Chapter 13 Enabling Single Sign-On Using CA SiteMinder and OpenSSO Enterprise
This chapter describes options for co-locating CA SiteMinder with Sun OpenSSO Enterprise in the same environment. For more detailed information about configuring end-to-end SiteMinder single sign-on using OpenSSO, see the Sun OpenSSO Enterprise 8.0 Integration Guide.
The following topics are contained in this chapter:
About CA SiteMinder
Computer Associates (CA) SiteMinder, formerly Netegrity SiteMinder, is an enterprise infrastructure product that enables centralized, secure Web access management. Its features include user authentication and single sign-on, policy-based authorization, and identity federation. One of the first single sign-on products to arrive on the market, legacy SiteMinder installations still exist to protect enterprise applications in many company networks.
Analyzing the Deployment Architecture Options
This chapter describes single sign-On between OpenSSO Enterprise and SiteMinder in both intranet and federated extranet environments. The examples in this chapter describe single sign-on, but do not include authorization.
SiteMinder and OpenSSO Enterprise typically co-exist in the following use cases:
-
Simple Single Sign-On
Major components are OpenSSO Enterprise, an OpenSSO Enterprise Policy Agent, a custom OpenSSO Enterprise authentication module, SiteMinder, and a SiteMinder Policy Agent.
-
Federated Single Sign-On in an Identity Provider Environment
Major components are OpenSSO Enterprise, an OpenSSO Enterprise Policy Agent, a custom OpenSSO Enterprise authentication module, SiteMinder, and a SiteMinder Policy Agent.
-
Federated Single Sign-On in a Service Provider Environment
Major components are OpenSSO Enterprise, a custom OpenSSO Enterprise authentication module, SiteMinder, a custom SiteMinder plug-in, and SiteMinder Policy Agent.
Single logout for any these of these use cases can be implemented in many ways.
Logical architecture diagrams and process flow diagrams for these deployment options are described in the following section “Understanding the Business Use Cases.”
Considering Assumptions, Dependencies, and Constraints
This chapter describes the conceptual integration between the two access management products. However, in real deployments the use cases will vary. In all the deployment architecture examples, the common data store is shared between two products when they are co-located. This document focuses on mutual validation of user sessions. However, mutual validation can be extended to attributes and other state information. The sessions are managed independently, and managing session timeouts are outside the scope of this document. Also, this document assumes the logout is relatively simple and involves invalidating both sessions as POST Logout process. For federation single sign-on, this document assumes SAMLv2 protocols. However, similar functionality can be achieved using other federation protocols such as ID-FF, WS-Federation, and SAML1.
Understanding Typical Business Use Cases
The following use cases focus on single sign-on enablement and do not describe authorization options:
Simple Single Sign-On
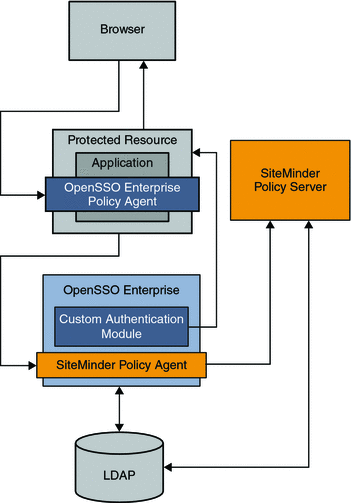
In a simple single sign-on example, the SiteMinder instance is already deployed and configured to protect some of the enterprise applications in a company intranet. In the architecture figure below, the legacy application is contained in the Protected Resource . The company wants to continue leveraging the legacy SiteMinder deployment as the authentication authority. The company also wants to add OpenSSO Enterprise to the environment to leverage its advanced features such as identity federation, XACML policies, web services, and so on. An OpenSSO Enterprise policy agent protects the Protected Resource, while OpenSSO Enterprise itself is protected by a SiteMinder policy agent. The following figure illustrates the deployment architecture for single sign-on using both SiteMinder and OpenSSO Enterprise.
