Part III Installing Over a Wide Area Network
This part describes how to use the WAN boot installation method to install a system over a wide area network (WAN).
Chapter 9 WAN Boot (Overview)
This chapter provides an overview of the WAN boot installation method. This chapter describes the following topics.
What Is WAN Boot?
The WAN boot installation method enables you to boot and install software over a wide area network (WAN) by using HTTP. By using WAN boot, you can install the Solaris OS on SPARC based systems over a large public network where the network infrastructure might be untrustworthy. You can use WAN boot with security features to protect data confidentiality and installation image integrity.
The WAN boot installation method enables you to transmit an encrypted Solaris Flash archive over a public network to a remote SPARC based client. The WAN boot programs then install the client system by performing a custom JumpStart installation. To protect the integrity of the installation, you can use private keys to authenticate and encrypt data. You can also transmit your installation data and files over a secure HTTP connection by configuring your systems to use digital certificates.
To perform a WAN boot installation, you install a SPARC based system by downloading the following information from a web server over a HTTP or secure HTTP connection.
-
wanboot program – The wanboot program is the second level boot program that loads the WAN boot miniroot, client configuration files, and installation files. The wanboot program performs tasks similar to those that are performed by the ufsboot or inetboot second level boot programs.
-
WAN boot file system – WAN boot uses several different files to configure the client and retrieve data to install the client system. These files are located in the /etc/netboot directory of the web server. The wanboot-cgi program transmits these files to the client as a file system, called the WAN boot file system.
-
WAN boot miniroot – The WAN boot miniroot is a version of the Solaris miniroot that has been modified to perform a WAN boot installation. The WAN boot miniroot, like the Solaris miniroot, contains a kernel and just enough software to install the Solaris environment. The WAN boot miniroot contains a subset of the software in the Solaris miniroot.
-
Custom JumpStart configuration files – To install the system, WAN boot transmits sysidcfg, rules.ok, and profile files to the client. WAN boot then uses these files to perform a custom JumpStart installation on the client system.
-
Solaris Flash archive – A Solaris Flash archive is a collection of files that you copy from a master system. You can then use this archive to install a client system. WAN boot uses the custom JumpStart installation method to install a Solaris Flash archive on the client system. After you install an archive on a client system, the system contains the exact configuration of the master system.
Note –The flarcreate command no longer has size limitations on individual files. You can create a Solaris Flash archive that contains individual files over 4 Gbytes.
For more information, see Creating an Archive That Contains Large Files in Solaris 10 8/07 Installation Guide: Solaris Flash Archives (Creation and Installation).
You then install the archive on the client by using the custom JumpStart installation method.
You can protect the transfer of the previously listed information by using keys and digital certificates.
For a more detailed description of the sequence of events in a WAN boot installation, see How WAN Boot Works (Overview).
When to Use WAN Boot
The WAN boot installation method enables you to install SPARC based systems that are located in geographically remote areas. You might want to use WAN boot to install remote servers or clients that are accessible only over a public network.
If you want to install systems that are located on your local area network (LAN), the WAN boot installation method might require more configuration and administration than necessary. For information about how to install systems over a LAN, see Chapter 4, Installing From the Network (Overview).
How WAN Boot Works (Overview)
WAN boot uses a combination of servers, configuration files, Common Gateway Interface (CGI) programs, and installation files to install a remote SPARC based client. This section describes the general sequence of events in a WAN boot installation.
Sequence of Events in a WAN Boot Installation
Figure 9–1 shows the basic sequence of events in a WAN boot installation. In this figure, a SPARC based client retrieves configuration data and installation files from a web server and an install server over a WAN.
Figure 9–1 Sequence of Events in a WAN Boot Installation
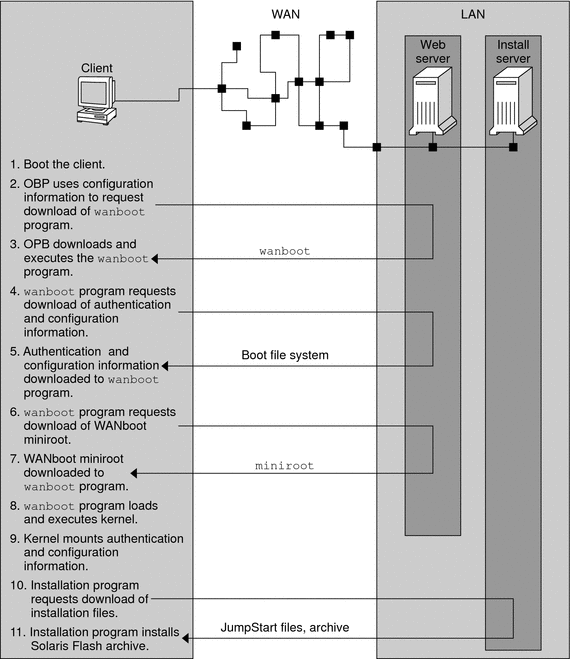
-
You boot the client in one of the following ways.
-
Boot from the network by setting network interface variables in the Open Boot PROM (OBP).
-
Boot from the network with the DHCP option.
-
Boot from a local CD-ROM.
-
-
The client OBP obtains configuration information from one of the following sources.
-
From boot argument values that are typed at the command line by the user
-
From the DHCP server, if the network uses DHCP
-
-
The client OBP requests the WAN boot second level boot program (wanboot).
The client OBP downloads the wanboot program from the following sources.
-
From a special web server, called the WAN boot server, by using the Hyper Text Transfer Protocol (HTTP)
-
From a local CD-ROM (not shown in the figure)
-
-
The wanboot program requests the client configuration information from the WAN boot server.
-
The wanboot program downloads configuration files that are transmitted by the wanboot-cgi program from the WAN boot server. The configuration files are transmitted to the client as the WAN boot file system.
-
The wanboot program requests the download of the WAN boot miniroot from the WAN boot server.
-
The wanboot program downloads the WAN boot miniroot from the WAN boot server by using HTTP or secure HTTP.
-
The wanboot program loads and executes the UNIX kernel from the WAN boot miniroot.
-
The UNIX kernel locates and mounts the WAN boot file system for use by the Solaris installation program.
-
The installation program requests the download of a Solaris Flash archive and custom JumpStart files from an install server.
The installation program downloads the archive and custom JumpStart files over an HTTP or HTTPS connection.
-
The installation program performs a custom JumpStart installation to install the Solaris Flash archive on the client.
Protecting Data During a WAN Boot Installation
The WAN boot installation method enables you to use hashing keys, encryption keys, and digital certificates to protect your system data during the installation. This section briefly describes the different data protection methods that are supported by the WAN boot installation method.
Checking the Integrity of Data With a Hashing Key
To protect the data you transmit from the WAN boot server to the client, you can generate a Hashed Message Authentication Code (HMAC) key. You install this hashing key on both the WAN boot server and the client. The WAN boot server uses this key to sign the data to be transmitted to the client. The client then uses this key to verify the integrity of the data that is transmitted by the WAN boot server. After you install a hashing key on a client, the client uses this key for future WAN boot installations.
For instructions about how to use a hashing key, see (Optional) To Create a Hashing Key and an Encryption Key.
Encrypting Data With Encryption Keys
The WAN boot installation method enables you to encrypt the data you transmit from the WAN boot server to the client. You can use WAN boot utilities to create a Triple Data Encryption Standard (3DES) or Advanced Encryption Standard (AES) encryption key. You can then provide this key to both the WAN boot server and the client. WAN boot uses this encryption key to encrypt the data sent from the WAN boot server to the client. The client can then use this key to decrypt the encrypted configuration files and security files that are transmitted during the installation.
Once you install an encryption key on a client, the client uses this key for future WAN boot installations.
Your site might not permit the use of encryption keys. To determine if your site permits encryption, ask your site's security administrator. If your site permits encryption, ask your security administrator which type of encryption key, either 3DES or AES, you should use.
For instructions on how to use encryption keys, see (Optional) To Create a Hashing Key and an Encryption Key.
Protecting Data by Using HTTPS
WAN boot supports the use of HTTP over Secure Sockets Layer (HTTPS) to transfer data between the WAN boot server and the client. By using HTTPS, you can require the server, or both the server and the client, to authenticate themselves during the installation. HTTPS also encrypts the data that is transferred from the server to the client during the installation.
HTTPS uses digital certificates to authenticate systems that exchange data over the network. A digital certificate is a file that identifies a system, either a server or client, as a system to trust during online communication. You can request a digital certificate from an external certificate authority, or create your own certificate and certificate authority.
To enable the client to trust the server and accept data from the server, you must install a digital certificate on the server. You then instruct the client to trust this certificate. You can also require the client to authenticate itself to the servers by providing a digital certificate to the client. You can then instruct the server to accept the certificate's signer when the client presents the certificate during the installation.
To use digital certificates during the installation, you must configure your web server to use HTTPS. See your web server documentation for information about how to use HTTPS.
For information about the requirements to use digital certificates during your WAN boot installation, see Digital Certificate Requirements. For instructions about how to use digital certificates in your WAN boot installation, see (Optional) To Use Digital Certificates for Server and Client Authentication.
Security Configurations Supported by WAN Boot (Overview)
WAN boot supports varying levels of security. You can use a combination of the security features that are supported in WAN boot to meet the needs of your network. A more secure configuration requires more administration, but also protects your system data to a greater extent. For more critical systems, or those systems you want to install over a public network, you might choose the configuration in Secure WAN Boot Installation Configuration. For less critical systems, or systems on semi-private networks, consider the configuration that is described in Insecure WAN Boot Installation Configuration.
This section briefly describes the different configurations you can use to set the level of security for your WAN boot installation. The section also describes the security mechanisms that are required by these configurations.
Secure WAN Boot Installation Configuration
This configuration protects the integrity of the data exchanged between the server and client, and helps keep the contents of the exchange confidential. This configuration uses an HTTPS connection, and uses either the 3DES or AES algorithm to encrypt the client configuration files. This configuration also requires the server to authenticate itself to the client during the installation. A secure WAN boot installation requires the following security features.
-
HTTPS enabled on the WAN boot server and the install server
-
HMAC SHA1 hashing key on the WAN boot server and the client
-
3DES or AES encryption key for the WAN boot server and the client
-
Digital certificate of a certificate authority for the WAN boot server
If you want to also require client authentication during the installation, you must also use the following security features.
-
Private key for the WAN boot server
-
Digital certificate for the client
For a list of the tasks that are required to install with this configuration, see Table 11–1.
Insecure WAN Boot Installation Configuration
This security configuration requires the least administration effort, but provides the least secure transfer of data from the web server to the client. You do not need to create a hashing key, encryption key, or digital certificates. You do not need to configure your web server to use HTTPS. However, this configuration transfers the installation data and files over an HTTP connection, which leaves your installation vulnerable to interception over the network.
If you want the client to check the integrity of the data that is transmitted, you can use a HMAC SHA1 hashing key with this configuration. However, the Solaris Flash archive is not protected by the hashing key. The archive is transferred insecurely between the server and the client during the installation.
For a list of the tasks that are required to install with this configuration, see Table 11–2.
Chapter 10 Preparing to Install With WAN Boot (Planning)
This chapter describes how to prepare your network for a WAN boot installation. This chapter describes the following topics.
WAN Boot Requirements and Guidelines
The section describes the system requirements to perform a WAN boot installation.
Table 10–1 System Requirements for WAN Boot Installation|
System and Description |
Requirements |
|---|---|
|
WAN boot server – The WAN boot server is a web server that provides the wanboot program, the configuration and security files, and the WAN boot miniroot. |
|
|
Install server – The install server provides the Solaris Flash archive and custom JumpStart files that are required to install the client. |
If the install server is a different system than the WAN boot server, the install server must meet these additional requirements.
|
|
Client system – The remote system you want to install over a WAN |
|
|
(Optional) DHCP server – You can use a DHCP server to provide client configuration information. |
If you are using a SunOS DHCP server, you must perform one of the following tasks.
If the DHCP server is on a different subnet than the client, you must configure a BOOTP relay agent. For more information about how to configure a BOOTP relay agent, see Chapter 14, Configuring the DHCP Service (Tasks), in System Administration Guide: IP Services. |
|
(Optional) Logging server – By default, all booting and installation log messages are displayed on the client console during a WAN installation. If you want to view these messages on another system, you can specify a system to serve as a logging server. |
Must be configured as web server. Note – If you use HTTPS during your installation, the logging server must be the same system as the WAN boot server. |
|
(Optional) Proxy server – You can configure the WAN boot feature to use an HTTP proxy during the download of the installation data and files. |
If the installation uses HTTPS, the proxy server must be configured to tunnel HTTPS. |
Web Server Software Requirements and Guidelines
The web server software you use on your WAN boot server and install server must meet the following requirements.
-
Operating system requirements – WAN boot provides a Common Gateway Interface (CGI) program (wanboot-cgi) that converts data and files into a specific format that the client machine expects. To perform a WAN boot installation with these scripts, the web server software must run on the Solaris 9 12/03 OS, or compatible version.
-
File size limitations – Your web server software might limit the size of the files you can transmit over HTTP. Check your web server documentation to make sure the software can transmit files that are the size of a Solaris Flash archive.
Note –The flarcreate command no longer has size limitations on individual files. You can create a Solaris Flash archive that contains individual files over 4 Gbytes.
For more information, see Creating an Archive That Contains Large Files in Solaris 10 8/07 Installation Guide: Solaris Flash Archives (Creation and Installation).
-
SSL support – If you want to use HTTPS in your WAN boot installation, the web server software must support SSL version 3.
Server Configuration Options
You can customize the configuration of the servers that are required by WAN boot to meet your network needs. You can host all the servers on one system, or place the servers on multiple systems.
-
Single server – If you want to centralize the WAN boot data and files on one system, you can host all the servers on the same machine. You can administer all your different servers on one system, and you only need to configure one system as a web server. However, a single server might not be able to support the volume of traffic that is required for a large number of simultaneous WAN boot installations.
-
Multiple servers – If you want to distribute the installation data and files across your network, you can host these servers on multiple machines. You might set up a central WAN boot server, and configure multiple install servers to host Solaris Flash archives across your network. If you host the install server and logging server on independent machines, you must configure those servers as web servers.
Storing Installation and Configuration Files in the Document Root Directory
The wanboot-cgi program transmits the following files during a WAN boot installation.
-
wanboot program
-
WAN boot miniroot
-
Custom JumpStart files
-
Solaris Flash archive
To enable the wanboot-cgi program to transmit these files you must store these files in a directory that is accessible to the web server software. One way to make these files accessible is to place these files in the document root on your web server.
The document root, or primary document directory, is the directory on your web server where you store files you want to make available to clients. You can name and configure this directory in your web server software. See your web server documentation for more information about setting up the document root directory on your web server.
You might want to create different subdirectories of the document root directory to store your different installation and configuration files. For example, you might want to create specific subdirectories for each group of clients that you want to install. If you plan to install several different releases of the Solaris OS across your network, you might create subdirectories for each release.
Figure 10–1 shows a basic sample structure for a document root directory. In this example, the WAN boot server and install server are on the same machine. The server is running the Apache web server software.
Figure 10–1 Sample Structure for Document Root Directory
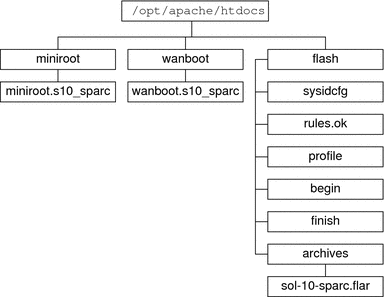
This sample document directory uses the following structure.
-
The /opt/apache/htdocs directory is the document root directory.
-
The WAN boot miniroot (miniroot) directory contains the WAN boot miniroot.
-
The Solaris Flash (flash) directory contains the custom JumpStart files that are required to install the client and the subdirectory archives. The archives directory contains the current Solaris release Flash archive.
Note –
If the WAN boot server and the install server are different systems, you might want to store the flash directory on the install server. Ensure that these files and directories are accessible to the WAN boot server.
For information about how to create the document root directory, see your web server documentation. For detailed instructions about how to create and store these installation files, see Creating the Custom JumpStart Installation Files.
Storing Configuration and Security Information in the /etc/netboot Hierarchy
The /etc/netboot directory contains the configuration information, private key, digital certificate, and certificate authority that are required for a WAN boot installation. This section describes the files and directories you can create in the /etc/netboot directory to customize your WAN boot installation.
Customizing the Scope of the WAN Boot Installation
During the installation, the wanboot-cgi program searches for the client information in the /etc/netboot directory on the WAN boot server. The wanboot-cgi program converts this information into the WAN boot file system, and then transmits the WAN boot file system to the client. You can create subdirectories within the /etc/netboot directory to customize the scope of the WAN installation. Use the following directory structures to define how configuration information is shared among the clients that you want to install.
