Managing Server Encryption
The Identity Manager server encryption feature allows you to create new 3DES server encryption keys and encrypt these keys by using 3DES, PKCS#5, or AES (Advanced Encryption Standard) encryption. Only users with Security Administrator capabilities can run the Manage Server Encryption task, which is configured from the Manage Server Encryption page.
 To Access the Manage Server Encryption Page
To Access the Manage Server Encryption Page
To open the Manage Server Encryption page,
-
Select Server Tasks > Run Tasks from the menu bar.
-
When the Available Tasks page displays, click Manage Server Encryption to open the Manage Server Encryption page.
Figure 12–1 Manage Server Encryption Page
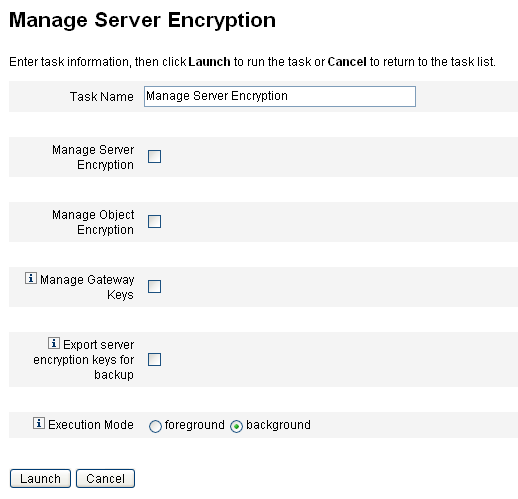
 To Configure Server Encryption
To Configure Server Encryption
Use this page to configure server and object encryption, gateway keys, back-up options, and execution mode.
-
Enter a Task Name.
This field defaults to Manage Server Encryption. You can enter a different task name if you do not want to use the default setting.
-
Choose one or more of the following options.
As you make a selection, .
-
Manage Server Encryption. Choose this option to configure server encryption.
The following additional options display:
-
Encryption of server encryption keys. You must specify a method for encrypting server encryption keys. Encryption types can include Triple DES, PKCS#5 (DES), or PKCS#5 (AES)
Note –-
Only those encryption types that are instantiable on your system will be displayed on this page. For example, if your system does not support PKCS#5 (AES), only Triple DES and PKCS#5 (DES) are displayed.
-
PKCS#5 (AES) requires that you download and configure the "Unlimited Strength Jurisdiction Policy Files" for the JVM running Identity Manager. Refer to your Java vendor's documentation for details..
Also, PKCS#5 (AES) requires that you install and configure the Bouncy Castle JCE provider jar file as a JCE provider for the JVM running Identity Manager. This jar file is packaged in the Identity Manager install image and can be found in the wshome/WEB-INF/lib directory. Two jar files are provided; bcprov-jdk15-137.jar and bcprov-jdk16-137.jar for use with corresponding versions of Java. Refer to your Java vendor's documentation and the Bouncy Castle documentation for more details.
-
-
Generate new server encryption key and set as current server encryption key. Select to generate a new server encryption key. Each piece of encrypted data generated after you make this selection is encrypted with this key. Generating a new server encryption key does not affect the key applied to existing encrypted data.
-
Generate new secure random PBE password. Select this option to generate a new password, based on a server-specific secret, each time the server is started. If you do not select this option, or if your server is not configured to use password-based encryption, then Identity Manager will use the default key to encrypt the server keys.
-
-
Manage Object Encryption. Choose this option to specify which object types should be re-encrypted and which encryption method to use.
-
Encryption of object types. Choose one of the displayed encryption types, which can include Triple DES (default), AES 256–bit key, AES, 192–bit key, or AES 128–bit key.
Note –AES using 192– or 256–bit keys requires that you download and configure the “Unlimited Strength Jurisdiction Policy Files” for the JVM running Identity Manager. Refer to your Java vendor's documentation for more details.
Only those encryption types that are instantiable on your system will be displayed on this page. For example, if your system does not support AES 192– or 256–bit keys using the “Unlimited Strength Jurisdiction Policy Files”, only Triple DES and AES 128–bit key options are displayed.
-
Select object types to re-encrypt with current server encryption key. Choose one or more Identity Manager object types listed in the table.
-
-
Manage Gateway Keys. Choose this option to specify gateway encryption.
The following options display:
-
Select gateway key option. Choose one of the following options:
-
Generate a new key and synchronize all gateways. Choose this option when initially enabling a secure gateway environment. This option generates a new gateway key and communicates that key to all gateways.
-
Synchronize all gateways with current gateway key. Select to synchronize any new gateways, or gateways that have not communicated the new gateway key. Select this option if you had a gateway that was down when all gateways were synchronized with the current gateway key, or when you want to force a key update for a new gateway.
-
-
Gateway key type. Choose one of the displayed key types, which can include Triple DES, AES 256–bit key, AES, 192–bit key, or AES 128–bit key.
Note –AES using 192– or 256–bit keys requires that you download and configure the “Unlimited Strength Jurisdiction Policy Files” for the JVM running Identity Manager. Refer to your Java vendor's documentation for more details.
Only those encryption types that are instantiable on your system will be displayed on this page. For example, if your system does not support AES 192– or 256–bit keys using the “Unlimited Strength Jurisdiction Policy Files”, only Triple DES and AES 128–bit key options are displayed.
-
-
Export server encryption keys for backup. Choose this option to export existing server encryption keys to an XML-formatted file. When you select this option, Identity Manager displays an additional field for you to specify a path and file name to export the keys.
Note –Select this option if you are using PKCS#5 encryption and chose to generate and set a new server encryption key. In addition, you should store the exported keys on removable media and in a secure location (not on a network).
-
-
Choose the Execution Mode.
You can run this task in the foreground or background (default setting).
Note –If you choose to re-encrypt one or more object types with a newly generated key, that task can take some time and is best run in the background.
-
When you are finished configuring the options on this page, click Launch.
- © 2010, Oracle Corporation and/or its affiliates
