Use Case 2
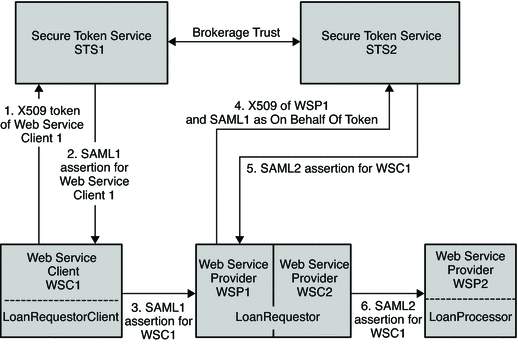
The following figure illustrates the process flow for a bank loan web service using a SAML 1 security token.
Figure 11–7 Process Flow for a Bank Loan Web Service Using SAML1 Security Token
-
WSC1 authenticates to STS1 with its X509 token.
-
WSC1 gets to SAML1 token (owner is WSC1).
-
WSC1 secures web service to WSP1 with its SAML1 token.
-
WSP1 then authenticates to STS2 with its X509 token, and sends the SAML1 token of WSC1.
-
The SAML1 token is sent on behalf of the X509 token in order to convert it to SAML2 token for WSC1.
-
WSC2 just passes through this SAML2 token of WSC1 to WSP2.
WSC2 secures the web service to WSP2 with the SAML2 token of WSC1.
The following are configuration suggestions for the Bank Loan use case:
-
WSC agent - profile name is LoanRequestorService for WSC1
- Security Mechanism:
-
STSSecurity
- STS config:
-
SecurityTokenService
-
WSP agent - profile name is wsp for WSP1
- WSP End Point:
-
Default
- Authentication Chain:
-
ldapService
- Token Conversion Type:
-
SAML2 token
-
WSC agent - profile name is LoanProcessorService for WSC2
- Use Pass Through Security Token
-
Enabled
- © 2010, Oracle Corporation and/or its affiliates
