 To Configure a Directory-Type Data Store
To Configure a Directory-Type Data Store
Use the following steps to configure a Directory-type data store.
-
Choose Directory from the Data Store Type menu. Additional options display.
Figure 5–16 Data Store Configuration Page: Directory
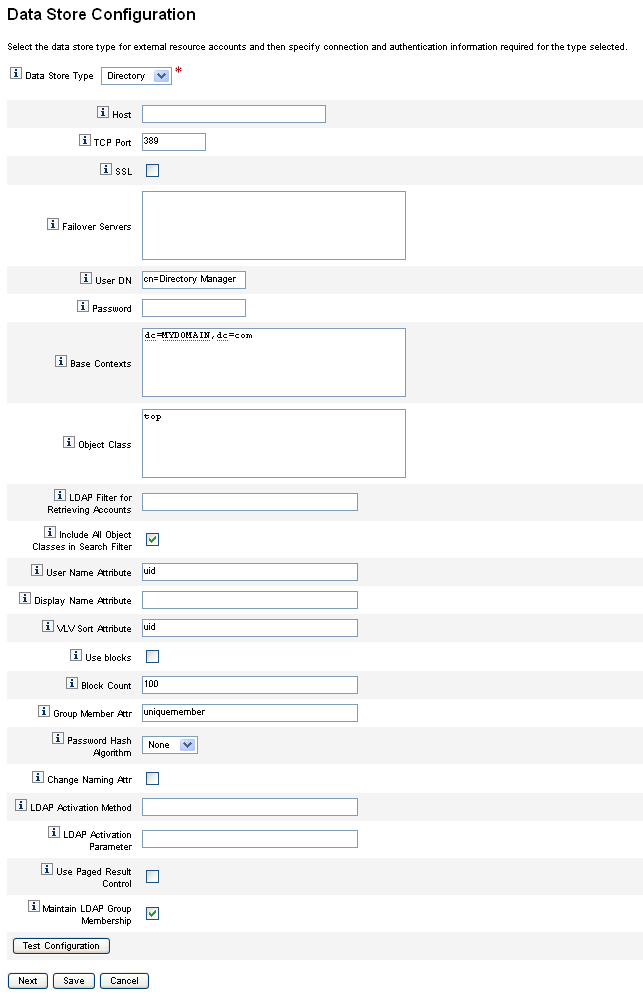
-
You must specify connection and authentication information for a Directory-type data store.
Configure the following options:
-
Host. Enter the IP address or the name of the host where the LDAP server is running.
-
TCP Port. Enter the TCP/IP port being used to communicate with the LDAP server.
-
If you are using SSL, this port is typically 636.
-
If you are using non-SSL, this port is typically 389.
-
-
SSL. Check this option to connect to the LDAP server using SSL.
-
Failover Servers. List all of the servers being used for failover if the preferred server fails. Enter this information in the following format, which follows the standard LDAP version 3 URLs described in RFC 2255:
ldap://ldap.example.com:389/o=LdapFailover
Only the host, port, and distinguished name (dn) portion of the URL are relevant in this setting.
If the preferred server fails, JNDI will automatically connect to the next server in this list.
-
User DN. Enter the dn used to authenticate to the LDAP server when making updates. (Defaults to cn=Directory Manager)
-
Password. Enter the principal's password.
-
Base Contexts. Specify one or more starting points that Identity Manager can use when searching the LDAP tree for users. (Defaults to dc=MYDOMAIN,dc=com)
Identity Manager performs searches when trying to discover users from the LDAP server or when looking for groups in which users are members.
-
Object Class. Enter one or more object classes to use when creating new user objects in the LDAP tree. (Defaults to top)
Each entry must be on a separate line. Do not use commas or spaces to separate entries.
Some LDAP servers require you to specify all of the object classes in a class hierarchy. For example, you might be required to specify top, person, organizationalperson, and inetorgperson instead of just using inetorgperson.