-
Global configuration – If you want all the clients on your network to share configuration information, store the files that you want to share in the /etc/netboot directory.
-
Network-specific configuration – If you want only those machines on a specific subnet to share configuration information, store the configuration files that you want to share in a subdirectory of /etc/netboot. Have the subdirectory follow this naming convention.
/etc/netboot/net-ip
In this example, net-ip is the IP address of the client's subnet. For example, if you want all systems on the subnet with the IP address of 192.168.255.0 to share configuration files, create a /etc/netboot/192.168.255.0 directory. Then, store the configuration files in this directory.
-
Client-specific configuration – If you want only a specific client to use the boot file system, store the boot file system files in a subdirectory of /etc/netboot. Have the subdirectory follow this naming convention.
/etc/netboot/net-ip/client-ID
In this example, net-ip is the IP address of the subnet. client-ID is either the client ID that is assigned by the DHCP server, or a user-specified client ID. For example, if you want a system with the client ID 010003BA152A42 on the subnet 192.168.255.0 to use specific configuration files, create a /etc/netboot/192.168.255.0/010003BA152A42 directory. Then, store the appropriate files in this directory.
Specifying Security and Configuration Information in the /etc/netboot Directory
You specify the security and configuration information by creating the following files and storing the files in the /etc/netboot directory.
-
wanboot.conf – This file specifies the client configuration information for a WAN boot installation.
-
System configuration file (system.conf) – This system configuration file specifies the location of the client's sysidcfg file and custom JumpStart files.
-
keystore – This file contains the client's HMAC SHA1 hashing key, 3DES or AES encryption key, and SSL private key.
-
truststore – This file contains the digital certificates of certificate signing authorities that the client should trust. These trusted certificates instruct the client to trust the server during the installation.
-
certstore – This file contains the client's digital certificate.
Note –The certstore file must be located in the client ID directory. See Customizing the Scope of the WAN Boot Installation for more information about subdirectories of the /etc/netboot directory.
For detailed instructions on how to create and store these files, see the following procedures.
Sharing Security and Configuration Information in the /etc/netboot Directory
To install clients on your network, you might want to share security and configuration files among several different clients, or across entire subnets. You can share these files by distributing your configuration information throughout the /etc/netboot/net-ip/client-ID, /etc/netboot/net-ip, and /etc/netboot directories. The wanboot-cgi program searches these directories for the configuration information that best fits the client, and uses that information during the installation.
The wanboot-cgi program searches for client information in the following order.
-
/etc/netboot/net-ip/client-ID – The wanboot-cgi program first checks for configuration information that is specific to the client machine. If the /etc/netboot/net-ip/client-ID directory contains all the client configuration information, the wanboot-cgi program does not check for configuration information elsewhere in the /etc/netboot directory.
-
/etc/netboot/net-ip – If all the required information is not located in the /etc/netboot/net-ip/client-ID directory, the wanboot-cgi program then checks for subnet configuration information in the /etc/netboot/net-ip directory.
-
/etc/netboot – If the remaining information is not located in the /etc/netboot/net-ip directory, the wanboot-cgi program then checks for global configuration information in the /etc/netboot directory.
Figure 10–2 demonstrates how you can set up the /etc/netboot directory to customize your WAN boot installations.
Figure 10–2 Sample /etc/netboot Directory
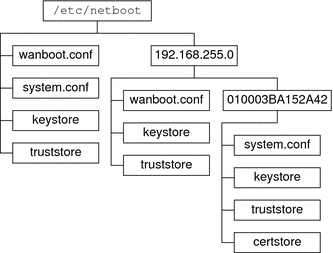
The /etc/netboot directory layout in Figure 10–2 enables you to perform the following WAN boot installations.
-
When you install the client 010003BA152A42, the wanboot-cgi program uses the following files in the /etc/netboot/192.168.255.0/010003BA152A42 directory.
-
system.conf
-
keystore
-
truststore
-
certstore
The wanboot-cgi program then uses the wanboot.conf file in the /etc/netboot/192.168.255.0 directory.
-
-
When you install a client that is located on the 192.168.255.0 subnet, the wanboot-cgi program uses the wanboot.conf, keystore, and truststore files in the /etc/netboot/192.168.255.0 directory. The wanboot-cgi program then uses the system.conf file in the /etc/netboot directory.
-
When you install a client machine that is not located on the 192.168.255.0 subnet, the wanboot-cgi program uses the following files in the /etc/netboot directory.
-
wanboot.conf
-
system.conf
-
keystore
-
truststore
-
Storing the wanboot-cgi Program
The wanboot-cgi program transmits the data and files from the WAN boot server to the client. You must ensure that this program is in a directory on the WAN boot server that is accessible to the client. One method to make this program accessible to the client is to store this program in the cgi-bin directory of the WAN boot server. You might need to configure your web server software to use the wanboot-cgi program as a CGI program. See your web server documentation for information about CGI program requirements.
Digital Certificate Requirements
If you want to add security to your WAN boot installation, you can use digital certificates to enable server and the client authentication. WAN boot can use a digital certificate to establish the identity of the server or the client during an online transaction. Digital certificates are issued by a certificate authority (CA). These certificates contain a serial number, expiration dates, a copy of the certificate holder's public key, and the certificate authority's digital signature.
If you want to require server or both client and server authentication during your installation, you must install digital certificates on the server. Follow these guidelines when you use digital certificates.
-
If you want to use digital certificates, the digital certificates must be formatted as part of a Public-Key Cryptography Standards #12 (PKCS#12) file.
-
If you create your own certificates, you must create the certificates as PKCS#12 files.
-
If you receive your certificates from third-party certificate authorities, request your certificates in the PKCS#12 format.
For detailed instructions on how to use PKCS#12 certificates during your WAN boot installation, see (Optional) To Use Digital Certificates for Server and Client Authentication.
WAN Boot Security Limitations
While WAN boot provides several different security features, WAN boot does not address these potential insecurities.
-
Denial of service (DoS) attacks – A denial of service attack can take many forms, with the goal of preventing users from accessing a specific service. A DoS attack can overwhelm a network with large amounts of data, or aggressively consume limited resources. Other DoS attacks manipulate the data that is transmitted between systems in transit. The WAN boot installation method does not protect servers or clients from DoS attacks.
-
Corrupted binaries on the servers – The WAN boot installation method does not check the integrity of the WAN boot miniroot or the Solaris Flash archive before you perform your installation. Before you perform your installation, check the integrity of your Solaris binaries against the Solaris Fingerprint Database at http://sunsolve.sun.com.
-
Encryption key and hashing key privacy – If you use encryption keys or a hashing key with WAN boot, you must type the key value on the command line during your installation. Follow the precautions that are necessary for your network to make sure that these key values remain private.
-
Compromise of the network naming service – If you use a naming service on your network, check the integrity of your name servers before you perform your WAN boot installation.
Gathering Information for WAN Boot Installations
You need to gather a wide variety of information to configure your network for a WAN boot installation. You might want to write down this information as you prepare to install over a WAN.
Use the following worksheets to record the WAN boot installation information for your network.
Table 10–2 Worksheet for Collecting Server InformationTable 10–3 Worksheet for Collecting Client Information
|
Information |
Notes |
|---|---|
|
IP address for the client's subnet |
|
|
IP address for the client's router |
|
|
IP address of the client |
|
|
Subnet mask for the client |
|
|
Host name for the client |
|
|
MAC address of the client |
|
Chapter 11 Installing With WAN Boot (Tasks)
This chapter describes the following tasks that are necessary to prepare your network for a WAN boot installation.
Installing Over a Wide Area Network (Task Maps)
The following tables list the tasks you need to perform to prepare for a WAN boot installation.
-
For a list of the tasks you need to perform to prepare for a secure WAN boot installation, see Table 11–1.
For a description of a secure WAN boot installation over HTTPS, see Secure WAN Boot Installation Configuration.
-
For a list of the tasks you need to perform to prepare for an insecure WAN boot installation, see Table 11–2.
For a description of an insecure WAN boot installation, see Insecure WAN Boot Installation Configuration.
To use a DHCP server or a logging server, complete the optional tasks that are listed at the bottom of each table.
Table 11–1 Task Map: Preparing to Perform a Secure WAN Boot Installation|
Task |
Description |
For Instructions |
|---|---|---|
|
Decide what security features you want to use in your installation. |
Review the security features and configurations to decide what level of security you want to use in your WAN boot installation. | |
|
Collect WAN boot installation information. |
Complete the worksheet to record all the information you need to perform a WAN boot installation. | |
|
Create the document root directory on the WAN boot server. |
Create the document root directory and any subdirectories to serve the configuration and installation files. | |
|
Create the WAN boot miniroot. |
Use the setup_install_server command to create the WAN boot miniroot. | |
|
Verify that the client system supports WAN boot. |
Check the client OBP for boot argument support of WAN boot. | |
|
Install the wanboot program on the WAN boot server. |
Copy the wanboot program to the document root directory of the WAN boot server. | |
|
Install the wanboot-cgi program on the WAN boot server. |
Copy the wanboot-cgi program to the WAN boot server's CGI directory. | |
|
(Optional) Set up the logging server. |
Configure a dedicated system for displaying boot and installation log messages. | |
|
Set up the /etc/netboot hierarchy. |
Populate the /etc/netboot hierarchy with the configuration and security files that are required for a WAN boot installation. | |
|
Configure the web server to use secure HTTP for a more secure WAN boot installation. |
Identify the web server requirements that are necessary to perform a WAN installation with HTTPS. | |
|
Format digital certificates for a more secure WAN boot installation. |
Split PKCS#12 file into a private key and a certificate to use with the WAN installation. |
(Optional) To Use Digital Certificates for Server and Client Authentication |
|
Create a hashing key and an encryption key for a more secure WAN boot installation. |
Use the wanbootutil keygen command to create HMAC SHA1, 3DES, or AES keys. | |
|
Create the Solaris Flash archive. |
Use the flarcreate command to create an archive of the software that you want to install on the client. | |
|
Create the installation files for the custom JumpStart installation. |
Use a text editor to create the following files:
| |
|
Create the system configuration file. |
Set the configuration information in the system.conf file. | |
|
Create the WAN boot configuration file. |
Set the configuration information in the wanboot.conf file. | |
|
(Optional) Configure the DHCP server to support a WAN boot installation. |
Set Sun vendor options and macros in the DHCP server. |
Preconfiguring System Configuration Information With the DHCP Service (Tasks) |
Table 11–2 Task Map: Preparing to Perform an Insecure WAN Boot Installation
|
Task |
Description |
For Instructions |
|---|---|---|
|
Decide what security features you want to use in your installation. |
Review the security features and configurations to decide what level of security you want to use in your WAN boot installation. | |
|
Collect WAN boot installation information. |
Complete the worksheet to record all the information you need to perform a WAN boot installation. | |
|
Create the document root directory on the WAN boot server. |
Create the document root directory and any subdirectories to serve the configuration and installation files. | |
|
Create the WAN boot miniroot. |
Use the setup_install_server command to create the WAN boot miniroot. | |
|
Verify that the client system supports WAN boot. |
Check the client OBP for boot argument support of WAN boot. | |
|
Install the wanboot program on the WAN boot server. |
Copy the wanboot program to the document root directory of the WAN boot server. | |
|
Install the wanboot-cgi program on the WAN boot server. |
Copy the wanboot-cgi program to the WAN boot server's CGI directory. | |
|
(Optional) Set up the logging server. |
Configure a dedicated system for displaying boot and installation log messages. | |
|
Set up the /etc/netboot hierarchy. |
Populate the /etc/netboot hierarchy with the configuration and security files that are required for a WAN boot installation. | |
|
(Optional) Create a hashing key. |
Use the wanbootutil keygen command to create HMAC SHA1 key. For insecure installations that check data integrity, complete this task to create an HMAC SHA1 hashing key. | |
|
Create the Solaris Flash archive. |
Use the flarcreate command to create an archive of the software that you want to install on the client. | |
|
Create the installation files for the custom JumpStart installation. |
Use a text editor to create the following files:
| |
|
Create the system configuration file. |
Set the configuration information in the system.conf file. | |
|
Create the WAN boot configuration file. |
Set the configuration information in the wanboot.conf file. | |
|
(Optional) Configure the DHCP server to support a WAN boot installation. |
Set Sun vendor options and macros in the DHCP server. |
Preconfiguring System Configuration Information With the DHCP Service (Tasks) |
Configuring the WAN Boot Server
The WAN boot server is a web server that provides the boot and configuration data during a WAN boot installation. For a list of the system requirements for the WAN boot server, see Table 10–1.
This section describes the following tasks required to configure the WAN boot server for a WAN boot installation.
Creating the Document Root Directory
To serve the configuration and installation files, you must make these files accessible to the web server software on the WAN boot server. One method to make these files accessible is to store them in the WAN boot server's document root directory.
If you want to use a document root directory to serve the configuration and installation files, you must create this directory. See your web server documentation for information about how to create the document root directory. For detailed information about how to design your document root directory, see Storing Installation and Configuration Files in the Document Root Directory.
For an example of how to set up this directory, see Create the Document Root Directory.
After you create the document root directory, create the WAN boot miniroot. For instructions, see Creating the WAN Boot Miniroot.
Creating the WAN Boot Miniroot
WAN boot uses a special Solaris miniroot that has been modified to perform a WAN boot installation. The WAN boot miniroot contains a subset of the software in the Solaris miniroot. To perform a WAN boot installation, you must copy the miniroot from the Solaris DVD or the Solaris Software - 1 CD to the WAN boot server. Use the -w option to the setup_install_server command to copy the WAN boot miniroot from the Solaris software media to your system's hard disk.
 SPARC: To Create a WAN Boot Miniroot
SPARC: To Create a WAN Boot Miniroot
This procedure creates a SPARC WAN boot miniroot with SPARC media. If you want to serve a SPARC WAN boot miniroot from an x86–based server, you must create the miniroot on a SPARC machine. After you create the miniroot, copy the miniroot to the document root directory on the x86–based server.
Before You Begin
This procedure assumes that the WAN boot server is running the Volume Manager. If you are not using the Volume Manager, see System Administration Guide: Devices and File Systems.
-
Become superuser or assume an equivalent role on the WAN boot server.
The system must meet the following requirements.
-
Include a CD-ROM or DVD-ROM drive
-
Be part of the site's network and naming service
If you use a naming service, the system must already be in a naming service, such as NIS, NIS+, DNS, or LDAP. If you do not use a naming service, you must distribute information about this system by following your site's policies.
-
-
Insert the Solaris Software - 1 CD or the Solaris DVD in the install server's drive.
-
Create a directory for the WAN boot miniroot and Solaris installation image.
# mkdir -p wan-dir-path install-dir-path
- -p
-
Instructs the mkdir command to create all the necessary parent directories for the directory you want to create.
- wan-dir-path
-
Specifies the directory where the WAN boot miniroot is to be created on the install server. This directory needs to accommodate miniroots that are typically 250 Mbytes in size.
- install-dir-path
-
Specifies the directory on the install server where the Solaris software image is to be copied. This directory can be removed later in this procedure.
-
Change to the Tools directory on the mounted disc.
# cd /cdrom/cdrom0/s0/Solaris_10/Tools
In the previous example, cdrom0 is the path to the drive that contains the Solaris OS media.
-
Copy the WAN boot miniroot and the Solaris software image to the WAN boot server's hard disk.
# ./setup_install_server -w wan-dir-path install-dir-path
- wan-dir-path
-
Specifies the directory where the WAN boot miniroot is to be copied
- install-dir-path
-
Specifies the directory where the Solaris software image is to be copied
Note –The setup_install_server command indicates whether you have enough disk space available for the Solaris Software disc images. To determine available disk space, use the df -kl command.
The setup_install_server -w command creates the WAN boot miniroot and a network installation image of the Solaris software.
-
(Optional) Remove the network installation image.
You do not need the Solaris software image to perform a WAN installation with a Solaris Flash archive. You can free up disk space if you do not plan to use the network installation image for other network installations. Type the following command to remove the network installation image.
# rm -rf install-dir-path
-
Make the WAN boot miniroot available to the WAN boot server in one of the following ways.
-
Create a symbolic link to the WAN boot miniroot in the document root directory of the WAN boot server.
# cd /document-root-directory/miniroot # ln -s /wan-dir-path/miniroot .
- document-root-directory/miniroot
-
Specifies the directory in the WAN boot server's document root directory where you want to link to the WAN boot miniroot
- /wan-dir-path/miniroot
-
Specifies the path to the WAN boot miniroot
-
Move the WAN boot miniroot to the document root directory on the WAN boot server.
