Chapter 16 Planning for the PPP Link (Tasks)
Setting up a PPP link involves a set of discrete tasks, which includes planning tasks and other activities that are not related to PPP. This chapter explains how to plan for the most common PPP links, for authentication, and for PPPoE.
The task chapters that follow Chapter 16, Planning for the PPP Link (Tasks) use sample configurations to illustrate how to set up a particular link. These sample configurations are introduced in this chapter.
Topics that are covered include the following:
Overall PPP Planning (Task Map)
PPP requires planning tasks before you actually can set up the link. Moreover, if you want to use a PPPoE tunneling, you first have to set up the PPP link and then provide tunneling. The following task map lists the large planning tasks that are discussed in this chapter. You might need to use only the general task for the link type to be configured. Or you might require the task for the link, authentication, and perhaps PPPoE.
Table 16–1 Task Map for PPP Planning|
Task |
Description |
For Instructions |
|---|---|---|
|
Plan for a dial-up PPP link |
Gather information that is required to set up a dial-out machine or a dial-in server | |
|
Plan for a leased-line link |
Gather information that is required to set up a client on a leased line | |
|
Plan for authentication on the PPP link |
Gather information that is required to configure PAP or CHAP authentication on the PPP link | |
|
Plan for a PPPoE tunnel |
Gather information that is required to set up a PPPoE tunnel over which a PPP link can run |
Planning a Dial-up PPP Link
Dial-up links are the most commonly used PPP links. This section includes the following information:
-
Planning information for a dial-up link
-
Explanation of the sample link to be used in Chapter 17, Setting Up a Dial-up PPP Link (Tasks)
Typically, you only configure the machine at one end of the dial-up PPP link, the dial-out machine, or the dial-in server. For an introduction to dial-up PPP, refer to Dial-up PPP Overview.
Before You Set Up the Dial-out Machine
Before you configure a dial-out machine, gather the information that is listed in the following table.
Note –
The planning information in this section does not include information to be gathered about authentication or PPPoE. For details about authentication planning, refer to Planning for Authentication on a Link. For PPPoE planning, refer to Planning for DSL Support Over a PPPoE Tunnel.
Table 16–2 Information for a Dial-out Machine
|
Information |
Action |
|---|---|
|
Maximum modem speed |
Refer to documentation that was provided by the modem manufacturer. |
|
Modem connection commands (AT commands) |
Refer to documentation that was provided by the modem manufacturer. |
|
Name to use for dial-in server at the other end of the link |
Create any name that helps you identify the dial-in server. |
|
Login sequence that was required by dial-in server |
Contact the dial-in server's administrator or ISP documentation if dial-in server is at the ISP. |
Before You Set Up the Dial-in Server
Before you configure a dial-in server, gather the information that is listed in the following table.
Note –
The planning information in this section does not include information to be gathered about authentication or PPPoE. For details about authentication planning, refer to Planning for Authentication on a Link. For PPPoE planning, refer to Planning for DSL Support Over a PPPoE Tunnel.
Table 16–3 Information for a Dial-in Server
|
Information |
Action |
|---|---|
|
Maximum modem speed |
Refer to documentation that was provided by the modem manufacturer. |
|
User names of people who are permitted to call the dial-in server |
Obtain the names of the prospective users before you set up their home directories, as discussed in How to Configure Users of the Dial-in Server. |
|
Dedicated IP address for PPP communications |
Obtain an address from the individual at your company who is responsible for delegating IP addresses. |
Example of a Configuration for Dial-up PPP
The tasks to be introduced in Chapter 17, Setting Up a Dial-up PPP Link (Tasks) execute a small company's requirement to let employees work at home a few days a week. Some employees require the Solaris OS on their home machines. These workers also need to log in remotely to their work machines on the corporate Intranet.
The tasks set up a basic dial-up link with the following features:
-
The dial-out machines are at the houses of employees who need to call the corporate intranet.
-
The dial-in server is a machine on the corporate intranet that is configured to receive incoming calls from employees.
-
UNIX-style login is used to authenticate the dial-out machine. Stronger Solaris PPP 4.0 authentication methods are not required by the company`s security policy.
The next figure shows the link that is set up in Chapter 17, Setting Up a Dial-up PPP Link (Tasks).