Figure 13–1 Deployment Architecture for Simple Single Sign-On with SiteMinder
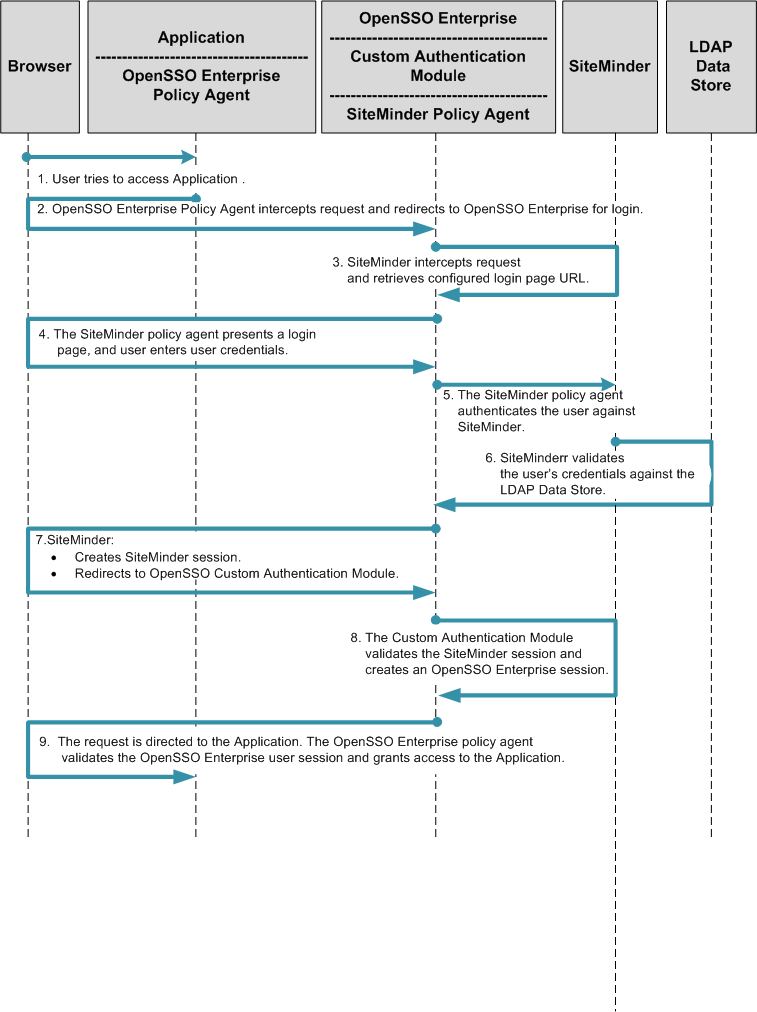
The following figure illustrates the process flow in this deployment.
Figure 13–2 Process Flow for Simple Single Sign-On with SiteMinder
Federated Single Sign-On
The SAML, ID-FF, and WS-Federation protocols provide cross-domain single sign-on among multiple trusted business entities. These protocols are also used in Identity Federation. Identity Federation involves an Identity Provider, also known as an authentication provider, and a Service Provider where the user authentication session at the Identity provider is consumed. The following are common use cases in which SiteMinder is enabled for federation protocols:
-
Enabling SiteMinder for federation protocols in a Service Provider environment
-
Enabling SiteMinder for federation protocols in an Identity Provider environment
Federated Single Sign-On in an Identity Provider Environment
This is the most common of the deployments. This is a good approach when you want to use OpenSSO Enterprise for establishing partner relations and still leverage the SiteMinder authentication framework.
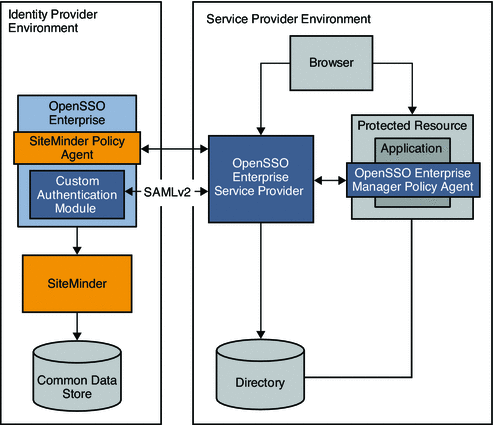
For example, as a company partners with external companies, the company deploys OpenSSO in the Service Provider environment to leverage the SAMLv2 Federation protocols. The following figure illustrates how SiteMinder can be enabled in an Identity Provider environment using OpenSSO Enterprise for federation protocols.