# mv /wan-dir-path/miniroot /document-root-directory/miniroot/miniroot-name
- wan-dir-path/miniroot
-
Specifies the path to the WAN boot miniroot.
- /document-root-directory/miniroot/
-
Specifies the path to the WAN boot miniroot directory in the WAN boot server's document root directory.
- miniroot-name
-
Specifies the name of the WAN boot miniroot. Name the file descriptively, for example miniroot.s10_sparc.
-
Example 11–1 Creating the WAN Boot Miniroot
Use the setup_install_server(1M) with the -w option to copy the WAN boot miniroot and the Solaris software image to the /export/install/Solaris_10 directory of wanserver-1.
Insert the Solaris Software media in the media drive that is attached to wanserver-1. Type the following commands.
wanserver-1# mkdir -p /export/install/cdrom0 wanserver-1# cd /cdrom/cdrom0/s0/Solaris_10/Tools wanserver-1# ./setup_install_server -w /export/install/cdrom0/miniroot \ /export/install/cdrom0 |
Move the WAN boot miniroot to the document root directory (/opt/apache/htdocs/) of the WAN boot server. In this example the name the WAN boot miniroot is set to miniroot.s10_sparc.
wanserver-1# mv /export/install/cdrom0/miniroot/miniroot \ /opt/apache/htdocs/miniroot/miniroot.s10_sparc |
Continuing the WAN Boot Installation
After you create the WAN boot miniroot, verify that the client OpenBoot PROM (OBP) supports WAN boot. For instructions, see Verifying WAN Boot Support on the Client.
See Also
For additional information about the setup_install_server command, see install_scripts(1M).
Verifying WAN Boot Support on the Client
To perform an unattended WAN boot installation, the client system's OpenBoot PROM (OBP) must support WAN boot. If the client's OBP does not support WAN boot, you can perform a WAN boot installation by providing the necessary programs on a local CD.
You can determine if the client supports WAN boot by checking the client's OBP configuration variables. Perform the following procedure to check the client for WAN boot support.
 To Check the Client OBP for WAN Boot Support
To Check the Client OBP for WAN Boot Support
This procedure describes how to determine if the client OBP supports WAN boot.
-
Become superuser or assume an equivalent role.
Roles contain authorizations and privileged commands. For more information about roles, see Configuring RBAC (Task Map) in System Administration Guide: Security Services.
-
Check the OBP configuration variables for WAN boot support.
# eeprom | grep network-boot-arguments
-
If the variable network-boot-arguments is displayed, or if the previous command returns the output network-boot-arguments: data not available, the OBP supports WAN boot installations. You do not need to update the OBP before you perform your WAN boot installation.
-
If the previous command does not return any output, the OBP does not support WAN boot installations. You must perform one of the following tasks.
-
Update the client OBP. For those clients who do have an OBP that is capable of supporting WAN boot installations, see your system documentation for information about how to update the OBP.
Note –Not all client OBPs support WAN Boot. For those clients use the next option.
-
After you complete the preparation tasks and are ready to install the client, perform the WAN boot installation from the Solaris Software CD1 or DVD. This option works in all cases when the current OBP does not provide WAN Boot support.
For instructions about how to boot the client from CD1, see To Perform a WAN Boot Installation With Local CD Media. To continue preparing for the WAN boot installation, see Creating the /etc/netboot Hierarchy on the WAN Boot Server.
-
-
Example 11–2 Verifying OBP Support for WAN Boot on the Client
The following command shows how to check the client OBP for WAN boot support.
# eeprom | grep network-boot-arguments network-boot-arguments: data not available |
In this example, the output network-boot-arguments: data not available indicates that the client OBP supports WAN boot.
Continuing the WAN Boot Installation
After you verify that the client OBP supports WAN boot, you must copy the wanboot program to the WAN boot server. For instructions, see Installing the wanboot Program on the WAN Boot Server.
If the client OBP does not support WAN boot, you do not need to copy the wanboot program to the WAN boot server. You must provide the wanboot program to the client on a local CD. To continue the installation, see Creating the /etc/netboot Hierarchy on the WAN Boot Server.
See Also
For additional information about the setup_install_server command, see Chapter 4, Installing From the Network (Overview).
Installing the wanboot Program on the WAN Boot Server
WAN boot uses a special second-level boot program (wanboot) to install the client. The wanboot program loads the WAN boot miniroot, client configuration files, and installation files that are required to perform a WAN boot installation.
To perform a WAN boot installation, you must provide the wanboot program to the client during the installation. You can provide this program to the client in the following ways.
-
If your client's PROM supports WAN boot, you can transmit the program from the WAN boot server to the client. You must install the wanboot program on the WAN boot server.
To check if your client's PROM supports WAN boot, see To Check the Client OBP for WAN Boot Support.
-
If your client's PROM does not support WAN boot, you must provide the program to the client on a local CD. If your client's PROM does not support WAN boot, go to Creating the /etc/netboot Hierarchy on the WAN Boot Server to continue preparing for your installation.
 SPARC: To Install the wanboot Program on the WAN Boot Server
SPARC: To Install the wanboot Program on the WAN Boot Server
This procedure describes how to copy the wanboot program from Solaris media to the WAN boot server.
This procedure assumes that the WAN boot server is running the Volume Manager. If you are not using the Volume Manager, see System Administration Guide: Devices and File Systems.
Before You Begin
Verify that your client system supports WAN boot. See To Check the Client OBP for WAN Boot Support for more information.
-
Become superuser or assume an equivalent role on the install server.
-
Insert the Solaris Software - 1 CD or the Solaris DVD in the install server's drive.
-
Change to the sun4u platform directory on the Solaris Software - 1 CD or the Solaris DVD.
# cd /cdrom/cdrom0/s0/Solaris_10/Tools/Boot/platform/sun4u/
-
Copy the wanboot program to the install server.
# cp wanboot /document-root-directory/wanboot/wanboot-name
- document-root-directory
-
Specifies the document root directory of the WAN boot server.
- wanboot-name
-
Specifies the name of the wanboot program. Name this file descriptively, for example, wanboot.s10_sparc.
-
Make the wanboot program available to the WAN boot server in one of the following ways.
-
Create a symbolic link to the wanboot program in the document root directory of the WAN boot server.
# cd /document-root-directory/wanboot # ln -s /wan-dir-path/wanboot .
- document-root-directory/wanboot
-
Specifies the directory in the WAN boot server's document root directory where you want to link to the wanboot program
- /wan-dir-path/wanboot
-
Specifies the path to the wanboot program
-
Move the WAN boot miniroot to the document root directory on the WAN boot server.
# mv /wan-dir-path/wanboot /document-root-directory/wanboot/wanboot-name
- wan-dir-path/wanboot
-
Specifies the path to the wanboot program
- /document-root-directory/wanboot/
-
Specifies the path to the wanboot program directory in the WAN boot server's document root directory.
- wanboot-name
-
Specifies the name of the wanboot program. Name the file descriptively, for example wanboot.s10_sparc.
-
Example 11–3 Installing the wanboot Program on the WAN Boot Server
To install the wanboot program on the WAN boot server, copy the program from the Solaris Software media to the WAN boot server's document root directory.
Insert the Solaris DVD or the Solaris Software - 1 CD in the media drive that is attached to wanserver-1 and type the following commands.
wanserver-1# cd /cdrom/cdrom0/s0/Solaris_10/Tools/Boot/platform/sun4u/ wanserver-1# cp wanboot /opt/apache/htdocs/wanboot/wanboot.s10_sparc |
In this example, the name of the wanboot program is set to wanboot.s10_sparc.
Continuing the WAN Boot Installation
After you install the wanboot program on the WAN boot server, you must create the /etc/netboot hierarchy on the WAN boot server. For instructions, see Creating the /etc/netboot Hierarchy on the WAN Boot Server.
See Also
For overview information about the wanboot program, see What Is WAN Boot?.
Creating the /etc/netboot Hierarchy on the WAN Boot Server
During the installation, WAN boot refers to the contents of the /etc/netboot hierarchy on the web server for instructions about how to perform the installation. This directory contains the configuration information, private key, digital certificate, and certificate authority required for a WAN boot installation. During the installation, the wanboot-cgi program converts this information into the WAN boot file system. The wanboot-cgi program then transmits the WAN boot file system to the client.
You can create subdirectories within the /etc/netboot directory to customize the scope of the WAN installation. Use the following directory structures to define how configuration information is shared among the clients that you want to install.
-
Global configuration – If you want all the clients on your network to share configuration information, store the files that you want to share in the /etc/netboot directory.
-
Network-specific configuration – If you want only those machines on a specific subnet to share configuration information, store the configuration files that you want to share in a subdirectory of /etc/netboot. Have the subdirectory follow this naming convention.
/etc/netboot/net-ip
In this example, net-ip is the IP address of the client's subnet.
-
Client-specific configuration – If you want only a specific client to use the boot file system, store the boot file system files in a subdirectory of /etc/netboot. Have the subdirectory follow this naming convention.
/etc/netboot/net-ip/client-ID
In this example, net-ip is the IP address of the subnet. client-ID is either the client ID that is assigned by the DHCP server, or a user-specified client ID.
For detailed planning information about these configurations, see Storing Configuration and Security Information in the /etc/netboot Hierarchy.
The following procedure describes how to create the /etc/netboot hierarchy.
 To Create the /etc/netboot Hierarchy
on the WAN Boot Server
To Create the /etc/netboot Hierarchy
on the WAN Boot Server
Follow these steps to create the /etc/netboot hierarchy.
-
Become superuser or assume an equivalent role on the WAN boot server.
-
Create the /etc/netboot directory.
# mkdir /etc/netboot
-
Change the permissions of the /etc/netboot directory to 700.
# chmod 700 /etc/netboot
-
Change the owner of the /etc/netboot directory to the web server owner.
# chown web-server-user:web-server-group /etc/netboot/
- web-server-user
-
Specifies the user owner of the web server process
- web-server-group
-
Specifies the group owner of the web server process
-
Exit the superuser role.
# exit
-
Assume the user role of the web server owner.
-
Create the client subdirectory of the /etc/netboot directory.
# mkdir -p /etc/netboot/net-ip/client-ID
- -p
-
Instructs the mkdir command to create all the necessary parent directories for the directory you want to create.
- (Optional) net-ip
-
Specifies the network IP address of the client's subnet.
- (Optional) client-ID
-
Specifies the client ID. The client ID can be a user-defined value or the DHCP client ID. The client-ID directory must be a subdirectory of the net-ip directory.
-
For each directory in the /etc/netboot hierarchy, change the permissions to 700.
# chmod 700 /etc/netboot/dir-name
Example 11–4 Creating the /etc/netboot Hierarchy on the WAN Boot Server
The following example shows how to create the /etc/netboot hierarchy for the client 010003BA152A42 on subnet 192.168.198.0. In this example, the user nobody and the group admin own the web server process.
The commands in this example perform the following tasks.
-
Create the /etc/netboot directory.
-
Change the permissions of the /etc/netboot directory to 700.
-
Change the ownership of the /etc/netboot directory to the owner of the web server process.
-
Assume the same user role as the web server user.
-
Create a subdirectory of /etc/netboot that is named after the subnet (192.168.198.0).
-
Create a subdirectory of the subnet directory that is named after the client ID.
-
Change the permissions of the /etc/netboot subdirectories to 700.
# cd / # mkdir /etc/netboot/ # chmod 700 /etc/netboot # chown nobody:admin /etc/netboot # exit server# su nobody Password: nobody# mkdir -p /etc/netboot/192.168.198.0/010003BA152A42 nobody# chmod 700 /etc/netboot/192.168.198.0 nobody# chmod 700 /etc/netboot/192.168.198.0/010003BA152A42 |
Continuing the WAN Boot Installation
After you create the /etc/netboot hierarchy, you must copy the WAN Boot CGI program to the WAN boot server. For instructions, see Copying the WAN Boot CGI Program to the WAN Boot Server.
See Also
For detailed planning information about how to design the /etc/netboot hierarchy, see Storing Configuration and Security Information in the /etc/netboot Hierarchy.
Copying the WAN Boot CGI Program to the WAN Boot Server
The wanboot-cgi program creates the data streams that transmit the following files from the WAN boot server to the client.
-
wanboot program
-
WAN boot file system
-
WAN boot miniroot
The wanboot-cgi program is installed on the system when you install the current Solaris release software. To enable the WAN boot server to use this program, copy this program to the cgi-bin directory of the WAN boot server.
 To Copy the wanboot-cgi Program
to the WAN Boot Server
To Copy the wanboot-cgi Program
to the WAN Boot Server
-
Become superuser or assume an equivalent role on the WAN boot server.
-
Copy the wanboot-cgi program to the WAN boot server.
# cp /usr/lib/inet/wanboot/wanboot-cgi /WAN-server-root/cgi-bin/wanboot-cgi
- /WAN-server-root
-
Specifies the root directory of the web server software on the WAN boot server
-
On the WAN boot server, change the permissions of the CGI program to 755.
# chmod 755 /WAN-server-root/cgi-bin/wanboot-cgi
Continuing the WAN Boot Installation
After you copy the WAN boot CGI program to the WAN boot server, you can optionally set up a logging server. For instructions, see (Optional) To Configure the WAN Boot Logging Server.
If you do not want to set up a separate logging server, see (Optional) Protecting Data by Using HTTPS for instructions about how to set up the security features of a WAN boot installation.
See Also
For overview information about the wanboot-cgi program, see What Is WAN Boot?.
 (Optional) To Configure the WAN Boot Logging
Server
(Optional) To Configure the WAN Boot Logging
Server
By default, all WAN boot logging messages are displayed on the client system. This default behavior enables you to quickly debug any installation issues.
If you want to record boot and installation logging messages on a system other than the client, you must set up a logging server. If you want to use a logging server with HTTPS during the installation, you must configure the WAN boot server as the logging server.
To configure the logging server, follow these steps.
-
Copy the bootlog-cgi script to the logging server's CGI script directory.
# cp /usr/lib/inet/wanboot/bootlog-cgi \ log-server-root/cgi-bin
- log-server-root/cgi-bin
-
Specifies the cgi-bin directory in the logging server's web server directory
-
Change the permissions of the bootlog-cgi script to 755.
# chmod 755 log-server-root/cgi-bin/bootlog-cgi
-
Set the value of the boot_logger parameter in the wanboot.conf file.
In the wanboot.conf file, specify the URL of the bootlog-cgi script on the logging server.
For more information about setting parameters in the wanboot.conf file, see To Create the wanboot.conf File.
During the installation, boot and installation log messages are recorded in the /tmp directory of the logging server. The log file is named bootlog.hostname, where hostname is the host name of the client.
Example 11–5 Configuring a Logging Server for WAN Boot Installation Over HTTPS
The following example configures the WAN boot server as a logging server.
# cp /usr/lib/inet/wanboot/bootlog-cgi /opt/apache/cgi-bin/ # chmod 755 /opt/apache/cgi-bin/bootlog-cgi |
Continuing the WAN Boot Installation
After you set up the logging server, you can optionally set up the WAN boot installation to use digital certificates and security keys. See (Optional) Protecting Data by Using HTTPS for instructions about how to set up the security features of a WAN boot installation.
(Optional) Protecting Data by Using HTTPS
To protect your data during the transfer from the WAN boot server to the client, you can use HTTP over Secure Sockets Layer (HTTPS). To use the more secure installation configuration that is described in Secure WAN Boot Installation Configuration, you must enable your web server to use HTTPS.
If you do not want to perform a secure WAN boot, skip the procedures in this section. To continue preparing for your less secure installation, see Creating the Custom JumpStart Installation Files.
To enable the web server software on the WAN boot server to use HTTPS, you must perform the following tasks.
-
Activate Secure Sockets Layer (SSL) support in your web server software.
The processes for enabling SSL support and client authentication vary by web server. This document does not describe how to enable these security features on your web server. For information about these features, see the following documentation.
-
For information about activating SSL on the SunONE and iPlanet web servers, see the SunONE and iPlanet documentation collections on http://docs.sun.com.
-
For information about activating SSL on the Apache web server, see the Apache Documentation Project at http://httpd.apache.org/docs-project/.
-
If you are using web server software that is not listed in the previous list, see your web server software documentation.
-
-
Install digital certificates on the WAN boot server.
For information about using digital certificates with WAN boot, see (Optional) To Use Digital Certificates for Server and Client Authentication.
-
Provide a trusted certificate to the client.
For instructions about how to create a trusted certificate, see (Optional) To Use Digital Certificates for Server and Client Authentication.
-
Create a hashing key and an encryption key.
For instructions about how to create keys, see (Optional) To Create a Hashing Key and an Encryption Key.
-
(Optional) Configure the web server software to support client authentication.
