Chapter 1 Using SPML 1.0 With Sun Identity Manager Web Services
Service Provisioning Markup Language (SPML) 1.0 is an OASIS standard used to provide an open interface for communicating with service provisioning activities. You access SunTM Identity Manager Web Services by using SPML requests for HTTP.
This chapter describes SPML 1.0 support in Sun Identity Manager software (Identity Manager) and Sun Identity Manager Service Provider (Service Provider) and includes information about which features are supported and why, how to configure SPML 1.0 support, and how to extend support in the field.
The information is organized as follows:
Note –
Identity Manager supports both SPML Version 1.0 and Version 2.0. The concepts described in this chapter relate specifically to SPML 1.0. However, this information also provides a good basis for understanding concepts described in Chapter 2, Using SPML 2.0 With Sun Identity Manager Web Services.
Important Notes About Using SPML 1.0
Before you start working with SPML 1.0 and Identity Manager Web Services, note the following:
-
For optimal performance when you are working with the Identity Manager Web Services interfaces, use the OpenSPML Toolkit that is co-packaged with Identity Manager. Using the openspml.jar file from the http://www.openspml.org web site might cause memory leaks.
-
The Service Provider REF Kit contains an SpmlUsage.java file that demonstrates how to use the Service Provider SPML interface.
-
You can access Service Provider features through SPML 1.0. (These features are not available with SPML Version 2.0.)
The Service Provider SPML interface is very similar to the Identity Manager SPML interface. Differences in configuration and operation are noted in this chapter where appropriate.
Configuring SPML
To expose the SPML interface, you must properly configure the Identity Manager server by installing and modifying specific repository objects and by editing the Waveset.properties file.
Instructions for configuring the SPML interface are provided in the following sections:
Installing and Modifying Repository Objects
The following table describes the repository objects that you must install and modify to configure SPML for Identity Manager.
Table 1–1 Repository Objects Used to Configure SPML
Identity Manager includes a sample set of SPML configuration objects in the sample/spml.xml file. You must manually import the sample/spml.xml file because the file is not imported by default when the repository is initialized.
The sample configuration defines a person class to track the evolving standard schema defined by the SPML working group. Do not customize this class. You must keep the person class consistent with the standard schema, except when you are configuring the Service Provider SPML interface.
When configuring the Service Provider SPML interface, you must install and modify the Configuration:SPE SPML configuration object as follows:
-
Configure the person class (the only object class defined by default) to use the Service Provider-specific view handler (IDMXUser).
-
Use the form attribute to define a user form that translates between the SPML request or SPML response and the view.
The form attribute can take a special value (view): in which no form processing is applied to the view. For example, the view is passed directly between the client and Identity Manager.
You access the Service Provider SPML interface from the following (default) path:
/servlet/spespml
For example, if you deploy Identity Manager in the /idm context on host:port, you can access the interface at the following URL:
http://host:port/idm/servlet/spespml
where:
-
host is the machine on which you are running Identity Manager.
-
port is the number of the TCP port on which the server is listening.
Note –
See the SPML 1.0 Specification at http://www.openspml.org for the most current information about the standard SPML schema.
Editing the Waveset.properties File
The following table describes three optional entries in the Waveset.properties file that you can use to control how SPML requests are authorized.
Table 1–2 Optional Entries in Waveset.properties|
Entry Name |
Description |
|---|---|
|
soap.username |
Name of the Identity Manager user who performs SPML requests |
|
soap.password |
Clear text password for the user specified by soap.username |
|
soap.epassword |
Base-64 representation of an encrypted password for the user specified by soap.username |
Editing soap.epassword and soap.password Properties
The user specified in soap.username is known as the proxy user.
You can specify only one password property for the proxy user:
-
Specifying soap.password is the simplest option, but this property exposes a clear text password in the properties file.
-
Specifying soap.epassword is a more secure option, but you must perform extra steps to generate an encrypted password.
Establishing a proxy user is convenient for clients because authentication is not required by the web service. This configuration is common for portal environments where the Identity Manager server is only accessed by other applications that handle user authentication.
