6.3 Configuring the Access Manager Load Balancer
The Access Manager servers are fronted by one load balancer (Load Balancer 3). Users internal to the company will access the servers through the non-secure port 7070. Users external to the company will access the servers through the secure port 9443. Additionally, configuring two load balancer instances enables you to customize internal-facing and external-facing login pages. Users external to your company first access the Distributed Authentication User Interface which, in turn, routes the request to the secure port 9443. The following figure illustrates this architecture.
Figure 6–1 Load Balancer 3 Fronts Two Access Manager Servers
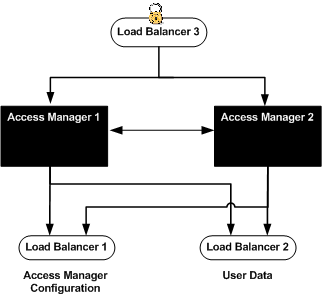
Load Balancer 3 sends the user and agent requests to the server where the session originated. Secure Sockets Layer (SSL) is terminated before a request is forwarded to the Access Manager servers to allow the load balancer to inspect the traffic for proper routing. Load Balancer 3 is capable of the following types of load balancing:
|
Cookie-based |
The load balancer makes decisions based on client's cookies. The load balancer looks at the request and detects the presence of a cookie by a specific name. If the cookie is detected in the request, the load balancer routes the request to the specific server to which the cookie has been assigned. If the cookie is not detected in the request, the load balancer balances client requests among the available servers. |
|
IP-based |
This is similar to cookie-based load balancing, but the decision is based on the IP address of the client. The load balancer sends all requests from a specific IP address to the same server. |
|
TCP |
The load balancer mainstreams session affinity. This means that all requests related to a TCP session, are forwarded to the same server. In this deployment example, Load Balancer 3 forwards all requests from a single client to exactly the same server. When the session is started and maintained by one client, session affinity is guaranteed. This type of load-balancing is applicable to the TCP-based protocols. |
Use the following list of procedures as a checklist for configuring the Access Manager load balancer. The first procedure tests the Directory Server load balancing and system failover configurations.
-
To Request an Secure Sockets Layer Certificate for the Access Manager Load Balancer
-
To Import a Certificate Authority Root Certificate on the Access Manager Load Balancer
-
To Install an SSL Certificate on the Access Manager Load Balancer
-
To Create an SSL Proxy for SSL Termination on the Access Manager Load Balancer
 To Verify Successful Directory Server Load
Balancing and System Failover for Access Manager 1 and Access Manager 2
To Verify Successful Directory Server Load
Balancing and System Failover for Access Manager 1 and Access Manager 2
Perform the following steps to confirm that Access Manager directory requests are directed to only one instance of Directory Server, and that system failover and recovery work properly. The steps in this procedure are specific to Access Manager 1. Substitute http://AccessManager-2.example.com:1080/amserver/console where appropriate to perform this procedure for Access Manager 2.
-
Confirm that the load balancer is properly configured for simple persistence.
-
As a root user, log in to the DirectoryServer–1 and the DirectoryServer–2 host machines.
-
On each server, use the tail command to watch the Directory Server access log.
# cd /var/opt/mps/am-config/logs # tail-f logs/access
-
Access http://AccessManager-1.example.com:1080/amserver/console from a web browser and log in to the Access Manager 1 console as the default administrator.
- Username
-
amadmin
- Password
-
4m4dmin1
-
Navigate inside the Access Manager 1 console while paying attention to the Directory Server access logs.
You should see all directory accesses are directed to one Directory Server instance only, excluding the health check probing from the load balancer device. The navigation should not have any errors.
-
Log out of the Access Manager 1 console and close the browser when successful.
-
-
Confirm that Directory Server failover is working properly.
-
Stop Directory Server 1 instance.
# cd /var/opt/mps/serverroot/ds6/bin # ./dsadm stop /var/opt/mps/am-config Server stopped
-
Access http://AccessManager-1.example.com:1080/amserver/console from a web browser and log in to the Access Manager 1 console as the default administrator.
- Username
-
amadmin
- Password
-
4m4dmin1
-
Navigate inside the Access Manager 1 console while paying attention to the Directory Server access logs.
