Understanding High Availability Configuration Examples
Businesses use various combinations of single or multiple OpenSSO Enterprise servers and load balancers, in single or multiple sites, to achieve system failover and session failover. The following examples illustrate typical high-availability configurations and their respective process flows:
-
Single OpenSSO Enterprise Server Load Balancer in Single Site, No Session Failover
-
Multiple OpenSSO Enterprise Server Load Balancers in a Single Site, No Session Failover
-
Multiple OpenSSO Enterprise Server Load Balancers in Multiple Sites, No Session Failover
-
Single OpenSSO Enterprise Server Load Balancer in a Single Site with Session Failover
-
Multiple OpenSSO Enterprise Server Load Balancers in a Single Site with Session Failover
-
Multiple OpenSSO Enterprise Server Load Balancers in Multiple Sites with Session Failover
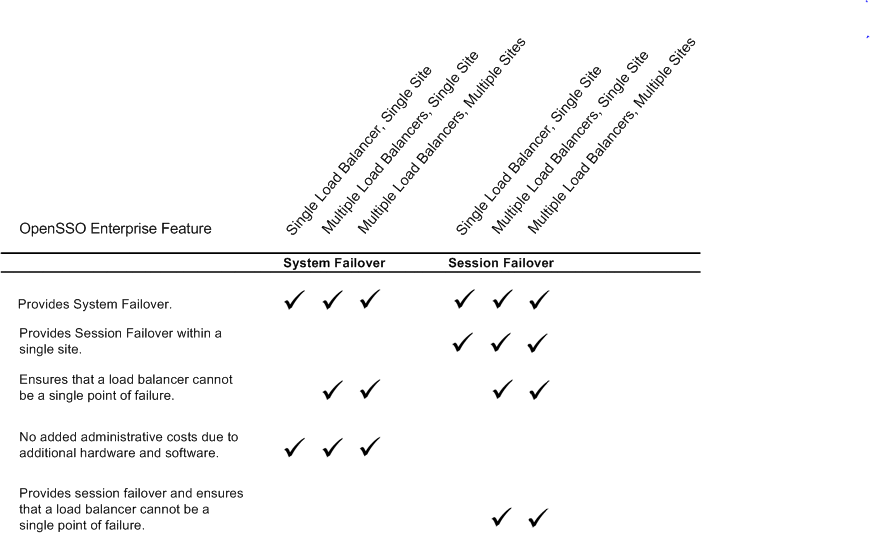
The following table summarizes the OpenSSO Enterprise features associated with each configuration example.
Figure 17–3 Comparison of High Availability Configuration Examples
Single OpenSSO Enterprise Server Load Balancer in Single Site, No Session Failover
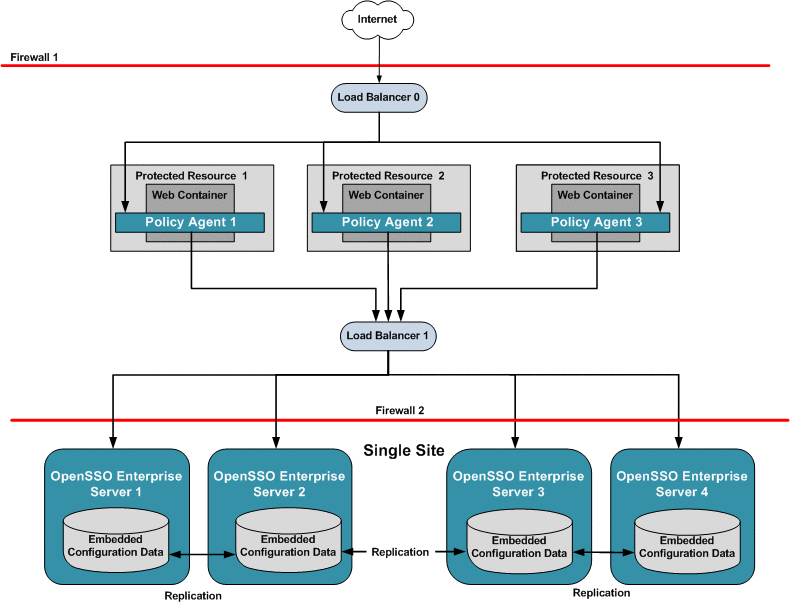
This is the most basic high-availability configuration. The single OpenSSO Enterprise server load balancer increases transaction throughput. When one OpenSSO Enterprise server is inaccessible, requests are automatically routed to other servers. However, the single load balancer can be a single point of failure. When this load balancer is inaccessible, no OpenSSO Enterprise services or session data are available to the Policy Agents.
