Architectural Changes In This Release
Access Manager includes new components that enable you to implement authentication and authorization solutions without having to make changes in your existing user directory information tree.
Access Control Realms
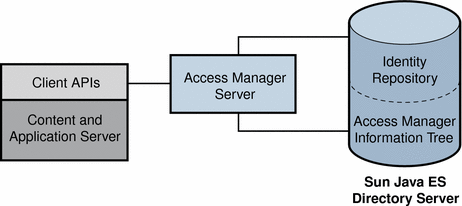
In Access Manager an access control realm is a group of authentication properties and authorization policies you can associate with a user or group of users. Realm data is stored in a proprietary information tree that Access Manager creates within a data store you specify. The Access Manager framework aggregates policies and properties contained in each realm within the Access Manager information tree.
By default, Access Manager automatically inserts the Access Manager information tree as a special branch in Sun Java Enterprise System Directory Server, apart from the user data.
Figure 1–4 Default Configuration for Access Manager Information Tree
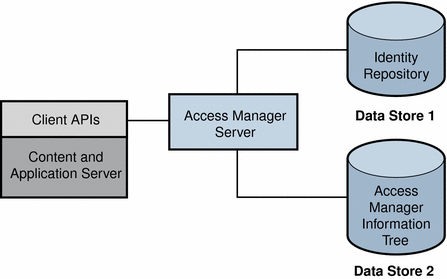
You can use access control realms while using any user database. The following figure illustrates the Access Manager information tree configured in a separate data store from the identity repository.
Figure 1–5 Access Manager Information Tree Configured in Second Data Store
When a user logs into an application, Access Manager plug-ins retrieve all user information and access information that Access Manager needs to form a temporary, virtual user identity. Authentication service and Policy service use the virtual user identity to authenticate the user and to enforce authorization policies. The virtual user identity is destroyed when the user’s session ends.
Identity Repository Framework
An identity repository is a database where you can store user attributes and user configuration data. Previous versions of Access Manager relied on Sun Java System Directory Server as the only supported identity repository and the only supported software for creating, managing, and storing user data.
Access Manager provides an identity repository plug-in that connects to an identity repository framework. This new model enables you to view and retrieve Access Manager user information without having to make changes in your existing user database. The Access Manager framework integrates data from the identity repository plug-in with data from other Access Manager plug-ins to form a virtual identity for each user. Access Manager can then use the universal identity in authentication and authorization processes among more than one identity repository. The virtual user identity is destroyed when the user’s session ends.
You can configure the Identity Repository Management Service per realm to use its own list of Identity Repositories.
Using realm-based configuration, you can specify a single Identity Repository that will store service configurations for both users and roles. The Identity Repository Service provides a list of Identity Repositories that can provide user attributes to Policy, SAML , and Liberty services. The Identity Repository Services pluggable interface combines attributes obtained from different repositories. Identity Repository plug-ins provide interfaces to create, read , edit, and delete objects such as Realm, Role, Group, User, and Agent.
The default identity repository plug-in is designed to work with Sun Java Directory Server which is based on LDAP. In previous Access Manager versions, the functionality of this default plug-in was provided by the AM SDK component. In Access Manager 7.0, the AM SDK functionality still exists, but now in plug-in form.
Realm Mode and Legacy Mode
When you install Access Manager, you are asked to choose either Realm Mode or Legacy Mode.
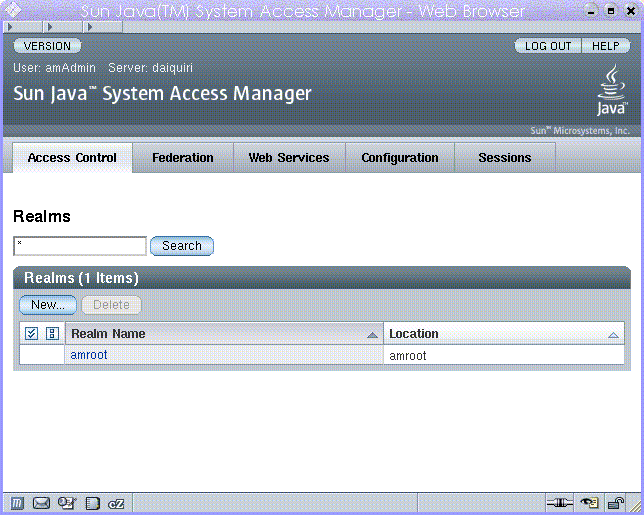
Realm mode is new in Access Manager 7.0, and is based on the Access Manager information tree and Identity Repository Management Service described in the previous sections. Realm mode is appropriate in most new Access Manager deployments where you want to keep identity repositories independent of access management, or where you cannot maintain user data within the required object classes of Sun Java System Directory Server.
If you choose Realm Mode at installation, then after installation your identity repositories can exist in any of the following configurations:
-
In the same Directory Server instance and the same suffix as the Access Manager information tree.
-
In the same Directory Server instance but in a different suffix as the Access Manager information tree.
-
In a different directory server instance from the Access Manager information tree.