You should see all directory accesses are directed to Directory Server 2. The navigation should not have any errors.
-
Log out and close the browser when successful.
-
Start the Directory Server 1 instance.
# cd /var/opt/mps/serverroot/ds6/bin # ./dsadm start /var/opt/mps/am-config Server started
-
Stop Directory Server 2 instance.
# cd /var/opt/mps/serverroot/ds6/bin # ./dsadm stop /var/opt/mps/am-config Server stopped
-
Access http://AccessManager-1.example.com:1080/amserver/console from a web browser and log in as the administrator, if necessary.
- Username
-
amadmin
- Password
-
4m4dmin1
-
Navigate inside the Access Manager 1 console while paying attention to the Directory Server access logs.
You should see all directory accesses are directed to Directory Server 1. The navigation should not have any errors.
-
Log out and close the browser when successful.
-
Start the Directory Server 2 instance.
# cd /var/opt/mps/serverroot/ds6/bin # ./dsadm start /var/opt/mps/am-config Server started
-
-
Confirm that both Directory Servers are running and log out of both host machines.
-
Repeat this procedure for Access Manager 2.
Substitute http://AccessManager-2.example.com:1080/amserver/console where applicable and perform these steps again.
 To Configure the Access Manager Load Balancer
To Configure the Access Manager Load Balancer
Before You Begin
-
This procedure assumes that you have already installed a load balancer.
-
The load balancer hardware and software used for this deployment is BIG-IP® manufactured by F5 Networks. If you are using different load balancer software, see the documentation that comes with that product for detailed settings information.
-
Contact your network administrator to obtain two available virtual IP addresses.
-
Know the IP address of the load balancer hardware, the URL for the load balancer login page, and a username and password for logging in to the load balancer application.
-
Get the IP addresses for Access Manager 1 and Access Manager 2 by running the following command on each host machine:
# ifconfig -a
-
Access https://is-f5.example.com, the BIG-IP load balancer login page, in a web browser.
-
Log in using the following information:
- User name:
-
username
- Password:
-
password
-
Click Configure your BIG-IP (R) using the Configuration Utility.
-
Create a Pool.
A pool contains all the backend server instances.
-
In the left pane, click Pools.
-
On the Pools tab, click Add.
-
In the Add Pool dialog, provide the following information.
- Pool Name
-
AccessManager-Pool
- Load Balancing Method
-
Round Robin
- Resources
-
Add the IP addresses and port numbers for the Access Manager servers: AccessManager-1:1080 and AccessManager-2:1080.
-
Click Done.
-
-
Add a Virtual Server for the non-secure port 7070 on the Access Manager Load Balancer 3.
This step defines instances of the load balancer.
Note –If you encounter JavaScriptTM errors or otherwise cannot proceed to create a virtual server, try using Internet Explorer.
-
In the left frame, click Virtual Servers.
-
On the Virtual Servers tab, click Add.
-
In the Add a Virtual Server dialog box, provide the following information:
- Address
-
Enter the IP address for LoadBalancer-3.example.com
- Service
-
7070
- Pool
-
AccessManager-Pool
-
Continue to click Next until you reach the Pool Selection dialog box.
-
In the Pool Selection dialog box, assign the AccessManager-Pool Pool.
-
Click Done.
-
-
Add Monitors.
Access Manager comes with a JSP file named isAlive.jsp that can be contacted to determine if the server is down. In the following steps, you create a custom monitor that periodically accesses the JSP. If a success response can be obtained, it means not only that Access Manager is responding to TCP connection request, but also that free threads exist to process the request.
-
Click the Monitors tab
-
Click Add and provide the following information.
- Name:
-
AccessManager-http
- Inherits From:
-
Choose http.
-
Click Next on the Configure Basic Properties page.
-
Enter the following value in the Send String field of the Configure ECV HTTP Monitor dialog.
GET /amserver/isAlive.jsp
-
On the Destination Address and Service (Alias) page, click Done.
The monitor you entered is now added to the list of monitors.
-
Click the Basic Associations tab.
-
Find the IP address for AccessManager-1:1080 and AccessManager-2:1080.
-
Mark the Add checkbox for AccessManager-1 and AccessManager-2.
