Chapter 4 Overview of TCP/IP
This chapter introduces the Solaris implementation of the TCP/IP network protocol suite. The information is particularly geared to network administrators who are unfamiliar with TCP/IP. (For an introduction to basic network concepts, see Chapter 2, Network Services Overview.) If you are an experienced TCP/IP network administrator, consider moving on to chapters covering the tasks you want to perform. The following subjects are covered in this chapter:
Introducing the Internet Protocol Suite
This section presents an in-depth introduction to the protocols that compose TCP/IP. Although the information is conceptual, you should learn the names of the protocols and what each does. This is important because TCP/IP books explain tasks with the assumption that you understand the concepts introduced here.
TCP/IP is the commonly used nickname for the set of network protocols composing the Internet Protocol suite. Many texts use the term "Internet" to describe both the protocol suite and the global wide-area network. In this book, the "TCP/IP" refers specifically to the Internet protocol suite; "Internet" refers to the wide-area network and the bodies that govern it.
To interconnect your TCP/IP network with other networks, you must obtain a unique IP network number. At the time of this writing, IP network numbers are assigned by an organization known as the InterNIC.
If hosts on your network are going to participate in the Internet Domain Name system (DNS), you must obtain and register a unique domain name. The InterNIC also handles the registration of domain names under certain top-level domains such as .com (commercial), .edu (education), and .gov (government). Chapter 5, Planning Your TCP/IP Network contains more information about the InterNIC. (For more information on DNS, refer to Solaris Naming Administration Guide.)
Protocol Layers and the OSI Model
Most network protocol suites are structured as a series of layers, sometimes referred to collectively as a protocol stack. Each layer is designed for a specific purpose and exists on both the sending and receiving hosts. Each is designed so that a specific layer on one machine sends or receives exactly the same object sent or received by its peer process on another machine. These activities take place independently from what is going on in layers above or below the layer under consideration. In other words, each layer on a host acts independently of other layers on the same machine, and in concert with the same layer on other hosts.
OSI Reference Model
Most network protocol suites are viewed as structured in layers. This is a result of the Open Systems Interconnect (OSI) Reference Model designed by the International Standards Organization (ISO). The OSI model describes network activities as having a structure of seven layers, each of which has one or more protocols associated with it. The layers represent data transfer operations common to all types of data transfers among cooperating networks.
The protocol layers of the OSI Reference Model are traditionally listed from the top (layer 7) to the bottom (layer 1) up, as shown in the following table.
Table 4-1 The Open Systems Interconnect Reference Model|
Layer No. |
Layer Name |
Description |
|---|---|---|
|
7 |
Consists of standard communication services and applications that everyone can use |
|
|
6 |
Ensures that information is delivered to the receiving machine in a form that it can understand |
|
|
5 |
Manages the connections and terminations between cooperating computers |
|
|
4 |
Manages the transfer of data and assures that received and transmitted data are identical |
|
|
3 |
Manages data addressing and delivery between networks |
|
|
2 |
Handles the transfer of data across the network media |
|
|
1 |
Defines the characteristics of the network hardware |
The operations defined by the OSI model are conceptual and not unique to any particular network protocol suite. For example, the OSI network protocol suite implements all seven layers of the OSI Reference Model. TCP/IP uses some of OSI model layers and combines others. Other network protocols, such as SNA, add an eighth layer.
TCP/IP Protocol Architecture Model
The OSI model describes an idealized network communications protocol family. TCP/IP does not correspond to this model directly, as it either combines several OSI layers into a single layer, or does not use certain layers at all. The following table shows the layers of the Solaris implementation of TCP/IP, listed from topmost layer (application) to lowest (physical network).
Table 4-2 TCP/IP Protocol Stack|
OSI Ref. Layer No. |
OSI Layer Equivalent |
TCP/IP Layer |
TCP/IP Protocol Examples |
|---|---|---|---|
|
5,6,7 |
Application, Session, Presentation |
NFS, NIS+, DNS, telnet, ftp, rlogin, rsh, rcp, RIP, RDISC, SNMP, and others |
|
|
4 |
Transport |
TCP, UDP |
|
|
3 |
Network |
IP, ARP, ICMP |
|
|
2 |
Data Link |
PPP, IEEE 802.2 |
|
|
1 |
Physical |
Ethernet (IEEE 802.3) Token Ring, RS-232, others |
The table shows the TCP/IP protocol layers, their OSI Model equivalents, and examples of the protocols available at each level of the TCP/IP protocol stack. Each host involved in a communication transaction runs its own implementation of the protocol stack.