Using a proxy user can be dangerous if the HTTP port on which the responding server resides is generally accessible. Anyone who knows the Identity Manager server’s URL and understands how to build SPML requests can configure Identity Manager operations for the proxy user to perform.
The SPML standard does not specify how to perform authentication and authorization. Several related web standards are available for authentication, but these standards are not yet in common use. At this time, the most common approach for authentication is to use the Secure Socket Layer (SSL) between applications and the server. Identity Manager does not dictate how to configure SSL.
If you cannot use a proxy user or SSL, Identity Manager supports a vendor-specific extension to SPML that allows the client to log in and maintain a session token, which can be used to authenticate subsequent requests. You can use the LighthouseClient class (an extension of the SpmlClient class that includes support for specifying credentials) to perform a login request and pass a session token in all SPML requests.
Note –
The Service Provider SPML interface does not support authentication and authorization. However, you can configure the Identity Manager SPML interface to use the IDMXUser view instead of using Service Provider SPML.
Service Provider assumes that clients accessing Identity Manager have been authenticated and authorized by an access management application. The client has all possible rights when using the Service Provider SPML interface.
To prevent sensitive data from being exposed between the client and Identity Manager, consider accessing the Service Provider SPML interface over SSL.
Creating an Encrypted Password
Use one of the following methods to create an encrypted password:
-
Open the Identity Manager console and use the encrypt command.
-
Open the Identity Manager Debug pages or console and view the XML for the proxy user. Find the WSUser element for the password attribute value and use that value for the soap.epassword property.
Note –To access the Debug pages, open the Identity Manager Administrator interface and type the following URL:
http://host:port/idm/debug
where host is the local server where Identity Manager is running, and port is the TCP port on which the server is listening.
Editing Configuration Objects
Applications require a mechanism to send SPML messages and to receive SPML responses.
To configure SPML for Identity Manager, you must edit the following configuration objects:
Note –
The Service Provider SPML interface has only one configuration object, Configuration:SPE SPML, which is similar to the Configuration:SPML object in structure.
Configuration: SPML Object
The Configuration: SPML object contains definitions for the SPML schemas that you want to expose, and information about how those SPML schemas are mapped into Identity Manager views. This information is represented by using a GenericObject that is stored as an extension of the configuration object.
The following attributes are defined in GenericObject: schemas and classes:
-
Schemas. A list of strings, where each string contains the escaped XML for one SPML <schema> element. Because the SPML elements are not defined in the waveset.dtd, you cannot directly include them in an Identity Manager XML document. Instead, you must include them as escaped text.
-
Classes. A list of objects containing information about the supported SPML classes and how those classes are mapped into views. Define one object from this list for each class defined by the SPML schemas on the schemas list.
Initially, the distinction between the two lists might be confusing. The information in the schemas list defines what Identity Manager returns in response to an SPML SchemaRequest message. The client uses this information to decide which attributes can be included in other messages such as AddRequest. Identity Manager does not care about the contents of the schemas list. This list is simply returned verbatim to the client.
You are not required to define SPML schemas. Identity Manager works without schemas. If you do not define an SPML schema, Identity Manager returns an empty response after receiving a schema request message. Without a schema, clients must rely on pre-existing knowledge about the supported classes and attributes.
Best Practice:
Writing SPML schemas is considered a best practice, because it enables you to use general purpose tools (such as the OpenSPML Browser) to build requests.
Default SPML Configuration
The following example shows the default SPML configuration. The text of the SPML schema definitions have been omitted for brevity.
Example 1–1 Default SPML Configuration
<Configuration name='SPML' authType='SPML'>
<Extension>
<Object>
<Attribute name='classes'>
<List>
<Object name='person'>
<Attribute name='type' value='User'/>
<Attribute name='form' value='SPMLPerson'/>
<Attribute name='default' value='true'/>
<Attribute name='identifier' value='uid'/>
</Object>
<!-- Class 'user' defines no form so we'll default to a builtin
simplified schema. I don't really like this but SimpleRpc currently depends on it.