-
At the top of the Node column, choose the monitor that you just added, AccessManager-http.
-
Click Apply.
-
-
Configure the load balancer for persistence.
-
In the left pane, click Pools.
-
Click the name of the pool you want to configure.
-
Click the Persistence tab.
-
Under Persistence Type, select Cookie Hash and set the following values.
In this type of persistence, the load balancer uses a portion of the cookie as a hash ID.
- Cookie Name:
-
amlbcookie
- Offset:
-
1
- Length:
-
1
-
Click Apply.
-
-
Log out of the load balancer console.
-
Verify that the Access Manager load balancer is configured properly.
-
As a root user, log in to the AccessManager–1 host machine.
-
Run tail to view the access log.
# cd /opt/SUNWwbsvr/https-AccessManager-1.example.com/logs # tail -f access
If you see frequent entries similar to the one below, the custom monitor is configured properly.
IP_address--[12/Oct/2006:13:10:20-0700] "GET /amserver/isAlive.jsp" 200 118
If you do not see “GET /amserver/isAlive.jsp”, you must troubleshoot the load balancer configuration.
-
As a root user, log in to the AccessManager–2 host machine.
-
Run tail to view the access log.
# cd /opt/SUNWwbsvr/https-AccessManager-2.example.com/logs # tail -f access
If you see frequent entries similar to the one below, the custom monitor is configured properly.
IP_address--[12/Oct/2006:13:10:20-0700] "GET /amserver/isAlive.jsp" 200 118
If you do not see “GET /amserver/isAlive.jsp”, you must troubleshoot the load balancer configuration.
-
Access http://LoadBalancer-3.example.com:7070/, the internal-facing load balancer, in a web browser.
 Caution –
Caution – Do not supply the amserver prefix.
If the browser displays the default Sun Java System Web Server document root page, it is configured properly.
-
Log out of both Access Manager host machines.
-
 To Request an Secure Sockets Layer Certificate
for the Access Manager Load Balancer
To Request an Secure Sockets Layer Certificate
for the Access Manager Load Balancer
Generate a request for a Secure Sockets Layer (SSL) certificate to send to a certificate authority.
-
Access https://is-f5.example.com, the BIG-IP load balancer login page, in a web browser.
-
Log in to the BIG-IP console using the following information.
- Username
-
username
- Password
-
password
-
Click Configure your BIG-IP (R) using the Configuration Utility.
-
In the left pane, click Proxies.
-
Click the Cert-Admin tab.
-
On the SSL Certificate Administration page, click Generate New Key Pair/Certificate Request.
-
In the Create Certificate Request page, provide the following information.
- Key Identifier:
-
LoadBalancer-3.example.com
- Organizational Unit Name:
-
Deployment
- Domain Name:
-
LoadBalancer-3.example.com
- Challenge Password:
-
password
- Retype Password:
-
password
-
Click Generate Key Pair/Certificate Request.
On the SSL Certificate Request page, the request is generated in the Certificate Request field.
-
Save the text contained in the Certificate Request field to a text file.
-
Log out of the console and close the browser.
-
Send the certificate request text you saved to the Certificate Authority of your choice.
A Certificate Authority (CA) is an entity that issues certified digital certificates; VeriSign, Thawte, Entrust, and GoDaddy are just a few. In this deployment, CA certificates were obtained from OpenSSL. Follow the instructions provided by your Certificate Authority to submit a certificate request.
 To Import a Certificate Authority Root Certificate
on the Access Manager Load Balancer
To Import a Certificate Authority Root Certificate
on the Access Manager Load Balancer
The CA root certificate proves that the particular CA (such as VeriSign or Entrust) did, in fact, issue a particular SSL certificate. You install the root certificate on Load Balancer 3 to ensure that a link between the Load Balancer 3 SSL certificate can be maintained with the issuing company. CA root certificates are publicly available.
Before You Begin
You should have a CA root certificate.
-
Access https://is-f5.example.com, the BIG-IP load balancer login page, in a web browser.
-
Log in with the following information.
- User name:
-
username
- Password:
-
password
-
In the BIG-IP load balancer console, click Proxies.