Physical Network Layer
The physical network layer specifies the characteristics of the hardware to be used for the network. For example, it specifies the physical characteristics of the communications media. The physical layer of TCP/IP describes hardware standards such as IEEE 802.3, the specification for Ethernet network media, and RS-232, the specification for standard pin connectors.
Data-Link Layer
The data-link layer identifies the network protocol type of the packet, in this case TCP/IP. It also provides error control and "framing." Examples of data-link layer protocols are Ethernet IEEE 802.2 framing and Point-to-Point Protocol (PPP) framing.
Internet Layer
This layer, also known as the network layer, accepts and delivers packets for the network. It includes the powerful Internet protocol (IP), the Address Resolution Protocol (ARP) protocol, and the Internet Control Message Protocol (ICMP) protocol.
IP Protocol
The IP protocol and its associated routing protocols are possibly the most significant of the entire TCP/IP suite. IP is responsible for:
-
IP addressing - The IP addressing conventions are part of the IP protocol. (Chapter 5, Planning Your TCP/IP Network describes IPv4 addressing in detail and Chapter 14, Overview of IPv6 describes IPv6 addressing in detail.)
-
Host-to-host communications - IP determines the path a packet must take, based on the receiving host's IP address.
-
Packet formatting - IP assembles packets into units known as IP datagrams. Datagrams are fully described in "Internet Layer".
-
Fragmentation - If a packet is too large for transmission over the network media, IP on the sending host breaks the packet into smaller fragments. IP on the receiving host then reconstructs the fragments into the original packet.
Previous releases of the Solaris operating environment implemented version 4 of the Internet Protocol, which is written IPv4. However, because of the rapid growth of the Internet, it was necessary to create a new Internet Protocol with improved capabilities, such as increased address space. This new version, known as version 6, is written IPv6. The Solaris operating environment supports both versions, which are described in this book. To avoid confusion when addressing the Internet Protocol, the following convention is used:
-
When the term IP is used in a description, the description applies to both IPv4 and IPv6.
-
When the term IPv4 is used in a description, the description applies only to IPv4.
-
When the term IPv6 is used in a description, the description applies only to IPv6.
ARP Protocol
The Address Resolution Protocol (ARP) conceptually exists between the data link and Internet layers. ARP assists IP in directing datagrams to the appropriate receiving host by mapping Ethernet addresses (48 bits long) to known IP addresses (32 bits long).
ICMP Protocol
Internet Control Message Protocol (ICMP) is the protocol responsible for detecting network error conditions and reporting on them. ICMP reports on:
-
Dropped packets (when packets are arriving too fast to be processed)
-
Connectivity failure (when a destination host can't be reached)
-
Redirection (which tells a sending host to use another router)
The "ping Command" contains more information on the operating system commands that use ICMP for error detection.
Transport Layer
The TCP/IP transport layer protocols ensure that packets arrive in sequence and without error, by swapping acknowledgments of data reception, and retransmitting lost packets. This type of communication is known as "end-to-end." Transport layer protocols at this level are Transmission Control Protocol (TCP) and User Datagram Protocol (UDP).
TCP Protocol
TCP enables applications to communicate with each other as though connected by a physical circuit. TCP sends data in a form that appears to be transmitted in a character-by-character fashion, rather than as discreet packets. This transmission consists of a starting point, which opens the connection, the entire transmission in byte order, and an ending point, which closes the connection.
TCP attaches a header onto the transmitted data. This header contains a large number of parameters that help processes on the sending machine connect to peer processes on the receiving machine.
TCP confirms that a packet has reached its destination by establishing an end-to-end connection between sending and receiving hosts. TCP is therefore considered a "reliable, connection-oriented" protocol.
UDP Protocol
UDP, the other transport layer protocol, provides datagram delivery service. It does not provide any means of verifying that connection was ever achieved between receiving and sending hosts. Because UDP eliminates the processes of establishing and verifying connections, applications that send small amounts of data use it rather than TCP.