Figure 16–1 Sample Dial-up Link
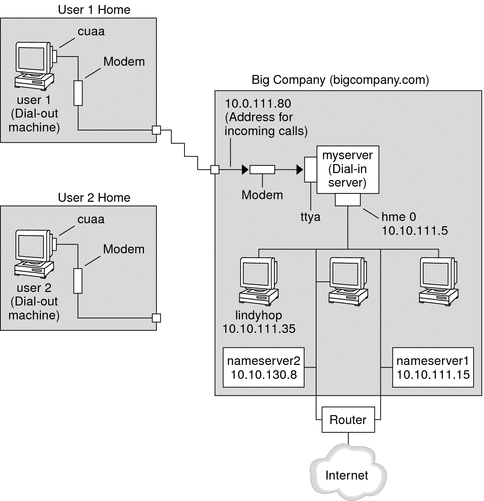
In this figure, a remote host dials out through its modem over telephone lines to Big Company's Intranet. Another host is configured to dial out to Big Company but currently is inactive. The calls from remote users are answered in the order received by the modem that is attached to the dial-in server at Big Company. A PPP connection is established between the peers. The dial-out machine can then remotely log in to a host machine on the Intranet.
Where to Go for More Information About Dial-up PPP
Refer to the following:
-
To set up a dial-out machine, see Table 17–2.
-
To set up a dial-in machine, see Table 17–3.
-
To get an overview of dial-up links, see Dial-up PPP Overview.
-
To get detailed information about PPP files and commands, see Using PPP Options in Files and on the Command Line.
Planning a Leased-Line Link
Setting up a leased-line link involves configuring the peer at one end of a switched or unswitched service that is leased from a provider.
This section includes the following information:
-
Planning information for a leased-line link
-
Explanation of the sample link that is shown in Figure 16–2
For an introduction to leased-line links, refer to Leased-Line PPP Overview. For tasks about setting up the leased line, see Chapter 18, Setting Up a Leased-Line PPP Link (Tasks).
Before You Set Up the Leased-Line Link
When your company rents a leased-line link from a network provider, you typically configure only the system at your end of the link. The peer at the other end of the link is maintained by another administrator. This individual might be a system administrator at a remote location in your company or a system administrator at an ISP.
Hardware That Is Needed for a Leased-Line Link
In addition to the link media, your end of the link requires the following hardware:
-
Synchronous interface for your system
-
Synchronous unit (CSU/DSU)
-
Your system
Some network providers include a router, synchronous interface, and a CSU/DSU as part of the customer premises equipment (CPE). However, necessary equipment varies, based on the provider and any governmental restrictions in your locale. The network provider can give you information about the unit that is needed, if this equipment is not provided with the leased line.
Information to Be Gathered for the Leased-Line Link
Before you configure the local peer, you might need to gather the items that are listed in the next table.
Table 16–4 Planning for a Leased-Line Link|
Information |
Action |
|---|---|
|
Device name of the interface |
Refer to the interface card documentation. |
|
Configuration instructions for the synchronous interface card |
Refer to the interface card documentation. You need this information to configure the HSI/P interface. You might not need to configure other types of interface cards. |
|
(Optional) IP address of the remote peer |
Refer to the service provider documentation. Alternatively, contact the system administrator of the remote peer. This information is needed only if the IP address is not negotiated between the two peers. |
|
(Optional) Name of the remote peer |
Refer to the service provider documentation. Alternatively, you can contact the system administrator of the remote peer. |
|
(Optional) Speed of the link |
Refer to the service provider documentation. Alternatively, you can contact the system administrator of the remote peer. |
|
(Optional) Compression that is used by the remote peer |
Refer to the service provider documentation. Alternatively, you can contact the system administrator of the remote peer. |
Example of a Configuration for a Leased-Line Link
The tasks in Chapter 18, Setting Up a Leased-Line PPP Link (Tasks) show how to implement the goal of a medium-sized organization (LocalCorp) to provide Internet access for its employees. Currently, the employees' computers are connected on a private corporate intranet.
LocalCorp requires speedy transactions and access to the many resources on the Internet. The organization signs a contract with Far ISP, a service provider, which allows LocalCorp to set up its own leased line to Far ISP. Then, LocalCorp leases a T1 line from Phone East, a telephone company. Phone East puts in the leased line between LocalCorp and Far ISP. Then, Phone East provides a CSU/DSU that is already configured to LocalCorp.
The tasks set up a leased-line link with the following characteristics.