-
Click the Cert-Admin tab.
-
Click Import.
-
In the Import Type field, choose Certificate, and click Continue.
-
Click Browse in the Certificate File field on the Install SSL Certificate page.
-
In the Choose File dialog, choose Browser.
-
Navigate to the file that includes the root CA certificate and click Open.
-
In the Certificate Identifier field, enter OpenSSL_CA_cert.
-
Click Install Certificate.
-
On the Certificate OpenSSL_CA_Cert page, click Return to Certificate Administration.
The root certificate OpenSSL_CA_Cert is now included in the Certificate ID list.
 To Install an SSL Certificate on the Access
Manager Load Balancer
To Install an SSL Certificate on the Access
Manager Load Balancer
Before You Begin
This procedure assumes you have received an SSL certificate from a CA and just completed To Import a Certificate Authority Root Certificate on the Access Manager Load Balancer.
-
In the BIG-IP load balancer console, click Proxies.
-
Click the Cert-Admin tab.
The key LoadBalancer-3.example.com is in the Key List. This was generated in To Request an Secure Sockets Layer Certificate for the Access Manager Load Balancer.
-
In the Certificate ID column, click Install for LoadBalancer-3.example.com.
-
In the Certificate File field, click Browse.
-
In the Choose File dialog, navigate to the file that contains the certificate text sent to you by the CA and click Open.
-
Click Install Certificate.
-
On the Certificate LoadBalancer-3.example.com page, click Return to Certificate Administration Information.
Verify that the Certificate ID indicates LoadBalancer-3.example.com on the SSL Certificate Administration page.
-
Log out of the load balancer console.
 To Create an SSL Proxy for SSL Termination
on the Access Manager Load Balancer
To Create an SSL Proxy for SSL Termination
on the Access Manager Load Balancer
Secure Socket Layer (SSL) termination at Load Balancer 3 increases performance on the Access Manager level, and simplifies SSL certificate management. Because Load Balancer 3 sends unencrypted data to the Access Manager server, it does not have to perform decryption, and the burden on its processor is relieved. Clients send SSL-encrypted data to Load Balancer 3 which, in turn, decrypts the data and sends the unencrypted data to the appropriate Access Manager server. Load Balancer 3 also encrypts responses from the Access Manager server, and sends these encrypted responses back to the client. Towards this end, you create an SSL proxy, the gateway for decrypting HTTP requests and encrypting the reply.
Note –
SSL communication is terminated at Load Balancer 3 before a request is forwarded to the Access Manager servers.
Before You Begin
Before creating the SSL proxy, you should have a certificate issued by a recognized CA.
-
Access https://is-f5.example.com, the BIG-IP load balancer login page, in a web browser.
-
Log in with the following information.
- User name:
-
username
- Password:
-
password
-
Click Configure your BIG-IP (R) using the Configuration Utility.
-
In the left pane, click Proxies.
-
Under the Proxies tab, click Add.
-
In the Add Proxy dialog, provide the following information.
- Proxy Type:
-
Check the SSL checkbox.
- Proxy Address:
-
The IP address of Load Balancer 3.
- Proxy Service:
-
9443
The secure port number
- Destination Address:
-
The IP address of Load Balancer 3.
- Destination Service:
-
7070
The non-secure port number
- Destination Target:
-
Choose Local Virtual Server.
- SSL Certificate:
-
Choose LoadBalancer-3.example.com.
- SSL Key:
-
Choose LoadBalancer-3.example.com.
- Enable ARP:
-
Check this checkbox.
-
Click Next.
-
In the Rewrite Redirects field, choose Matching.
-
Click Done.
The new proxy server is added to the Proxy Server list.
-
Log out of the load balancer console.
-
Access https://LoadBalancer-3.example.com:9443/index.html from a web browser.
If the Web Server index page is displayed, you can access the Web Server using the new proxy server port number and the load balancer is configured properly.
Tip –A message may be displayed indicating that the browser doesn't recognize the certificate issuer. If this happens, install the CA root certificate in the browser so that the browser recognizes the certificate issuer. See your browser's online help system for information on installing a root CA certificate.
-
Close the browser.
- © 2010, Oracle Corporation and/or its affiliates