For information about how to configure your web server to support client authentication, see your web server documentation.
This section describes how to use digital certificates and keys in your WAN boot installation.
 (Optional) To Use Digital Certificates
for Server and Client Authentication
(Optional) To Use Digital Certificates
for Server and Client Authentication
The WAN boot installation method can use PKCS#12 files to perform an installation over HTTPS with server or both client and server authentication. For requirements and guidelines about using PKCS#12 files, see Digital Certificate Requirements.
To use a PKCS#12 file in a WAN boot installation, you perform the following tasks.
-
Split the PKCS#12 file into separate SSL private key and trusted certificate files.
-
Insert the trusted certificate in the client's truststore file in the /etc/netboot hierarchy. The trusted certificate instructs the client to trust the server.
-
(Optional) Insert the contents of the SSL private key file in the client's keystore file in the /etc/netboot hierarchy.
The wanbootutil command provides options to perform the tasks in the previous list.
If you do not want to perform a secure WAN boot, skip this procedure. To continue preparing for your less secure installation, see Creating the Custom JumpStart Installation Files.
Follow these steps to create a trusted certificate and a client private key.
Before You Begin
Before you split a PKCS#12 file, create the appropriate subdirectories of the /etc/netboot hierarchy on the WAN boot server.
-
For overview information that describes the /etc/netboot hierarchy, see Storing Configuration and Security Information in the /etc/netboot Hierarchy.
-
For instructions about how to create the /etc/netboot hierarchy, see Creating the /etc/netboot Hierarchy on the WAN Boot Server.
-
Assume the same user role as the web server user on the WAN boot server.
-
Extract the trusted certificate from the PKCS#12 file. Insert the certificate in the client's truststore file in the /etc/netboot hierarchy.
# wanbootutil p12split -i p12cert \ -t /etc/netboot/net-ip/client-ID/truststore
- p12split
-
Option to wanbootutil command that splits a PKCS#12 file into separate private key and certificate files.
- -i p12cert
-
Specifies the name of the PKCS#12 file to split.
- -t /etc/netboot/net-ip/client-ID/truststore
-
Inserts the certificate in the client's truststore file. net-ip is the IP address of the client's subnet. client-ID can be a user-defined ID or the DHCP client ID.
-
(Optional) Decide if you want to require client authentication.
-
If no, go to (Optional) To Create a Hashing Key and an Encryption Key.
-
If yes, continue with the following steps.
-
Insert the client certificate in the client's certstore.
# wanbootutil p12split -i p12cert -c \ /etc/netboot/net-ip/client-ID/certstore -k keyfile
- p12split
-
Option to wanbootutil command that splits a PKCS#12 file into separate private key and certificate files.
- -i p12cert
-
Specifies the name of the PKCS#12 file to split.
- -c /etc/netboot/net-ip/client-ID/certstore
-
Inserts the client's certificate in the client's certstore. net-ip is the IP address of the client's subnet. client-ID can be a user-defined ID or the DHCP client ID.
- -k keyfile
-
Specifies the name of the client's SSL private key file to create from the split PKCS#12 file.
-
Insert the private key in the client's keystore.
# wanbootutil keymgmt -i -k keyfile \ -s /etc/netboot/net-ip/client-ID/keystore -o type=rsa
-
-
Example 11–6 Creating a Trusted Certificate for Server Authentication
In the following example, you use a PKCS#12 file to install client 010003BA152A42 on subnet 192.168.198.0. This command sample extracts a certificate from a PKCS#12 file that is named client.p12. The command then places the contents of the trusted certificate in the client's truststore file.
Before you execute these commands, you must first assume the same user role as the web server user. In this example, the web server user role is nobody.
server# su nobody Password: nobody# wanbootutil p12split -i client.p12 \ -t /etc/netboot/192.168.198.0/010003BA152A42/truststore nobody# chmod 600 /etc/netboot/192.168.198.0/010003BA152A42/truststore |
Continuing the WAN Boot Installation
After you create a digital certificate, create a hashing key and an encryption key. For instructions, see(Optional) To Create a Hashing Key and an Encryption Key.
See Also
For more information about how to create trusted certificates, see the man page wanbootutil(1M).
 (Optional) To Create a Hashing Key and
an Encryption Key
(Optional) To Create a Hashing Key and
an Encryption Key
If you want to use HTTPS to transmit your data, you must create a HMAC SHA1 hashing key and an encryption key. If you plan to install over a semi-private network, you might not want to encrypt the installation data. You can use a HMAC SHA1 hashing key to check the integrity of the wanboot program.
By using the wanbootutil keygen command, you can generate these keys and store them in the appropriate /etc/netboot directory.
If you do not want to perform a secure WAN boot, skip this procedure. To continue preparing for your less secure installation, see Creating the Custom JumpStart Installation Files.
To create a hashing key and an encryption key, follow these steps.
-
Assume the same user role as the web server user on the WAN boot server.
-
Create the master HMAC SHA1 key.
# wanbootutil keygen -m
- keygen -m
-
Creates the master HMAC SHA1 key for the WAN boot server
-
Create the HMAC SHA1 hashing key for the client from the master key.
# wanbootutil keygen -c -o [net=net-ip,{cid=client-ID,}]type=sha1- -c
-
Creates the client's hashing key from the master key.
- -o
-
Indicates that additional options are included for the wanbootutil keygen command.
- (Optional) net=net-ip
-
Specifies the IP address for the client's subnet. If you do not use the net option, the key is stored in the /etc/netboot/keystore file, and can be used by all WAN boot clients.
- (Optional) cid=client-ID
-
Specifies the client ID. The client ID can be a user-defined ID or the DHCP client ID. The cid option must be preceded by a valid net= value. If you do not specify the cid option with the net option, the key is stored in the /etc/netboot/net-ip/keystore file. This key can be used by all WAN boot clients on the net-ip subnet.
- type=sha1
-
Instructs the wanbootutil keygen utility to create a HMAC SHA1 hashing key for the client.
-
Decide if you need to create an encryption key for the client.
You need to create an encryption key to perform a WAN boot installation over HTTPS. Before the client establishes an HTTPS connection with the WAN boot server, the WAN boot server transmits encrypted data and information to the client. The encryption key enables the client to decrypt this information and use this information during the installation.
-
If you are performing a more secure WAN installation over HTTPS with server authentication, continue.
-
If you only want to check the integrity of the wanboot program, you do not need to create an encryption key. Go to Step 6.
-
-
Create an encryption key for the client.
# wanbootutil keygen -c -o [net=net-ip,{cid=client-ID,}]type=key-type- -c
-
Creates the client's encryption key.
- -o
-
Indicates that additional options are included for the wanbootutil keygen command.
- (Optional) net=net-ip
-
Specifies the network IP address for the client. If you do not use the net option, the key is stored in the /etc/netboot/keystore file, and can be used by all WAN boot clients.
- (Optional) cid=client-ID
-
Specifies the client ID. The client ID can be a user-defined ID, or the DHCP client ID. The cid option must be preceded by a valid net= value. If you do not specify the cid option with the net option, the key is stored in the /etc/netboot/net-ip/keystore file. This key can be used by all WAN boot clients on the net-ip subnet.
- type=key-type
-
Instructs the wanbootutil keygen utility to create an encryption key for the client. key-type can have a value of 3des or aes.
-
Install the keys on the client system.
For instructions about how to install keys on the client, see Installing Keys on the Client.
Example 11–7 Creating Required Keys for WAN Boot Installation Over HTTPS
The following example creates a master HMAC SHA1 key for the WAN boot server. This example also creates a HMAC SHA1 hashing key and 3DES encryption key for client 010003BA152A42 on subnet 192.168.198.0.
Before you execute these commands, you must first assume the same user role as the web server user. In this example, the web server user role is nobody.
server# su nobody Password: nobody# wanbootutil keygen -m nobody# wanbootutil keygen -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 nobody# wanbootutil keygen -c -o net=192.168.198.0,cid=010003BA152A42,type=3des |
Continuing the WAN Boot Installation
After you create a hashing and an encryption key, you must create the installation files. For instructions, see Creating the Custom JumpStart Installation Files.
See Also
For overview information on hashing keys and encryption keys, see Protecting Data During a WAN Boot Installation.
For more information about how to create hashing and encryption keys, see the man page wanbootutil(1M).
Creating the Custom JumpStart Installation Files
WAN boot performs a custom JumpStart installation to install a Solaris Flash archive on the client. The custom JumpStart installation method is a command–line interface that enables you to automatically install several systems, based on profiles that you create. The profiles define specific software installation requirements. You can also incorporate shell scripts to include preinstallation and postinstallation tasks. You choose which profile and scripts to use for installation or upgrade. The custom JumpStart installation method installs or upgrades the system, based on the profile and scripts that you select. Also, you can use a sysidcfg file to specify configuration information so that the custom JumpStart installation is completely free of manual intervention.
To prepare the custom JumpStart files for a WAN boot installation, complete the following tasks.
For detailed information on the custom JumpStart installation method, see Chapter 2, Custom JumpStart (Overview), in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
 To Create the Solaris Flash Archive
To Create the Solaris Flash Archive
The Solaris Flash installation feature enables you to use a single reference installation of the Solaris OS on a system, which is called the master system. You can then create a Solaris Flash archive, which is a replica image of the master system. You can install the Solaris Flash archive on other systems in the network, creating clone systems.
This section describes how to create a Solaris Flash archive.
Before You Begin
-
Before you create a Solaris Flash archive, you must first install the master system.
-
For information about installing a master system, see Installing the Master System in Solaris 10 8/07 Installation Guide: Solaris Flash Archives (Creation and Installation).
-
For detailed information about Solaris Flash archives, see Chapter 1, Solaris Flash (Overview), in Solaris 10 8/07 Installation Guide: Solaris Flash Archives (Creation and Installation).
-
-
File Size Issues:
Check your web server software documentation to verify that the software can transmit files that are the size of a Solaris Flash archive.
-
Check your web server software documentation to verify that the software can transmit files that are the size of a Solaris Flash archive.
-
The flarcreate command no longer has size limitations on individual files. You can create a Solaris Flash archive that contains individual files over 4 Gbytes.
For more information, see Creating an Archive That Contains Large Files in Solaris 10 8/07 Installation Guide: Solaris Flash Archives (Creation and Installation).
-
-
Boot the master system.
Run the master system in as inactive a state as possible. When possible, run the system in single-user mode. If that is not possible, shut down any applications that you want to archive and any applications that require extensive operating system resources.
-
To create the archive, use the flarcreate command.
# flarcreate -n name [optional-parameters] document-root/flash/filename
- name
-
The name that you give the archive. The name you specify is the value of the content_name keyword.
- optional-parameters
-
You can use several options to the flarcreate command to customize your Solaris Flash archive. For detailed descriptions of these options, see Chapter 5, Solaris Flash (Reference), in Solaris 10 8/07 Installation Guide: Solaris Flash Archives (Creation and Installation).
- document-root/flash
-
The path to the Solaris Flash subdirectory of the install server's document root directory.
- filename
-
The name of the archive file.
To conserve disk space, you might want to use the -c option to the flarcreate command to compress the archive. However, a compressed archive can affect the performance of your WAN boot installation. For more information about creating a compressed archive, see the man page flarcreate(1M).
-
If the archive creation is successful, the flarcreate command returns an exit code of 0.
-
If the archive creation fails, the flarcreate command returns a nonzero exit code.
Example 11–8 Creating a Solaris Flash Archive for a WAN Boot Installation
In this example, you create your Solaris Flash archive by cloning the WAN boot server system with the host name wanserver. The archive is named sol_10_sparc, and is copied exactly from the master system. The archive is an exact duplicate of the master system. The archive is stored in sol_10_sparc.flar. You save the archive in the flash/archives subdirectory of the document root directory on the WAN boot server.
wanserver# flarcreate -n sol_10_sparc \ /opt/apache/htdocs/flash/archives/sol_10_sparc.flar |
Continuing the WAN Boot Installation
After you create the Solaris Flash archive, preconfigure the client information in the sysidcfg file. For instructions, see To Create the sysidcfg File.
See Also
For detailed instructions about how to create a Solaris Flash archive, see Chapter 3, Creating Solaris Flash Archives (Tasks), in Solaris 10 8/07 Installation Guide: Solaris Flash Archives (Creation and Installation).
For more information about the flarcreate command, see the man page flarcreate(1M).
 To Create the sysidcfg File
To Create the sysidcfg File
You can specify a set of keywords in the sysidcfg file to preconfigure a system.
To create the sysidcfg file, follow these steps.
Before You Begin
Create the Solaris Flash archive. See To Create the Solaris Flash Archive for detailed instructions.
-
Create a file called sysidcfg in a text editor on the install server.
-
Type the sysidcfg keywords you want.
For detailed information about sysidcfg keywords, see sysidcfg File Keywords.
-
Save the sysidcfg file in a location that is accessible to the WAN boot server.
Save the file to one of the following locations.
-
If the WAN boot server and install server are hosted on the same machine, save this file to the flash subdirectory of the document root directory on the WAN boot server.
-
If the WAN boot server and install server are not on the same machine, save this file to the flash subdirectory of the document root directory of the install server.
-
Example 11–9 sysidcfg File for WAN Boot Installation
The following is an example of a sysidcfg file for a SPARC based system. The host name, IP address, and netmask of this system have been preconfigured by editing the naming service.
network_interface=primary {hostname=wanclient
default_route=192.168.198.1
ip_address=192.168.198.210
netmask=255.255.255.0
protocol_ipv6=no}
timezone=US/Central
system_locale=C
terminal=xterm
timeserver=localhost
name_service=NIS {name_server=matter(192.168.255.255)
domain_name=mind.over.example.com
}
security_policy=none
Continuing the WAN Boot Installation
After you create the sysidcfg file, create a custom JumpStart profile for the client. For instructions, see To Create the Profile.
See Also
For more detailed information about sysidcfg keywords and values, see Preconfiguring With the sysidcfg File.
 To Create the Profile
To Create the Profile
A profile is a text file that instructs the custom JumpStart program how to install the Solaris software on a system. A profile defines elements of the installation, for example, the software group to install.
For detailed information about how to create profiles, see Creating a Profile in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
To create the profile, follow these steps.
Before You Begin
Create the sysidcfg file for the client. See To Create the sysidcfg File for detailed instructions.
-
Create a text file on the install server. Name the file descriptively.
Ensure that the name of the profile reflects how you intend to use the profile to install the Solaris software on a system. For example, you might name the profiles basic_install, eng_profile, or user_profile.
-
Add profile keywords and values to the profile.
For a list of profile keywords and values, see Profile Keywords and Values in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
Profile keywords and their values are case sensitive.
-
Save the profile in a location that is accessible to the WAN boot server.
Save the profile in one of the following locations.
-
If the WAN boot server and install server are hosted on the same machine, save this file to the flash subdirectory of the document root directory on the WAN boot server.
-
If the WAN boot server and install server are not on the same machine, save this file to the flash subdirectory of the document root directory of the install server.
-
-
Ensure that root owns the profile and that the permissions are set to 644.
-
(Optional) Test the profile.
Testing a Profile in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations contains information about testing profiles.
Example 11–10 Retrieving a Solaris Flash Archive From a Secure HTTP Server
In the following example, the profile indicates that the custom JumpStart program retrieves the Solaris Flash archive from a secure HTTP server.
# profile keywords profile values # ---------------- ------------------- install_type flash_install archive_location https://192.168.198.2/sol_10_sparc.flar partitioning explicit filesys c0t1d0s0 4000 / filesys c0t1d0s1 512 swap filesys c0t1d0s7 free /export/home
The following list describes some of the keywords and values from this example.
- install_type
-
The profile installs a Solaris Flash archive on the clone system. All files are overwritten as in an initial installation.
- archive_location
-
The compressed Solaris Flash archive is retrieved from a secure HTTP server.
- partitioning
-
The file system slices are determined by the filesys keywords, value explicit. The size of root (/) is based on the size of the Solaris Flash archive. The size of swap is set to the necessary size and is installed on c0t1d0s1. /export/home is based on the remaining disk space. /export/home is installed on c0t1d0s7.
Continuing the WAN Boot Installation
After you create a profile, you must create and validate the rules file. For instructions, see To Create the rules File.
See Also
For more information about how to create a profile, see Creating a Profile in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
For more detailed information about profile keywords and values, see Profile Keywords and Values in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
 To Create the rules File
To Create the rules File
The rules file is a text file that contains a rule for each group of systems on which you want to install the Solaris OS. Each rule distinguishes a group of systems that are based on one or more system attributes. Each rule also links each group to a profile. A profile is a text file that defines how the Solaris software is to be installed on each system in the group. For example, the following rule specifies that the JumpStart program use the information in the basic_prof profile to install any system with the sun4u platform group.
karch sun4u - basic_prof - |
The rules file is used to create the rules.ok file, which is required for custom JumpStart installations.