-->
<Object name='user'>
<Attribute name='type' value='User'/>
<Attribute name='identifier' value='waveset.accountId'/>
</Object>
<!-- Class 'userview' defines the form "view" which causes the view
to pass through unmodified--> <Object name='userview'>
<Attribute name='type' value='User'/>
<Attribute name='form' value='view'/>
<Attribute name='identifier' value='waveset.accountId'/>
<Attribute name='multiValuedAttributes'>
<List>
<String>waveset.resources</String>
<String>waveset.roles</String>
<String>waveset.applications</String>
</List>
</Attribute>
</Object>
<Object name='role'>
<Attribute name='type' value='Role'/>
<Attribute name='form' value='SPMLRole'/>
<Attribute name='default' value='true'/>
<Attribute name='identifier' value='name'/> <!-- attribute ...for now? -->
</Object>
</Configuration>
Two classes are defined in this example:
-
The standard person class
-
An Identity Manager extension named request
The following attributes are supported in a class definition:
-
name – Identifies the class name. The name value can correspond to an <ObjectClassDefinition> element in an SPML schema, although this value is not required. You can use this name as the value for the objectclass attribute in an AddRequest or a SearchRequest.
-
type – Defines the Identity Manager view type used to manage instances of this class. Generally, this attribute is User, but it can be any repository type that is accessible through a view. For information about views, see Sun Identity Manager Deployment Reference.
-
form – Identifies the name of a configuration object containing a form. This attribute contains the rules for transforming between the external attributes defined by the class and the internal view attributes.
-
default – Specify true to indicate that this attribute is the default class for this type only. For more than one SPML class implemented on the same type, you must designate one class as the default.
-
identifier – Each class typically defines one attribute as the object identity. The identifier attribute in the class definition specifies which attribute represents the identity. Where possible, use the identifier attribute value as the name of the corresponding repository object you create to represent the instance.
-
filter – When evaluating an SPML search request for a class, you typically include all repository objects associated with that class in that search. This approach is fine for User objects, but some classes might be implemented by using generic types such as TaskDefinition or Configuration, not all of which are considered instances of the SPML class.
To prevent unwanted objects from being included in the search, you can specify the filter attribute. The value is expected to be an <AttributeCondition> element or a <List> of <AttributeCondition> elements. Because custom classes are typically created for the User type, using a filter is uncommon. The default configuration uses filters to expose a subset of the TaskInstance objects that are known to have been created to handle asynchronous SPML requests.
Default Schemas
The schemas attribute contains a list of strings that contain the escaped XML for an SPML <schema> element. If you examine the spml.xml file, note that the schema elements are surrounded by a CDATA-marked section. Using CDATA-marked sections is convenient for escaping long strings of XML. When Identity Manager normalizes the spml.xml file, the CDATA-marked sections are converted into strings containing < and > character entities.
The default SPML configuration includes two schemas:
-
A standard schema that is being defined by the SPML working group.
-
A custom schema that is defined by Identity Manager. Do not customize these schemas.
The Identity Manager schema contains a class definition for request and various extended requests for common account management operations.
Configuration: SPMLPerson Object
Each class defined in the Configuration:SPML object typically has an associated form object containing the rules for transforming between the external attribute model defined by the class and the internal model defined by the associated view.
The following example shows how the standard person class references a form.
Example 1–2 Standard Person Class Referencing a Form
<Configuration name='SPMLPerson'>
<Extension>
<Form>
<Field name='cn'>
<Derivation><ref>global.fullname</ref></Derivation>
</Field>
<Field name='global.fullname'>
<Expansion><ref>cn</ref></Expansion>
</Field>
<Field name='email'>
<Derivation><ref>global.email</ref></Derivation>
</Field>
<Field name='global.email'>
<Expansion><ref>email</ref></Expansion>
</Field>
<Field name='description'>
<Derivation>
<ref>accounts[Lighthouse].description</ref>
</Derivation>
</Field>
<Field name='accounts[Lighthouse].description'>
<Expansion><ref>description</ref></Expansion>
</Field>
<Field name='password'>
<Derivation><ref>password.password</ref></Derivation>
</Field>
<Field name='password.password'>
<Expansion><ref>password</ref></Expansion>
</Field>
<Field name='sn'>
<Derivation><ref>global.lastname</ref></Derivation>
</Field>
<Field name='global.lastname'>
<Expansion><ref>sn</ref></Expansion>
</Field>
<Field name='gn'>
<Derivation><ref>global.firstname</ref></Derivation>
</Field>
<Field name='global.firstname'>
<Expansion><ref>gn</ref></Expansion>
</Field>
<Field name='telephone'>
<Derivation>
<ref>accounts[Lighthouse].telephone</ref>
</Derivation>
</Field>
<Field name='accounts[Lighthouse].telephone'>
<Expansion><ref>telephone</ref></Expansion>
</Field>
</Form>
</Extension>
</Configuration>
|
SPML class forms
-
Contain no <Display> elements
-
Are only defined for data transformation
-
Are not intended for interactive editing
Each attribute in a class definition contains two field definitions:
-
One field uses a <Derivation> expression to transform the internal view attribute name to the external name.