Figure 17–4 Single OpenSSO Enterprise Server Load Balancer in a Single Site Configuration
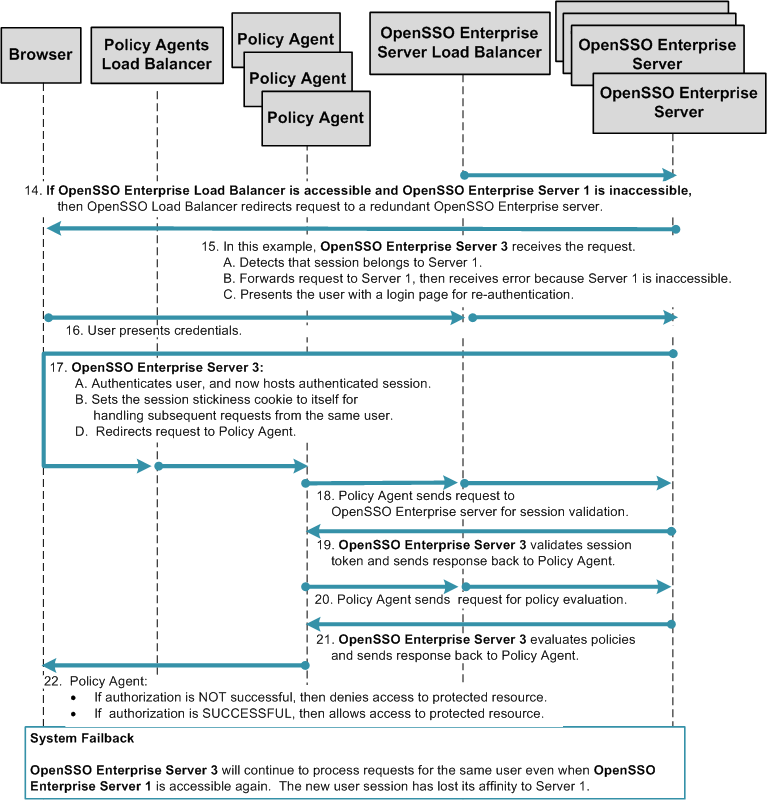
The following figure illustrates the session handling part of the process flow. See Figure 17–2 for a detailed illustration of steps 1 through 13.
Figure 17–5 Process Flow for Single OpenSSO Enterprise Server Load Balancer in a Single Site, No Session Failover
Multiple OpenSSO Enterprise Server Load Balancers in a Single Site, No Session Failover
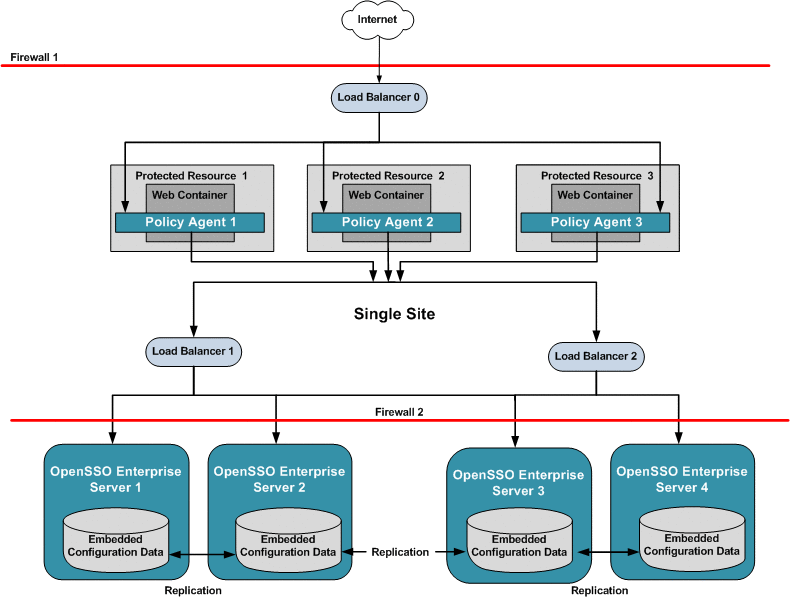
The following figure illustrates a deployment with multiple OpenSSO Enterprise server load balancers in front of redundant OpenSSO Enterprise servers. In this example, both OpenSSO Enterprise server load balancers are specified in each Policy Agent bootstrap configuration. The load balancers are also configured as login URL's in each Policy Agent configuration. Policy Agent configuration can reside on the same host as the Policy Agent, or can reside in the OpenSSO Enterprise embedded configuration data store. Regardless of where the configuration is hosted, when one OpenSSO Enterprise server load balancer is inaccessible, all requests are automatically routed to the other load balancer.
