Determining the Architecture
Service Provider may be deployed in either a one-tier or two-tier architecture. The following sections describe both of these architectures.
All implementations require a relational database for storing transaction information. There are no specific requirements for the database, or its host, other than it must be able to connect to Service Provider with JDBC. See the release notes for a list of supported databases.
Service Provider uses transactions to encapsulate provisioning work. (Workflows are not implemented in this product, but callouts are available.) Transactions include resource operations as well as updates to meta-data in a user’s entry in the master directory. The transaction manager, which executes these transactions, is configurable from the Identity Manager Administrator Interface. Configuration options include whether to process transactions synchronously, and when and how often to persist transactions. Transactions are stored in a database, and are tracked to completion through resource or server failures.
Service Provider requires an LDAP directory to query and provision user accounts. LDAP user account information is not stored in an Identity Manager repository. However, information stored in an LDAP directory may be provisioned to other accounts on other resources.
One-Tier Architecture
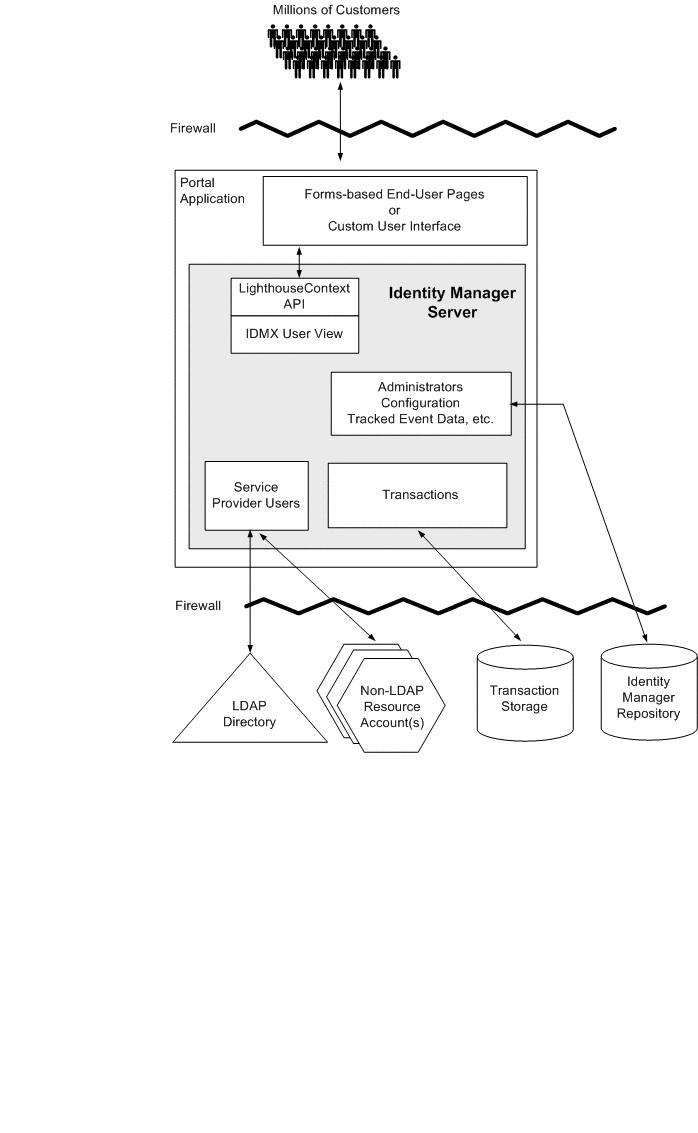
In a one-tier architecture, Service Provider and the user interface are installed on the same application server (or servers). This option is less secure, because the web server must have access to the internal databases and resources. The following diagram illustrates Service Provider in a one-tier environment.
Figure 2–1 Service Provider in a One-Tier Architecture
Two-Tier Architecture
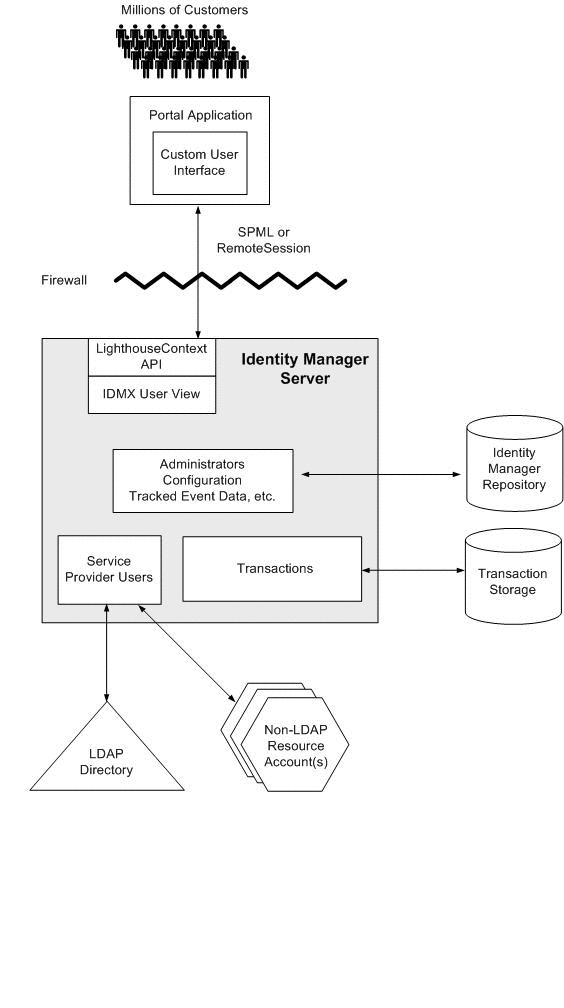
In a two-tier architecture, the portal is in a demilitarized zone (DMZ), while Service Provider remains secure within the enterprise. The portal accesses Service Provider over SPML or with a RemoteContext.
Implementing a two-tier architecture means you must take additional security precautions. It is recommended that you perform the following steps to secure your network:
-
Install a firewall between the portal server and the Service Provider server.
-
Use either HTTPS or HTTP in conjunction with SSL for communications between the servers. This is especially true if Service Provider resides in an untrusted domain.
-
Restrict the IP addresses that the portal server and Service Provider server can use to communicate.
The following diagram illustrates how Service Provider can be implemented in a two-tier architecture.
Figure 2–2 Two-Tier Architecture with a Custom User Interface
- © 2010, Oracle Corporation and/or its affiliates
