 To Configure the OpenSSO Enterprise Identity
and Service Providers for SAML2 Protocols
To Configure the OpenSSO Enterprise Identity
and Service Providers for SAML2 Protocols
-
Generate the metadata templates on both Identity Provider and Service Provider environments.
Use the famadm command, or used use a browser to go to the following URL:
http:<host>:<port>/opensso/famadm.jsp
-
At the Identity Provider:
famadm create-metadata-templ -y idp_entity_id -u amadmin -f admin_password_file_name -m idp_standard_metadata -x idp_extended_metadata -i idp_meta_alias
where idp_meta_alias is /idp
-
At the Service Provider:
famadm create-metadata-templ -y sp_entity_id -u amadmin -f admin_password_file_name -m sp_standard_metadata -x sp_extended_metadata -s sp_meta_alias
where sp_meta_alias is /sp
-
-
Customize the Service Provider extended metadata.
Add the Service Provider extended metadata as an attribute named as spAdapter. This attribute is used by the SAML protocols to do any post single sign-on authentication processes. In the architecture diagram, this the Oracle Access Manager Plug-in. The OAMPlugin uses the OpenSSO Enterprise session to authenticate against Oracle Access Manager and establish ObSSOCookie. The Service Provider metadata must have the following attributes:
<Attribute name="spAdapter"> <Value>com.sun.identity.saml2.plugins.SMAdapter</Value> </Attribute> <Attribute name="spAdapterEnv"> <Value>FAMCookieName=iPlanetDirectoryPro</Value> <Value>OAMCookieName=ObSSOCookie</Value> <Value>CookieDomain=.red.example.com</Value> <Value>Resource=/test/index.html</Value> <Value>ObSDKInstallDir=/export/oam/AccessServerSDK</Value> </Attribute> -
Set the value for transientUser to the anonymous user.
The Service Provider extended metadata has an attribute named as transientUser. Make sure that the OpenSSO Enterprise Service Provider is enabled for Anonymous authentication.
<Attribute name="transientUser"> <Value>anonymous</Value> </Attribute>
-
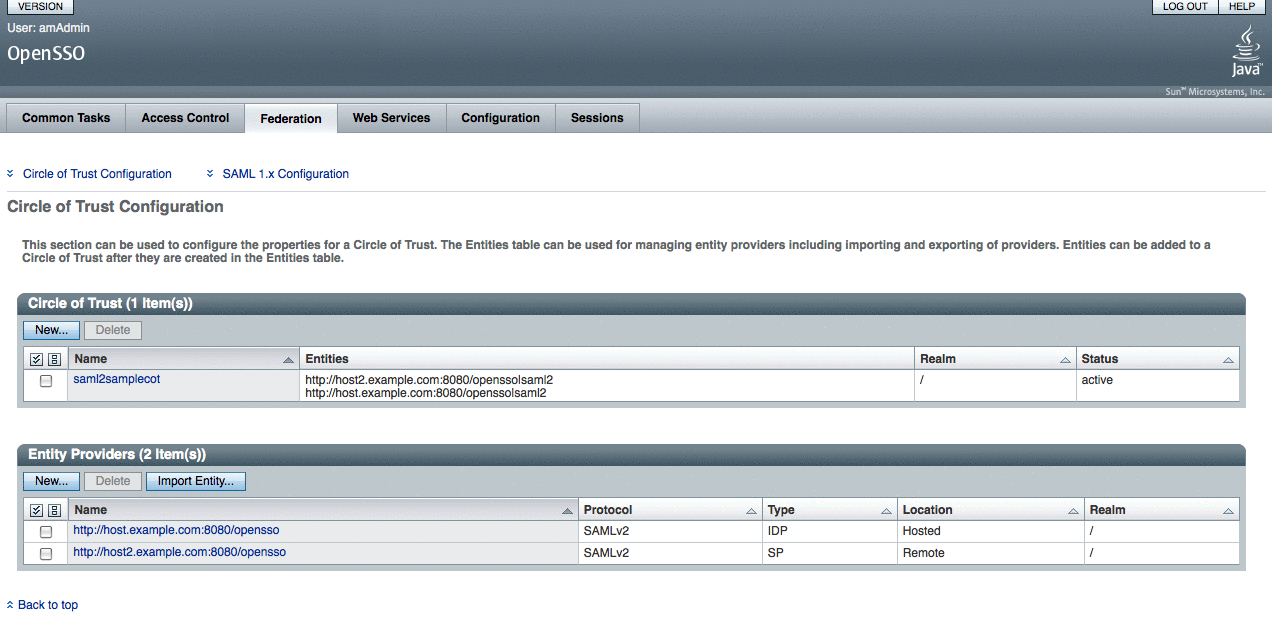
Create a circle of trust.
The circle of trust should also be added in your extended metadata.
-
Load the metadata.
-
Edit the following attribute to one of your circle of trust.
The extended template files contains a sample circle of trust.
<Attribute name="cotlist"> <Value>samplesaml2cot</Value> </Attribute>
You can also add the circle of trust through the OpenSSO Enterprise administration console.
-
Load the hosted metadata in both the Identity Provider and Service Provider.
You can use the famadm command or the OpenSSO Enterprise administration console.
-
Exchange the metadata between Identity Provider and Service Provider.
and load the metadata.
-
Verify through OpenSSO Enterprise administration console that the metadata is configured properly.
- © 2010, Oracle Corporation and/or its affiliates
