Configuring Reverse Proxy in Web Server 7.0
The Sun Java System Web Server 7.0 integrates the reverse proxy functionality within the core server.
When web server is configured with reverse proxy functionality, it acts as a proxy for one or more backend servers and serves as a single point of access or gateway in a server farm. In a reverse proxy setup, the web server forwards the HTTP request it received from the browser client to the appropriate backend server. The HTML response from the backend server is sent back to the browser through the web server. Thus, the web server with reverse proxy hides the existence of backend servers.
Figure 4–4 Reverse Proxy Setup
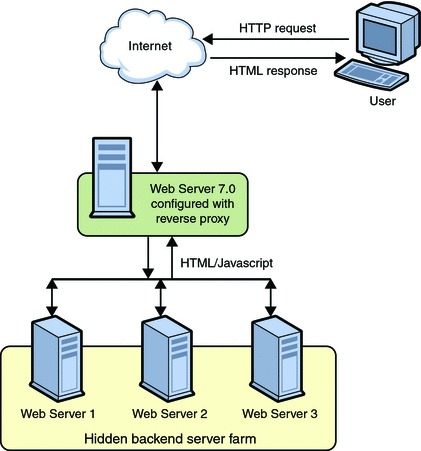
Web Server 7.0 with reverse proxy functionality acts as a simple software load balancer with the added ability to forward the sticky requests back to the same backend server.
Web server with reverse proxy can serve static content like gif and html files from its internal cache. At the same time, it functions as a load balancer and processes request for dynamic content like jsp, servlet or php files to the backend server. When web server is deployed in this configuration, disabling the Java web container will significantly reduce the memory footprint of the server. For information about disabling Java web container, see Tuning Web Container Within Web Server 7.0 in Sun Java System Web Server 7.0 Update 4 Performance Tuning, Sizing, and Scaling Guide. See CLI Reference, disable-java(1).
The advantages of reverse proxy within Web Server 7.0 are:
-
Conditional processing of request to the backend servers using the integrated regular expression support. For example, you can configure web server to function as reverse proxy only for Servlet and JSP. See Customizing Reverse Proxy.
-
Ability to efficiently edit the response received from the backend server using sed-response filter before sending the response. For information about sed-response, see sed-response in Sun Java System Web Server 7.0 Update 4 Administrator’s Configuration File Reference.
-
Ability to dynamically scale the web site by adding more backend servers with less configuration changes and minimal downtime. To add an additional backend server, you should edit the virtual server specific obj.conf and run the reconfig command. For information about reconfig command, see Dynamic Reconfiguration in Sun Java System Web Server 7.0 Update 4 Administrator’s Configuration File Reference.
Note –
In a typical deployment, one or more reverse proxies will be deployed between the browsers and the backend servers.
Configuring Reverse Proxy for Load-balancing
Web Server 7.0 provides a sophisticated built-in load balancer, the reverse proxy, which distributes load or request from the client to several backend servers.
Web Server provides GUI and CLI support for configuring the reverse proxy.
 Configuring Reverse Proxy Using Administration Console
Configuring Reverse Proxy Using Administration Console
-
Install Web Server on the node that you want to use for configuring reverse proxy.
-
Create a configuration. For example, rp.
-
Using the Administration Console, select Configurations > Virtual Servers > Content Handling > Reverse Proxy tab. Click New.
-
Specify values for the following parameters:
-
URI — The reverse proxy URI
-
Server URL — Comma separated server URLs of all the machines in the cluster separated by comma. If multiple values are given, the server will distribute load among the specified servers.
The format for entering the server URL is hostname:portnumber. For example, http://<content server-hostname>:port
-
-
Click the OK button.
-
Click the Deployment Pending link in the top right of the screen to deploy the modified configuration and to apply changes to the configuration.
-
Click the Deploy button.
Deployment successful message appears.
-
Start all instances of this modified configuration.
This completes configuring the reverse proxy for load balancing HTTP requests.
Note –To configure a reverse proxy in a cluster environment, issue a wildcard server certificate or the alternate subject names that can be set to the actual origin server host names. The other option of specifying the original server's host names in the subject name field limits the size of the cluster, leading the cluster to fail if another node is added to the cluster.