Figure 17–6 Multiple OpenSSO Enterprise Server Load Balancers in a Single Site, No Session Failover
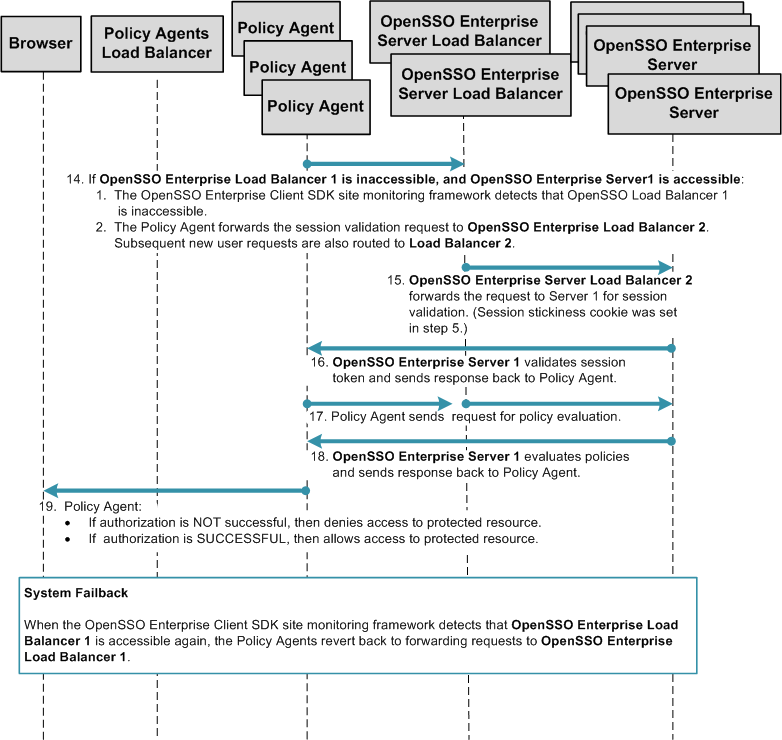
The following figure illustrates the session handling part of the process flow. See Figure 17–2 for a detailed illustration of steps 1 through 13.
Figure 17–7 Process Flow for Multiple OpenSSO Enterprise Server Load Balancers in a Single Site, No Session Failover
Multiple OpenSSO Enterprise Server Load Balancers in Multiple Sites, No Session Failover
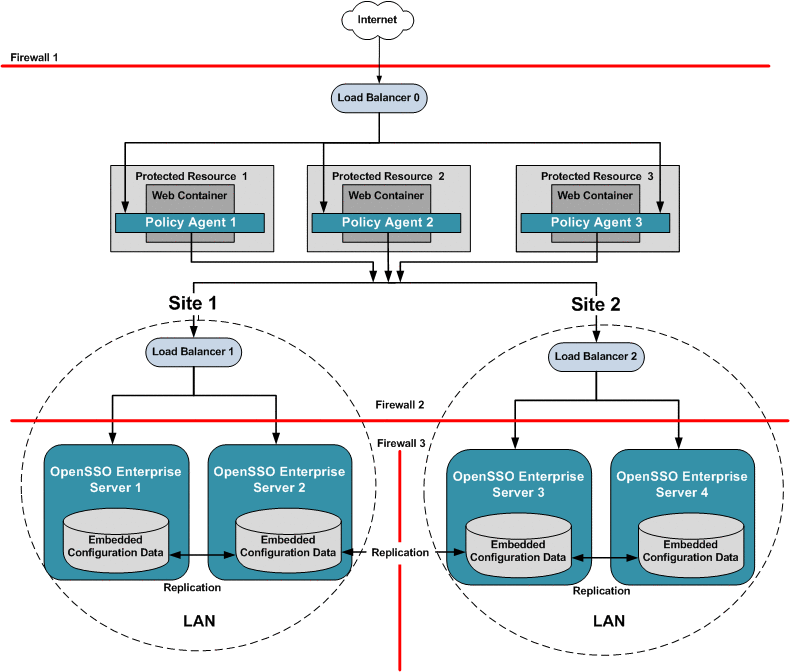
This deployment is useful if you want to logically group redundant OpenSSO Enterprise servers in a LAN or WAN environment. For example, you can configure redundant OpenSSO Enterprise servers to work as a single unit under a single site identifier. The redundant OpenSSO Enterprise servers provide one level of system failover. When you deploy multiple sites this way, the OpenSSO Enterprise servers in one site are logically isolated from the OpenSSO Enterprise servers in other sites.
