External Resource Integration
The external resource integration is provided to accommodate customers who already have an investment in an SAP Access Enforcer 5.1 or 5.2 custom workflow. The external resource provides the best way to integrate with this type of asynchronous functionality because in this configuration, SAP Access Control is considered a black box and as disconnected until the pending provisioning operation has been performed.
SAP Access Control can be considered a write-only resource because it has no user store of any kind. The external resource data store contains the user data sent to SAP Access Control on each request. This data store provides a way for Waveset to read the data that was last sent to Access Control. However, the data is not necessarily synchronized with SAP Access Control back-end systems. It only provisions the users to its configured SAP systems (applications).
Note –
This integration does not perform an external policy check or generate compliance violations.
The following diagram illustrates the interaction between Waveset and SAP Access Control in this integration.
Figure 6–2 External Resource Integration
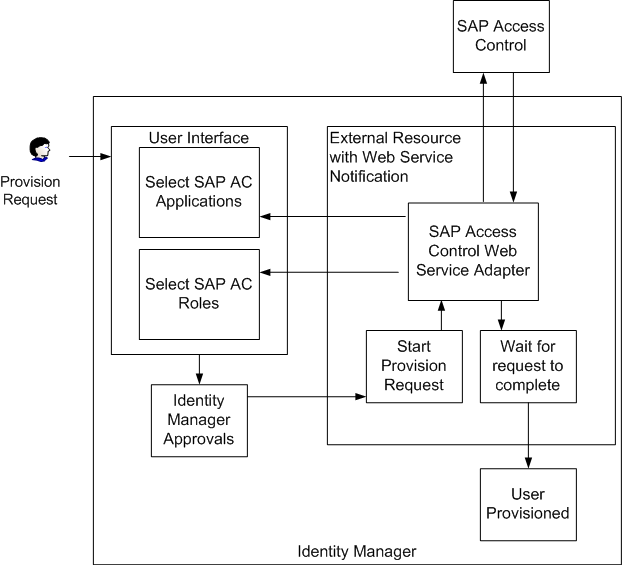
The external resource must be configured with a database user store (not LDAP) that contains the attribute values being provisioned. In addition, it must be configured to perform notifications by web services. To do this, set the Provisioner Notification Type parameter to Web Service. When the external resource is configured in this way, you must specify a rule to determine the status of web service requests. The $WSHOME/sample/rules/SAPAccessControlRules.xml file provides the SAP Access Control Check Status rule to fulfill this requirement.
The User Deferred Task Scanner polls SAP Access Control for the status of the provisioning request sent to SAP Access Control. When the request is complete, Waveset updates the workitem to indicate that the provisioning request is no longer pending, setting the status of the associated provisioning request work item to either completed or not complete.
The SAP Access Control AuditLog Report can be used to return information that is contained in the SAP Access Control audit log. This report is not installed by default, but is provided in the $WSHOME/sample/sapreports.xml file.
Supported Web Services
The external resource integration supports the following web services for Compliant User Provisioning (CUP):
-
SAPGRC_AC_IDM_REQUESTSTATUS
-
SAPGRC_AC_IDM_ROLEDETAILS
-
SAPGRC_AC_IDM_SEARCHROLES
-
SAPGRC_AC_IDM_SELECTAPPLICATION
-
SAPGRC_AC_IDM_SUBMITREQUEST
In addition, the SAP Access Control AuditLog Report uses the SAPGRC_AC_IDM_AUDITTRAIL web service.
Implementing a New External Resource Integration
Use the following procedure to integrate Waveset with SAP Access Control using an external resource.
-
Create an SAP Access Control Web Service adapter.
-
Import the following files:
-
$WSHOME/sample/rules/SAPAccessControlRules.xml
-
$WSHOME/sample/forms/ExternalSAPAccessControlUserForm.xml
-
-
Create an external resource. Refer to Understanding and Managing External Resources in Oracle Waveset 8.1.1 Business Administrator’s Guide for more information. The resource must have a database data source with Web Service notification. Be sure to follow these steps:
-
Select Web Service as the Provisioner Notification Type.
-
Select the desired SAP Access Control resource.
-
Select either the SAP Access Control Check Status Rule or your customized rule to perform the status check. The SAP Access Control Check Status Rule is provided in the SAPAccessControlRules.xml file.
-
Select the Provisioning Request form for SAP Access Control. The recommended form is the SAP Access Control Provisioning Request Form, but you may also select a customized form.
-
-
The account attributes page will be populated with attributes from the SAP Access Control resource, but they cannot be edited. If you make any changes to the attributes on the SAP Access Control resource, load the external resource account attributes page and click the Save button. Refer to the SAP Access Control adapter documentation for a list of default attributes.
-
Merge the External SAP Access Control User Form with your version of the Tabbed User Form.
-
Configure the User Deferred Task Scanner to run periodically. The interval for this task will determine how often the status of the provisioning request will be checked. The default interval is 1 hour.
Migrating from Access Enforcer Version 5.1 or 5.2
Upgrading from an SAP Access Enforcer resource to an external resource that connects to SAP Access Control 5.3 requires multiple tasks. Read the following procedure carefully.
Waveset provides a sample workflow, InstallDir/sample/wfexternalmigration.xml, for the purpose of migrating users from SAP Access Enforcer to SAP Access Control 5.3. It must be customized according to your environment and configuration.
The workflow requires the following account attributes:
-
acRequestorId
-
acRequestorFirstname
-
acRequestorLastname
-
acRequestorEmail
-
acManagerId
-
acManagerFirstname
-
acManagerLastname
-
acManagerEmail
-
acPriority
-
acUserId
-
acApplications
-
acRole
You may add attributes as needed.
This workflow currently displays the result of each user update. The current way around this is to modify the taskLaunch.jsp so that instead of displaying the results, the page is redirected back to the taskList.jsp page.
-
Determine the attributes that need to be migrated and update the workflow defined in the InstallDir/sample/wfexternalmigration.xml file.
-
Import the updated workflow.
-
Create an external resource for the SAP Access Control 5.3 integration. Ensure that the External Resource user store is configured properly. Refer to Understanding and Managing External Resources in Oracle Waveset 8.1.1 Business Administrator’s Guide for more information.
Note –The SAP Access Control adapter, which uses Metro for Web Service communication, can not be instantiated in some application servers together with the Access Enforcer resource adapter, which uses Apache Axis for Web Service Communication.
-
Run the Sample SAP Access Enforcer To Access Control Migration server task. The system should not be in use by anyone else during this process..
-
Remove Apache Axis from application server.
-
Download and install Glassfish Metro 1.5 from the following location: https://metro.dev.java.net/1.5/
-
Remove the Access Enforcer resource from Waveset.
-
Create the SAP Access Control resource.
-
Modify the external resource to use SAP Access Control web services.
- © 2010, Oracle Corporation and/or its affiliates
