify in the template assigned to the host. For example, CIPSO type hosts require certain options, and RIPSO type hosts require other options.
-
Create a template or use an appropriate one in the tnrhtp, and check that the correct template is assigned to the host in the tnrhdb database.
Double-check the attributes in the template, for example, host type and labe range.
-
Once these checks are passed, try Step 3 in "To Check Network Connections for Sending Mail" to confirm that the network connection works.
-
-
If the destination host is running an unlabeled operating system, check that the sending host has properly configured tnrhdb/tnrhtp entries for the receiving host.
-
Check that the destination host has been assigned the correct template name in the tnrhdb database, and that the template correctly defines the host's type as
unlabeled. -
Check that the default label for the unlabeled host in the assigned template in the tnrhtp allows communications at the label of the mail that is not being delivered.
-
Once these checks are passed, try Step 3 in "To Check Network Connections for Sending Mail" to confirm that the network connection works.
-
To Troubleshoot Loss of Mail Icons
If all mail icons disappear from the Front Panel, replace them from the $HOME/.dt/fp.dynamics directory.
-
Assume the System Administrator role and go to an
ADMIN_HIGHworkspace. -
Investigate the account's .dt/fp.dynamics directory in its home directory.
During the operation of the system, all changes to the Front Panel are stored in each account's .dt/fp.dynamics directory at the session clearance.
-
Copy the contents of fp.dynamics to a backup directory and restore the files one by one until the Front Panel configuration is restored.
To Create a Multilevel Action for the Alternate Mail Application
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Use the Admin Editor action from the System_Admin folder to bring up the /usr/dt/appconfig/types/C/dtwm.fp file to edit.
-
Find the control section for mail shown below.
CONTROL Mail { TYPE icon CONTAINER_NAME Top CONTAINER_TYPE BOX POSITION_HINTS 5 ICON DTmail LABEL Mail ALTERNATE_ICON DtMnew MONITOR_TYPE mail DROP_ACTION Compose PUSH_ACTION DTWmail PUSH_RECALL true CLIENT_NAME dtmail HELP_TOPIC FPOnItemMail HELP_VOLUME FPanel } -
Copy the control text to a file whose name has the .fp extension, for example, mail.fp, and quit the dtwm.fp file.
-
Bring up the Admin Editor action from the System_Admin folder and open the new mail.fp file for editing.
-
Change the title of the mail control to OW_Mail.
CONTROL OW_Mail
-
Change the following variables to the following values:
ICON OWmailtool LABEL OW Mail Tool PUSH_ACTION OWmailtool CLIENT_NAME mailtool
The ICON field identifies the icon of the replacement application.
The LABEL field changes the icon label that appears with the icon of the replacement application.
The PUSH_ACTION field identifies the replacement action to be run when the user clicks on the new mail icon. The action name supplied here must be defined in the one of the application search paths. The OWmailtool action shown is defined in sunOW.dt in the /usr/dt/appconfig/types/locale directory.
The CLIENT_NAME field identifies the executable for the replacement application. The path for CLIENT_NAME must be defined by an EXEC_STRING in the action's definition. For example, the OWmailtool action has EXEC_STRING defined as /usr/openwin/bin/mailtool.
-
Change DROP_ACTION or leave as shown below.
DROP_ACTION Compose
Other mailers may or may not have a Compose action. For example, OpenWindows mailtool does not. If you leave the DROP_ACTION as Compose, if someone drags mail to the mail icon, a dtmail Compose window will come up. If you remove the DROP_ACTION, nothing happens if mail is dragged to the mail icon.
-
Leave the rest of the variables unchanged, as shown below.
TYPE icon CONTAINER_NAME Top CONTAINER_TYPE BOX POSITION_HINTS 5 ALTERNATE_ICON DtMnew MONITOR_TYPE mail PUSH_RECALL true HELP_TOPIC FPOnItemMail HELP_VOLUME FPanel
When PUSH_RECALL is true, an application that is launched for a second time uses an existing application window.