In this example, both OpenSSO Enterprise server load balancers are specified in each Policy Agent bootstrap configuration. The load balancers are also configured as login URL's in each Policy Agent configuration. Policy Agent configuration can reside on the same host as the Policy Agent, or can reside in the OpenSSO Enterprise embedded configuration data store. When system failure occurs at the load balancer, one site fails over to another site.
The following figure illustrates minimum components required for a multiple-site configuration.
Figure 17–8 Multiple OpenSSO Enterprise Load Balancers in Multiple Sites, No Session Failover
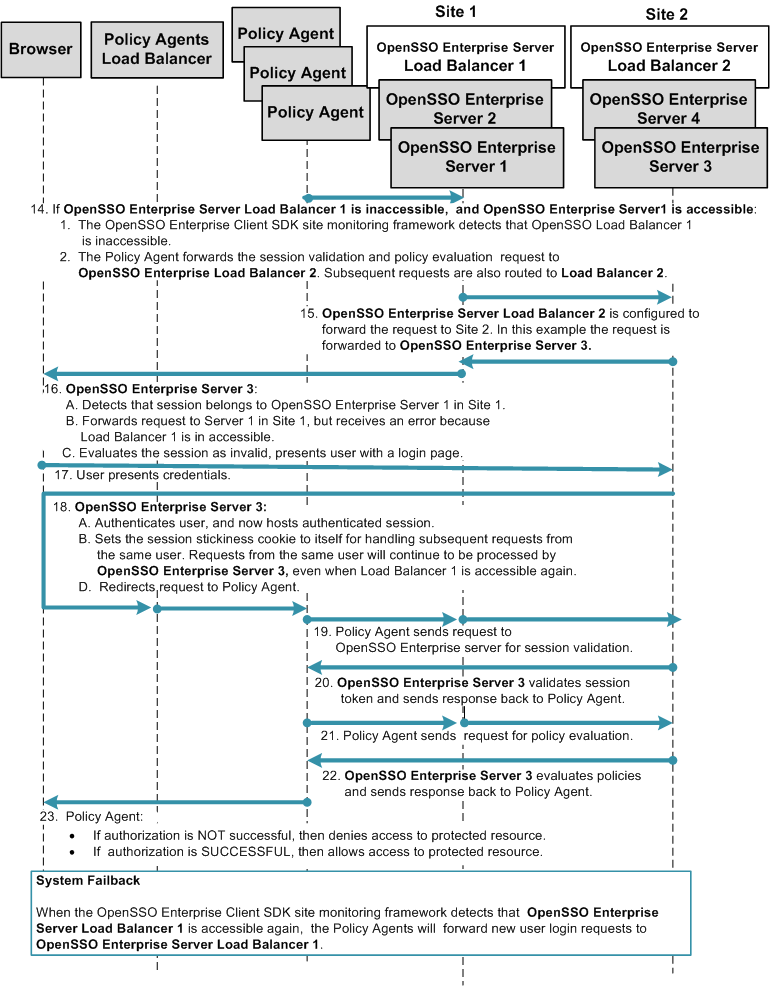
The following figure illustrates the session handling part of the process flow. See Figure 17–2 for a detailed illustration of steps 1 through 13.