For detailed information about how to create a rules file, see Creating the rules File in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
To create the rules file, follow these steps.
Before You Begin
Create the profile for the client. See To Create the Profile for detailed instructions.
-
On the install server, create a text file that is named rules.
-
Add a rule in the rules file for each group of systems you want to install.
For detailed information about how to create a rules file, see Creating the rules File in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
-
Save the rules file on the install server.
-
$ ./check -p path -r file-name
- -p path
-
Validates the rules by using the check script from the current Solaris release software image instead of the check script from the system you are using. path is the image on a local disk or a mounted Solaris DVD or a Solaris Software - 1 CD.
Use this option to run the most recent version of check if your system is running a previous version of the Solaris OS.
- -r file_name
-
Specifies a rules file other than the file that is named rules. By using this option, you can test the validity of a rule before you integrate the rule into the rules file.
As the check script runs, the script reports the checking of the validity of the rules file and each profile. If no errors are encountered, the script reports: The custom JumpStart configuration is ok. The check script creates the rules.ok file.
-
Save the rules.ok file in a location that is accessible to the WAN boot server.
Save the file to one of the following locations.
-
If the WAN boot server and install server are hosted on the same machine, save this file to the flash subdirectory of the document root directory on the WAN boot server.
-
If the WAN boot server and install server are not on the same machine, save this file to the flash subdirectory of the document root directory of the install server.
-
-
Ensure that root owns the rules.ok file and that the permissions are set to 644.
Example 11–11 Creating and Validating the rules File
The custom JumpStart programs use the rules file to select the correct installation profile for the wanclient-1 system. Create a text file that is named rules. Then, add keywords and values to this file.
The IP address of the client system is 192.168.198.210, and the netmask is 255.255.255.0. Use the network rule keyword to specify the profile that the custom JumpStart programs should use to install the client.
network 192.168.198.0 - wanclient_prof - |
This rules file instructs the custom JumpStart programs to use the wanclient_prof to install the current Solaris release software on the client.
Name this rule file wanclient_rule.
After you create the profile and the rules file, you run the check script to verify that the files are valid.
wanserver# ./check -r wanclient_rule |
If the check script does not find any errors, the script creates the rules.ok file.
Save the rules.ok file in the /opt/apache/htdocs/flash/ directory.
Continuing the WAN Boot Installation
After you create the rules.ok file, you can optionally set up begin and finish scripts for your installation. For instructions, see (Optional) Creating Begin and Finish Scripts.
If you do not want to set up begin and finish scripts, see Creating the Configuration Files to continue the WAN boot installation.
See Also
For more information about how to create a rules file, see Creating the rules File in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
For more detailed information about rules file keywords and values, see Rule Keywords and Values in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
(Optional) Creating Begin and Finish Scripts
Begin and finish scripts are user-defined Bourne shell scripts that you specify in the rules file. A begin script performs tasks before the Solaris software is installed on a system. A finish script performs tasks after the Solaris software is installed on a system, but before the system reboots. You can use these scripts only when using custom JumpStart to install Solaris.
You can use begin scripts to create derived profiles. Finish scripts enable you to perform various postinstallation tasks, such as adding files, packages, patches, or additional software.
You must store the begin and finish scripts in the same directory as the sysidcfg, rules.ok, and profile files on the install server.
-
For more information about creating begin scripts, see Creating Begin Scripts in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
-
For more information about creating finish scripts, see Creating Finish Scripts in Solaris 10 8/07 Installation Guide: Custom JumpStart and Advanced Installations.
To continue preparing for your WAN boot installation, see Creating the Configuration Files.
Creating the Configuration Files
WAN boot uses the following files to specify the location of the data and files that are required for a WAN boot installation.
-
System configuration file (system.conf)
-
wanboot.conf file
This section describes how to create and store these two files.
 To Create the System Configuration File
To Create the System Configuration File
In the system configuration file, you can direct the WAN boot installation programs to the following files.
-
sysidcfg file
-
rules.ok file
-
Custom JumpStart profile
WAN boot follows the pointers in the system configuration file to install and configure the client.
The system configuration file is a plain text file, and must be formatted in the following pattern.
setting=value |
To use a system configuration file to direct the WAN installation programs to the sysidcfg, rules.ok, and profile files, follow these steps.
Before You Begin
Before you create the system configuration file, you must create the installation files for you WAN boot installation. See Creating the Custom JumpStart Installation Files for detailed instructions.
-
Assume the same user role as the web server user on the WAN boot server.
-
Create a text file. Name the file descriptively, for example, sys-conf.s10–sparc.
-
Add the following entries to the system configuration file.
- SsysidCF=sysidcfg-file-URL
-
This setting points to the flash directory on the install server that contains the sysidcfg file. Make sure that this URL matches the path to the sysidcfg file that you created in To Create the sysidcfg File.
For WAN installations that use HTTPS, set the value to a valid HTTPS URL.
- SjumpsCF=jumpstart-files-URL
-
This setting points to the Solaris Flash directory on the install server that contains the rules.ok file, profile file, and begin and finish scripts. Make sure that this URL matches the path to the custom JumpStart files that you created in To Create the Profile and To Create the rules File.
For WAN installations that use HTTPS, set the value to a valid HTTPS URL.
-
Save the file to a directory that is accessible to the WAN boot server.
For administration purposes, you might want to save the file to the appropriate client directory in the /etc/netboot directory on the WAN boot server.
-
Change the permissions on the system configuration file to 600.
# chmod 600 /path/system-conf-file
Example 11–12 System Configuration File for WAN Boot Installation Over HTTPS
In the following example, the WAN boot programs check for the sysidcfg and custom JumpStart files on the web server https://www.example.com on port 1234. The web server uses secure HTTP to encrypt data and files during the installation.
The sysidcfg and custom JumpStart files are located in the flash subdirectory of the document root directory /opt/apache/htdocs.
SsysidCF=https://www.example.com:1234/flash SjumpsCF=https://www.example.com:1234/flash
Example 11–13 System Configuration File for Insecure WAN Boot Installation
In the following example, the WAN boot programs check for the sysidcfg and custom JumpStart files on the web server http://www.example.com. The web server uses HTTP, so the data and files are not protected during the installation.
The sysidcfg and custom JumpStart files are located in the flash subdirectory of the document root directory /opt/apache/htdocs.
SsysidCF=http://www.example.com/flash SjumpsCF=http://www.example.com/flash
Continuing the WAN Boot Installation
After you create the system configuration file, create the wanboot.conf file. For instructions, see To Create the wanboot.conf File.
 To Create the wanboot.conf File
To Create the wanboot.conf File
The wanboot.conf file is a plain text configuration file that the WAN boot programs use to perform a WAN installation. The wanboot-cgi program, the boot file system, and the WAN boot miniroot all use the information included in the wanboot.conf file to install the client machine.
Save the wanboot.conf file in the appropriate client subdirectory in the /etc/netboot hierarchy on the WAN boot server. For information about how to define the scope of your WAN boot installation with the /etc/netboot hierarchy, see Creating the /etc/netboot Hierarchy on the WAN Boot Server.
If the WAN boot server is running the current Solaris release, a sample wanboot.conf file is located in /etc/netboot/wanboot.conf.sample. You can use this sample as a template for your WAN boot installation.
You must include the following information in the wanboot.conf file.
You specify this information by listing parameters with associated values in the following format.
parameter=value |
For detailed information about wanboot.conf file parameters and syntax, see wanboot.conf File Parameters and Syntax.
To create the wanboot.conf file, follow these steps.
-
Assume the same user role as the web server user on the WAN boot server.
-
Create the wanboot.conf text file.
You can create a new text file that is named wanboot.conf, or use the sample file that is located in /etc/netboot/wanboot.conf.sample. If you use the sample file, rename the file wanboot.conf after you add parameters.
-
Type the wanboot.conf parameters and values for your installation.
For detailed descriptions of wanboot.conf parameters and values, see wanboot.conf File Parameters and Syntax.
-
Save the wanboot.conf file to the appropriate subdirectory of the /etc/netboot hierarchy.
For information about how to create the /etc/netboot hierarchy, see Creating the /etc/netboot Hierarchy on the WAN Boot Server.
-
Validate the wanboot.conf file.
# bootconfchk /etc/netboot/path-to-wanboot.conf/wanboot.conf
- path-to-wanboot.conf
-
Specifies the path to the client's wanboot.conf file on the WAN boot server
-
If the wanboot.conf file is structurally valid, the bootconfchk command returns an exit code of 0.
-
If the wanboot.conf file is invalid, the bootconfchk command returns a nonzero exit code.
-
Change the permissions on the wanboot.conf file to 600.
# chmod 600 /etc/netboot/path-to-wanboot.conf/wanboot.conf
Example 11–14 wanboot.conf File for WAN Boot Installation Over HTTPS
The following wanboot.conf file example includes configuration information for a WAN installation that uses secure HTTP. The wanboot.conf file also indicates that a 3DES encryption key is used in this installation.
boot_file=/wanboot/wanboot.s10_sparc root_server=https://www.example.com:1234/cgi-bin/wanboot-cgi root_file=/miniroot/miniroot.s10_sparc signature_type=sha1 encryption_type=3des server_authentication=yes client_authentication=no resolve_hosts= boot_logger=https://www.example.com:1234/cgi-bin/bootlog-cgi system_conf=sys-conf.s10–sparc
This wanboot.conf file specifies the following configuration.
- boot_file=/wanboot/wanboot.s10_sparc
-
The second level boot program is named wanboot.s10_sparc. This program is located in the /wanboot directory in the WAN boot server's document root directory.
- root_server=https://www.example.com:1234/cgi-bin/wanboot-cgi
-
The location of the wanboot-cgi program on the WAN boot server is https://www.example.com:1234/cgi-bin/wanboot-cgi. The https portion of the URL indicates that this WAN boot installation uses secure HTTP.
- root_file=/miniroot/miniroot.s10_sparc
-
The WAN boot miniroot is named miniroot.s10_sparc. This miniroot is located in the /miniroot directory in the WAN boot server's document root directory.
- signature_type=sha1
-
The wanboot.s10_sparc program and the WAN boot file system are signed with a HMAC SHA1 hashing key.
- encryption_type=3des
-
The wanboot.s10_sparc program and the boot file system are encrypted with a 3DES key.
- server_authentication=yes
-
The server is authenticated during the installation.
- client_authentication=no
-
The client is not authenticated during the installation.
- resolve_hosts=
-
No additional host names are needed to perform the WAN installation. All required files and information are located in the document root directory on the WAN boot server.
- boot_logger=https://www.example.com:1234/cgi-bin/bootlog-cgi
-
(Optional) Booting and installation log messages are recorded on the WAN boot server by using secure HTTP.
For instructions on how to set up a logging server for your WAN boot installation, see (Optional) To Configure the WAN Boot Logging Server.
- system_conf=sys-conf.s10–sparc
-
The system configuration file that contains the locations of the sysidcfg and JumpStart files is located in a subdirectory of the /etc/netboot hierarchy. The system configuration file is named sys-conf.s10–sparc.
Example 11–15 wanboot.conf File for Insecure WAN Boot Installation
The following wanboot.conf file example includes configuration information for a less secure WAN boot installation that uses HTTP. This wanboot.conf file also indicates that the installation does not use an encryption key or a hashing key.
boot_file=/wanboot/wanboot.s10_sparc root_server=http://www.example.com/cgi-bin/wanboot-cgi root_file=/miniroot/miniroot.s10_sparc signature_type= encryption_type= server_authentication=no client_authentication=no resolve_hosts= boot_logger=http://www.example.com/cgi-bin/bootlog-cgi system_conf=sys-conf.s10–sparc
This wanboot.conf file specifies the following configuration.
- boot_file=/wanboot/wanboot.s10_sparc
-
The second level boot program is named wanboot.s10_sparc. This program is located in the /wanboot directory in the WAN boot server's document root directory.
- root_server=http://www.example.com/cgi-bin/wanboot-cgi
-
The location of the wanboot-cgi program on the WAN boot server is http://www.example.com/cgi-bin/wanboot-cgi. This installation does not use secure HTTP.
- root_file=/miniroot/miniroot.s10_sparc
-
The WAN boot miniroot is named miniroot.s10_sparc. This miniroot is located in the /miniroot subdirectory in the WAN boot server's document root directory.
- signature_type=
-
The wanboot.s10_sparc program and the WAN boot file system are not signed with a hashing key.
- encryption_type=
-
The wanboot.s10_sparc program and the boot file system are not encrypted.
- server_authentication=no
-
The server is not authenticated with keys or certificates during the installation.
- client_authentication=no
-
The client is not authenticated with keys or certificates during the installation.
- resolve_hosts=
-
No additional host names are needed to perform the installation. All required files and information are located in the document root directory on the WAN boot server.
- boot_logger=http://www.example.com/cgi-bin/bootlog-cgi
-
(Optional) Booting and installation log messages are recorded on the WAN boot server.
For instructions on how to set up a logging server for your WAN boot installation, see (Optional) To Configure the WAN Boot Logging Server.
- system_conf=sys-conf.s10–sparc
-
The system configuration file that contains the locations of the sysidcfg and JumpStart files is named sys-conf.s10–sparc. This file is located in the appropriate client subdirectory of the /etc/netboot hierarchy.
Continuing the WAN Boot Installation
After you create the wanboot.conf file, you can optionally configure a DHCP server to support WAN boot. For instructions, see (Optional) Providing Configuration Information With a DHCP Server.
If you do not want to use a DHCP server in your WAN boot installation, see To Check the net Device Alias in the Client OBP to continue the WAN boot installation.
See Also
For detailed descriptions of wanboot.conf parameters and values, see wanboot.conf File Parameters and Syntax and the man page wanboot.conf(4).
(Optional) Providing Configuration Information With a DHCP Server
If you use a DHCP server on your network, you can configure the DHCP server to supply the following information.
-
Proxy server's IP address
-
Location of the wanboot-cgi program
You can use the following DHCP vendor options in your WAN boot installation.
- SHTTPproxy
- SbootURI
-
Specifies the URL of the wanboot-cgi program on the WAN boot server
For information about setting these vendor options on a Solaris DHCP server, see Preconfiguring System Configuration Information With the DHCP Service (Tasks).
For detailed information about setting up a Solaris DHCP server, see Chapter 14, Configuring the DHCP Service (Tasks), in System Administration Guide: IP Services.
To continue with your WAN boot installation, see Chapter 12, SPARC: Installing With WAN Boot (Tasks).
Chapter 12 SPARC: Installing With WAN Boot (Tasks)
This chapter describes how to perform a WAN boot installation on a SPARC based client. For information about how to prepare for a WAN boot installation, see Chapter 11, Installing With WAN Boot (Tasks).
This chapter describes the following tasks.
Task Map: Installing a Client With WAN Boot
The following table lists the tasks you need to perform to install a client over a WAN.
Table 12–1 Task Map: Performing a WAN Boot Installation|
Task |
Description |
For Instructions |
|---|---|---|
|
Prepare the network for a WAN boot installation. |
Set up the servers and files that are required to perform a WAN boot installation. | |
|
Verify that the net device alias is set correctly in the client OBP. |
Use the devalias command to verify that the net device alias is set to the primary network interface. | |
|
Provide keys to the client |
Provide keys to the client by setting OBP variables or entering key values during the installation. This task is required for secure installation configurations. For insecure installations that check data integrity, complete this task to provide the HMAC SHA1 hashing key to the client. | |
|
Install the client over a wide area network. |
Choose the appropriate method to install your client. |
To Perform a Noninteractive WAN Boot Installation To Perform an Interactive WAN Boot Installation |
Preparing the Client for a WAN Boot Installation
Before you install the client system, prepare the client by performing the following tasks.
 To Check the net Device
Alias in the Client OBP
To Check the net Device
Alias in the Client OBP
To boot the client from the WAN with the boot net, the net device alias must be set to the client's primary network device. On most systems, this alias is already set correctly. However, if the alias is not set to the network device you want to use, you must change the alias.
For more information about setting device aliases, see “The Device Tree” in OpenBoot 3.x Command Reference Manual.
Follow these steps to check the net device alias on the client.
-
Become superuser or assume an equivalent role on the client.
-
Bring the system to run level 0.
# init 0
The ok prompt is displayed.