Figure 13–3 Deployment Architecture for Federated Single Sign-On in an Identity Provider Environment
In this example, OpenSSO Enterprise provides federated single sign-on among enterprise applications in partner environments, while SiteMinder continues to provide authentication. The following two figures illustrates a typical transaction flow.
Figure 13–4 Process Flow for Federated Single Sign-On in an Identity Provider Environment
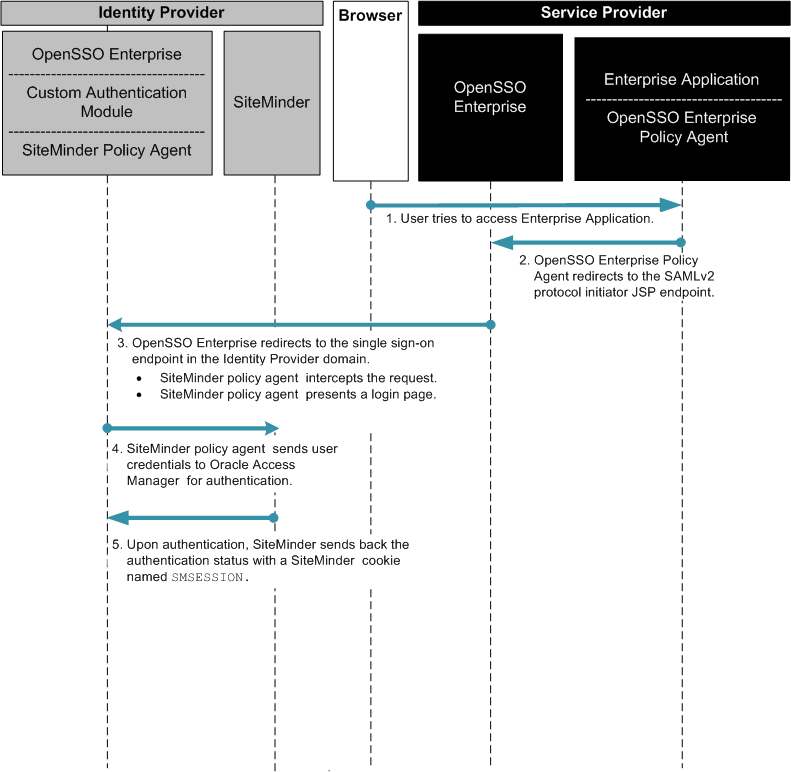
Figure 13–5 Process Flow for Federated Single Sign-On in an Identity Provider Environment (Continued)
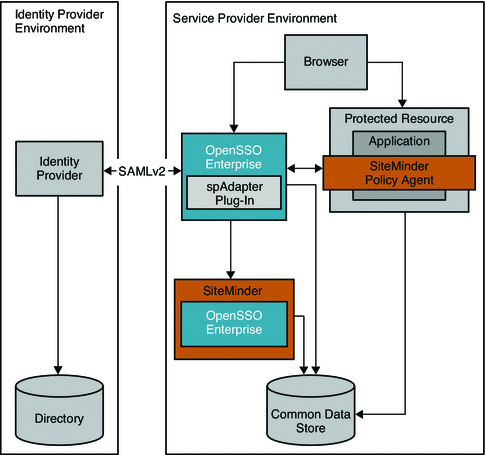
Federated Single Sign-On Use Case in the Service Provider Environment
In this example, the company uses SiteMinder in the Service Provider environment to protect legacy applications. OpenSSO Enterprise is installed solely to invoke Federation protocols. This deployment quickly enables partners (Service Providers) to establish federation environments with their trusted Identity Providers where the authenticates must be delegated.