Figure 17–9 Process Flow for Multiple OpenSSO Enterprise Server Load Balancers in Multiple Sites, No Session Failover
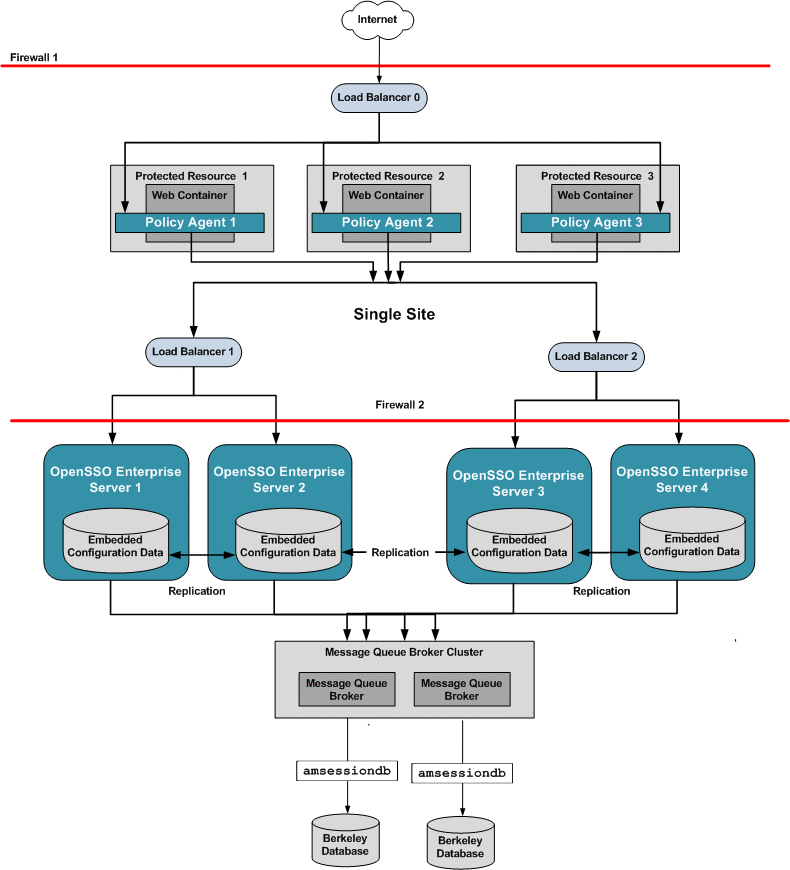
Single OpenSSO Enterprise Server Load Balancer in a Single Site with Session Failover
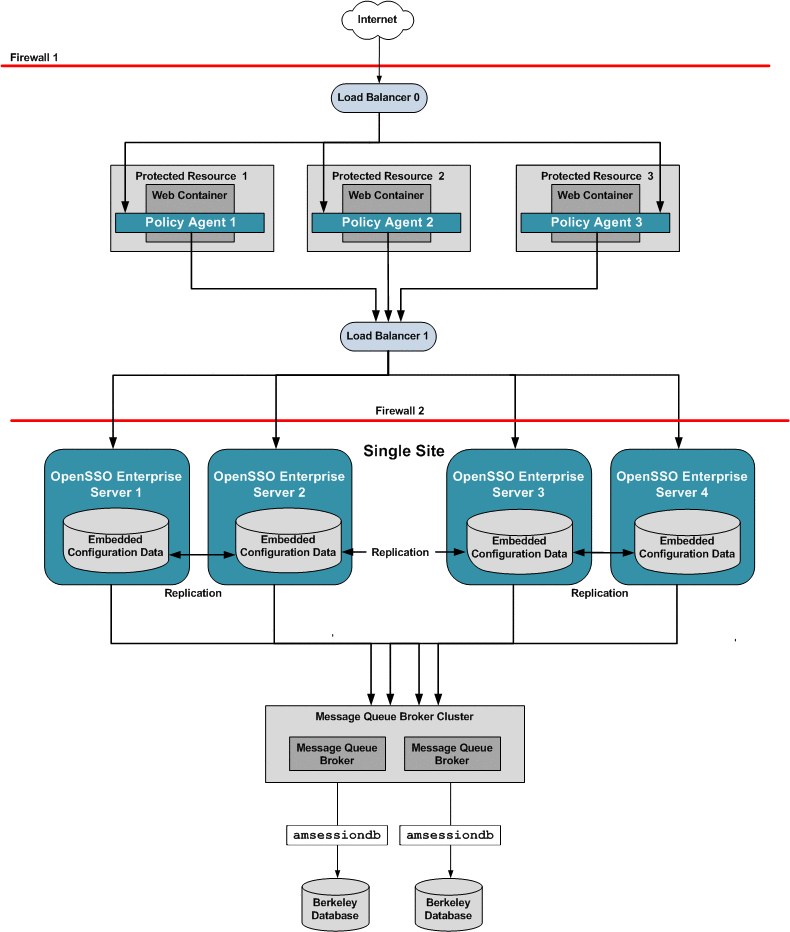
When you configure OpenSSO Enterprise for session failover, the user's authenticated session state is stored in the Berkeley Database in the event of a single hardware or software failure. In session failover deployments, you configure the OpenSSO Enterprise servers to communicate with Message Queue brokers which manage session state persistence in the Berkeley Database. This configuration enables the users session to fail over to a backup OpenSSO Enterprise server without losing any session state information. The user does not have to login again. The backup OpenSSO Enterprise server is determined among the available servers in the configuration list by an internal algorithm.