-
LocalCorp has set up a system as a gateway router, which forwards packets over the leased line to hosts on the Internet.
-
Far ISP also has set up a peer as a router to which leased lines from customers are attached.
Figure 16–2 Example of a Leased-Line Configuration
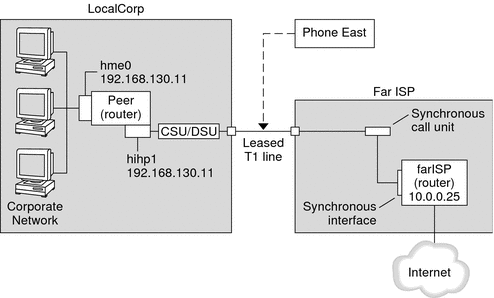
In the figure, a router is set up for PPP at LocalCorp. The router connects to the corporate Intranet through its hme0 interface. The second connection is through the machine's HSI/P interface (hihp1) to the CSU/DSU digital unit. The CSU/DSU then connects to the installed leased line. The administrator at LocalCorp configures the HSI/P interface and PPP files. The administrator then types /etc/init.d/pppd to initiate the link between LocalCorp and Far ISP.
Where to Go for More Information About Leased Lines
Refer to the following:
Planning for Authentication on a Link
This section contains planning information for providing authentication on the PPP link. Chapter 19, Setting Up PPP Authentication (Tasks) contains tasks for implementing PPP authentication at your site.
PPP offers two types of authentication, PAP, which is described in detail in Password Authentication Protocol (PAP) and CHAP, which is described in Challenge-Handshake Authentication Protocol (CHAP).
Before you set up authentication on a link, you must choose which authentication protocol best meets your site's security policy. Then, you set up the secrets file and PPP configuration files for the dial-in machines, or callers' dial-out machines, or both types of machines. For information about choosing the appropriate authentication protocol for your site, see Why Use PPP Authentication?.
This section includes the following information:
-
Planning information for both PAP and CHAP authentication
-
Explanations of the sample authentication scenarios that are shown in Figure 16–3 and Figure 16–4
For tasks about setting up authentication, see Chapter 19, Setting Up PPP Authentication (Tasks).
Before You Set Up PPP Authentication
Setting up authentication at your site should be an integral part of your overall PPP strategy. Before implementing authentication, you should assemble the hardware, configure the software, and test the link.
Table 16–5 Prerequisites Before Configuring Authentication|
Information |
For Instructions |
|---|---|
|
Tasks for configuring a dial-up link | |
|
Tasks for testing the link | |
|
Security requirements for your site |
Your corporate security policy. If you do not have a policy, setting up PPP authentication gives you an opportunity to create a security policy. |
|
Suggestions about whether to use PAP or CHAP at your site |
Why Use PPP Authentication?. For more detailed information about these protocols, refer to Authenticating Callers on a Link. |
Examples of PPP Authentication Configurations
This section contains examples of authentication scenarios to be used in the procedures in Chapter 19, Setting Up PPP Authentication (Tasks).
Example of a Configuration Using PAP Authentication
The tasks in Configuring PAP Authentication show how to set up PAP authentication over the PPP link. The procedures use as an example a PAP scenario that was created for the fictitious “Big Company” in Example of a Configuration for Dial-up PPP.
Big Company wants to enable its users to work from home. The system administrators want a secure solution for the serial lines to the dial-in server. UNIX-style login that uses the NIS password databases has served Big Company's network well in the past. The system administrators want a UNIX-like authentication scheme for calls that come in to the network over the PPP link. So, the administrators implement the following scenario that uses PAP authentication.
Figure 16–3 Example of a PAP Authentication Scenario (Working From Home)
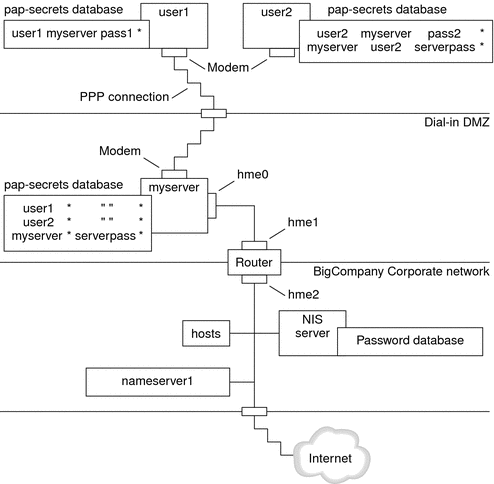
The system administrators create a dedicated dial-in DMZ that is separated from the rest of the corporate network by a router. The term DMZ comes from the military term “demilitarized zone.” The DMZ is an isolated network that is set up for security purposes. The DMZ typically contains resources that a company offers to the public, such as web servers, anonymous FTP servers, databases, and modem servers. Network designers often place the DMZ between a firewall and a company's Internet connection.