-
One field uses an <Expansion> expression to transform the external name to the internal name.
The form is processed in such a way that when attributes are returned to the client, only the result of the <Derivation> expressions are included. When attributes are being sent from the client to the server, only <Expansion> expression results are assimilated back into the view. The effect is similar to the schema map of a Resource definition.
Configuration: IDM Schema Configuration Object
If you want to use attributes in an SPML search filter, you must define those attributes as extended attributes for Identity Manager users. Identity Manager stores extended attribute values in the repository, even when that value is also stored as a resource account attribute.
Try to minimize the use of extended attributes. Too many extended attributes can increase the repository size and might cause consistency problems between attributes stored in Identity Manager and the real value of the attribute stored on a resource. To use an attribute in an Identity Manager query, you must declare the attribute as an extended attribute to ensure that the value is accessible when the repository query indexes are built.
To include attributes in a user’s set of summary attributes, you must define those attributes as extended attributes. You can use summary attributes to optimize searches by avoiding deserialization of the object XML, and instead return only a few of the most important user attributes. In the Identity Manager SPML implementation, summary attributes are returned when you do not explicitly provide a list of return attributes in the search request.
In the following example, firstname, lastname, fullname, description, and telephone are extended attributes that are present on the User IDMObjectClassConfiguration after being defined in IDMAttributeConfigurations. Only firstname, lastname, and telephone are queryable and summary attributes.
Example 1–3 telephone and description Declared as Extended Attributes
<Configuration name="IDM Schema Configuration"
id=’#ID#Configuration:IDM_Schema_Configuration’
authType=’IDMSchemaConfig’>
<IDMSchemaConfiguration>
<IDMAttributeConfigurations>
<!-- this is the standard set -->
<IDMAttributeConfiguration name=’firstname’
syntax=’STRING’/>
<IDMAttributeConfiguration name=’lastname’
syntax=’STRING’/>
<IDMAttributeConfiguration name=’fullname’
syntax=’STRING’/>
<!-- these are the SPML extensions -->
<IDMAttributeConfiguration name=’description’
syntax=’STRING’/>
<IDMAttributeConfiguration name=’telephone’
syntax=’STRING’/>
</IDMAttributeConfigurations>
<IDMObjectClassConfigurations>
<IDMObjectClassConfiguration name=’User’
extends=’Principal’
description=’User description’>
<IDMObjectClassAttributeConfiguration name=’firstname’
queryable=’true’
summary=’true’/>
<IDMObjectClassAttributeConfiguration name=’lastname’
queryable=’true’
summary=’true’/>
<IDMObjectClassAttributeConfiguration name=’fullname’/>
<IDMObjectClassAttributeConfiguration name=’description’/>
<IDMObjectClassAttributeConfiguration name=’telephone’
queryable=’true’
summary=’true’/>
</IDMObjectClassConfiguration>
</IDMObjectClassConfigurations>
</IDMSchemaConfiguration>
</Configuration>
|
You can customize the list of attributes according to the needs of your site.
The names you choose for extended attributes depend on the mappings performed in the class form. Because the default SPMLPerson form maps sn into lastname, you must declare the extended attribute as lastname. The form does not transform the name of telephone or description, so the extended attribute name comes directly from the SPML schema.