This type of deployment ensures the state availability even if one of the OpenSSO Enterprise servers is inaccessible due to scheduled maintenance, hardware failure, or software failure. However, the single load balancer can be a single point of failure. When this load balancer is inaccessible, no OpenSSO Enterprise services or session data are available to the Policy Agents.
The following figure illustrates the components in a basic OpenSSO Enterprise deployment using session failover.
Figure 17–10 Single OpenSSO Enterprise Server Load Balancer in a Single Site with Session Failover
The following figure illustrates the session handling part of the process flow. See Figure 17–2 for a detailed illustration of steps 1 through 13.
Figure 17–11 Single OpenSSO Enterprise Server Load Balancer in a Single Site with Session Failover
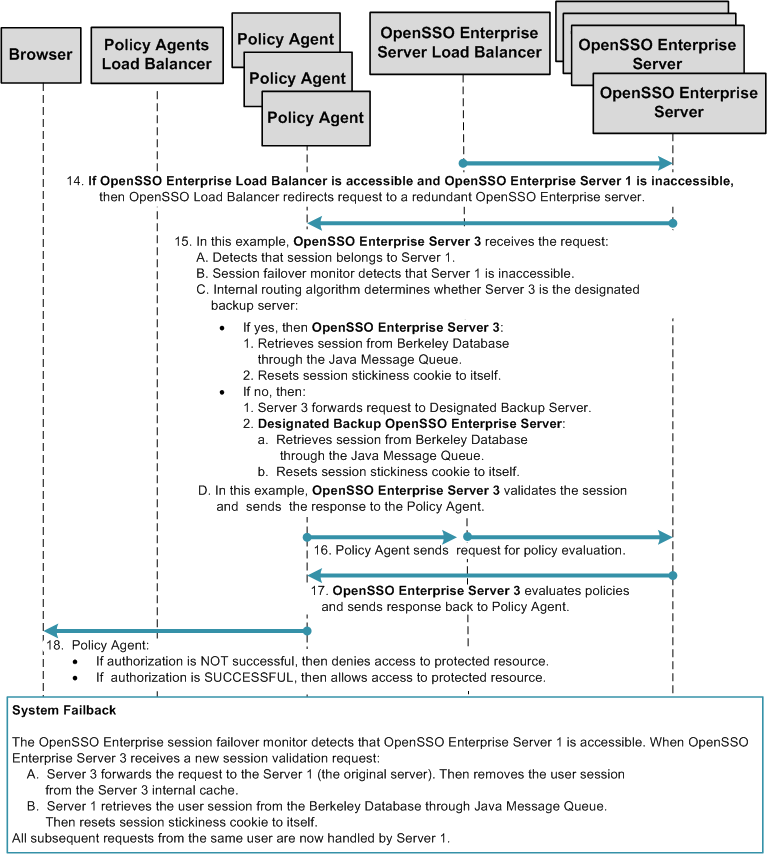
Multiple OpenSSO Enterprise Server Load Balancers in a Single Site with Session Failover
This deployment is very similar to Single OpenSSO Enterprise Server Load Balancer in a Single Site with Session Failover , but with two important differences. In this deployment multiple OpenSSO Enterprise server load balancers exist. Additionally, the OpenSSO Enterprise server load balancers are specified in each Policy Agent bootstrap configuration. This deployment provides load balancer failover to ensure continuous service when system failure occurs. When system failure occurs at the load balancer, one site fails over to another site.
The load balancers are also configured as login URL's in each Policy Agent configuration. Policy Agent configuration can reside on the same host as the Policy Agent, or can reside in the OpenSSO Enterprise embedded configuration data store.
The following figure illustrates a deployment with multiple OpenSSO Enterprise server load balancers with session failover.