Figure 13–6 Deployment Architecture for Federated Single Sign-On In the Service Provider Environment
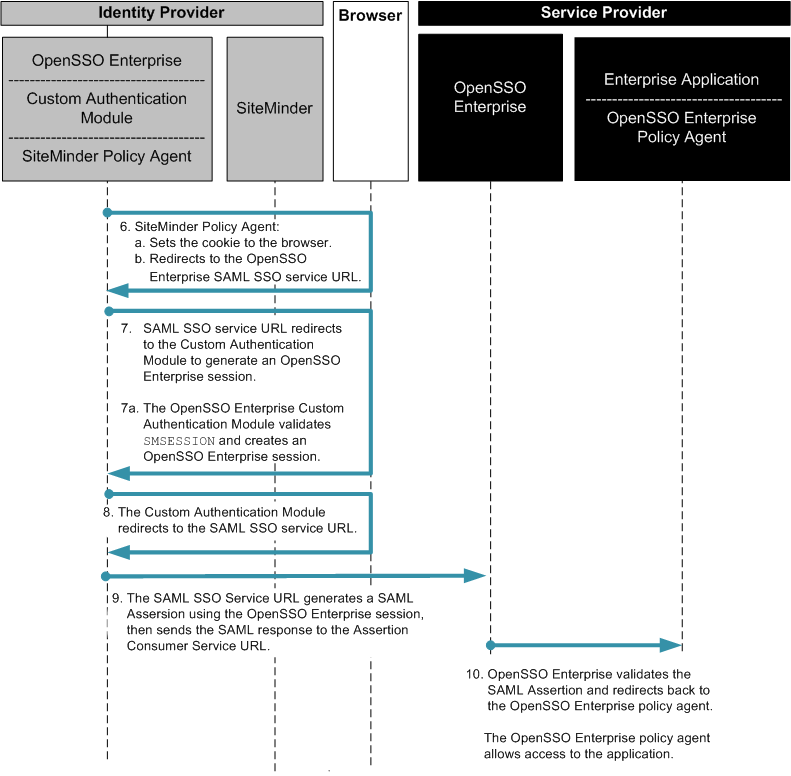
The following two figures illustrate the steps in the single sign-on flow:
Figure 13–7 Process Flow for SiteMinder Federation in the Service Provider Environment
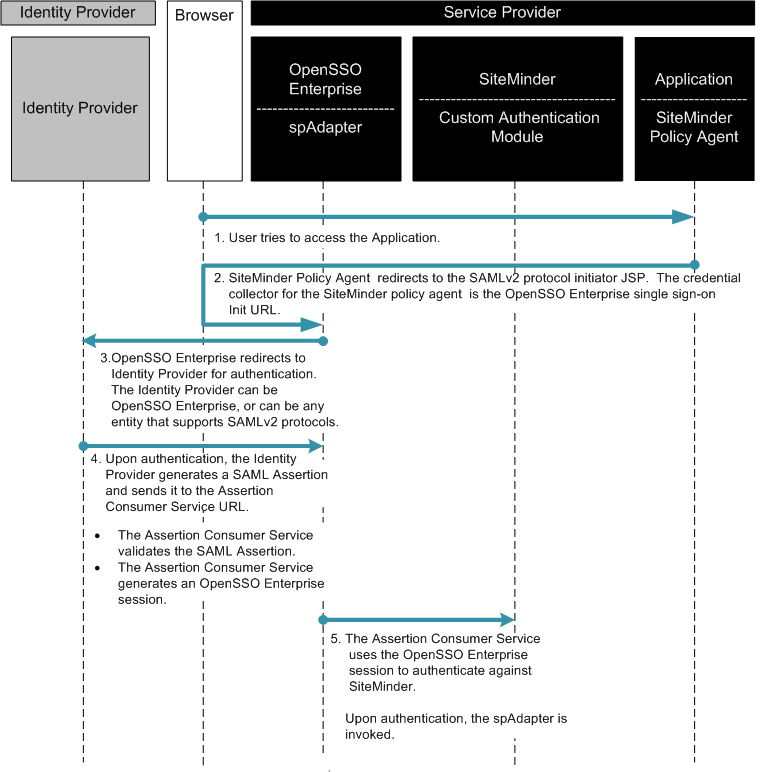
Figure 13–8 Process Flow for SiteMinder Federation in the Service Provider Environment (continued)
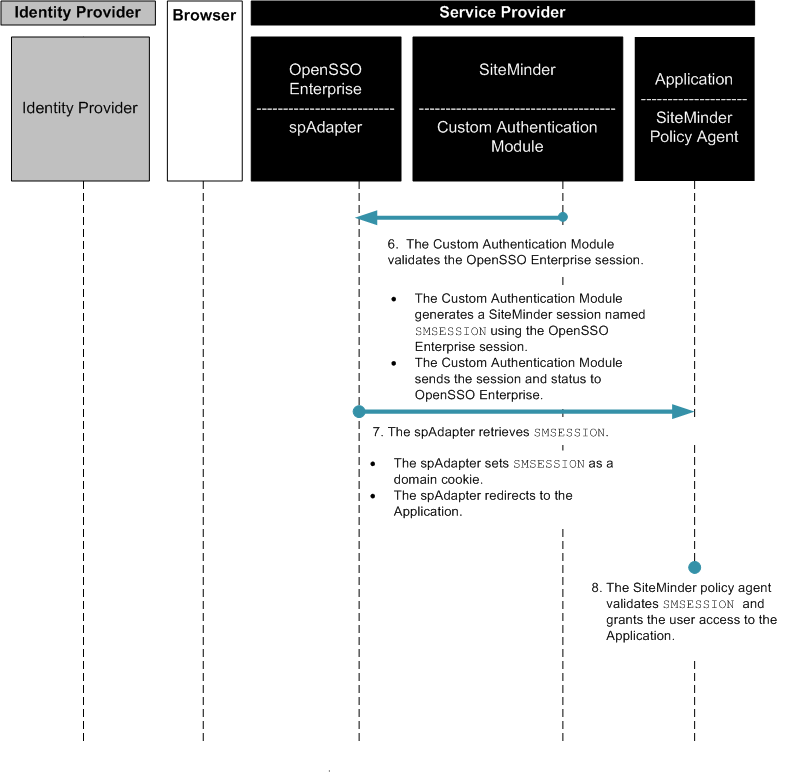
Setting Up and Configuring Single Sign-On with SiteMinder and OpenSSO Enterprise
To co-locate both SiteMinder and OpenSSO Enterprise in the same federation environment, you must install the OpenSSO Enterprise server and OpenSSO Enterprise policy agents. The setup requires OpenSSO Enterprise 8.0 and the corresponding Policy Agents. OpenSSO Enterprise is supported on various containers, however, you must choose a container where both OpenSSO Enterprise and SiteMinder Policy Agents are supported.
The SiteMinder software is not available online, and you must have an account with Computer Associates to obtain the software. To validate this document, the following components were deployed in a lab environment:
-
Sun OpenSSO Enterprise 8.0
-
Sun Web Server 6.1 SP5
-
Sun Directory Server 5.2 SP2
-
CA SiteMinder Server 6.0 SP5
-
CA SiteMinder Agent 6.0 for iPlanet Web Server 6.1
-
CA SiteMinder SDK 6.0 SP5
-
Custom codes (Bundled in the OpenSSO Enterprise zip)
The OpenSSO Enterprise bundle ships integration bits contained in the OpenSSO Enterprise WAR file. Instructions for configuring the authentication modules are described in corresponding README files. For more detailed steps for complete integration see the Chapter 2, Integrating CA SiteMinder, in Sun OpenSSO Enterprise 8.0 Integration Guide.