Beyond declaring extended attributes, you must also modify the same Configuration: object to declare which of the attributes are queryable, or usable in an SPML filter, and which attributes are summary attributes to be returned by an optimized search result.
TaskDefinition: SPMLRequest Object
The spml.xml file also includes a brief definition for a new system task named SpmlRequest. You can use this task to implement asynchronous SPML requests. When the server receives an asynchronous request, it launches a new instance of this task and passes the SPML message as an input variable for the task. The server then returns the task instance repository ID in the SPML response for later status requests. For example:
<TaskDefinition name=’SPMLRequest’ executor=’com.waveset.rpc.SpmlExecutor’ execMode=’asyncImmediate’ resultLimit=’86400’> </TaskDefinition> |
Do not change the definition name, the executor name, or the execution mode. You can change the resultLimit value. When asynchronous requests have completed, the system typically retains the result value for a specified time so the client can issue an SPML status request to obtain the results. How long to retain these results is site-specific.
Use a positive resultLimit value to specify how long (in seconds) the system can retain results after completing a task. The default value for SPMLRequest is typically 3600 seconds or approximately one hour. Other tasks default to 0 seconds unless you change the task name to a different value.
If negative, the request instance is never removed automatically.
Tip –
To avoid cluttering the repository, set the resultLimit value to the shortest possible time.
Note –
The Service Provider SPML interface does not support asynchronous requests.
Deployment Descriptor
You must edit the Identity Manager deployment descriptor, typically found in the WEB-INF/web.xml file, to contain a declaration for the servlet that receives SPML requests.
If you are having difficulty contacting the SPML web service, look in the web.xml file for a servlet declaration. The following example shows a servlet declaration.
Example 1–4 Servlet Declaration
<servlet>
<servlet-name>rpcrouter2</servlet-name>
<display-name>OpenSPML SOAP Router</display-name>
<description>no description</description>
<servlet-class>
org.openspml.server.SOAPRouter
</servlet-class>
<init-param>
<param-name>handlers</param-name>
<param-value>com.waveset.rpc.SimpleRpcHandler</param-value>
</init-param>
<init-param>
<param-name>spmlHandler</param-name>
<param-value>com.waveset.rpc.SpmlHandler</param-value>
</init-param>
<init-param>
<param-name>rpcHandler</param-name>
<param-value>com.waveset.rpc.RemoteSessionHandler</param-value>
</init-param>
</servlet>
|
This declaration allows you to access addRequest, modifyRequest, and searchRequest web services through the URL:
http://<host>:<port>/idm/servlet/rpcrouter2
where
-
host is the machine on which you are running Identity Manager.
-
port is the number of the TCP port on which the server is listening.
Although you can, you are not required to define a servlet-mapping. Do not modify the contents of this servlet declaration.
Starting the OpenSPML Browser
You can use the OpenSPML Browser application to test your Identity Manager SPML configuration.
 To Start the OpenSPML Browser
To Start the OpenSPML Browser
Connecting to the Identity Manager Server
 To Connect to the Identity Manager Server
To Connect to the Identity Manager Server
-
Open the OpenSPML browser and click the Connect tab.
Figure 1–1 Example OpenSPML Browser
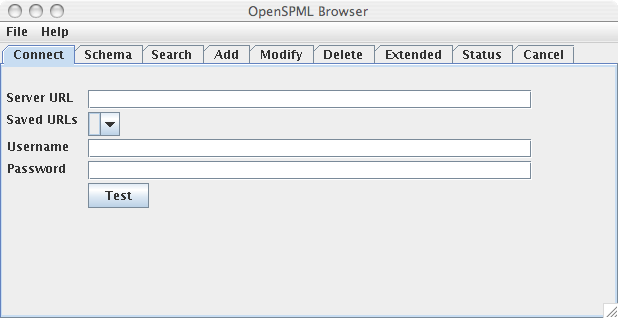
-
Type the URL of the Identity Manager server into the Server URL field.
For example, if the server is running on port 8080 on a local machine, the URL would be http://host:8080/idm/servlet/rpcrouter2.