Figure 17–12 Multiple OpenSSO Enterprise Server Load Balancers in a Single Site with Session Failover
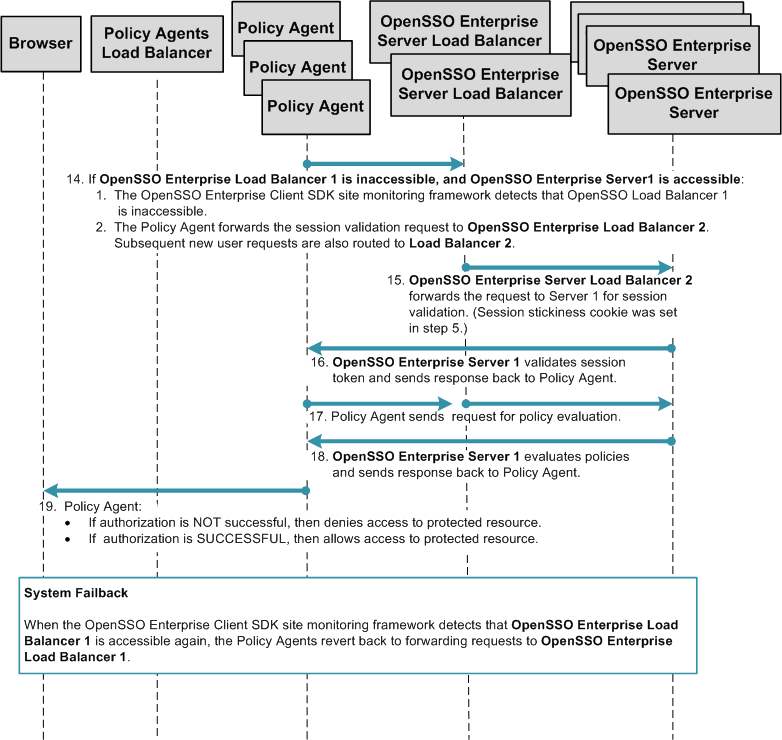
The following figure illustrates the session handling part of the process flow. See Figure 17–2 for a detailed illustration of steps 1 through 13.
Figure 17–13 Multiple OpenSSO Enterprise Server Load Balancers in a Single Site with Session Failover
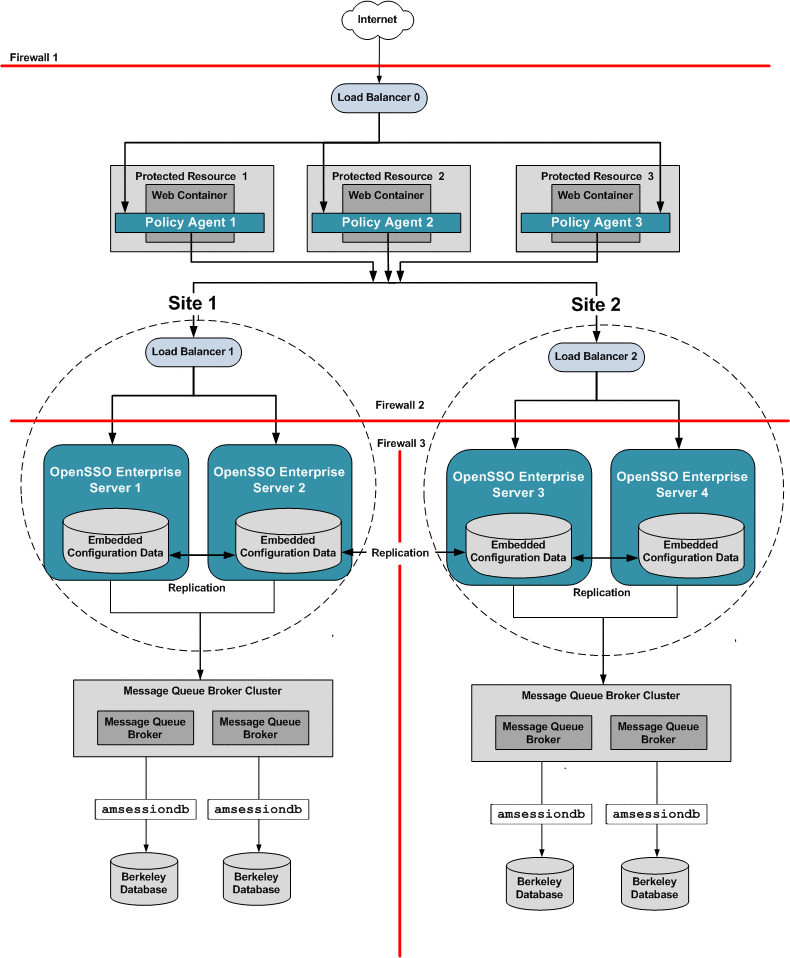
Multiple OpenSSO Enterprise Server Load Balancers in Multiple Sites with Session Failover
This deployment is useful if you want to logically group redundant OpenSSO Enterprise servers in a LAN or WAN environment. For example, you can configure redundant OpenSSO Enterprise servers to work as a single unit under a single site identifier. Redundant OpenSSO Enterprise servers provide one level of system failover. When you deploy multiple sites this way, the OpenSSO Enterprise servers in one site are logically isolated from the OpenSSO Enterprise servers in other sites.
