Client Configuration — Web Service Attributes
The Client Configuration web service attributes exposed in the WS Policy Attachment Editor are dependent on the project and the server configuration.
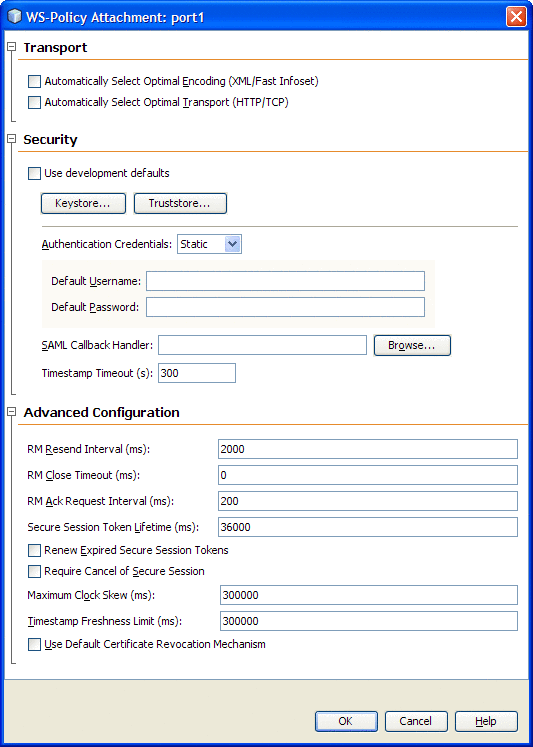
The attributes exposed by the HTTP Binding Component are described in the following table.
|
Attribute |
Description |
Value |
|---|---|---|
|
Transport Settings |
||
|
Automatically Select Optimal Encoding (XML/Fast Infoset) |
Specifies whether to use XML or Fast Infoset encoding. Fast Infoset is a more efficient alternative to XML that uses a binary encoding. If the service is configured to allow Fast Infoset, select this option to use Fast Infoset for faster parsing, faster serializing, and smaller document sizes when compared with equivalent XML documents. |
Select the checkbox to enable. |
|
Automatically Select Optimal Transport (XML/Fast Infoset) |
Specifies whether client runtime checks to see if the service supports TCP. If it does, the client uses TCP transport automatically for service-client communication. TCP provides better performance when sending smaller messages. The performance enhancement is visible mostly in smaller messages because the overhead of sending messages over the HTTP protocol is eliminated. If the service does not support TCP, or if this option is not selected for the client, HTTP is used for transport. |
Select the checkbox to enable. |
|
Security Settings |
||
|
Use development defaults |
Specifies whether to import certificates into the GlassFish Keystore and Truststore so that they can be used immediately for development. The security mechanisms require the use of v3 certificates. The default GlassFish Keystore and Truststore do not contain v3 certificates at this time. In order to use message security mechanisms with GlassFish, it is necessary to obtain Keystore and Truststore files that contain v3 certificates and import the appropriate certificates into the default GlassFish stores. In addition to importing certificates, when this option is selected a default user is created in the file realm with username wsitUser. For a production environment, provide your own certificates and user settings. |
Select the checkbox to enable. |
|
Keystore |
Click the Keystore button to open the Keystore Configuration Editor. The editor specifies the following information:
|
Configure the Keystore from the Keystore Configuration Editor. |
|
Truststore |
Click the Truststore button to open the Truststore Configuration Editor. The editor specifies the following information:
|
Configure the Truststore from the Truststore Configuration Editor. |
|
Authentication Credentials |
Specifies whether the Authentication Credentials are Dynamic or Static. The two proceeding property fields that are associated with Authentication Credentials change, depending on the Authentication Credentials property value. When the value is set as Static, specify the default username and password. Note: The Static option has a risk of exposing the password as a plain text String stored in the WSIT client side configuration. However, when used in the context of GlassFish, this static option has a special utility for embedded web service clients (Example: A servlet or an EJB acting as a web service Client). The Password in this case can be specified as a PlaceHolder by starting the password String start with a "$" character. The WSIT security runtime then makes a SecretKeyCallback passing the password placeholder (minus the "$" character). The actual password is then obtained as a result of the SecretKeyCallback. For more information seeWSIT Security Configuration Demystified |
Dynamic |
|
Username Callback Handleror Username |