Application Layer
The application layer defines standard Internet services and network applications that anyone can use. These services work with the transport layer to send and receive data. There are many applications layer protocols, some of which you probably already use. Some of the protocols include:
-
Standard TCP/IP services such as the ftp, tftp, and telnet commands
-
UNIX "r" commands, such as rlogin and rsh
-
Name services, such as NIS+ and Domain Name System (DNS)
-
File services, such as the NFS service
-
Simple Network Management Protocol (SNMP), which enables network management
Standard TCP/IP Services
-
FTP and Anonymous FTP - The File Transfer Protocol (FTP) transfers files to and from a remote network. The protocol includes the ftp command (local machine) and the in.ftpd daemon (remote machine). FTP enables a user to specify the name of the remote host and file transfer command options on the local host's command line. The in.ftpd daemon on the remote host then handles the requests from the local host. Unlike rcp, ftp works even when the remote computer does not run a UNIX-based operating system. A user must log in to the remote computer to make an ftp connection unless it has been set up to allow anonymous FTP.
You can now obtain a wealth of materials from anonymous FTP servers connected to the Internet. These servers are set up by universities and other institutions to make certain software, research papers, and other information available to the public domain. When you log in to this type of server, you use the login name anonymous, hence the term "anonymous FTP servers."
Using anonymous FTP and setting up anonymous FTP servers is outside the scope of this manual. However, many trade books, such as The Whole Internet User's Guide & Catalog, discuss anonymous FTP in detail. Instructions for using FTP to reach standard machines are in System Administration Guide, Volume 1. The ftp(1) man page describes all ftp command options, including those invoked through the command interpreter. The ftpd(1M) man page describes the services provided by the daemon in.ftpd.
-
Telnet - The Telnet protocol enables terminals and terminal-oriented processes to communicate on a network running TCP/IP. It is implemented as the program telnet (on local machines) and the daemon in.telnet (on remote machines). Telnet provides a user interface through which two hosts can communicate on a character-by-character or line-by-line basis. The application includes a set of commands that are fully documented in the telnet(1) man page.
-
TFTP - The trivial file transfer protocol (tftp) provides functions similar to ftp, but it does not establish ftp's interactive connection. As a result, users cannot list the contents of a directory or change directories. This means that a user must know the full name of the file to be copied. The tftp(1) man page describes the tftp command set.
UNIX "r" Commands
The UNIX "r" commands enable users to issue commands on their local machines that are actually carried out on the remote host that they specify. These commands include
-
rcp
-
rlogin
-
rsh
Instructions for using these commands are in rcp(1), rlogin(1), and rsh(1) man pages.
Name Services
Two name services are available from the Solaris implementation of TCP/IP: NIS+ and DNS.
-
NIS+ - NIS+ provides centralized control over network administration services, such as mapping host names to IP and Ethernet addresses, verifying passwords, and so on. See Solaris Naming Administration Guide for complete details.
-
Domain Name System - The Domain Name System (DNS) provides host names to the IP address service. It also serves as a database for mail administration. For a complete description of this service, see Solaris Naming Administration Guide. See also the in.named(1M) man page.
File Services
The NFS application layer protocol provides file services for the Solaris operating environment. You can find complete information about the NFS service in Chapter 29, Solaris NFS Environment.
Network Administration
The Simple Network Management Protocol (SNMP) enables you to view the layout of your network, view status of key machines, and obtain complex network statistics from graphical user interface based software. Many companies offer network management packages that implement SNMP; SunNet ManagerTM software is an example.
Routing Protocols
The Routing Information Protocol (RIP) and the Router Discovery Protocol (RDISC) are two routing protocols for TCP/IP networks. They are described in "Routing Protocols".
How the TCP/IP Protocols Handle Data Communications
When a user issues a command that uses a TCP/IP application layer protocol, a chain of events is set in motion. The user's command or message passes through the TCP/IP protocol stack on the local machine, and then across the network media to the protocols on the recipient. The protocols at each layer on the sending host add information to the original data.
As the user's command makes its way through the protocol stack, protocols on each layer of the sending host also interact with their peers on the receiving host. The following figure shows this interaction.