Testing Your SPML Configuration
After connecting to the OpenSPML browser, use the following procedure to test your configuration.
 To Test Your SPML Configuration
To Test Your SPML Configuration
-
If necessary, click the Connect tab and click Test.
A dialog displays to indicate that the connection was successful.
-
Click the Schema tab and click Submit.
The system displays a hierarchical view of the schemas supported by the Identity Manager server.
Troubleshooting
If you cannot establish a successful connection, do the following:
-
Verify that you typed the URL correctly.
-
If the error message you receive contains phrases such as “no response” or “connection refused,” the problem is most likely the host or port used in the connection URL.
-
If the error message suggests that a connection was made, but the web application or servlet could not be located, the problem is most likely in the WEB-INF/web.xml file. See Deployment Descriptor for more information.
Developing SPML Applications
After configuring the server, your SPML application requires a mechanism for sending SPML messages and receiving SPML responses. For JavaTM applications, use the OpenSPML Toolkit to configure this mechanism.
Note –
For optimal performance when you are working with the Identity Manager Web Service Interfaces, use the OpenSPML Toolkit that is co-packaged with Identity Manager.
Using the openspml.jar file from the http://www.openspml.org/ web site might cause memory leaks.
The OpenSPML Toolkit provides the following components:
-
Java class model for SPML messages
-
Classes to send and receive messages on the client
-
Classes to receive and process requests on the server
The following table describes the most important classes provided by the toolkit. Each request type has a corresponding class. Consult the JavadocTM tool distributed with the toolkit for complete information.
Table 1–3 Classes Provided by the OpenSPML Toolkit|
Class |
Description |
|---|---|
|
AddRequest |
Constructs a message to request creation of a new object. You define the object type by passing an objectclass attribute. Other passed attributes must adhere to the schema associated with the object class. SPML does not yet define standard schemas, but you can configure Identity Manager to support almost all schemas. |
|
BatchRequest |
Constructs a message that can contain more than one SPML request. |
|
CancelRequest |
Constructs a message to cancel a request that was formerly executed asynchronously. |
|
DeleteRequest |
Constructs a message to request the deletion of an object. |
|
ModifyRequest |
Constructs a message to request modification of an object. Include only those attributes that you want to modify in the request. Attributes omitted from the request will retain their current values. |
|
SchemaRequest |
Constructs a message to request information about SPML object classes supported by the server. |
|
SearchRequest |
Constructs a message to request object attributes that match certain criteria. |
|
SpmlClient |
Presents a simple interface for sending and receiving SPML messages. |
|
SpmlResponse |
Includes the base class for objects representing response messages sent back from the server. Each request class has a corresponding response class, for example, AddResponse and ModifyResponse. |
|
StatusRequest |
Constructs a message to request the status of a request that was formerly executed asynchronously. |
The Service Provider REF Kit contains an SpmlUsage.java file that demonstrates how to use the Service Provider SPML interface. This REF Kit also contains an ant script that compiles the SpmlUsage class.
Usage:
java [ -Dtrace=true ] com.sun.idm.idmx.example.SpmlUsage [ URL ]
where URL points to the Service Provider SPML interface. The URL defaults to
http://host:port/idm/spespml
where
-
host is the machine on which you are running Identity Manager Service Provider.
-
port is the number of the TCP port on which the server is listening.
You can enable trace for Service Provider to print Service Provider SPML messages to standard output.
ExtendedRequest Examples
The following table describes the different ExtendedRequest classes that you can use to send messages to and receive messages from the client.
Table 1–4 ExtendedRequest Classes for Sending and Receiving Messages|
ExtendedRequest Class |
Description |
|---|---|
|
changeUserPassword |
Constructs a message to request a user password change. |
|
deleteUser |
Constructs a message to request a user deletion. |
|
disableUser |
Constructs a message to request the disabling of a user. |
|
enableUser |
Constructs a message to request the enabling of a user. |
|
launchProcess |
Constructs a message to request the launch of a process. |
|
listResourceobjects |
Constructs a message to request the name of a resource object in the Identity Manager repository, and the type of object supported by that resource. The request returns a list of names. |
|
resetUserPassword |
Constructs a message to request the reset of a user password. |
|
runForm |
Allows you to create custom SPML requests that return information obtained by calling the Identity Manager Session API. |
The server code converts each ExtendedRequest into a view operation.