-
Save the changes and quit the file.
-
Place the mail.fp file, in an accessible directory, such as $HOME/secadmin.
$ mv mail.fp /home/secadmin/cde_changes/
To Substitute an Alternate Mail Application for All Users
Do this procedure on every system before users start getting mail. If you do it later, you will need to clean up the contents of directories created by the window system in every .dt/fp.dynamics directory in every SLD in every home directory MLD.
-
Make sure that the alternate mail action has been fully tested.
-
Assume the System Administrator role and go to an
ADMIN_LOWworkspace. -
In a terminal, go to the /etc/init.d directory and stop sendmail.
$ cd /etc/init.d $ sendmail stop
-
Assume the Security Administrator role and go to an
ADMIN_LOWworkspace. -
Use the Admin Editor to replace the CONTROL Mail section of the /usr/dt/appconfig/types/locale/dtwm.fp file with the contents of the mail.fp file.
Replace --
CONTROL Mail { TYPE icon CONTAINER_NAME Top CONTAINER_TYPE BOX POSITION_HINTS 5 ICON DTmail LABEL Mail ALTERNATE_ICON DtMnew MONITOR_TYPE mail DROP_ACTION Compose PUSH_ACTION DTWmail PUSH_RECALL true CLIENT_NAME dtmail HELP_TOPIC FPOnItemMail HELP_VOLUME FPanel }With the contents of the mail.fp file --
CONTROL OW_Mail { TYPE icon CONTAINER_NAME Top CONTAINER_TYPE BOX POSITION_HINTS 5 ICON OWmailtool LABEL OW Mail Tool ALTERNATE_ICON DtMnew MONITOR_TYPE mail DROP_ACTION Compose PUSH_ACTION OWmailtool PUSH_RECALL true CLIENT_NAME mailtool HELP_TOPIC FPOnItemMail HELP_VOLUME FPanel } -
Change the name of the CONTROL back to Mail and save the dtwm.fp file.
CONTROL OWMail :wq
-
If the system has been receiving mail, remove all contents of the
$HOME/.dt/fp.dynamics directory. -
Restart the Workspace Manager from the workspace menu to see the changes to the dtwm.fp go into effect in the Front Panel.
-
Assume the System Administrator role and go to an
ADMIN_LOWworkspace. -
In a terminal emulator such as dtterm, restart sendmail.
$ cd /etc/init.d $ sendmail start
To Install an Alternate Mailer in the Front Panel
-
Assume the System Administrator role and go to an
ADMIN_LOWworkspace on the system where you want to install an alternate mail program. -
In a terminal, go to the /etc/init.d directory and stop sendmail.
$ cd /etc/init.d $ sendmail stop
-
Using the File Manager, change to the directory where the alternate mail application's control file (mail.fp) resides.
The Security Administrator placed it in an accessible directory in Step 11 of "To Create a Multilevel Action for the Alternate Mail Application ".
-
Add mail.fp to the /usr/dt/appconfig/types/locale or /etc/dt/appconfig/types/locale directory.
-
Go to a user workspace.
-
Click the Mailer subpanel access button to bring up the subpanel.
-
Drag the icon for the alternate mailer's front panel control file to the Install Icon dropsite in the Mailer subpanel.
The icon for the alternate mail application should appear in the Mail slider.
-
Click the right mouse button while the pointer is over the alternate mail and select Copy to Main Panel.
-
Remove each old mail icon in the subpanel by clicking the right mouse button over an icon for the old application and selecting Delete.
Note -Remove all old icons. You cannot have a mixture of mail applications running at the same time.
-
Select Restart Workspace Manager from the Workspace Menu to adjust the size of the subpanel.
-
Return to the System Administrator workspace and restart sendmail.
$ cd /etc/init.d $ sendmail start
-
If this is an end user system, delete the System Administrator workspace.
- © 2010, Oracle Corporation and/or its affiliates
