 Reboot and Log In to Trusted Extensions
Reboot and Log In to Trusted Extensions
At most sites, two or more administrators, who serve as an install team, are present when configuring the system.
Before You Begin
Before you first log in, become familiar with the desktop and label options in Trusted Extensions. For details, see Chapter 2, Logging In to Trusted Extensions (Tasks), in Solaris Trusted Extensions User’s Guide.
-
Reboot the system.
# /usr/sbin/reboot
If your system does not have a graphical display, go to Chapter 6, Configuring a Headless System With Trusted Extensions (Tasks).
-
Log in to the Solaris Trusted Extensions (CDE) desktop as superuser.
-
In the login window, select Solaris Trusted Extensions (CDE) as the desktop.
This Trusted CDE desktop contains actions that are useful when configuring the system.
-
In the login dialog box, type root and the root password.
Users must not disclose their passwords to another person, as that person might then have access to the data of the user and will not be uniquely identified or accountable. Note that disclosure can be direct, through the user deliberately disclosing his/her password to another person, or indirect, such as through writing it down, or choosing an insecure password. Trusted Extensions software provides protection against insecure passwords, but cannot prevent a user disclosing his/her password or writing it down.
-
-
Read the information in the Last Login dialog box.
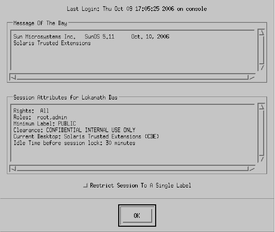
Then click OK to dismiss the box.
-
Read the Label Builder.
Click OK to accept the default label.
Once the login process is complete, the Trusted Extensions screen appears briefly, and you are in a desktop session with four workspaces. The Trusted Path symbol is displayed in the trusted stripe.
Note –You must log off or lock the screen before leaving a system unattended. Otherwise, a person can access the system without having to pass identification and authentication, and that person would not be uniquely identified or accountable.
- © 2010, Oracle Corporation and/or its affiliates