Evaluating Benefits and Tradeoffs
As you design your deployment architecture, be sure to consider the benefits, tradeoffs. The following lists may help you determine if enabling federation using SiteMinder and OpenSSO Enterprise is appropriate to meet your business needs.
Benefits
-
OpenSSO Enterprise allows you to continue using an existing SiteMinder deployment for authentication while leveraging the more advanced features of Federation Access Manager.
-
OpenSSO Enterprise quickly enables federation protocols for SiteMinder without few changes to the existing infrastructure.
-
OpenSSO Enterprise supports a variety of industry standard protocols such as SAMLv2 , ID-FF, ID-WSF, WS-Federation, XACML, WS-*, and others.
-
OpenSSO Enterprise supports any generic LDAP repository for users, and can work with the existing SiteMinder database.
-
OpenSSO Enterprise leverages its own configuration data store, which minimizes the need to migrate data from a different data store.
Tradeoffs
In general, when integrating any two access management products, you must consider the increased costs in resources and maintenance.
-
When co-locating SiteMinder and OpenSSO, session management for both the products must be synchronized.
-
Full integration requires you to set up session synchronization, possibly by using notification mechanisms effectively
-
Administrators must be trained and proficient in the use of both products.
Finding More Information
See the Chapter 2, Integrating CA SiteMinder, in Sun OpenSSO Enterprise 8.0 Integration Guide for detailed information about implementing single sign-on using CA SiteMinder and OpenSSO Enterprise.
- © 2010, Oracle Corporation and/or its affiliates