Data Encapsulation and the TCP/IP Protocol Stack
The packet is the basic unit of information transferred across a network, consisting, at a minimum, of a header with the sending and receiving hosts' addresses, and a body with the data to be transferred. As the packet travels through the TCP/IP protocol stack, the protocols at each layer either add or remove fields from the basic header. When a protocol on the sending host adds data to the packet header, the process is called data encapsulation. Moreover, each layer has a different term for the altered packet, as shown in the following figure.
Figure 4-1 How a Packet Travels Through the TCP/IP Stack
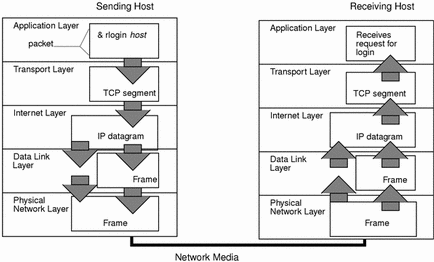
This section summarizes the life cycle of a packet from the time the user issues a command or sends a message to the time it is received by the appropriate application on the receiving host.
Application Layer--User Initiates Communication
The packet's history begins when a user on one host sends a message or issues a command that must access a remote host. The application protocol associated with the command or message formats the packet so that it can be handled by the appropriate transport layer protocol, TCP or UDP.
Suppose the user issues an rlogin command to log in to the remote host, as shown in Figure 4-1. The rlogin command uses the TCP transport layer protocol. TCP expects to receive data in the form of a stream of bytes containing the information in the command. Therefore, rlogin sends this data as a TCP stream.
Not all application layer protocols use TCP, however. Suppose a user wants to mount a file system on a remote host, thus initiating the NIS+ application layer protocol. NIS+ uses the UDP transport layer protocol. Therefore, the packet containing the command must be formatted in a manner that UDP expects. This type of packet is referred to as a message.
Transport Layer--Data Encapsulation Begins
When the data arrives at the transport layer, the protocols at the layer start the process of data encapsulation. The end result depends on whether TCP or UDP has handled the information.
TCP Segmentation
TCP is often called a "connection-oriented" protocol because it ensures the successful delivery of data to the receiving host. Figure 4-1 shows how the TCP protocol receives the stream from the rlogin command. TCP divides the data received from the application layer into segments and attaches a header to each segment.
Segment headers contain sender and recipient ports, segment ordering information, and a data field known as a checksum. The TCP protocols on both hosts use the checksum data to determine whether data has transferred without error.
Establishing a TCP Connection
TCP uses segments to determine whether the receiving host is ready to receive the data. When the sending TCP wants to establish connections, it sends a segment called a SYN to the peer TCP protocol running on the receiving host. The receiving TCP returns a segment called an ACK to acknowledge the successful receipt of the segment. The sending TCP sends another ACK segment, then proceeds to send the data. This exchange of control information is referred to as a three-way handshake.
UDP Packets
UDP is a "connectionless" protocol. Unlike TCP, it does not check to make sure that data arrived at the receiving host. Instead, UDP takes the message received from the application layer and formats it into UDP packets. UDP attaches a header to each packet, which contains the sending and receiving host ports, a field with the length of the packet, and a checksum.
The sending UDP process attempts to send the packet to its peer UDP process on the receiving host. The application layer determines whether the receiving UDP process acknowledges that the packet was received. UDP requires no notification of receipt. UDP does not use the three-way handshake.
Internet Layer
As shown in Figure 4-1, both TCP and UDP pass their segments and packets down to the Internet layer, where they are handled by the IP protocol. IP prepares them for delivery by formatting them into units called IP datagrams. IP then determines the IP addresses for the datagrams, so they can be delivered effectively to the receiving host.
IP Datagrams
IP attaches an IP header to the segment or packet's header in addition to the information added by TCP or UDP. Information in the IP header includes the IP addresses of the sending and receiving hosts, datagram length, and datagram sequence order. This information is provided in case the datagram exceeds the allowable byte size for network packets and must be fragmented.
Data-Link Layer--Framing Takes Place
Data-link layer protocols, such as PPP, format the IP datagram into a frame. They attach a third header and a footer to "frame" the datagram. The frame header includes a cyclical redundancy check (CRC) field that checks for errors as the frame travels over the network media. Then the data-link layer passes the frame to the physical layer.
Physical Network Layer--Preparing the Frame for Transmission
The physical network layer on the sending host receives the frames and converts the IP addresses into the hardware addresses appropriate to the network media. The physical network layer then sends the frame out over the network media.