A wildcard server certificate can be created using the administration interfaces. After creating the server certificate use certutil to get the base64 encoded version of the certificate and install it as a trusted CA certificate on the load balancer configuration.
Type the following command to generate the base64 encoded certificate bash$./certutil -L -a -d instancedir/config. Copy the output of the command and paste it in the install certificate wizard.
 Configuring Reverse Proxy Using CLI
Configuring Reverse Proxy Using CLI
Perform the following steps to configure reverse proxy in CLI mode. You will create a configuration config1 and an instance rp as reverse proxy.
-
Start the Administration Server:
$ <install-dir>/admin-server/bin/startserv
-
Invoke the CLI shell:
<install-dir>/admin-server/bin/wadm -user <username>
You can see the wadm shell
-
Create config1:
wadm>create-config --http-port=8080 --server-name=config1 --server-user=root config1
-
Create an instance for the config1 configuration:
wadm>create-instance --config=config1 <host-name>
-
Add the web application on the created configuration:
wadm>add-webapp --config=config1 -vs=config1 --uri/test <warfile>
-
Deploy the web application.
wadm>deploy-config --user=admin --password-file=admin.pwd --host=serverhost --port=8989 config1
-
Create a rp configuration:
wadm>create-config --http-port=8081 --server-name=rp --server-user=root rp
-
Enable the rp configuration to reverse proxy using the following command:
wadm> create-reverse-proxy --user=admin --password-file=admin.pwd --host=serverhost --config=rp --vs=rp --uri-prefix=// --server=http://rick.india.sun.com:8080
To redirect to a secure site, follow the same step and provide the
httpsaddress for the--serveroption.See CLI Reference, create-reverse-proxy(1).
-
Create an instance for the rp configuration.
wadm>create-instance --config=rp <host-name>
-
Start the instances:
wadm>start-instance --config=config1 <host-name>
wadm>start-instance --config=rp <hostname>
The web application deployed in config1 can be viewed through rp instance.
http://<rp instance hostname>:8081/test
See CLI Reference, list-reverse-proxy-uris(1), set-reverse-proxy-prop(1), get-reverse-proxy-prop(1), forward-reverse-proxy-header(1), block-reverse-proxy-header(1), and list-reverse-proxy-headers(1)
Modifying Reverse Proxy Parameters
 To Modify Reverse Proxy Parameters
To Modify Reverse Proxy Parameters
-
Using the Administration Console, select Configurations > Virtual Servers > Content Handling > Reverse Proxy tab.
-
Click the URI button.
You can edit the following parameters:
-
URI — The reverse proxy URI
-
Server URL — Comma separated URLs of the remote server. If multiple values are given, the server will distribute load among the specified servers.
-
Sticky Cookie — Name of a cookie that when present in a response, will cause subsequent requests to stick to that origin server.
-
Sticky URI Parameter — Name of a URI parameter to inspect for route information. When the URI parameter is present in a request URI and its value contains a colon `:' followed by a route ID, the request will "stick" to the origin server identified by that route ID.
-
Route Header — Name of the HTTP request header used to communicate route IDs to origin servers.
-
Route Cookie — Name of the cookie generated by the server when it encounters a stickycookie in a response. The routecookie stores a route ID that enables the server to direct subsequent requests back to the same origin server.
-
Rewrite Headers — Comma separated list of HTTP request headers.
-
Configuring Timeout Parameter in Reverse Proxy
-
Using the Administration Console, select Configurations > Virtual Servers > Content Handling > Reverse Proxy tab.
-
Click the URI button.
A new window appears.
-
Click the HTTP Client Configuration link.
You can edit the Idle Timeout parameter. The default value is 300.
Customizing Reverse Proxy
You can configure conditional request processing in reverse proxy by manually editing the virtual server specific obj.conf file or through CLI. After the configuration changes are done, it is recommended to deploy the configuration and start the instance so that the changes are implemented.
wadm>deploy-config config_name |
wadm>start-instance --config config_name hostname |
See CLI Reference, deploy-config(1), start-instance(1)
Note –
The appropriate obj.conf file used by your virtual server should be modified. It can be <vs>-obj.conf or the default obj.conf, depending on the configuration.
