AUTH_SYS
AUTH_SYS This is the same as the authentication flavor previously known as AUTH_UNIX. The caller of a remote procedure might wish to identify itself using traditional UNIX process permissions authentication. The flavor of the opaque_auth of such an RPC call message is AUTH_SYS. The bytes of the body encode the following structure:
struct auth_sysparms {
unsigned int stamp;
string machinename<255>;
uid_t uid;
gid_t gid;
gid_t gids<10>;
};
- stamp
-
is an arbitrary ID that the caller machine can generate.
- machinename
-
is the name of the caller's machine.
- uid
-
is the caller's effective user ID.
- gid
-
is the caller's effective group ID.
- gids
-
is a counted array of groups in which the caller is a member.
The flavor of the verifier accompanying the credentials should be AUTH_NONE.
AUTH_SHORT Verifier
When using AUTH_SYS authentication, the flavor of the response verifier received in the reply message from the server might be AUTH_NONE or AUTH_SHORT.
If AUTH_SHORT, the bytes of the response verifier's string encode a short_hand_verf structure. This opaque structure can now be passed to the server instead of the original AUTH_SYS credentials.
The server keeps a cache that maps the shorthand opaque structures to the original credentials of the caller. These structures are passed back by way of an AUTH_SHORT style response verifier. The caller can save network bandwidth and server CPU cycles by using the new credentials.
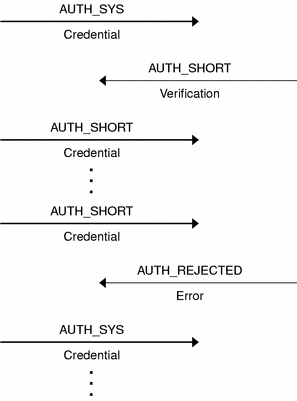
The server can flush the shorthand opaque structure at any time. If a flush occurs, the remote procedure call message is rejected because of an authentication error. The reason for the failure is AUTH_REJECTEDCRED. At this point, the caller might try the original AUTH_SYS style of credentials, as shown in the following figure.
Figure B–1 Authentication Process Map
- © 2010, Oracle Corporation and/or its affiliates