-
At the ok prompt, check device aliases that are set in the OBP.
ok devalias
The devalias command outputs information that is similar to the following example.
screen /pci@1f,0/pci@1,1/SUNW,m64B@2 net /pci@1f,0/pci@1,1/network@c,1 net2 /pci@1f,0/pci@1,1/network@5,1 disk /pci@1f,0/pci@1/scsi@8/disk@0,0 cdrom /pci@1f,0/pci@1,1/ide@d/cdrom@0,0:f keyboard /pci@1f,0/pci@1,1/ebus@1/su@14,3083f8 mouse /pci@1f,0/pci@1,1/ebus@1/su@14,3062f8
-
If the net alias is set to the network device you wan to use during the installation, you do not need to reset the alias. Go to Installing Keys on the Client to continue your installation.
-
If the net alias is not set to the network device you want to use, you must reset the alias. Continue.
-
-
Set the net device alias.
Choose one of the following commands to set the net device alias.
Example 12–1 Checking and Resetting the net Device Alias
The following commands show how to check and reset the net device alias.
Check the device aliases.
ok devalias screen /pci@1f,0/pci@1,1/SUNW,m64B@2 net /pci@1f,0/pci@1,1/network@c,1 net2 /pci@1f,0/pci@1,1/network@5,1 disk /pci@1f,0/pci@1/scsi@8/disk@0,0 cdrom /pci@1f,0/pci@1,1/ide@d/cdrom@0,0:f keyboard /pci@1f,0/pci@1,1/ebus@1/su@14,3083f8 mouse /pci@1f,0/pci@1,1/ebus@1/su@14,3062f8 |
If you want to use the /pci@1f,0/pci@1,1/network@5,1 network device, type the following command.
ok devalias net /pci@1f,0/pci@1,1/network@5,1 |
Continuing the WAN Boot Installation
After you check the net device alias, see the appropriate section to continue the installation.
-
If you are using a hashing key and an encryption key in your installation, see Installing Keys on the Client.
-
If you are performing a less secure installation without keys, see Installing the Client.
Installing Keys on the Client
For a more secure WAN boot installation or an insecure installation with data integrity checking, you must install keys on the client. By using a hashing key and an encryption key, you can protect the data that is transmitted to the client. You can install these keys in the following ways.
-
Set OBP variables – You can assign key values to OBP network boot argument variables before you boot the client. These keys can then be used for future WAN boot installations of the client.
-
Enter the key values during the boot process – You can set key values at the wanboot program boot> prompt. If you use this method to install keys, the keys are only used for the current WAN boot installation.
You can also install keys in the OBP of a running client. If you want to install keys on a running client, the system must be running the Solaris 9 12/03 OS, or compatible version.
When you install keys on your client, ensure that the key values are not transmitted over an insecure connection. Follow your site's security policies to ensure the privacy of the key values.
-
For instructions about how to assign key values to OBP network boot argument variables, see To Install Keys in the Client OBP.
-
For instructions about how to install keys during the boot process, see To Perform an Interactive WAN Boot Installation.
-
For instructions about how to install keys in the OBP of a running client, see To Install a Hashing Key and an Encryption Key on a Running Client.
 To Install Keys in the Client OBP
To Install Keys in the Client OBP
You can assign key values to OBP network boot argument variables before you boot the client. These keys can then be used for future WAN boot installations of the client.
To install keys in the client OBP, follow these steps.
If you want to assign key values to OBP network boot argument variables, follow these steps.
-
Assume the same user role as the web server user on the WAN boot server.
-
Display the key value for each client key.
# wanbootutil keygen -d -c -o net=net-ip,cid=client-ID,type=key-type
- net-ip
-
The IP address of the client's subnet.
- client-ID
-
The ID of the client you want to install. The client ID can be a user-defined ID or the DHCP client ID.
- key-type
-
The key type you want to install on the client. Valid key types are 3des, aes, or sha1.
The hexadecimal value for the key is displayed.
-
Repeat the previous step for each type of client key you want to install.
-
Bring the client system to run level 0.
# init 0
The ok prompt is displayed.
-
At the client ok prompt, set the value for the hashing key.
ok set-security-key wanboot-hmac-sha1 key-value
- set-security-key
-
Installs the key on the client
- wanboot-hmac-sha1
-
Instructs OBP to install a HMAC SHA1 hashing key
- key-value
-
Specifies the hexadecimal string that is displayed in Step 2.
The HMAC SHA1 hashing key is installed in the client OBP.
-
At the client ok prompt, install the encryption key.
ok set-security-key wanboot-3des key-value
- set-security-key
-
Installs the key on the client
- wanboot-3des
-
Instructs OBP to install a 3DES encryption key. If you want to use an AES encryption key, set this value to wanboot-aes.
- key-value
-
Specifies the hexadecimal string that represents the encryption key.
The 3DES encryption key is installed in the client OBP.
After you install the keys, you are ready to install the client. See Installing the Client for instructions about how to install the client system.
-
(Optional) Verify that the keys are set in the client OBP.
ok list-security-keys Security Keys: wanboot-hmac-sha1 wanboot-3des -
(Optional) If you need to delete a key, type the following command.
ok set-security-key key-type
Example 12–2 Installing Keys in the Client OBP
The following example shows how to install a hashing key and an encryption key in the client OBP.
Display the key values on the WAN boot server.
# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 # wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous example uses the following information.
- net=192.168.198.0
-
Specifies the IP address of the client's subnet
- cid=010003BA152A42
-
Specifies the client's ID
- b482aaab82cb8d5631e16d51478c90079cc1d463
-
Specifies the value of the client's HMAC SHA1 hashing key
- 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04
-
Specifies the value of the client's 3DES encryption key
If you use an AES encryption key in your installation, change wanboot-3des to wanboot-aes to display the encryption key value.
Install the keys on the client system.
ok set-security-key wanboot-hmac-sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 ok set-security-key wanboot-3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous commands perform the following tasks.
-
Installs the HMAC SHA1 hashing key with a value of b482aaab82cb8d5631e16d51478c90079cc1d463 on the client
-
Installs the 3DES encryption key with a value of 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 on the client
If you use an AES encryption key in your installation, change wanboot-3des to wanboot-aes.
Continuing the WAN Boot Installation
After you install keys on your client, you are ready to install the client over the WAN. For instructions, see Installing the Client.
See Also
For more information about how to display key values, see the man page wanbootutil(1M).
 To Install a Hashing Key and an Encryption
Key on a Running Client
To Install a Hashing Key and an Encryption
Key on a Running Client
You can set key values at the wanboot program boot> prompt on a running system. If you use this method to install keys, the keys are only used for the current WAN boot installation.
If you want to install a hashing key and an encryption key in the OBP of a running client, follow these steps.
Before You Begin
This procedure makes the following assumptions.
-
The client system is powered on.
-
The client is accessible over a secure connection, such as a secure shell (ssh).
-
Assume the same user role as the web server user on the WAN boot server.
-
Display the key value for the client keys.
# wanbootutil keygen -d -c -o net=net-ip,cid=client-ID,type=key-type
- net-ip
-
The IP address of the client's subnet.
- client-ID
-
The ID of the client you want to install. The client ID can be a user-defined ID or the DHCP client ID.
- key-type
-
The key type you want to install on the client. Valid key types are 3des, aes, or sha1.
The hexadecimal value for the key is displayed.
-
Repeat the previous step for each type of client key you want to install.
-
Become superuser or assume an equivalent role on the client machine.
-
Install the necessary keys on the running client machine.
# /usr/lib/inet/wanboot/ickey -o type=key-type > key-value
- key-type
-
Specifies the key type you want to install on the client. Valid key types are 3des, aes, or sha1.
- key-value
-
Specifies the hexadecimal string that is displayed in Step 2.
-
Repeat the previous step for each type of client key you want to install.
After you install the keys, you are ready to install the client. See Installing the Client for instructions about how to install the client system.
Example 12–3 Installing Keys in the OBP of a Running Client System
The following example shows how to install keys in the OBP of a running client.
Display the key values on the WAN boot server.
# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 # wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous example uses the following information.
- net=192.168.198.0
-
Specifies the IP address of the client's subnet
- cid=010003BA152A42
-
Specifies the client's ID
- b482aaab82cb8d5631e16d51478c90079cc1d463
-
Specifies the value of the client's HMAC SHA1 hashing key
- 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04
-
Specifies the value of the client's 3DES encryption key
If you use an AES encryption key in your installation, change type=3des to type=aes to display the encryption key value.
Install the keys in the OBP of the running client.
# /usr/lib/inet/wanboot/ickey -o type=sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 # /usr/lib/inet/wanboot/ickey -o type=3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous commands perform the following tasks.
-
Installs a HMAC SHA1 hashing key with a value of b482aaab82cb8d5631e16d51478c90079cc1d463 on the client
-
Installs a 3DES encryption key with a value of 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 on the client
Continuing the WAN Boot Installation
After you install keys on your client, you are ready to install the client over the WAN. For instructions, see Installing the Client.
See Also
For more information about how to display key values, see the man page wanbootutil(1M).
For additional information about how to install keys on a running system, see ickey(1M).
Installing the Client
When you finish preparing your network for a WAN boot installation, you can choose from the following ways to install the system.
Table 12–2 Methods to Install the Client|
Method |
Description |
Instructions |
|---|---|---|
|
Noninteractive installation |
Use this installation method if you want to install keys on the client and set the client configuration information before you boot the client. |
|
|
Interactive installation |
Use this installation method if you want to set the client configuration information during the boot process. | |
|
Installing with a DHCP server |
Use this installation method if you configured the network DHCP server to provide client configuration information during the installation. |
|
|
Installing with local CD media |
If your client OBP does not support WAN boot, boot the client from a local copy of the Solaris Software CD. |
|
 To Perform a Noninteractive WAN Boot Installation
To Perform a Noninteractive WAN Boot Installation
Use this installation method if you prefer to install keys and set client configuration information before you install the client. You can then boot the client from the WAN and perform an unattended installation.
This procedure assumes that you have either installed keys in the client's OBP, or that you are performing an insecure installation. For information about installing keys on the client before your installation, see Installing Keys on the Client.
-
If the client system is currently running, bring the system to run level 0.
# init 0
The ok prompt is displayed.
-
At the ok prompt on the client system, set the network boot argument variables in OBP.
ok setenv network-boot-arguments host-ip=client-IP, router-ip=router-ip,subnet-mask=mask-value, hostname=client-name,http-proxy=proxy-ip:port, file=wanbootCGI-URL
Note –The line breaks in this command sample are included for formatting purposes only. Do not enter a carriage return until you finish typing the command.
-
Boot the client.
ok boot net - install
- net - install
-
Instructs the client to use the network boot argument variables to boot from the WAN
The client installs over the WAN. If the WAN boot programs do not find all the necessary installation information, the wanboot program prompts to provide the missing information. Type the additional information at the prompt.
Example 12–4 Noninteractive WAN Boot Installation
In the following example, the network boot argument variables for the client system myclient are set before the machine is booted. This example assumes that a hashing key and encryption key are already installed on the client. For information about installing keys before you boot from the WAN, see Installing Keys on the Client.
ok setenv network-boot-arguments host-ip=192.168.198.136, router-ip=192.168.198.129,subnet-mask=255.255.255.192 hostname=myclient,file=http://192.168.198.135/cgi-bin/wanboot-cgi ok boot net - install Resetting ... Sun Blade 100 (UltraSPARC-IIe), No Keyboard Copyright 1998-2003 Sun Microsystems, Inc. All rights reserved. OpenBoot 4.x.build_28, 512 MB memory installed, Serial #50335475. Ethernet address 0:3:ba:e:f3:75, Host ID: 83000ef3. Rebooting with command: boot net - install Boot device: /pci@1f,0/network@c,1 File and args: - install |
The following variables are set.
-
The client IP address is set to 192.168.198.136.
-
The client's router IP address is set to 192.168.198.129.
-
The client's subnet mask is set to 255.255.255.192.
-
The client's host name is set to seahag.
-
The wanboot-cgi program is located at http://192.168.198.135/cgi-bin/wanboot-cgi.
See Also
For more information about how to set network boot arguments, see set(1).
For more information about how to boot a system, see boot(1M).
 To Perform an Interactive WAN Boot Installation
To Perform an Interactive WAN Boot Installation
Use this installation method if you want to install keys and set client configuration information at the command line during the installation.
This procedure assumes that you are using HTTPS in your WAN installation. If you are performing an insecure installation that does not use keys, do not display or install the client keys.
-
Assume the same user role as the web server user on the WAN boot server.
-
Display the key value for each client key.
# wanbootutil keygen -d -c -o net=net-ip,cid=client-ID,type=key-type
- net-ip
-
The IP address of the subnet for the client you want to install.
- client-ID
-
The ID of the client you want to install. The client ID can be a user-defined ID or the DHCP client ID.
- key-type
-
The key type you want to install on the client. Valid key types are 3des, aes, or sha1.
The hexadecimal value for the key is displayed.
-
Repeat the previous step for each type of client key you are installing.
-
If the client system is currently running, bring the client to run level 0.
-
At the ok prompt on the client system, set the network boot argument variables in OBP.
ok setenv network-boot-arguments host-ip=client-IP,router-ip=router-ip, subnet-mask=mask-value,hostname=client-name, http-proxy=proxy-ip:port,bootserver=wanbootCGI-URL
Note –The line breaks in this command sample are included for formatting purposes only. Do not enter a carriage return until you finish typing the command.
- setenv network-boot-arguments
-
Instructs the OBP to set the following boot arguments
- host-ip=client-IP
-
Specifies the IP address of the client
- router-ip=router-ip
-
Specifies the IP address of the network router
- subnet-mask=mask-value
-
Specifies the subnet mask value
- hostname=client-name
-
Specifies the host name of the client
- (Optional) http-proxy=proxy-ip:port
-
Specifies the IP address and port of the network's proxy server
- bootserver=wanbootCGI-URL
-
Specifies the URL of the wanboot-cgi program on the web server
Note –The URL value for thebootserver variable must not be an HTTPS URL. The URL must start with http://.
-
At the client ok prompt, boot the system.
ok boot net -o prompt - install
- net -o prompt - install
-
Instructs the client to boot and install from the network. The wanboot program prompts the user to enter client configuration information at the boot> prompt.
The boot> prompt is displayed.
-
boot> 3des=key-value
- 3des=key-value
-
Specifies the hexadecimal string of the 3DES key that is displayed in Step 2.
If you use an AES encryption key, use the following format for this command.
boot> aes=key-value
-
Install the hashing key.
boot> sha1=key-value
- sha1=key-value
-
Specifies the hashing key value that is displayed in Step 2.
-
Type the following command to continue the boot process.
boot> go
The client installs over the WAN.
-
If prompted, type client configuration information on the command line.
If the WAN boot programs do not find all the necessary installation information, the wanboot program prompts to provide the missing information. Type the additional information at the prompt.
Example 12–5 Interactive WAN Boot Installation
In the following example, the wanboot program prompts you to set the key values for the client system during the installation.
Display the key values on the WAN boot server.
# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 # wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous example uses the following information.
- net=192.168.198.0
-
Specifies the IP address of the client's subnet
- cid=010003BA152A42
-
Specifies the client's ID
- b482aaab82cb8d5631e16d51478c90079cc1d463
-
Specifies the value of the client's HMAC SHA1 hashing key
- 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04
-
Specifies the value of the client's 3DES encryption key
If you use an AES encryption key in your installation, change type=3des to type=aes to display the encryption key value.
Set the network boot argument variables in the OBP on the client.
ok setenv network-boot-arguments host-ip=192.168.198.136, router-ip=192.168.198.129,subnet-mask=255.255.255.192,hostname=myclient, bootserver=http://192.168.198.135/cgi-bin/wanboot-cgi |
The following variables are set.
-
The client IP address is set to 192.168.198.136.
-
The client's router IP address is set to 192.168.198.129.
-
The client's subnet mask is set to 255.255.255.192.
-
The client's host name is set to myclient.
-
The wanboot-cgi program is located at http://192.168.198.135/cgi-bin/wanboot-cgi.
Boot and install the client.
ok boot net -o prompt - install Resetting ... Sun Blade 100 (UltraSPARC-IIe), No Keyboard Copyright 1998-2003 Sun Microsystems, Inc. All rights reserved. OpenBoot 4.x.build_28, 512 MB memory installed, Serial #50335475. Ethernet address 0:3:ba:e:f3:75, Host ID: 83000ef3. Rebooting with command: boot net -o prompt Boot device: /pci@1f,0/network@c,1 File and args: -o prompt boot> 3des=9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 boot> sha1=b482aaab82cb8d5631e16d51478c90079cc1d463 boot> go |
The previous commands perform the following tasks.
-
Installs the 3DES encryption key with the value 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 on the client
-
Installs the HMAC SHA1 hashing key with the value b482aaab82cb8d5631e16d51478c90079cc1d463 on the client
-
Starts the installation
See Also
For more information about how to display key values, see wanbootutil(1M).