The following examples discuss some of the possible configurations in Web Server.
-
Configuring reverse proxy for all .jsp, .php requests.
-
Create a rp configuration.
wadm>create-config --http-port=8081 --server-name=rp --server-user=root rp
-
Enable the rp configuration to reverse proxy using the following command:
wadm> create-reverse-proxy --user=admin --password-file=admin.pwd --host=serverhost --config=rp --vs=rp --uri-prefix=// --server=http://rick.india.sun.com:8080
-
Disable Java for the rp configuration.
wadm disable-java --user=admin --password-file=admin.pwd --host=serverhost --config=rp
See CLI Reference, disable-java(1).
-
Create an instance for the rp configuration.
wadm>create-instance --config=rp <host-name>
-
Modify the
<vs>-obj.conffile, so that the above expression is added to the NameTrans fn="map" directive.
NameTrans fn="map" from="/" to="http:/" name="custom_reverse_proxy" ... <Object name ="custom_reverse_proxy"> Route fn="set-origin-server" server="http://<hostname>:<port>" </Object> <Object name ppath="http:*" Service fn="proxy-retrieve" method="*" </Object>
-
-
Configuring http-referer header in reverse proxy.
-
Create a rp configuration.
wadm>create-config --http-port=8081 --server-name=rp --server-user=root rp
-
Enable the rp configuration to reverse proxy using the following command:
wadm> create-reverse-proxy --user=admin --password-file=admin.pwd --host=serverhost --config=rp --vs=rp --uri-prefix=/ilearn --server=http://rick.india.sun.com:8080
-
Create an instance for the rp configuration.
wadm>create-instance --config=rp <host-name>
-
Modify the
<vs>-obj.conffile, so that the above expression is added to the NameTrans fn="map" directive.
<Object name="reverse-proxy-/ilearn"> NameTrans fn="set-variable" $headers{'Referer'}="http://learning.sun.com/TOI/LEARN.html" Route fn="set-origin-server" server="http://spb-sls-dev.russia.sun.com:7777" </Object>
-
-
Setting up a simple failover scenario for the reverse proxy functionality.
For example, in a setup there are two reverse proxies which proxy to two separate web servers without load balancing. There is a one to one relationship in a normal scenario. However, if one backend server is down the reverse proxy should send request to the other live web server. Modify the obj.conf file as shown below.
<Object name="default"> <If $path =~ '/servlet' or $path =~ '\.jsp'> <If not $restarted> NameTrans fn="map" name="reverse-proxy" from="/" to="http:" </If> <If $restarted> NameTrans fn="map" name="reverse-proxy-alt" from="/" to="http:" </If> </If> </Object> <Object name="reverse-proxy"> Route fn="set-origin-server" server="<back-end-server>" # If back end server is not available, restart the request <If $code =~ 504> Error fn="restart" uri="$uri" </If> </Object> <Object name="reverse-proxy-alt"> Route fn="set-origin-server" server="<alternate-back-end-server>" </Object> <Object ppath="http:*"> Service fn="proxy-retrieve" method="*" </Object>
For every request, the server will first try to reach the first backend server. When this is not available, the request will be sent to the failover server or alternate backend server.
-
Setting up a software load balancer to two web server instances that host dynamic content.
Add server names in the server parameter, separated by a comma (,) and execute the command through CLI.
wadm> create-reverse-proxy --user=admin --password-file=admin.pwd --host=serverhost --config=rp --vs=rp --uri-prefix=// --servers=hostname:port,hostname1:port
-
Configuring timeout value for reverse proxy.
The Web Server 7.0 configured with reverse proxy, returns a gateway timeout error as the backend server takes a long time to respond. You can set the timeout value through CLI as below:
wadm> set-reverse-proxy-prop --user=admin --password-file=admin.pwd --host=serverhost --config=rp --vs=rp--uri-prefix=// --server=http://rick.india.sun.com:8080 timeout=400
See CLI reference, set-reverse-proxy-prop(1).
The default timeout value is 300 seconds. Once the response timeout value is defined, if the connection hangs for more than 400 seconds, the reverse proxy identifies the backend instance offline and closes the connection.
- © 2010, Oracle Corporation and/or its affiliates
