Installing the Client SDK by Deploying the Sample WAR
opensso-client.zip is in the samples directory of the downloaded and inflated opensso.zip. Unzipping opensso-client.zip reveals the war and sdk directories. The war directory contains two versions of the Client SDK WAR depending on the version of Java installed on your machine.
-
opensso-client-jdk15.war is for web containers running JDK 1.5 or later.
-
opensso-client-jdk14.war is for web containers running JDK 1.4.2 or later.
The following sections contain the procedures for deploying the Client SDK WAR and running the web-based and command line samples.
 To Install the Client SDK by Deploying the
Sample WAR
To Install the Client SDK by Deploying the
Sample WAR
Before You Begin
-
Download and unzip opensso_enterprise_80.zip as described in the Sun OpenSSO Enterprise 8.0 Installation and Configuration Guide. The compressed Client SDK ZIP is in the zip-root/opensso/samples/ directory where zip-root is the directory in which you unzipped the OpenSSO Enterprise download.
-
Deploy opensso.war as described in the Sun OpenSSO Enterprise 8.0 Installation and Configuration Guide.
-
Install a web container on the host machine on which the Client SDK will be deployed.
-
AMConfig.properties, openssoclientsdk.jar and servlet.jar are required in the CLASSPATH of the host machine on which the Client SDK is installed.
-
Copy the compressed opensso-client.zip to a staging directory on the host machine where you plan to deploy the Client SDK.
-
Unzip opensso-client.zip.
-
Set the JAVA_HOME environment variable to JDK 1.5 or 1.4, depending on the version of Java installed on your machine.
-
Deploy the appropriate Client SDK WAR (opensso-client-jdk14.war or opensso-client-jdk15.war) depending on the version of Java installed on your machine.
-
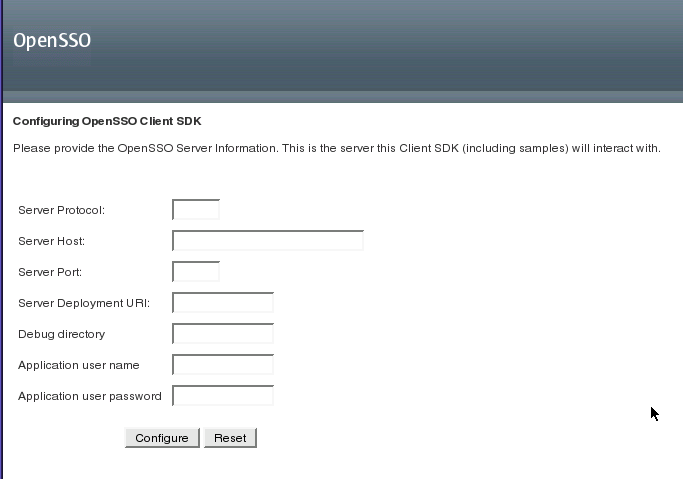
After successful deployment, launch the Client SDK configuration screen.
-
Provide the appropriate values pertaining to the instance of OpenSSO Enterprise with which the Client SDK will be communicating.
-
Server Protocol Protocol (http or https) used by the web container on which OpenSSO Enterprise is deployed.
-
Server Host Fully qualified domain name (FQDN) of the host machine on which OpenSSO Enterprise is deployed.
-
Server Port Port used by OpenSSO Enterprise server.
-
Server Deployment URI URI defined during OpenSSO Enterprise deployment. The default is /opensso. Be sure to include the leading slash (/).
-
Debug directory: Location of the debug directory; for example, /opensso/debug
-
Application user name:: The policy agent user that communicates with OpenSSO Enterprise; by default, agentAuth.
-
Application user password: Password of the policy agent user that communicates with OpenSSO Enterprise.
-
-
Click Configure.
A message signifying successful configuration is displayed.
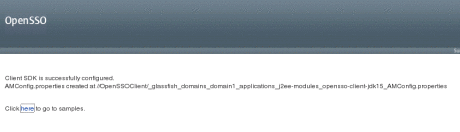
AMConfig.properties for the Client SDK is also created. AMConfig.properties has been deprecated for OpenSSO Enterprise. The server configuration data is now stored in an embedded data store. The Client SDK, however, still uses AMConfig.properties to store its configuration data as it is remote to the installed OpenSSO Enterprise server. For information about the location of the AMConfig.properties file and setting properties in the file, see Using AMConfig.properties With the Client SDK.
 To Run the Client SDK Web-based Samples
To Run the Client SDK Web-based Samples
Before You Begin
This procedure assumes you have completed To Install the Client SDK by Deploying the Sample WAR and the successful configuration screen is still displayed.
-
Click the word here on the successful configuration screen displayed at the end of To Install the Client SDK by Deploying the Sample WAR.
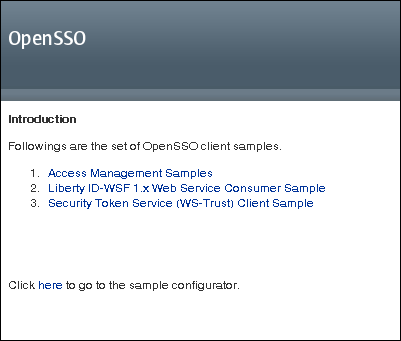
The web-based samples introduction page is displayed.
-
Click Access Management Samples.
The Client SDK - Samples page is displayed.

