Java Authentication Service Provider Interface for Containers
There are a number of organizations that work on web services security specifications, guidelines, and tools including the World Wide Web Consortium (W3C), the Organization for Advancement of Structured Information Standards (OASIS), the Liberty Alliance Project and the Java Community Process (JCP). The JCP primarily guides the development and approval of Java technical specifications, one of which is the Java Specification Request (JSR) 196. JSR 196 is a draft of the Java Authentication Service Provider Interface for Containers. It defines a standard service provider interface (SPI) with which a message level authentication agent can be developed for Java EE containers on either the client side or the server side. These agents may establish the authenticated identities used by the containers allowing:
-
A server side agent to verify security tokens or signatures on incoming requests and extract principal data or assertions before adding them to the client security context.
-
A client side agent to add security tokens to outgoing requests, sign messages, and interact with the trusted authority to locate targeted web service providers.
Note –
The JSR 196 draft specifications are available at http://www.jcp.org/en/jsr/detail?id=196.
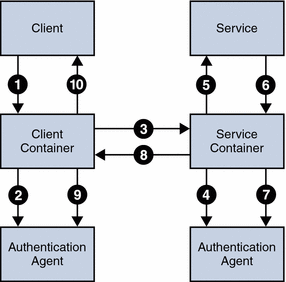
A typical interaction between a WSC and a WSP begins with a request from the WSC. The container to which the WSP is deployed receives the request and dispatches it to the correct web service to perform the requested operation. When the web service completes the operation, it creates a response that is returned back to the client. The following illustration illustrates this process in more detail with the steps provided below it. This process illustrates a scenario when both client and service web containers employ the Java Authentication SPI.
-
The client browser's attempt to invoke a web service is intercepted by the client's web container.
-
The deployed authentication agent on the client's web container is invoked to secure the request (based on the security policy of the web service being invoked).
-
The client's web container sends the secured request message to the web service.
-
The web service's web container receives the secured request message and it's deployed authentication agent is invoked to validate the request and obtain the identity of the caller.
-
Assuming successful authentication, the web service's web container invokes the requested web service.
-
This action (the invocation of the web service) is returned to the web service's web container as a response.
-
The deployed authentication agent on the web service's web container is invoked to secure the response message.
-
The web service's web container sends the secured response message to the client.
-
The deployed authentication agent on the client's web container is invoked to validate the secured response message.
-
The invocation of the web service is returned to the client browser.
The JSR–196 SPI is structured so that the security processes can be delegated to an authentication agent at any of four interaction points in this scenario. The four points represent the methods of the corresponding ClientAuthModule and ServerAuthModule interfaces defined by the SPI and include:
-
Securing a request on the client side
-
Validating a request on the provider side
-
Securing a response on the provider side
-
Validating a response on the client side
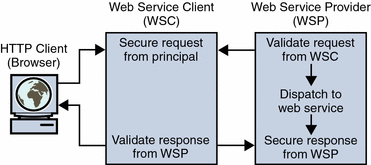
Thus, when a WSC and WSP are both deployed in a Java EE web container protected by a JSR–196 authentication agent, the initial request from the WSC is intercepted by the authentication agent on the client side. The client side agent queries a trusted authority (for example, the Discovery Service in Access Manager) to retrieve the necessary authorization credentials and secure them to the request. The request is then passed to the WSP. The authentication agent on the provider side receives the request to validate the authorization credentials. If validation is successful, the request is exposed to the web service and a response is created using the sender's credentials and the application specific request. The response is then intercepted by the authentication agent on the provider side to secure it and return it to the WSC. Upon receiving the response, the authentication agent on the client side validates it and dispatches it to the client application. This is illustrated in the following graphic.
- © 2010, Oracle Corporation and/or its affiliates