The following examples illustrate the typical formats for an ExtendedRequest and its classes:
ExtendedRequest Example
The following example shows the typical format for an ExtendedRequest.
Example 1–5 ExtendedRequest Format
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("changeUserPassword");
req.setAttribute("accountId", "exampleuser");
req.setAttribute("password", "xyzzy");
req.setAttribute("accounts","Lighthouse,LDAP,RACF");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
Most SPML ExtendedRequest requests accept the following arguments:
-
accountId – Identifies the Identity Manager user name.
-
accounts – Presents resource names in a comma-delimited list.
-
If you pass an accounts argument, the specified SPML operation only updates the specified resources. You must include the Lighthouse attribute in a non-null accounts list if you want to update the Identity Manager user in addition to specific resource accounts.
-
If you do not pass an accounts argument, the operation updates all resource accounts linked to the user, including the Identity Manager user account.
-
deleteUser Example
The following example shows the typical format for a deleteUser request (View -> Deprovision view).
Note –
If you customize this request, there might be side effects.
Example 1–6 deleteUser Request
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("deleteUser");
req.setAttribute("accountId","exampleuser");
req.setAttribute("accounts","Lighthouse,LDAP,RACF");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
disableUser Example
The following example shows the typical format for a disableUser request (View -> Disable view).
Example 1–7 disableUser Request
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("disableUser");
req.setAttribute("accountId","exampleuser");
req.setAttribute("accounts","Lighthouse,LDAP,RACF");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
enableUser Example
The following example shows the typical format for an enableUser request (View -> Enable view).
Example 1–8 enableUser Request
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("enableUser");
req.setAttribute("accountId","exampleuser");
req.setAttribute("accounts","Lighthouse,LDAP,RACF");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
launchProcess Example
The following example shows the typical format for a launchProcess request (View -> Process view).
Example 1–9 launchProcess Request
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("launchProcess");
req.setAttribute("process", "my custom process");
req.setAttribute("taskName", "my task instance");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
where:
-
launchProcess – Starts the custom processes.
-
process – Name of the TaskDefinition object in the Identity Manager repository to start.
-
taskName – Name of the task needed to start the workflow.
The task instance object holds the runtime state of the process.
The remaining attributes are arbitrary and they are passed into the task.
listResourceObjects Example
The following example shows the typical format for a listResourceObjects request.
Example 1–10 listResourceObjects Request
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("listResourceObjects");
req.setAttribute("resource", "LDAP");
req.setAttribute("type", "group");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
where:
-
resource – Specifies the name of a resource object in the Identity Manager repository.
-
type – Specifies the object type supported by that resource.
resetUserPassword Example
The following example shows the typical format for a resetUserPassword request (View -> Reset User Password view).
Example 1–11 resetUserPassword Request
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("resetUserPassword");
req.setAttribute("accountId","exampleuser");
req.setAttribute("accounts","Lighthouse,LDAP,RACF");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
runForm Example
The following example shows the typical format for a runForm request.
Example 1–12 runForm Request
ExtendedRequest req = new ExtendedRequest();
req.setOperationIdentifier("runForm");
req.setAttribute("form", "SPML Get Object Names");
ExtendedResponse res = (ExtendedResponse) client.send(req);
|
where form is the name of a configuration object containing a form.
Example Query Form
The following example shows a form that is used to run queries and return a list of the Role, Resource, and Organization names accessible to the current user.
Example 1–13 Query Form
<Configuration name='SPML Get Object Names'>
<Extension>
<Form>
<Field name='roles'>
<Derivation>
<invoke class='com.waveset.ui.FormUtil'>
<ref>display.session</ref>
<s>Role</s>
</invoke>
</Derivation>
</Field>
<Field name='resources'>
<Derivation>
<invoke class='com.waveset.ui.FormUtil'>
<ref>display.session</ref>
<s>Resource</s>
</invoke>
</Derivation>
</Field>
<Field name='organizations'>
<Derivation>
<invoke class='com.waveset.ui.FormUtil'>
<ref>display.session</ref>
<s>ObjectGroup</s>
</invoke>
</Derivation>
</Field>
</Form>
</Extension>
</Configuration>
|
You use the runForm request to create custom SPML requests that return information obtained by calling the Identity Manager Session API. For example, when configuring a user interface for editing user accounts, you might want to provide a selector that displays the names of the organizations, roles, resources, and policies that can be assigned to a user.