For an added level of system failover, you can configure one site to fail over to another site. In this example, both OpenSSO Enterprise server load balancers are specified in each Policy Agent bootstrap configuration. The load balancers are also configured as login URL's in each Policy Agent configuration. Policy Agent configuration can reside on the same host as the Policy Agent, or can reside in the OpenSSO Enterprise embedded configuration data store. When system failure occurs at the load balancer, one site fails over to another site.
This deployment ensures both system failover and session failover if one of the OpenSSO Enterprise load balancers or one of the OpenSSO Enterprise servers is inaccessible for any reason. The following issues are addressed in this deployment:
-
Logical grouping of OpenSSO servers can be achieved across distant geographic locations within a WAN environment or locally within a LAN environment.
-
The Message Queue broker and Berkeley Database provide the means for session failover.
-
Session failover is not supported among multiple sites.
-
The user's authenticated session state is maintained in the event of a single hardware or software failure. This allows the user session to fail over to a backup OpenSSO Enterprise server without losing session information. If system failure occurs within the site, the user does not have to log in again.
-
The backup OpenSSO Enterprise server is determined by an internal algorithm. The internal algorithm selects from the server configuration list one of the available servers from same site.
-
System failover works among OpenSSO Enterprise servers in different sites.
The following figure illustrates a complex high availability deployment using both system failover and session failover in multiple sites.
Figure 17–14 Multiple OpenSSO Enterprise Server Load Balancer in Multiple Sites with Session Failover
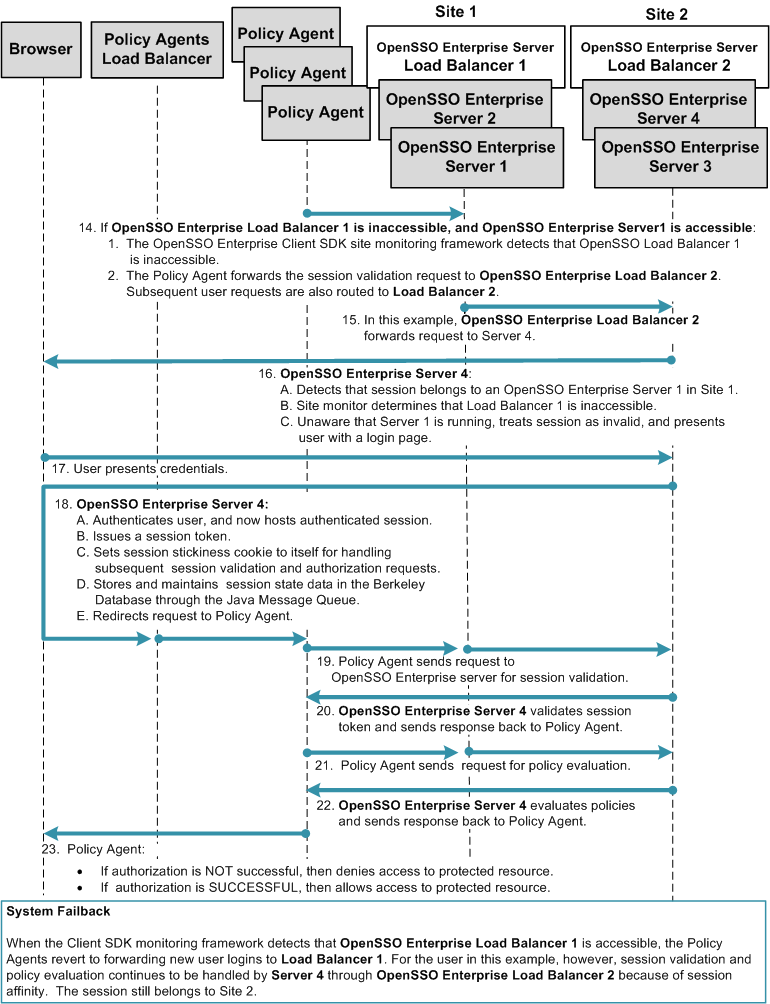
The following figure illustrates the session handling part of the process flow. See Figure 17–2 for a detailed illustration of steps 1 through 13.
Figure 17–15 Multiple OpenSSO Enterprise Server Load Balancers with Session Failover in Each Site
- © 2010, Oracle Corporation and/or its affiliates