-
LDAP Filter for Retrieving Accounts. Enter an LDAP filter to control which accounts are returned from the LDAP resource. If you do not specify a filter, Identity Manager returns all accounts that include all of the specified object classes.
-
Include All Object Classes in Search Filter. Check this box to require all accounts to include every specified object class and to match the filter specified in the LDAP Filter for Retrieving Accounts field.
Note –You must enable this option when no search filter is specified. If you disable this option, accounts that do not include all of the specified object classes can be loaded into Identity Manager by using the reconciliation or load from resource features.
After loading, the account's objectclass attribute is not automatically updated. If an attribute on a missing object class is exposed through the Administrator interface, then providing a value for this attribute without modifying the objectclass attribute will fail. To avoid this problem, override the objectclass value in the Reconciliation or Load from Resource form.
-
User Name Attribute. Enter the name of the LDAP attribute that maps to the name of the Identity Manager user when discovering users from the directory. This name is frequently uid or cn.
-
Display Name Attribute. Enter the resource account attribute name whose value is used when displaying this account name.
-
VLV Sort Attribute. Enter the name of a sort attribute to use for VLV indexes on the resource.
-
Use blocks. Check this box to retrieve and process users in blocks.
When you are performing operations on a large number of users, processing users in blocks reduces the amount of memory used by the operation.
-
Block Count. Enter the maximum number of users to be grouped in blocks for processing.
-
Group Member Attr. Enter the name of the group member attribute to be updated with the user distinguished name (DN) when a user is added to the group.
The attribute name depends on the group's object class. For example, the Sun JavaTM System Enterprise Edition Directory Server and other LDAP servers use groups with the groupOfUniqueNames object class, and the uniqueMember attribute. Other LDAP servers use groups with the groupOfUniqueNames object class and the member attribute.
-
Password Hash Algorithm. Enter an algorithm that Identity Manager can use to hash the password. Supported values include:
-
SSHA
-
SHA
-
SMD5
-
MD5
If you specify 0 or leave this field blank, Identity Manager will not hash passwords and will store cleartext passwords in LDAP unless the LDAP server performs the hash. For example, the Sun Java System Enterprise Edition Directory Server hashes passwords.
-
-
Change Naming Attr. Check this box to allow modifications to change the user attribute representing the left-most relative distinguished name (DN). Modifications frequently change naming attributes to uid or cn.
-
LDAP Activation Method.
-
Leave this field blank if you want the resource to use password assignment for enable or disable actions.
-
Enter the nsmanageddisabledrole keyword, the nsaccountlock keyword, or the class name to use when performing an activation action for users of this resource.
-
-
LDAP Activation Parameter. Enter a value, based on how you completed the LDAP Activation Method field:
-
If you specified the nsmanageddisabledrole keyword, you must enter a value in the following format:
IDMAttribute=CN=nsmanageddisabledrole,baseContext
-
If you specified the nsaccountlock keyword, you must enter a value in the following format:
IDMAttribute=true
-
If you specified a class name, you must enter a value in the following format:
IDMAttribute
Note –For more information about the LDAP Activation Method and the LDAP Activation Parameter, see the Sun Identity Manager 8.1 Resources Reference.
-
-
Use Paged Result Control. Check this box to use LDAP Paged Results Control instead of VLV Control to iterate accounts during reconciliation.
Note –The resource must support simple paging control.
-
Maintain LDAP Group Membership. Check this box to have the adapter maintain LDAP group memberships when renaming or deleting users.
If you do not enable this option, the LDAP resource maintains the group memberships.
-
-
Test your data store connection configuration by clicking the Test Connection button.
A message displays to confirm that the connection is successful or to report an error with the configuration.
-
When you are finished, click Save and then click Next to continue to the Provisioner Notification Configuration page.
Note –You must set up valid account attributes and an identity template before you can create users on an LDAP resource.
- © 2010, Oracle Corporation and/or its affiliates