You can configure the SPML interface to expose these objects as SPML object classes and use searchRequest to query for their names. However, this configuration requires four searchRequest requests to gather the information. To reduce the number of SPML requests, encode the queries in a form by using a single runForm request to perform the queries and return the combined results.
Using Trace With SPML
SPML includes options for turning on trace output so you can log Identity Manager SPML traffic and diagnose problems.
For more information about tracing SPML, see Chapter 5, Tracing and Troubleshooting, in Sun Identity Manager 8.1 System Administrator’s Guide.
Example Methods for Implementing SPML
The following examples illustrate some common methods for implementing SPML.
AddRequest Method
The following example shows a typical AddRequest method.
Example 1–14 AddRequest Example
SpmlClient client = new SpmlClient();
client.setURL("http://example.com:8080/idm/spml");
AddRequest req = new AddRequest();
req.setObjectClass("person");
req.setIdentifier("maurelius");
req.setAttribute("gn", "Marcus");
req.setAttribute("sn", "Aurelius");
req.setAttribute("email", "maurelius@example.com");
SpmlResponse res = client.request(req);
if (res.getResult() .equals(SpmlResponse.RESULT_SUCCESS))
System.out.println("Person was successfully created");
|
ModifyRequest Method
This section contains two authenticated SPML ModifyRequest examples.
Example 1–15 Authenticated SPML Request Example
SpmlClient client = new SpmlClient();
client.setURL("http://example.com:8080/idm/spml");
ModifyRequest req = new ModifyRequest();
req.setIdentifier("maurelius");
req.addModification("email", "marcus.aurelius@example.com");
SpmlResponse res = client.request(req);
if (res.getResult() .equals(SpmlResponse.RESULT_SUCCESS))
System.out.println("Person was successfully modified");
Example 1–16 Authenticated SPML Request Example With LighthouseClient
LighthouseClient client = new LighthouseClient();
client.setURL("http://example.com:8080/idm/spml");
client.setUser("maurelius");
client.setPassword("xyzzy");
ModifyRequest req = new ModifyRequest();
req.setIdentifier("maurelius");
req.addModification("email", "marcus.aurelius@example.com");
SpmlResponse res = client.request(req);
if (res.getResult() .equals(SpmlResponse.RESULT_SUCCESS))
System.out.println("Person was successfully modified");
The only difference between these examples is that the second example uses the LighthouseClient class and two additional method calls to client.setUser and client.setPassword. For example, you could use this example to avoid setting a proxy user in Waveset.properties, which results in the audit log reflecting the specified user instead of the proxy user.
This example is authenticated by client.setUser and client.setPassword when the request is sent.
SearchRequest Method
The following example shows a typical SearchRequest method.
Example 1–17 SearchRequest Example
SpmlClient client = new SpmlClient();
client.setURL("http://example.com:8080/idm/spml");
SearchRequst req = new SearchRequest();
// specify the attributes to return
req.addAttribute("sn");
req.addAttribute("email");
// specify the filter
FilterTerm ft = new FilterTerm();
ft.setOperation(FilterTerm.OP_EQUAL);
ft.setName("gn");
ft.setValue("Jeff");
req.addFilter(ft);
SearchResponse res = (SearchResponse)client.request(req);
// display the results
List results = res.getResults();
if (results != null) {
for (int i = 0 ; i < results.size() ; i++) {
SearchResult sr = (SearchResult)results.get(i);
System.out.println("Identifier=" +
sr.getIdentifierString() +
" sn=" +
sr.getAttribute("sn") +
" email=" +
sr.getAttribute("email"));
}
}
- © 2010, Oracle Corporation and/or its affiliates
