Directory Proxy Server Configured for Proxy Authorization
When Directory Proxy Server is configured for proxy authorization, Directory Proxy Server can add a proxy authorization control to a client request. The client request is then forwarded with the authorization of the specified in the proxy authorization control.
To simplify the configuration of ACIs, Directory Proxy Server can be configured to allow anonymous reads and to apply proxy authorization for write operations.
If Directory Proxy Server is configured for proxy authorization and the client request contains its own proxy authorization control, Directory Proxy Server does not add a proxy authorization control. In this case, Directory Proxy Server checks with the backend LDAP server that the client has the right to use its proxy authorization control. If the client has the right to use its proxy authorization control, Directory Proxy Server forwards the request with the authorization specified in the client's proxy authorization control.
For information about how to configure proxy authorization in Directory Proxy Server, see Forwarding Requests With Proxy Authorization in Sun Directory Server Enterprise Edition 7.0 Administration Guide
Connections When Directory Proxy Server Is Configured for Proxy Authorization
When Directory Proxy Server is configured for proxy authorization, a client is usually authenticated to the Directory Proxy Server by a non-anonymous BIND or by a SASL external BIND, however, clients can also be anonymous. Directory Proxy Server is usually bound to the data sources by using an administrative identity.
Figure 19–2 shows the connections between a client, Directory Proxy Server, and backend LDAP servers, when Directory Proxy Server is configured for proxy authorization.
Figure 19–2 Connections for Proxy Authorization
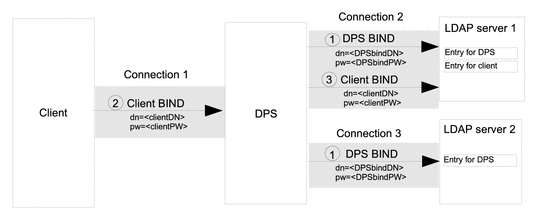
The connections for proxy authorization are made in the following stages:
-
When Directory Proxy Server is initiated, it opens a connection to each LDAP server. Directory Proxy Server binds to LDAP server 1 and LDAP server 2 by providing its DN and password, DPSbindDN and DPSbindPW.
An entry for DPSbindDN exists in both the LDAP servers and the BIND requests are granted. Directory Proxy Server is bound to the LDAP servers, on connection 2 and connection 3.
-
When a client connects to Directory Proxy Server, the client binds by providing its DN and a password, clientDN and clientPW.
-
The Directory Proxy Server authenticates the client to LDAP server 1 by using the client's credentials and by reusing connection 2.
An entry for the client exists in LDAP server 1 and the BIND request is granted. The client is bound to Directory Proxy Server on connection 1.
Directory Proxy Server Configured for Proxy Authorization and the Client Request Does Not Contain a Proxy Authorization
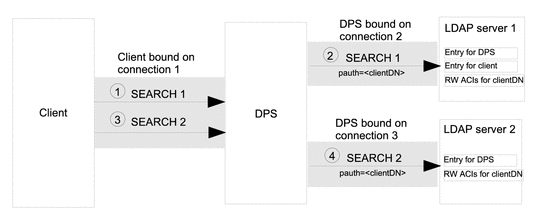
Figure 19–3 shows the flow of information when Directory Proxy Server is configured for proxy authorization. The client in Figure 19–2 makes, and Directory Proxy Server adds a proxy authorization control.
Figure 19–3 Information Flow When Proxy Authorization Control Is Added by Directory Proxy Server
-
The client sends a SEARCH request SEARCH 1, that does not contain a proxy authorization control. The request is targeted at LDAP server 1.
-
Directory Proxy Server adds a proxy authorization control to the request and forwards the SEARCH operation to LDAP server 1, reusing connection 2.
The SEARCH operation is performed with the authorization of the user specified in the proxy authorization control. That authorization is defined in the RW ACIs on the LDAP server for the user specified in the proxy authorization control.
-
The client sends a second SEARCH request, SEARCH 2, that does not contain a proxy authorization control. The request is targeted at LDAP server 2.
-
The Directory Proxy Server forwards the SEARCH operation to LDAP server 2, reusing connection 3.
Notice that it is not necessary for the client to bind to LDAP server 2 before the request can be processed, and it is not necessary for the LDAP server to contain an entry for the client.
Directory Proxy Server Configured for Proxy Authorization and the Client Request Does Contain a Proxy Authorization
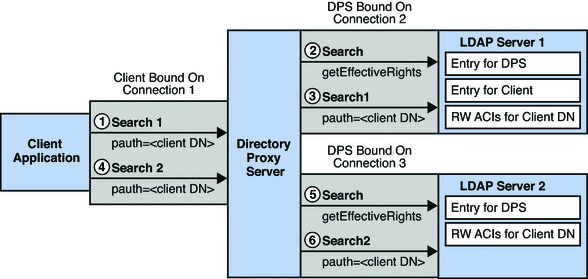
Figure 19–3 shows the flow of information when the client in Figure 19–2 makes a request that does contain a proxy authorization control. Directory Proxy Server verifies that the client has the right to use its proxy authorization control.
Figure 19–4 Information Flow When Proxy Authorization Control Is Contained in the Client Request
-
The client sends a SEARCH request SEARCH 1, that contains a proxy authorization control. The request is targeted at LDAP server 1.
-
Directory Proxy Server verifies that the clientDN has the right to use a proxy authorization control on LDAP server 1, by getting the effective rights of the client on LDAP server 1. For information about how to get effective rights, see Viewing Effective Rights in Sun Directory Server Enterprise Edition 7.0 Administration Guide
-
Directory Proxy Server forwards the SEARCH operation to LDAP server 1, reusing connection 2.
The SEARCH operation is performed with the authorization of the user specified in the proxy authorization control. The authorization is defined in the RW ACIs on the LDAP server.
-
The client sends a second SEARCH request, SEARCH 2, that contains a proxy authorization control. The request is targeted at LDAP server 2.
-
Directory Proxy Server verifies that the clientDN has the right to use a proxy authorization control on LDAP server 2, by getting the effective rights of the client on LDAP server 2.
-
The Directory Proxy Server forwards the SEARCH operation to LDAP server 2, reusing connection 3.
Notice that it is not necessary for the client to bind to LDAP server 2 before the request is processed, and it is not necessary for the LDAP server to contain an entry for the client.
Security Issues When Directory Proxy Server Is Configured for Proxy Authorization
Consider the following security risks before configuring Directory Proxy Server for proxy authorization:
-
When Directory Proxy Server is configured for proxy authorization, it assumes the rights of any client for which it forwards a request. A Directory Proxy Server that is not authorized to perform write operations on data, can perform those operations by using proxy authorization.
-
An LDAP server must contain an entry with the appropriate R/W ACIs for the user specified in the proxy authorization control. If the entry was accessed illegally by a third party, that party might be able to impersonate.
-
The authorization identity configured in the proxy authorization control must be protected from tampering.
- © 2010, Oracle Corporation and/or its affiliates