How the Receiving Host Handles the Packet
When the packet arrives on the receiving host, it travels through the TCP/IP protocol stack in the reverse order from that which it took on the sender. Figure 4-1 illustrates this path. Moreover, each protocol on the receiving host strips off header information attached to the packet by its peer on the sending host. Here is what happens:
-
Physical Network Layer receives the packet in its frame form. It computes the CRC of the packet, then sends the frame to the data link layer.
-
Data-Link Layer verifies that the CRC for the frame is correct and strips off the frame header and CRC. Finally, the data link protocol sends the frame to the Internet layer.
-
Internet Layer reads information in the header to identify the transmission and determine if it is a fragment. If the transmission was fragmented, IP reassembles the fragments into the original datagram. It then strips off the IP header and passes the datagram on to transport layer protocols.
-
Transport Layer (TCP and UDP) reads the header to determine which application layer protocol must receive the data. Then TCP or UDP strips off its related header and sends the message or stream up to the receiving application.
-
Application Layer receives the message and performs the operation requested by the sending host.
TCP/IP Internal Trace Support
TCP/IP provides internal trace support by logging TCP communication when a connection is terminated by an RST packet. When an RST packet is transmitted or received, information on as many as 10 packets, which were transmitted or received immediately before on that connection, is logged with the connection information.
Finding Out More About TCP/IP and the Internet
A great deal of information about TCP/IP and the Internet has been published. If you require specific information that is not covered in this text, you can probably find what you need in the sources cited below.
Computer Trade Books
Many books about TCP/IP and the Internet are available from your local library or computer bookstore. Three highly recommended books are:
-
Craig Hunt. TCP/IP Network Administration - This book contains some theory and much practical information for managing a heterogeneous TCP/IP network.
-
W. Richard Stevens. TCP/IP Illustrated, Volume I - This book is an in-depth explanation of the TCP/IP protocols. It is ideal for network administrators requiring a technical background in TCP/IP and for network programmers.
-
Ed Krol. The Whole Internet User's Guide & Catalog - This book is ideal for anyone interested in using the many tools available for retrieving information over the Internet.
RFCs and FYIs
Since 1969, developers working on the Internet protocol suite have described their protocols and related subjects in documents known as Requests for Comments (RFCs). Many RFCs are specifications for particular TCP/IP protocols and describe standards with which software implementing the protocols must comply. Other RFCs discuss the Internet, its topology, and its governing bodies. Still other RFCs explain how to manage TCP/IP applications, such as DNS.
All RFCs must be approved by the Internet Architecture Board (IAB) before they are placed in the public domain. Typically, the information in RFCs is geared to developers and other highly technical readers, though this isn`t always the case.
In recent years, for your information (FYI) documents have appeared as a subset of the RFCs. The FYIs contain information that does not deal with Internet standards; rather, they contain Internet information of a more general nature. For example, FYI documents include a bibliography listing introductory TCP/IP books and papers, an exhaustive compendium of Internet-related software tools, and a glossary of Internet and general networking terms.
You'll find references to relevant RFCs throughout this guide and other books in the Solaris System Administrator set.
The InterNIC Directory and Database Service maintains the repository of RFCs. If you have a connection to the Internet, you can retrieve online RFCs as follows:
-
Through ftp, by sending your requests to the InterNIC directory and database server ds.internic.net. Your request should have the format:
rfc/rfc.rfcnum.txt or rfc/rfc.rfcnum.ps
where rfcnum represents the number of the RFC you want. For example, if you wanted to retrieve RFC 1540 in PostScriptTM format, you would request rfc/rfc.1540.ps.
-
Through electronic mail, by emailing mailserv@ds.internic.net. This is an automatic server that expects the body of your request message to have the format:
document-by-name rfcrfcnum or document-by-name rfcrfcnum.ps
-
Through a World Wide Web browser, by specifying the URL http://ds.internic.net/ds/dspg1intdoc.html. The home page is http://ds.internic.net
If you need an online index of RFCs, send electronic mail to ds.internic.net with a message containing the request document-by-name rfc-index.
Note -
The InterNIC information above is current as of this writing. However, the Internet is expanding at a fast pace, and the addresses listed might no longer be current by the time you read this manual.
- © 2010, Oracle Corporation and/or its affiliates
