Redzone: 0xfeedface
The pattern 0xfeedface appears frequently in the buffer above. This pattern is known as the "redzone" indicator. It enables the allocator (and a programmer debugging a problem) to determine if the boundaries of a buffer have been violated by "buggy" code. Following the redzone is some additional information. The contents of that data depends upon other factors (see "Memory Allocation Logging"). The redzone and its suffix are collectively called the buftag region. Figure 6-1 summarizes this information.
Figure 6-1 The Redzone
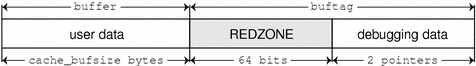
The buftag is appended to each buffer in a cache when any of the KMF_AUDIT, KMF_DEADBEEF, KMF_REDZONE, or KMF_CONTENTS flags are set in that buffer's cache. The contents of the buftag depend on whether KMF_AUDIT is set.
Decomposing the memory region presented above into distinct buffers is now simple:
0x70a9add8: deadbeef deadbeef \ 0x70a9ade0: deadbeef deadbeef +- User Data (free) 0x70a9ade8: deadbeef deadbeef / 0x70a9adf0: feedface feedface -- REDZONE 0x70a9adf8: 70ae3260 8440c68e -- Debugging Data 0x70a9ae00: 5 4ef83 \ 0x70a9ae08: 0 0 +- User Data (allocated) 0x70a9ae10: 1 bbddcafe / 0x70a9ae18: feedface 4fffed -- REDZONE 0x70a9ae20: 70ae3200 d1befaed -- Debugging Data 0x70a9ae28: deadbeef deadbeef \ 0x70a9ae30: deadbeef deadbeef +- User Data (free) 0x70a9ae38: deadbeef deadbeef / 0x70a9ae40: feedface feedface -- REDZONE 0x70a9ae48: 70ae31a0 8440c54e -- Debugging Data
In the free buffers at 0x70a9add8 and 0x70a9ae28, the redzone is filled with 0xfeedfacefeedface. This a convenient way of determining that a buffer is free.
In the allocated buffer beginning at 0x70a9ae00, the situation is different. Recall from "Allocator Basics" that there are two allocation types:
1) The client requested memory using kmem_cache_alloc(), in which case the size of the requested buffer is equal to the bufsize of the cache.
2) The client requested memory using kmem_alloc(9F), in which case the size of the requested buffer is less than or equal to the bufsize of the cache. For example, a request for 20 bytes will be fulfilled from the kmem_alloc_24 cache. The allocator enforces the buffer boundary by placing a marker, the redzone byte, immediately following the client data:
0x70a9ae00: 5 4ef83 \ 0x70a9ae08: 0 0 +- User Data (allocated) 0x70a9ae10: 1 bbddcafe / 0x70a9ae18: feedface 4fffed -- REDZONE 0x70a9ae20: 70ae3200 d1befaed -- Debugging Data
0xfeedface at 0x70a9ae18 is followed by a 32-bit word containing what seems to be a random value. This number is actually an encoded representation of the size of the buffer. To decode this number and find the size of the allocated buffer, use the formula:
size = redzone_value / (UINT_MAX / KMEM_MAXBUF)
The value of KMEM_MAXBUF is 16384, and the value of UINT_MAX is 4294967295. So, in this example,
size = 0x4fffed / (4294967295 / 16384) = 20 bytes.
This indicates that the buffer requested was of size 20 bytes. The allocator performs this decoding operation and finds that the redzone byte should be at offset 20. The redzone byte is the hex pattern 0xbb, which is present at 0x729084e4 (0x729084d0 + 0t20) as expected.
Figure 6-2 Sample kmem_alloc(9F) Buffer
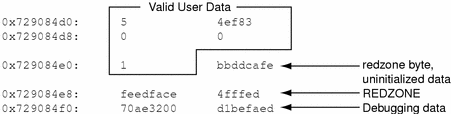
Figure 6-3 shows the general form of this memory layout.
Figure 6-3 Redzone Byte
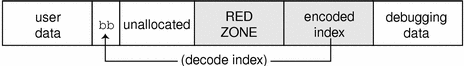
If the allocation size is the same as the bufsize of the cache, the redzone byte overwrites the first byte of the redzone itself, as shown in Figure 6-4.
Figure 6-4 Redzone Byte at the Beginning of the Redzone

This overwriting results in the first 32-bit word of the redzone being 0xbbedface, or 0xfeedfabb depending on the endianness of the hardware on which the system is running.
Note -
Why is the allocation size encoded this way? To encode the size, the allocator uses the formula ((UINT_MAX / KMEM_MAXBUF) * size + 1). When the size decode occurs, the integer division discards the remainder of '+1'. However, the addition of 1 is valuable because the allocator can check whether the size is valid by testing whether (size % (UINT_MAX / KMEM_MAXBUF) == 1). In this way, the allocator defends against corruption of the redzone byte index.
- © 2010, Oracle Corporation and/or its affiliates