Figure 1–6 Realm Mode User Interface
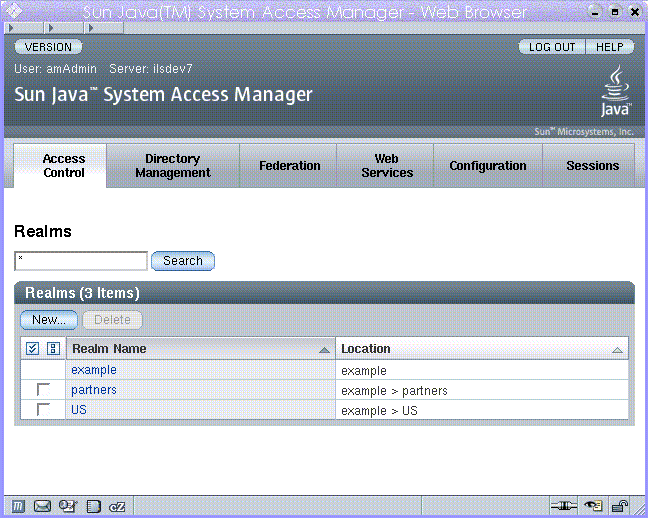
Legacy Mode is based on the Access Manager 6.3 architecture. This legacy Access Manager architecture uses the LDAP directory information tree (DIT) that comes with Sun Java System Directory Server. In Legacy Mode, both user information and access control information are stored in LDAP organizations. When you choose Legacy Mode, an LDAP organization is the equivalent of an access control realm. Realm information is integrated within LDAP organizations.
Legacy Mode is appropriate in deployments where you want to use Access Manager user management. Legacy Mode is typically used in deployments where Access Manager is built upon Sun Java System Portal Server or other Sun Java System communication products that require the use of Sun Java System Directory Server as the central identity repository.
If you choose Legacy Mode during installation, then after installation the top-level ream resides in the same Directory Server branch as the Access Manager information tree, and user information is intermingled with access information.
Figure 1–7 Legacy Mode User Interface
The following table compares realm mode and legacy mode.
Table 1–4 Comparison of Realm and Legacy Modes|
Realm Mode |
Legacy Mode |
|
|---|---|---|
|
Supports all new Access Manager 7 2005Q4 features. |
Yes |
Yes |
|
Supports identity repositories in Sun Java System Directory Server and in other data stores. |
Yes |
Yes |
|
Supports Access Manager 6 user management features. |
No |
Yes |
|
Can coexist with Access Manager 6 2005Q1 in multiple-server installations. |
No |
Yes |
|
Before installation, identity repository can exist in Sun Java Directory Server . |
Yes |
Yes |
|
Before installation, identity repository can exist in an LDAP version 3 compliant directory server. |
Yes |
No |
For more information about realm and legacy modes, see the Sun Java System Access Manager 7 2005Q4 Release Notes.
Distributed Authentication User Interface Component
The Distributed Authentication user interface enables a policy agent or an application that is deployed in a non-secured area to communicate with the Access Manager Authentication Service that is installed in a secured area of the deployment. Typically, the non-secured policy agent or application is separated from Access Manager by two firewalls. In such deployments, policy agents and applications are not usually allowed to communicate across two firewalls.
Figure 1–8 Distributed Authentication
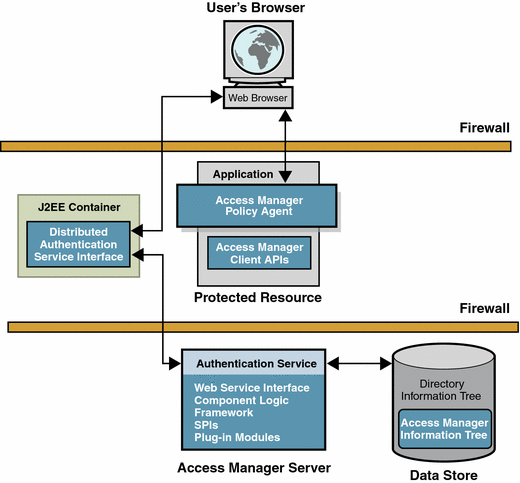
You can install the distributed authentication user interface on a J2EE web container within the non—secure layer of an Access Manager deployment. The web browser communicates an HTTP request to the remote authentication user interface, which in turn presents a login page to the user. The web browser sends user login information through a firewall to the remote authentication user interface. The remote authentication user interface communicates through the second firewall to the Access Manager Server. For detailed illustration and process flow, see User Authentication. For detailed installation and configuration instructions, see the Sun Java System Access Manager 7 2005Q4 Administration Guide.
Delegation Plug-In
The Delegation plug-in works together with the Identity Repository plug-in to determine a network administrator’s scope of privileges. Default administrator roles are defined in the Identity Repository plug-in. The Delegation plug-in forms rules that describe the scope of privileges for each network administrator, and also specifies the roles to which the rules apply. The following is a list of roles defined in the Identity Repository, and the default rule the Delegation plug-in applies to each role.
Table 1–5 Access Manager Roles and Scope of Privileges|
Identity Repository Role |
Delegation Rule |
|---|---|
|
Can access all data in all realms of the Access Control information tree. |
|
|
Can access all data within a specific realm of the Access Control information tree. |
|
|
Can access all policies in all realms of the Access Control information tree. |
|
|
Can access policies only within the specific realm of the Access Control information tree. |
Authentication service and Policy service use the aggregated data to perform authentication and authorization processes. The Delegation plug-in code is not public in Access Manager.
Service Configuration Plug-Ins
The Service Configuration plug-in stores and manages data required by other Access Manager plug-ins. In previous versions of Access Manager, the functionality provided by the Service Configuration plug-in was known as the Service Management Service (SMS).
- © 2010, Oracle Corporation and/or its affiliates