-
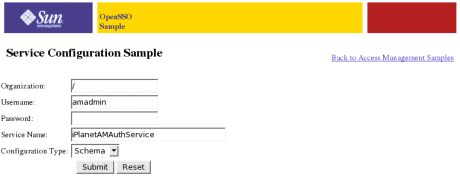
Click Service Configuration Sample Servlet.
The Service Configuration Sample page is displayed.
-
Enter the password for the amadmin user.
-
Choose either Schema or Config from the drop-down list.
Schema refers to the data structure of the service. Default values may be defined dependent of the service. Config is the actual data. The output is defined as key/value pairs.
-
Click Submit.
ServiceConfigServlet.java retrieves the attributes of the Authentication Service (or other input service) and the SSOToken of the questioning user.
Tip –If an error message is displayed, confirm that the com.sun.identity.agents.app.username has a value of agentAuth and com.iplanet.am.service.password has a value of changeit in the Client SDK AMConfig.properties. If you need to modify this file, restart the underlying web container.
-
Click Back to Access Management Samples.
-
Click User Profile (Attributes) Sample Servlet.
The User Profile Sample page is displayed.
-
Enter the password for the default amadmin or another defined user name and password and click Submit.
The UserProfileServlet.java retrieves and displays the profile that corresponds to the user ID entered in the Username text box.
-
Click Back to Access Management Samples.
-
Click Policy Evaluator Client Sample Servlet.
The Policy Evaluator Client Sample page is displayed.
-
Open a new browser window, login to OpenSSO Enterprise, and using the console, create a policy for the resource http://www.sun.com:80 with a GET allow and POST deny rule for all authenticated users on Fridays.
-
Back on the Policy Evaluator Client Sample page, enter the amadmin password and the resource http://www.sun.com:80.
-
Click Submit.
PolicyClientServlet.java is the call on the client side that initiates the retrieval of a policy decision (from the Policy Service) that would be passed to a web agent for enforcement.
-
Click Back to Access Management Samples.
-
Log in to the OpenSSO Enterprise as amadmin if not already.
You must be logged in and have an SSOToken for the Single Sign On Token Verification Servlet.
-
Back on the Access Management Samples page, click Single Sign On Token Verification Servlet.
The user profile associated with the SSOToken received after successful authentication is displayed. The code included with this sample is SSOTokenSampleServlet.java and SampleTokenListener.java. These files serve as a basis for using the SSO API, demonstrating how you can create an SSOToken, call various methods from the token, set up an event listener and get notified on event changes.
Next Steps
Two other samples using the Client SDK are included on the web-based samples introduction page: the Liberty ID-WSF 1.x Web Service Consumer Sample and the Security Token Service (WS-Trust) Client Sample. See the instructions for these samples when you click the sample name.
 To Run the Client SDK Command Line Samples
To Run the Client SDK Command Line Samples
This procedure documents compiling the command line samples as well as running them. It uses the scripts for the Solaris and Linux operating systems. opensso-client-zip-root refers to the directory in which you decompressed the appropriate Client SDK WAR.
Be sure to run all the scripts discussed one level up from the directory in which they are found.
Before You Begin
This procedure assumes you have completed To Install the Client SDK by Deploying the Sample WAR and the successful configuration screen is still displayed.
-
On the command line of the machine on which the Client SDK is installed, change to opensso-client-zip-root/sdk/scripts and run chmod to make the scripts executable.
# cd opensso-client-zip-root/sdk/scripts # chmod 755 *.sh
-
Execute compile-samples.sh to compile the scripts.
# cd ../ # scripts/compile-samples.sh
-
Run the setup script to initialize the command line samples.
# cd ../ # scripts/setup.sh
Note –Use setup.bat on Windows systems.
The script uses Main.java and creates AMConfig.properties with a pointer to the opensso-client-zip-root/sdk/resources directory.
-
Run the individual Client SDK samples by executing the rest of the scripts in the /scripts directory.
- Login.sh/Login.bat
-
Uses Login.java to log in and log out a user.
- CommandLineSSO.sh/CommandLineSSO.bat
-
Uses CommandLineSSO.java to retrieve a user profile.
- CommandLineIdrepo.sh/CommandLineIdrepo.bat
-
Uses its myriad source files to perform operations on the identity data store. For example, create an identity, delete an identity, and search or select an identity.
- CommandLineLogging.sh/CommandLineLogging.bat
-
Uses its myriad source files (including LogSample.java) to demonstrate the login process and write a log record of a successful authentication. You will need to authenticate two identities: the subject of the LogRecord and the logger (amadmin).
- SSOTokenSample.sh/SSOTokenSample.bat
-
to verify an SSOToken. Uses SSOTokenSample.java to demonstrate this and other functions of the session API.
Note –Before running this sample, you will need an SSO Token ID. You can get this by running the Service Configuration Sample in To Run the Client SDK Web-based Samples and copying the ID that is displayed.
- run-policy-evaluation-sample.sh/run-policy-evaluation-sample.bat
-
Returns a policy decision based on console created user and configured policy. Uses the code sourced in the policy directory on opensso.dev.jave.net.
- run-xacml-client-sample.sh/run-xacml-client-sample.bat
-
Uses XACMLClientSample.java to construct a XACML request, to make an authorization query, receive the decision, and print out the response.
Note –At run time, a sample might require additional property files to be setup in the /resources directory. Check the comments included in each individual script for more information.
- © 2010, Oracle Corporation and/or its affiliates