Specifies the Username Callback Handler (when the Authentication Credentials value is set as Dynamic). A CallbackHandler is a class that implements a javax.security.auth.callback. For the Username Callback Handler (javax.security.auth.callback.NameCallback), the NameCallback is used to retrieve the Username. This is necessary when the Security Mechanism requires the client to supply a Username and a Password. The CallbackHandler invocation only applies to a Plain J2SE web service client. For more information seeWSIT Security Configuration Demystified |
Username Callback Handler |
|
Specifies the name of an authorized user (when the Authentication Credentials value is set as Static). This option is best used only in the development environment. When the Default Username and Default Password are specified, the username and password are stored in the wsit-client.xml file in clear text, which presents a security risk. Do not use this option for production. |
Username |
|
|
Password Callback Handleror Password |
Specifies the Username Callback Handler (when the Authentication Credentials value is set as Dynamic). For the Password Callback Handler (javax.security.auth.callback.PasswordCallback), the PasswordCallback is used to retrieve the Password. This is necessary when the Security Mechanism requires the client to supply a Username and a Password. The CallbackHandler invocation only applies to a Plain J2SE web service Client. For more information seeWSIT Security Configuration Demystified |
Password Callback Handler |
|
Specifies the password for the authorized user (when the Authentication Credentials value is set as Static). This option is best used only in the development environment. When the Default Username and Default Password are specified, the username and password are stored in the wsit-client.xml file in clear text, which presents a security risk. Do not use this option for production. |
Password |
|
|
SAML Callback Handler |
Specifies the SAML Callback Handler. To use a SAML Callback Handler, you need to create one, as there is no default. A CallbackHandler is a class that implements a javax.security.auth.callback. The SAML Callback Handler (com.sun.xml.wss.impl.callback.SAMLCallback), is necessary when using a Security Mechanism that requires the client to supply a SAMLAssertion, such as a Sender-Vouches or a Holder-of-Key assertion. For more information seeWSIT Security Configuration Demystified |
SAML Callback Handler |
|
Advanced Configuration Settings |
||
|
RM Resend Interval (ms) |
Specifies the time interval (in milliseconds) at which the sender resends unacknowledged messages to the receiver. By default, the resend happens every 2000ms. |
2000 |
|
RM Close Timeout (ms) |
Specifies the interval (in milliseconds) at which the client waits for a close() call to return. If unacknowledged messages are received after this interval is reached, and the call to close has returned, an error is logged regarding the lost messages. |
0 |
|
RM Ack Request Interval (ms) |
Specifies the suggested minimum interval (in milliseconds) that the sender should allow to elapse between Acknowledgement requests to the receiver. |
200 |
|
Secure Session Token Lifetime (ms) |
Specifies the life span of the security session (the interval at which the security session expires). |
36000 |
|
Renew Expired Secure Session Tokens |
Specifies whether expired secure session tokens are renewed. |
Select the checkbox to enable. |
|
Require Cancel of Secure Session |
Specifies whether cancel of secure session is enabled. |
Select the checkbox to enable. |
|
Maximum Clock Skew (ms) |
Specifies the maximum difference allowed between the system clocks of the sender and recipient in milliseconds. |
300000 |
|
Timestamp Freshness Limit (ms) |
Specifies the Timestamp Freshness Limit in milliseconds. Timestamps received with a creation time older than the Timestamp Freshness Limit period are rejected by the receiver. |
300000 |
|
Use Default Certificate Revocation Mechanism |
If this option is selected, the default revocation checking mechanism of the underlying PKIX service provider is used. |
Select the checkbox to enable. |
- © 2010, Oracle Corporation and/or its affiliates