For more information about how to set network boot arguments, see set(1).
For more information about how to boot a system, see boot(1M).
 To Perform a WAN Boot Installation With
a DHCP Server
To Perform a WAN Boot Installation With
a DHCP Server
If you configured a DHCP server to support WAN boot options, you can use the DHCP server to provide client configuration information during the installation. For more information about configuring a DHCP server to support a WAN boot installation, see (Optional) Providing Configuration Information With a DHCP Server.
This procedure makes the following assumptions.
-
The client system is running.
-
You have either installed keys on the client, or you are performing an insecure installation.
For information about installing keys on the client before your installation, see Installing Keys on the Client.
-
You have configured your DHCP server to support the SbootURI and SHTTPproxy WAN boot options.
These options enable the DHCP server to provide the configuration information that is required by WAN boot.
For information about how to set installation options on your DHCP server, see Preconfiguring System Configuration Information With the DHCP Service (Tasks).
-
If the client system is currently running, bring the system to run level 0.
# init 0
The ok prompt is displayed.
-
At the ok prompt on the client system, set the network boot argument variables in OBP.
ok setenv network-boot-arguments dhcp,hostname=client-name
- setenv network-boot-arguments
-
Instructs the OBP to set the following boot arguments
- dhcp
-
Instructs the OBP to use the DHCP server to configure the client
- hostname=client-name
-
Specifies the host name you want to assign to the client
-
Boot the client from the network.
ok boot net - install
- net - install
-
Instructs the client to use the network boot argument variables to boot from the WAN
The client installs over the WAN. If the WAN boot programs do not find all the necessary installation information, the wanboot program prompts to provide the missing information. Type the additional information at the prompt.
Example 12–6 WAN Boot Installation With a DHCP Server
In the following example, the DHCP server on the network provides client configuration information. This sample requests the host name myclient for the client.
ok setenv network-boot-arguments dhcp, hostname=myclient ok boot net - install Resetting ... Sun Blade 100 (UltraSPARC-IIe), No Keyboard Copyright 1998-2003 Sun Microsystems, Inc. All rights reserved. OpenBoot 4.x.build_28, 512 MB memory installed, Serial #50335475. Ethernet address 0:3:ba:e:f3:75, Host ID: 83000ef3. Rebooting with command: boot net - install Boot device: /pci@1f,0/network@c,1 File and args: - install |
See Also
For more information about how to set network boot arguments, see set(1).
For more information about how to boot a system, see boot(1M).
For more information about how to configure a DHCP server, see (Optional) Providing Configuration Information With a DHCP Server.
 To Perform a WAN Boot Installation With
Local CD Media
To Perform a WAN Boot Installation With
Local CD Media
If your client's OBP does not support WAN boot, you can install with a Solaris Software - 1 CD inserted in the client's CD-ROM drive. When you use a local CD, the client retrieves the wanboot program from the local media, rather than from the WAN boot server.
This procedure assumes that you are using HTTPS in your WAN installation. If you are performing an insecure installation, do not display or install the client keys.
Follow these steps to perform a WAN boot installation from a local CD.
-
Assume the same user role as the web server user on the WAN boot server.
-
Display the key value for each client key.
# wanbootutil keygen -d -c -o net=net-ip,cid=client-ID,type=key-type
- net-ip
-
The network IP address for the client you are installing.
- client-ID
-
The ID of the client you are installing. The client ID can be a user-defined ID or the DHCP client ID.
- key-type
-
The key type you are installing on the client. Valid key types are 3des, aes, or sha1.
The hexadecimal value for the key is displayed.
-
Repeat the previous step for each type of client key you are installing.
-
On the client system, insert the Solaris Software - 1 CD in the CD-ROM drive.
-
Power on the client system.
-
Boot the client from the CD.
ok boot cdrom -o prompt -F wanboot - install
- cdrom
-
Instructs the OBP to boot from the local CD-ROM
- -o prompt
-
Instructs the wanboot program to prompt the user to enter client configuration information
- -F wanboot
-
Instructs the OBP to load the wanboot program from the CD-ROM
- - install
-
Instructs the client to perform a WAN boot installation
The client's OBP loads the wanboot program from the Solaris Software - 1 CD. The wanboot program boots the system, and the boot> prompt is displayed.
-
Type the encryption key value.
boot> 3des=key-value
- 3des=key-value
-
Specifies the hexadecimal string of the 3DES key that is displayed in step Step 2.
If you use an AES encryption key, use the following format for this command.
boot> aes=key-value
-
Type the hashing key value.
boot> sha1=key-value
- sha1=key-value
-
Specifies the hexadecimal string that represents the hashing key value that is displayed in step Step 2.
-
Set the network interface variables.
boot> variable=value[,variable=value*]
Type the following variable and value pairs at the boot> prompt.
- host-ip=client-IP
-
Specifies the IP address of the client.
- router-ip=router-ip
-
Specifies the IP address of the network router.
- subnet-mask=mask-value
-
Specifies the subnet mask value.
- hostname=client-name
-
Specifies the host name of the client.
- (Optional) http-proxy=proxy-ip:port
-
Specifies the IP address and port number of the network's proxy server.
- bootserver=wanbootCGI-URL
-
Specifies the URL of the wanboot-cgi program on the web server.
Note –The URL value for thebootserver variable must not be an HTTPS URL. The URL must start with http://.
You can enter these variables in the following ways.
-
Type one variable and value pair at the boot> prompt, then press the Return key.
boot> host-ip=client-IP boot> subnet-mask=mask-value
-
Type all the variable and value pairs on one boot> prompt line, then press the Return key. Type commas to separate each variable and value pair.
boot> host-ip=client-IP,subnet-mask=mask-value, router-ip=router-ip,hostname=client-name, http-proxy=proxy-ip:port,bootserver=wanbootCGI-URL
-
Type the following command to continue the boot process.
boot> go
The client installs over the WAN. If the WAN boot programs do not find all the necessary installation information, the wanboot program prompts to provide the missing information. Type the additional information at the prompt.
Example 12–7 Installing With Local CD Media
In the following example, the wanboot program on a local CD prompts you to set the network interface variables for the client during the installation.
Display the key values on the WAN boot server.
# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 # wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous example uses the following information.
- net=192.168.198.0
-
Specifies the IP address of the client's subnet
- cid=010003BA152A42
-
Specifies the client's ID
- b482aaab82cb8d5631e16d51478c90079cc1d463
-
Specifies the value of the client's HMAC SHA1 hashing key
- 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04
-
Specifies the value of the client's 3DES encryption key
If you use an AES encryption key in your installation, change type=3des to type=aes to display the encryption key value.
Boot and install the client.
ok boot cdrom -o prompt -F wanboot - install Resetting ... Sun Blade 100 (UltraSPARC-IIe), No Keyboard Copyright 1998-2003 Sun Microsystems, Inc. All rights reserved. OpenBoot 4.x.build_28, 512 MB memory installed, Serial #50335475. Ethernet address 0:3:ba:e:f3:75, Host ID: 83000ef3. Rebooting with command: boot cdrom -F wanboot - install Boot device: /pci@1f,0/network@c,1 File and args: -o prompt boot> 3des=9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 boot> sha1=b482aaab82cb8d5631e16d51478c90079cc1d463 boot> host-ip=192.168.198.124 boot> subnet-mask=255.255.255.128 boot> router-ip=192.168.198.1 boot> hostname=myclient boot> client-id=010003BA152A42 boot> bootserver=http://192.168.198.135/cgi-bin/wanboot-cgi boot> go |
The previous commands perform the following tasks.
-
Enters the 3DES encryption key with the value 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 on the client
-
Enters the HMAC SHA1 hashing key with the value b482aaab82cb8d5631e16d51478c90079cc1d463 on the client
-
Sets the client IP address to 192.168.198.124
-
Sets the client's subnet mask to 255.255.255.128
-
Sets the client's router IP address to 192.168.198.1
-
Sets the client's host name to myclient
-
Sets the client ID to 010003BA152A42
-
Sets the location of the wanboot-cgi program to http://192.168.198.135/cgi-bin/wanboot-cgi/
See Also
For more information about how to display key values, see wanbootutil(1M).
For more information about how to set network boot arguments, see set(1).
For more information about how to boot a system, see boot(1M).
Chapter 13 SPARC: Installing With WAN Boot (Examples)
This chapter provides an example of setting up and installing client systems over a wide area network (WAN). The examples in this chapter describe how to perform a secure WAN boot installation over an HTTPS connection.
-
(Optional) Configure the WAN Boot Server as a Logging Server
-
(Optional) Use Private Key and Certificate for Client Authentication
Sample Site Setup
Figure 13–1 shows the site setup for this example.
Figure 13–1 Sample Site for WAN Boot Installation
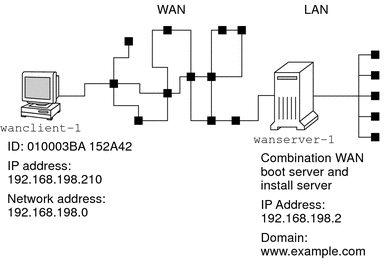
This sample site has the following characteristics.
-
The server wanserver-1 is to be configured as a WAN boot server and an install server.
-
The IP address of wanserver-1 is 192.168.198.2.
-
The domain name of wanserver-1 is www.example.com.
-
wanserver-1 is running the current Solaris release.
-
wanserver-1 is running the Apache web server. The Apache software on wanserver-1 is configured to support HTTPS.
-
The client to be installed is named wanclient-1.
-
wanclient-1 is an UltraSPARCII system.
-
The client ID for wanclient-1 is 010003BA152A42.
-
The IP address of wanclient-1 is 192.168.198.210.
-
The IP address of the client's subnet is 192.168.198.0.
-
The client system wanclient-1 has Internet access, but is not directly connected to the network that includes wanserver-1.
-
wanclient-1 is a new system that is to be installed with the current Solaris release software.
Create the Document Root Directory
To store the installation files and data, set up the following directories in the document root directory (/opt/apache/htdocs) on wanserver-1.
-
Solaris Flash directory
wanserver-1# mkdir -p /opt/apache/htdocs/flash/
-
WAN boot miniroot directory
wanserver-1# mkdir -p /opt/apache/htdocs/miniroot/
-
wanboot program directory
wanserver-1# mkdir -p /opt/apache/htdocs/wanboot/
Create the WAN Boot Miniroot
Use the setup_install_server(1M) with the -w option to copy the WAN boot miniroot and the Solaris software image to the /export/install/Solaris_10 directory of wanserver-1.
Insert the Solaris Software media in the media drive that is attached to wanserver-1. Type the following commands.
wanserver-1# mkdir -p /export/install/cdrom0 wanserver-1# cd /cdrom/cdrom0/s0/Solaris_10/Tools wanserver-1# ./setup_install_server -w /export/install/cdrom0/miniroot \ /export/install/cdrom0 |
Move the WAN boot miniroot to the document root directory (/opt/apache/htdocs/) of the WAN boot server.
wanserver-1# mv /export/install/cdrom0/miniroot/miniroot \ /opt/apache/htdocs/miniroot/miniroot.s10_sparc |
Check the Client OBP for WAN Boot Support
Determine that the client OBP supports WAN boot by typing the following command on the client system.
# eeprom | grep network-boot-arguments network-boot-arguments: data not available |
In the previous example, the network-boot-arguments: data not available output indicates that the client OBP supports WAN boot.
Install the wanboot Program on the WAN Boot Server
To install the wanboot program on the WAN boot server, copy the program from the Solaris Software media to the WAN boot server's document root directory.
Insert the Solaris DVD or the Solaris Software - 1 CD in the media drive that is attached to wanserver-1 and type the following commands.
wanserver-1# cd /cdrom/cdrom0/s0/Solaris_10/Tools/Boot/platform/sun4u/ wanserver-1# cp wanboot /opt/apache/htdocs/wanboot/wanboot.s10_sparc |
Create the /etc/netboot Hierarchy
Create the wanclient-1 subdirectories of the /etc/netboot directory on the WAN boot server. The WAN boot installation programs retrieve configuration and security information from this directory during the installation.
wanclient-1 is located on the subnet 192.168.198.0, and has a client ID of 010003BA152A42. To create the appropriate subdirectory of /etc/netboot for wanclient-1, perform the following tasks.
-
Create the /etc/netboot directory.
-
Change the permissions of the /etc/netboot directory to 700.
-
Change the ownership of the /etc/netboot directory to the owner of the web server process.
-
Assume the same user role as the web server user.
-
Create a subdirectory of /etc/netboot that is named after the subnet (192.168.198.0).
-
Create a subdirectory of the subnet directory that is named after the client ID.
-
Change the permissions of the /etc/netboot subdirectories to 700.
wanserver-1# cd / wanserver-1# mkdir /etc/netboot/ wanserver-1# chmod 700 /etc/netboot wanserver-1# chown nobody:admin /etc/netboot wanserver-1# exit wanserver-1# su nobody Password: nobody# mkdir -p /etc/netboot/192.168.198.0/010003BA152A42 nobody# chmod 700 /etc/netboot/192.168.198.0 nobody# chmod 700 /etc/netboot/192.168.198.0/010003BA152A42 |
Copy the wanboot-cgi Program to the WAN Boot Server
On systems that are running the current Solaris release, the wanboot-cgi program is located in the /usr/lib/inet/wanboot/ directory. To enable the WAN boot server to transmit the installation data, copy the wanboot-cgi program to the cgi-bin directory in the web server software directory.
wanserver-1# cp /usr/lib/inet/wanboot/wanboot-cgi \ /opt/apache/cgi-bin/wanboot-cgi wanserver-1# chmod 755 /opt/apache/cgi-bin/wanboot-cgi |
(Optional) Configure the WAN Boot Server as a Logging Server
By default, all WAN boot logging messages are displayed on the client system. This default behavior enables you to quickly debug any installation issues.
If you want to view the boot and installation messages on the WAN boot server, copy the bootlog-cgi script to the cgi-bin directory on wanserver-1.
wanserver-1# cp /usr/lib/inet/wanboot/bootlog-cgi /opt/apache/cgi-bin/ wanserver-1# chmod 755 /opt/apache/cgi-bin/bootlog-cgi |
Configure the WAN Boot Server to Use HTTPS
To use HTTPS in your WAN boot installation, you must enable SSL support in the web server software. You must also install a digital certificate on the WAN boot server. This example assumes that the Apache web server on wanserver-1 is configured to use SSL. This example also assumes that a digital certificate and a certificate authority that establish the identity of wanserver-1 are already installed on wanserver-1.
For examples about how to configure your web server software to use SSL, see you web server documentation.
Provide the Trusted Certificate to the Client
By requiring the server to authenticate itself to the client, you protect the data that is transmitted from the server to the client over HTTPS. To enable server authentication, you provide a trusted certificate to the client. The trusted certificate enables the client to verify the identity of the server during the installation.
To provide the trusted certificate to the client, assume the same user role as the web server user. Then, split the certificate to extract a trusted certificate. Then, insert the trusted certificate in the client's truststore file in the /etc/netboot hierarchy.
In this example, you assume the web server user role of nobody. Then, you split the server PKCS#12 certificate that is named cert.p12, and insert the trusted certificate in /etc/netboot directory for wanclient-1.
wanserver-1# su nobody Password: wanserver-1# wanbootutil p12split -i cert.p12 -t \ /etc/netboot/192.168.198.0/010003BA152A42/truststore |
(Optional) Use Private Key and Certificate for Client Authentication
To further protect your data during the installation, you might want to require wanclient-1 to authenticate itself to wanserver-1. To enable client authentication in your WAN boot installation, insert a client certificate and private key in the client subdirectory of the /etc/netboot hierarchy.
To provide a private key and certificate to the client, perform the following tasks.
-
Assume the same user role as the web server user
-
Split the PKCS#12 file into a private key and a client certificate
-
Insert the certificate in the client's certstore file
-
Insert the private key in the client's keystore file
In this example, you assume the web server user role of nobody. Then, you split the server PKCS#12 certificate that is named cert.p12. You insert certificate in the /etc/netboot hierarchy for wanclient-1. You then insert the private key that you named wanclient.key in the client's keystore file.
wanserver-1# su nobody Password: wanserver-1# wanbootutil p12split -i cert.p12 -c \ /etc/netboot/192.168.198.0/010003BA152A42/certstore -k wanclient.key wanserver-1# wanbootutil keymgmt -i -k wanclient.key \ -s /etc/netboot/192.168.198.0/010003BA152A42/keystore \ -o type=rsa |
Create the Keys for the Server and the Client
To protect the data transmitted between the server and client, you create a hashing key and an encryption key. The server uses the hashing key to protect the integrity of the wanboot program. The server uses the encryption key to encrypt the configuration and installation data. The client uses the hashing key to check the integrity of the downloaded wanboot program. The client uses the encryption key to decrypt the data during the installation.