The only occupants of the DMZ that is pictured in Figure 16–3 are the dial-in server myserver and the router. The dial-in server requires callers to provide PAP credentials, including user names and passwords, when setting up the link. Furthermore, the dial-in server uses the login option of PAP. Therefore, the callers' PAP user names and passwords must correspond exactly to their UNIX user names and passwords in the dial-in server's password database.
After the PPP link is established, the caller's packets are forwarded to the router. The router forwards the transmission to its destination on the corporate network or on the Internet.
Example of a Configuration Using CHAP Authentication
The tasks in Configuring CHAP Authentication show how to set up CHAP authentication. The procedures use as an example a CHAP scenario to be created for the fictitious LocalCorp that was introduced in Example of a Configuration for a Leased-Line Link.
LocalCorp provides connectivity to the Internet over a leased line to an ISP. The Technical Support department within LocalCorp generates heavy network traffic. Therefore, Technical Support requires its own, isolated private network. The department's field technicians travel extensively and need to access the Technical Support network from remote locations for problem-solving information. To protect sensitive information in the private network's database, remote callers must be authenticated in order to be granted permission to log in.
Therefore, the system administrators implement the following CHAP authentication scenario for a dial-up PPP configuration.
Figure 16–4 Example of a CHAP Authentication Scenario (Calling a Private Network)
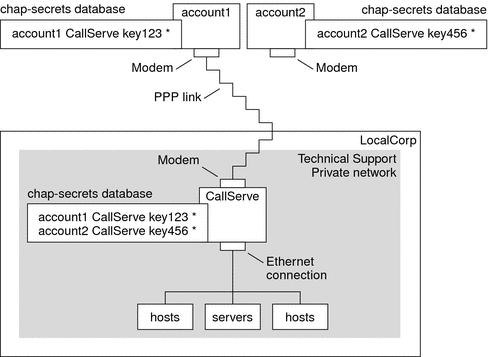
The only link from the Technical Support network to the outside world is the serial line to the dial-in server's end of the link. The system administrators configure the laptop computer of each field service representative for PPP with CHAP security, including a CHAP secret. The chap-secrets database on the dial-in server contains the CHAP credentials for all machines that are allowed to call in to the Technical Support network.
Where to Go for More Information About Authentication
Choose from the following:
-
See Authenticating Callers on a Link and the pppd(1M) man page.
Planning for DSL Support Over a PPPoE Tunnel
Some DSL providers require you to set up PPPoE tunneling for your site in order to run PPP over the providers' DSL lines and high-speed digital networks. For an overview of PPPoE, see Support for DSL Users Through PPPoE.
A PPPoE tunnel involves three participants: a consumer, a telephone company, and an ISP. You either configure PPPoE for consumers, such as PPPoE clients at your company or consumers in their homes, or you configure PPPoE on a server at an ISP.
This section contains planning information for running PPPoE on both clients and access servers. The following topics are covered:
-
Planning information for the PPPoE host and access server
-
Explanation of the PPPoE scenario that is introduced in Example of a Configuration for a PPPoE Tunnel
For tasks about setting up a PPPoE tunnel, see Chapter 20, Setting Up a PPPoE Tunnel (Tasks).
Before You Set Up a PPPoE Tunnel
Your preconfiguration activities depend on whether you configure the client side or server side of the tunnel. In either instance, you or your organization must contract with a telephone company. The telephone company provides the DSL lines for clients, and some form of bridging and possibly an ATM pipe for access servers. In most contracts, the telephone company assembles its equipment at your site.
Before Configuring a PPPoE Client
PPPoE client implementations usually consist of the following equipment:
-
Personal computer or other system that is used by an individual
-
DSL modem, which is usually installed by the telephone company or Internet access provider
-
(Optional) A hub, if more than one client is involved, as is true for corporate DSL consumers
-
(Optional) A splitter, usually installed by the provider
Many different DSL configurations are possible, which depend on the user or corporation's needs and the services that are offered by the provider.
