Overview
These are the basic steps in using the GSS-API:
-
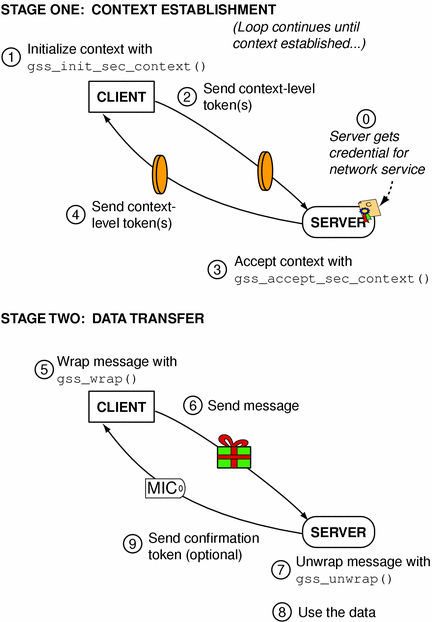
Each application, sender and recipient, acquires credentials explicitly, if credentials have not been acquired automatically.
-
The sender initiates a security context and the recipient accepts it.
-
The sender applies security protection to the message (data) it wants to transmit. This means that it either encrypts the message or stamps it with an identification tag. The sender transmits the protected message.
(The sender can choose not to apply either security protection, in which case the message has only the default GSS-API security service associated with it. That is authentication, in which the recipient knows that the sender is who it claims to be.)
-
The recipient decrypts the message (if needed) and verifies it (if appropriate).
-
(Optional) The recipient returns an identification tag to the sender for confirmation.
-
Both applications destroy the shared security context. If necessary, they can also deallocate any “leftover” GSS-API data.
Applications that use the GSS-API should include the file gssapi.h.
A general schema of this process is presented in Figure 1–6, which shows one way that the GSS-API can be used; other scenarios are possible.
Figure 1–6 Using the GSS-API: An Overview
- © 2010, Oracle Corporation and/or its affiliates