First, you assume the same user role as the web server user. In this example, the web server user role is nobody.
wanserver-1# su nobody Password: |
Then, you use the wanbootutil keygen command to create a master HMAC SHA1 key for wanserver-1.
wanserver-1# wanbootutil keygen -m |
Then, create a hashing key and an encryption key for wanclient-1.
wanserver-1# wanbootutil keygen -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 wanserver-1# wanbootutil keygen -c -o net=192.168.198.0,cid=010003BA152A42,type=3des |
The previous command creates a HMAC SHA1 hashing key and a 3DES encryption key for wanclient-1. 192.168.198.0 specifies the subnet of wanclient-1, and 010003BA152A42 specifies the client ID of wanclient-1.
Create the Solaris Flash Archive
In this example, you create your Solaris Flash archive by cloning the wanserver-1 master system. The archive is named sol_10_sparc, and is copied exactly from the master system. The archive is an exact duplicate of the master system. The archive is stored in sol_10_sparc.flar. You save the archive in the flash/archives subdirectory of the document root directory on the WAN boot server.
wanserver-1# flarcreate -n sol_10_sparc \ /opt/apache/htdocs/flash/archives/sol_10_sparc.flar |
Create the sysidcfg File
To preconfigure the wanclient-1 system, specify keywords and values in the sysidcfg file. Save this file in the appropriate subdirectory of the document root directory of wanserver-1.
Example 13–1 sysidcfg File for client-1 System
The following is an example of a sysidcfg file for wanclient-1. The host name, IP address, and netmask of these systems have been preconfigured by editing the naming service. This file is located in the /opt/apache/htdocs/flash/ directory.
network_interface=primary {hostname=wanclient-1
default_route=192.168.198.1
ip_address=192.168.198.210
netmask=255.255.255.0
protocol_ipv6=no}
timezone=US/Central
system_locale=C
terminal=xterm
timeserver=localhost
name_service=NIS {name_server=matter(192.168.254.254)
domain_name=leti.example.com
}
security_policy=none
Create the Client's Profile
For the wanclient-1 system, create a profile that is named wanclient_1_prof. The wanclient_1_prof file contains the following entries, which define the current Solaris release software to be installed on the wanclient-1 system.
# profile keywords profile values # ---------------- ------------------- install_type flash_install archive_location https://192.168.198.2/flash/archives/cdrom0.flar partitioning explicit filesys c0t1d0s0 4000 / filesys c0t1d0s1 512 swap filesys c0t1d0s7 free /export/home
The following list describes some of the keywords and values from this example.
- install_type
-
The profile installs a Solaris Flash archive on the clone system. All files are overwritten as in an initial installation.
- archive_location
-
The compressed Solaris Flash archive is retrieved from wanserver-1.
- partitioning
-
The file system slices are determined by the filesys keywords, value explicit. The size of root (/) is based on the size of the Solaris Flash archive. The size of swap is set to the necessary size and is installed on c0t1d0s1. /export/home is based on the remaining disk space. /export/home is installed on c0t1d0s7.
Create and Validate the rules File
The custom JumpStart programs use the rules file to select the correct installation profile for the wanclient-1 system. Create a text file that is named rules. Then, add keywords and values to this file.
The IP address of the wanclient-1 system is 192.168.198.210, and the netmask is 255.255.255.0. Use the network rule keyword to specify the profile that the custom JumpStart programs should use to install wanclient-1.
network 192.168.198.0 - wanclient_1_prof - |
This rules file instructs the custom JumpStart programs to use the wanclient_1_prof to install the current Solaris release software on wanclient-1.
Name this rule file wanclient_rule.
After you create the profile and the rules file, you run the check script to verify that the files are valid.
wanserver-1# ./check -r wanclient_rule |
If the check script does not find any errors, the script creates the rules.ok file.
Save the rules.ok file in the /opt/apache/htdocs/flash/ directory.
Create the System Configuration File
Create a system configuration file that lists the locations of the sysidcfg file and the custom JumpStart files on the install server. Save this file in a directory that is accessible to the WAN boot server.
In the following example, the wanboot-cgi program looks for the sysidcfg and custom JumpStart files in the document root directory of the WAN boot server. The domain name of the WAN boot server is https://www.example.com. The WAN boot server is configured to use secure HTTP, so the data and files are protected during the installation.
In this example, the system configuration file is named sys-conf.s10–sparc, and the file is saved in the /etc/netboot hierarchy on the WAN boot server. The sysidcfg and custom JumpStart files are located in the flash subdirectory of the document root directory.
SsysidCF=https://www.example.com/flash/ SjumpsCF=https://www.example.com/flash/
Create the wanboot.conf File
WAN boot uses the configuration information that is included in the wanboot.conf file to install the client machine. Create the wanboot.conf file in a text editor. Save the file to the appropriate client subdirectory in the /etc/netboot hierarchy on the WAN boot server.
The following wanboot.conf file for wanclient-1 includes configuration information for a WAN installation that uses secure HTTP. This file also instructs WAN boot to use a HMAC SHA1 hashing key and a 3DES encryption key to protect data.
boot_file=/wanboot/wanboot.s10_sparc root_server=https://www.example.com/cgi-bin/wanboot-cgi root_file=/miniroot/miniroot.s10_sparc signature_type=sha1 encryption_type=3des server_authentication=yes client_authentication=no resolve_hosts= boot_logger= system_conf=sys-conf.s10–sparc
This wanboot.conf file specifies the following configuration.
- boot_file=/wanboot/wanboot.s10_sparc
-
The wanboot program is named wanboot.s10_sparc. This program is located in the wanboot directory in the document root directory on wanserver-1.
- root_server=https://www.example.com/cgi-bin/wanboot-cgi
-
The location of the wanboot-cgi program on wanserver-1 is https://www.example.com/cgi-bin/wanboot-cgi. The https portion of the URL indicates that this WAN boot installation uses secure HTTP.
- root_file=/miniroot/miniroot.s10_sparc
-
The WAN boot miniroot is named miniroot.s10_sparc. The miniroot is located in the miniroot directory in the document root directory on wanserver-1.
- signature_type=sha1
-
The wanboot program and the WAN boot file system are signed by using a HMAC SHA1 hashing key.
- encryption_type=3des
-
The wanboot program and the WAN boot file system are encrypted with a 3DES key.
- server_authentication=yes
-
The server is authenticated during the installation.
- client_authentication=no
-
The client is not authenticated during the installation.
Note –If you performed the tasks in (Optional) Use Private Key and Certificate for Client Authentication, set this parameter as client_authentication=yes
- resolve_hosts=
-
No additional host names are needed to perform the WAN installation. All the host names that are required by the wanboot-cgi program are specified in the wanboot.conf file and the client certificate.
- boot_logger=
-
Booting and installation log messages are displayed on the system console. If you configured the logging server in (Optional) Configure the WAN Boot Server as a Logging Server, and you want WAN boot messages to appear on the WAN boot server as well, set this parameter to boot_logger=https://www.example.com/cgi-bin/bootlog-cgi.
- system_conf=sys-conf.s10–sparc
-
The system configuration file that specifies the locations of the sysidcfg and JumpStart files is located in the sys-conf.s10–sparc file in the /etc/netboot hierarchy on wanserver-1.
In this example, you save the wanboot.conf file in the /etc/netboot/192.168.198.0/010003BA152A42 directory on wanserver-1.
Check the net Device Alias in OBP
To boot the client from the WAN with the boot net, the net device alias must be set to the client's primary network device. At the client ok prompt, type the devalias command to verify that the net alias is set to the primary network device /pci@1f,0/pci@1,1/network@c,1.
ok devalias screen /pci@1f,0/pci@1,1/SUNW,m64B@2 net /pci@1f,0/pci@1,1/network@c,1 net2 /pci@1f,0/pci@1,1/network@5,1 disk /pci@1f,0/pci@1/scsi@8/disk@0,0 cdrom /pci@1f,0/pci@1,1/ide@d/cdrom@0,0:f keyboard /pci@1f,0/pci@1,1/ebus@1/su@14,3083f8 mouse /pci@1f,0/pci@1,1/ebus@1/su@14,3062f8 |
In the previous output example, the primary network device /pci@1f,0/pci@1,1/network@c,1 is assigned to the net alias. You do not need to reset the alias.
Install Keys on the Client
In Create the Keys for the Server and the Client, you created the hashing key and encryption key to protect your data during the installation. To enable the client to decrypt the data transmitted from wanserver-1 during the installation, install these keys on wanclient-1.
On wanserver-1, display the key values.
wanserver-1# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 wanserver-1# wanbootutil keygen -d -c -o net=192.168.198.0,cid=010003BA152A42,type=3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous example uses the following information.
- net=192.168.198.0
-
Specifies the IP address of the client's subnet
- cid=010003BA152A42
-
Specifies the client's ID
- b482aaab82cb8d5631e16d51478c90079cc1d463
-
Specifies the value of the client's HMAC SHA1 hashing key
- 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04
-
Specifies the value of the client's 3DES encryption key
If you use an AES encryption key in your installation, change type=3des to type=aes to display the encryption key value.
At the ok prompt on wanclient-1, install the keys.
ok set-security-key wanboot-hmac-sha1 b482aaab82cb8d5631e16d51478c90079cc1d463 ok set-security-key wanboot-3des 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 |
The previous commands perform the following tasks.
-
Installs the HMAC SHA1 hashing key with a value of b482aaab82cb8d5631e16d51478c90079cc1d463 on wanclient-1
-
Installs the 3DES encryption key with a value of 9ebc7a57f240e97c9b9401e9d3ae9b292943d3c143d07f04 on wanclient-1
Install the Client
You can perform an unattended installation by setting network boot argument variables for wanclient-1 at the ok prompt, and then booting the client.
ok setenv network-boot-arguments host-ip=192.168.198.210, router-ip=192.168.198.1,subnet-mask=255.255.255.0,hostname=wanclient-1, file=http://192.168.198.2/cgi-bin/wanboot-cgi ok boot net - install Resetting ... Sun Blade 100 (UltraSPARC-IIe), No Keyboard Copyright 1998-2003 Sun Microsystems, Inc. All rights reserved. OpenBoot 4.x.build_28, 512 MB memory installed, Serial #50335475. Ethernet address 0:3:ba:e:f3:75, Host ID: 83000ef3. Rebooting with command: boot net - install Boot device: /pci@1f,0/network@c,1 File and args: - install <time unavailable> wanboot progress: wanbootfs: Read 68 of 68 kB (100%) <time unavailable> wanboot info: wanbootfs: Download complete Fri Jun 20 09:16:06 wanboot progress: miniroot: Read 166067 of 166067 kB (100%) Fri Jun 20Tue Apr 15 09:16:06 wanboot info: miniroot: Download complete SunOS Release 5.10 Version WANboot10:04/11/03 64-bit Copyright 1983-2003 Sun Microsystems, Inc. All rights reserved. Use is subject to license terms. Configuring devices. |
The following variables are set.
-
The client IP address is set to 192.168.198.210.
-
The client's router IP address is set to 192.168.198.1
-
The client's subnet mask is set to 255.255.255.0
-
The client's host name is set to wanclient-1
-
The wanboot-cgi program is located at http://192.168.198.2/cgi-bin/wanboot-cgi
The client installs over the WAN. If the wanboot program does not find all the necessary installation information, you might be prompted to provide the missing information at the command line.
Chapter 14 WAN Boot (Reference)
This chapter briefly describes the commands and files you use to perform a WAN installation.
WAN Boot Installation Commands
The following tables describe the commands you use to perform a WAN boot installation.
Table 14–1 Preparing the WAN Boot Installation and Configuration FilesTable 14–2 Preparing the WAN Boot Security Files
OBP Commands
The following table lists the OBP commands that you type at the client ok prompt to perform a WAN boot installation.
Table 14–3 OBP Commands for a WAN Boot Installation
System Configuration File Settings and Syntax
The system configuration file enables you to direct the WAN boot installation programs to the following files.
-
sysidcfg
-
rules.ok
-
Custom JumpStart profile
The system configuration file is a plain text file, and must be formatted in the following pattern.
setting=value
The system.conf file must contain the following settings.
- SsysidCF=sysidcfg-file-URL
-
This setting points to the directory on the install server that contains the sysidcfg file. For WAN installations that use HTTPS, set the value to a valid HTTPS URL.
- SjumpsCF=jumpstart-files-URL
-
This setting points to the custom JumpStart directory that contains the rules.ok and profile files. For WAN installations that use HTTPS, set the value to a valid HTTPS URL.
You can store the system.conf in any directory that is accessible to the WAN boot server.
wanboot.conf File Parameters and Syntax
The wanboot.conf file is a plain-text configuration file that the WAN boot installation programs use to perform a WAN installation. The following programs and files use the information included in the wanboot.conf file to install the client machine.
-
wanboot-cgi program
-
WAN boot file system
-
WAN boot miniroot
Save the wanboot.conf file in the appropriate client subdirectory in the /etc/netboot hierarchy on the WAN boot server. For information on how to define the scope of your WAN boot installation with the /etc/netboot hierarchy, see Creating the /etc/netboot Hierarchy on the WAN Boot Server.
You specify information in the wanboot.conf file by listing parameters with associated values in the following format.
parameter=value
Parameter entries cannot span lines. You can include comments in the file by preceding the comments with the # character.
For detailed information about the wanboot.conf file, see the man page wanboot.conf(4).
You must set the following parameters in the wanboot.conf file.
- boot_file=wanboot-path
-
This parameter specifies the path to the wanboot program. The value is a path relative to the document root directory on the WAN boot server.
boot_file=/wanboot/wanboot.s10_sparc
- root_server=wanbootCGI-URL/wanboot-cgi
-
This parameter specifies the URL of the wanboot-cgi program on the WAN boot server.
-
Use an HTTP URL if you are performing a WAN boot installation without client or server authentication.
root_server=http://www.example.com/cgi-bin/wanboot-cgi
-
Use an HTTPS URL if you are performing a WAN boot installation with server authentication, or server and client authentication.
root_server=https://www.example.com/cgi-bin/wanboot-cgi
-
- root_file=miniroot-path
-
This parameter specifies the path to the WAN boot miniroot on the WAN boot server. The value is a path relative to the document root directory on the WAN boot server.
root_file=/miniroot/miniroot.s10_sparc
- signature_type=sha1 | empty
-
This parameter specifies the type of hashing key to use to check the integrity of the data and files that are transmitted.
- encryption_type=3des | aes | empty
-
This parameter specifies the type of encryption to use to encrypt the wanboot program and WAN boot file system.
-
For WAN boot installations that use HTTPS, set this value to 3des or aes to match the key formats you use. You must also set the signature_type keyword value to sha1.
encryption_type=3des
or
encryption_type=aes
-
For an insecure WAN boot installations that do not use encryption key, leave this value blank.
encryption_type=
-
- server_authentication=yes | no
-
This parameter specifies if the server should be authenticated during the WAN boot installation.
-
For WAN boot installations with server authentication or server and client authentication, set this value to yes. You must also set the value of signature_type to sha1, encryption_type to 3des or aes, and the URL of root_server to an HTTPS value.
server_authentication=yes
-
For insecure WAN boot installations that do not use server authentication or server and client authentication, set this value to no. You can also leave the value blank.
server_authentication=no
-
- client_authentication=yes | no
-
This parameter specifies if the client should be authenticated during a WAN boot installation.
-
For WAN boot installations with server and client authentication, set this value to yes. You must also set the value of signature_type to sha1, encryption_type to 3des or aes, and the URL of root_server to an HTTPS value.
client_authentication=yes
-
For WAN boot installations that do not use client authentication, set this value to no. You can also leave the value blank.
client_authentication=no
-
- resolve_hosts=hostname | empty
-
This parameter specifies additional hosts that need to be resolved for the wanboot-cgi program during the installation.
Set the value to the host names of systems that are not specified previously in the wanboot.conf file or in a client certificate.
- boot_logger=bootlog-cgi-path | empty
-
This parameter specifies the URL to the bootlog-cgi script on the logging server.
-
To record boot or installation log messages on a dedicated logging server, set the value to the URL of the bootlog-cgi script on the logging server.
boot_logger=http://www.example.com/cgi-bin/bootlog-cgi
-
To display boot and installation messages on the client console, leave this value blank.
boot_logger=
-
- system_conf=system.conf | custom-system-conf
-
This parameter specifies the path to the system configuration file that includes the location of sysidcfg and custom JumpStart files.
Set the value to the path to the sysidcfg and custom JumpStart files on the web server.
system_conf=sys.conf
- © 2010, Oracle Corporation and/or its affiliates