Table 16–6 Planning for PPPoE Clients|
Information |
Action |
|---|---|
|
If setting up a home PPPoE client for an individual or yourself, get any setup information that is outside the scope of PPPoE. |
Ask the telephone company or ISP for any required setup procedures. |
|
If setting up PPPoE clients at a corporate site, gather the names of users who are being assigned PPPoE client systems. If you configure remote PPPoE clients, you might be responsible for giving users information about adding home DSL equipment. |
Ask management at your company for a list of authorized users. |
|
Find out which interfaces are available on the PPPoE client. |
Run the ifconfig -a command on each machine for interface names. |
|
(Optional) Obtain the password for the PPPoE client. |
Ask users for their preferred passwords. Or, assign passwords to the users. Note that this password is used for link authentication, not for UNIX login. |
Before Configuring a PPPoE Server
Planning for a PPPoE access server involves working with the telephone company that provides your connection to its data service network. The telephone company installs its lines, often ATM pipes, at your site, and provides some sort of bridging into your access server. You need to configure the Ethernet interfaces that access the services that your company provides. For example, you need to configure interfaces for Internet access, as well as the Ethernet interfaces from the telephone company's bridge.
Table 16–7 Planning for a PPPoE Access Server|
Information |
Action |
|---|---|
|
Interfaces that are used for lines from data service network |
Run the ifconfig -a command to identify interfaces. |
|
Types of services to provide from the PPPoE server |
Ask management and network planners for their requirements and suggestions. |
|
(Optional) Types of services to provide to the consumers |
Ask management and network planners for their requirements and suggestions. |
|
(Optional) Host names and passwords for remote clients |
Ask network planners and other individuals at your site who are responsible for contract negotiations. The host names and passwords are used for PAP or CHAP authentication, not for UNIX login. |
Example of a Configuration for a PPPoE Tunnel
This section contains an example of a PPPoE tunnel, which is used as an illustration for the tasks in Chapter 20, Setting Up a PPPoE Tunnel (Tasks). Though the illustration shows all participants in the tunnel, you only administer one end, either the client side or server side.
Figure 16–5 Example of a PPPoE Tunnel
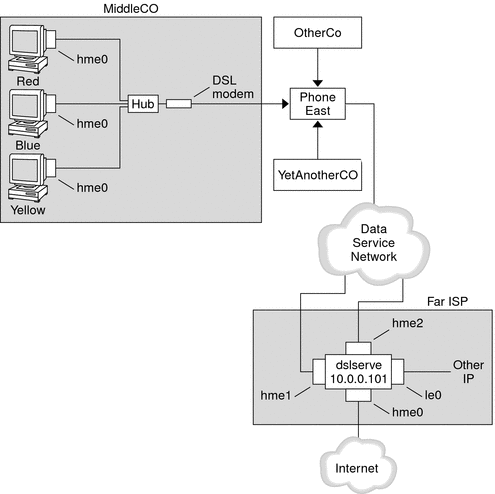
In the sample, MiddleCo wants to provide its employees with high-speed Internet access. MiddleCo buys a DSL package from Phone East, which, in turn, contracts with service provider Far ISP. Far ISP offers Internet and other IP services to customers who buy DSL from Phone East.
Example of a PPPoE Client Configuration
MiddleCo buys a package from Phone East that provides one DSL line for the site. The package includes a dedicated, authenticated connection to the ISP for MiddleCo's PPPoE clients. The system administrator cables the prospective PPPoE clients to a hub. Technicians from Phone East cable the hub to their DSL equipment.
Example of a PPPoE Server Configuration
To implement the business arrangement FarISP has with Phone East, the system administrator at FarISP configures the access server dslserve. This server has the following four interfaces:
-
eri0 – Primary network interface that connects to the local network
-
hme0 – Interface through which FarISP provides Internet service for its customers
-
hme1 – Interface contracted by MiddleCo for authenticated PPPoE tunnels
-
hme2 – Interface contracted by other customers for their PPPoE tunnels
Where to Get More Information About PPPoE
Choose from the following:
-
See Creating PPPoE Tunnels for DSL Support, and the pppoed(1M), pppoec(1M), and sppptun(1M) man pages.
- © 2010, Oracle Corporation and/or its affiliates
