Chapter 2 Product Architecture
This chapter provides an overview of the SunTM Identity Manager product architecture.
It includes the following topics:
-
Understanding the System Separation and Physical Proximity Guidelines
-
Understanding Identity Manager Service Provider System Architecture
Understanding Identity Manager Components
Identity Manager is a Java 2 Platform, Enterprise Edition (J2EETM platform) web application. The J2EE platform consists of a set of industry-standard services, APIs, and protocols that provide the functionality for developing multitiered, web-based, enterprise applications.
The Identity Manager system architecture is distributed across four logical tiers:
-
The user tier
-
The application tier
-
The database tier
-
The managed resources tier
Each tier is discussed in the following sections, starting with the application tier.
Figure 2–1 Identity Manager System Architecture
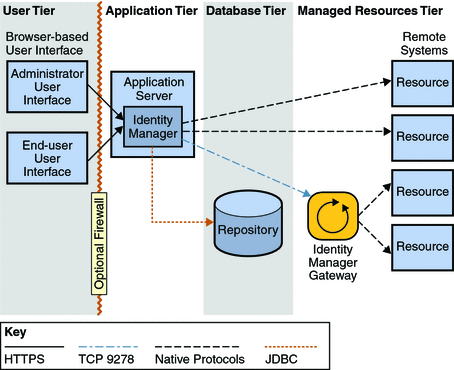
Understanding the Application Tier
Identity Manager (also known as the Identity Manager server) is installed in a J2EE web container inside an application server. Identity Manager server consists of JSPTM files, HTML, images, and JavaTM classes. Adapters and connectors, which interface with other IT systems (also known as resources), are also located in Identity Manager on the application server.
Note –
See Application Servers in Sun Identity Manager 8.1 Release Notes for a list of supported application servers.
Because Identity Manager is a web application, the user interface resides on the application server and pages are served to the user tier on a request-by-request basis.
Installing Identity Manager on the application server is straightforward: A graphical, wizard-based installer is provided, and, on UNIX® systems, a command-line installer is also available. The application server must have a bundled or installed Java Development Kit (JDKTM) to run the Java classes that perform actions within Identity Manager.
Understanding the Database Tier
Identity Manager stores all of its provisioning and state information in the Identity Manager repository. The repository is comprised of tables that store all the configuration data about Identity Manager. It is a single point for Identity Manager to look up data and lock objects. The repository also contains an audit log, which is a history of actions taken in Identity Manager. Identity Manager data is stored as XML. The repository can reside in local files or a relational database, although in production, a relational database is required.
Note –
See Repository Database Servers in Sun Identity Manager 8.1 Release Notes for a list of supported database servers.
Note that, beyond a minimal amount of identity information about individual users, user data is not kept in Identity Manager. Instead, only those attributes that are needed to identify and differentiate users within Identity Manager (for example, name and email address) are saved in the repository.
Identity Manager can connect to the repository over a direct JDBC connection, or it can use data source functionality made available by your application server.
The Identity Manager Service Provider feature requires an additional LDAP repository for storing user information. See Understanding Identity Manager Service Provider System Architecture for details.
Understanding the Managed Resource Tier
The managed resource tier consists of the applications and IT systems to which you provision and deprovision user accounts. It includes the Identity Manager Gateway, which is a helper application that allows Identity Manager to interact with certain resources.
Adapters and connectors provide user management functions, including creating, updating, deleting, and reading user accounts, and performing password change management functionality. Adapters and connectors can also extract account information from a remote system.
Note –
In most cases, Identity Manager manages user data on the remote system and does not maintain it in its own data store.
Some common resources that require the use of the Sun Identity Manager Gateway include Microsoft Exchange, Windows Active Directory, Novell eDirectory (formerly Netware Directory Services), Lotus Domino, and several others. (See Sun Identity Manager Gateway in Sun Identity Manager 8.1 Release Notes for a complete list.) The Gateway installs as a service in Windows and communicates with Identity Manager using TCP port 9278. Communication is initiated from Identity Manager using a proprietary encrypted protocol. The Gateway then interfaces with managed resources using the resources native protocols.
From an installation perspective, there are two type of adapters and connectors: Identity Manager adapters and connectors and custom adapters and connectors. Identity Manager adapters and connectors are pre-installed in Identity Manager. Custom adapters and connectors, however, need to be copied to a designated directory in the Identity Manager installation directory located on the application server.
Custom adapters are easy to create using the Identity Manager Resource Extension Facility (REF) kit. The REF kit provides the API and a number of template adapters that companies can use to jump start the development process. Simple resource functionality can be achieved by implementing only eight Java methods.
Understanding the User Tier
The user tier consists of administrators and end users who interact with Identity Manager through one of the user interfaces. The main user interface for the product is a web browser, which communicates with Identity Manager over HTTPS. The two browser-based UIs, the administrator user interface and the end-user interface, primarily consist of HTML pages, although some features may use Java applets.
For clarity, only the administrator user interface and the end-user user interface are shown in figure Figure 2–1. Other user interfaces, however, are also located in the user tier. These include the IVR telephone interface, the Identity Manager IDE, the SPML web services interface, and the Identity Manager console.
Understanding the System Separation and Physical Proximity Guidelines
This section contains basic guidelines on what Identity Manager components should run on what servers. It also contains recommendations on which components should be physically sited near one another in order to minimize performance issues that could arise due to latency and network congestion.
Note –
Only basic guidelines are provided. For information on designing a high-availability Identity Manager architecture, see Chapter 3, Clustering and High Availability.
In a development environment, the application server and database can reside on the same machine. In testing and production environments, however, each Identity Manager instance should be installed on its own dedicated server. The relational database also requires a dedicated server.
The Identity Manager Gateway, if required, must be installed on one or more Windows machines. The Gateway is a lightweight component and does not require a dedicated server. All Windows domains managed by a Gateway must be part of the same forest. Managing domains across forest boundaries is unsupported. If you have multiple forests, install at least one Gateway in each forest. In production the Gateway must be made highly available. See Making the Gateway Highly Available for details.
In a production environment, the highest amount of network traffic occurs between the database and application servers. These two environments must be on the same LAN with the shortest network hop possible. Gateway instances, as well as managed resources, do not need to be on the same network as Identity Manager.
If Identity Manager will be used for external users in a Service Provider configuration, a set of web servers should be setup in a DMZ. See Understanding the Recommended Service Provider HA Architecture for details.
Understanding SPML and the Web Services System Architecture
Service Provisioning Markup Language (SPML) and Identity Manager Web Services can be used to implement a custom front-end for Identity Manager. Identity Manager sends and receives SPML messages and responses using the HTTPS protocol.
For more information about SPML and Web Services, see Sun Identity Manager 8.1 Web Services.
Understanding Identity Manager Service Provider System Architecture
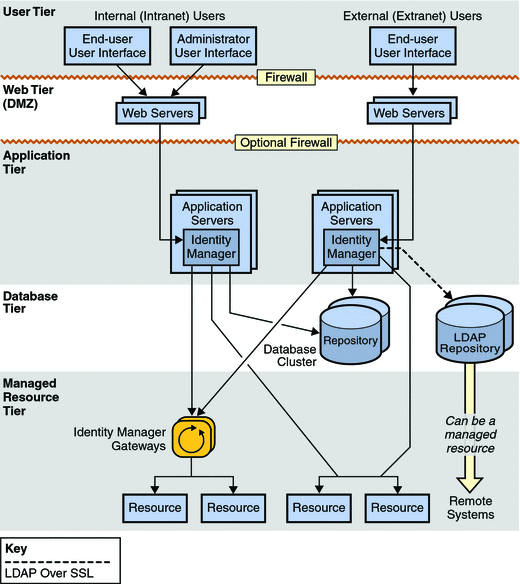
If the Identity Manager Service Provider feature is implemented, a fifth tier is required. This tier is called the Web tier and it consists of one or more web servers located in a DMZ. No Identity Manager components are installed in the web tier. Instead, the web servers in the DMZ support one or more application servers in the application tier by responding to web page requests. Adding one or more web servers to the web tier provides enhanced scalability, and placing the web servers in a DMZ provides better network security.
The Service Provider feature also requires an LDAP repository. This repository resides in the database tier. Because the LDAP repository can be a managed resource, the LDAP server can be understood as residing in the managed resource tier, as well.
Note –
In a service-provider-only implementation, an Identity Manager repository is recommended in addition to the LDAP repository, but it is not required. If an Identity Manager repository is not deployed, some functionality such as certain reporting capabilities will not be available.
Figure 2–2 Identity Manager Service Provider System Architecture
- © 2010, Oracle Corporation and/or its affiliates
