8.4 Configuring the Distributed Authentication User Interface Load Balancer
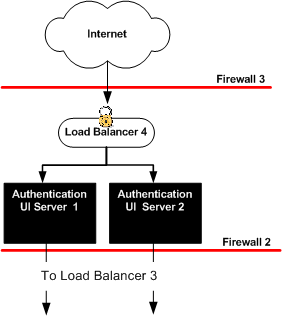
The following figure illustrates how Load Balancer 4 is configured in front of the two instances of the Distributed Authentication User Interface.
Figure 8–1 Distributed Authentication
Use the following list of procedures as a checklist for configuring the Distributed Authentication User Interface load balancer.
-
To Configure the Distributed Authentication User Interface Load Balancer
-
To Configure Load Balancer Cookies for the Distributed Authentication User Interface
-
To Import a CA Root Certificate on the Distributed Authentication User Interface Load Balancer
-
To Install an SSL Certificate on the Distributed Authentication User Interface Load Balancer
-
To Configure SSL Termination on the Distributed Authentication User Interface Load Balancer
 To Configure the Distributed Authentication User Interface Load Balancer
To Configure the Distributed Authentication User Interface Load Balancer
Before You Begin
-
This procedure assumes that you have already installed a load balancer.
-
The load balancer hardware and software used in the lab facility for this deployment is BIG-IP® manufactured by F5 Networks. If you are using different load balancer software, see the documentation that comes with that product for detailed settings information.
-
Contact your network administrator to obtain two available virtual IP addresses.
-
Know the IP address of the load balancer hardware, the URL for the load balancer login page, and a username and password for logging in to the load balancer application.
-
Get the IP addresses for Distributed Authentication User Interface 1 and Distributed Authentication User Interface 2 by running the following command on each host machine:
# ifconfig -a
-
Access https://is-f5.example.com, the Big IP load balancer login page, from a web browser.
-
Log in using the following information.
- User name:
-
username
- Password:
-
password
-
Click Configure your BIG-IP (R) using the Configuration Utility.
-
Create a Pool.
A pool contains all the backend server instances.
-
In the left pane, click Pools.
-
On the Pools tab, click Add.
-
In the Add Pool dialog, provide the following information:
- Pool Name
-
AuthenticationUI-Pool
- Load Balancing Method
-
Round Robin
- Resources
-
Add the IP address and port number of both Distributed Authentication User Interface host machines: AuthenticationUI-1:1080 and AuthenticationUI-2:1080.
-
Click Done.
-
-
Add a Virtual Server.
This step defines instances of the load balancer.
Tip –If you encounter JavaScriptTM errors or otherwise cannot proceed to create a virtual server, try using Internet Explorer.
-
In the left frame, Click Virtual Servers.
-
On the Virtual Servers tab, click Add.
-
In the Add Virtual Server wizard, enter the virtual server IP address and port number.
- Address
-
Enter the IP address for LoadBalancer-4.example.com
- Service
-
90
- Pool
-
AuthenticationUI-Pool
-
Continue to click Next until you reach the Pool Selection dialog box.
-
In the Pool Selection dialog box, assign the AuthenticationUI-Pool Pool.
-
Click Done.
-
-
Add Monitors.
Monitors are required for the load balancer to detect the backend server failures.
-
Configure the load balancer for persistence.
-
To verify that the Distributed Authentication User Interface load balancer is configured properly, access http://LoadBalancer-4.example.com:90/ from a web browser.
If the browser successfully renders the default Web Server document root page, the load balancer has been configured properly.
 To Configure Load Balancer Cookies for the Distributed Authentication User Interface
To Configure Load Balancer Cookies for the Distributed Authentication User Interface
Modify AMconfig.properties on both Distributed Authentication User Interface host machines.
-
Log in as a root user to the AuthenticationUI–1 host machine.
-
Change to the classes directory.
# cd /opt/SUNWwbsvr/https-AuthenticationUI-1.example.com/ web-app/AuthenticationUI-1.example.com/distAuth/WEB-INF/classes
-
Make the following changes to AMconfig.properties.
Tip –Backup AMConfig.properties before you modify it.
-
Save the file and close it.
-
Restart the AuthenticationUI–1 host machine.
-
Log in as a root user to the AuthenticationUI–2 host machine.
-
Change to the classes directory.
# cd /opt/SUNWwbsvr/https-AuthenticationUI-2.example.com/ web-app/AuthenticationUI-2.example.com/distAuth/WEB-INF/classes
-
Make the following changes to AMconfig.properties.
Tip –Backup AMConfig.properties before you modify it.
-
Save the file and close it.
-
Restart the AuthenticationUI–2 host machine.
 To Request a Secure Sockets Layer Certificate
for the Distributed Authentication User Interface Load Balancer
To Request a Secure Sockets Layer Certificate
for the Distributed Authentication User Interface Load Balancer
Generate a request for a Secure Sockets Layer (SSL) certificate to send to a certificate authority.
-
Access https://is-f5.example.com, the BIG-IP load balancer login page, from a web browser.
-
Log in to the BIG-IP console using the following information.
- User Name:
-
username
- Password:
-
password
-
Click Configure your BIG-IP (R) using the Configuration Utility.
-
In the left pane, click Proxies.
-
Click the Cert-Admin tab.
-
On the SSL Certificate Administration page, click Generate New Key Pair/Certificate Request.
-
On the Create Certificate Request page, provide the following information:
- Key Identifier:
-
LoadBalancer-4.example.com
- Organizational Unit Name:
-
Deployment
- Domain Name:
-
LoadBalancer-4.example.com
- Challenge Password:
-
password
- Retype Password:
-
password
-
Click Generate Key Pair/Certificate Request.
On the SSL Certificate Request page, the request is generated in the Certificate Request field.
-
Save the text contained in the Certificate Request field to a text file.
-
Log out of the console and close the browser.
-
Send the certificate request text you saved to the Certificate Authority of your choice.
A Certificate Authority (CA) is an entity that issues certified digital certificates; VeriSign, Thawte, Entrust, and GoDaddy are just a few. In this deployment, CA certificates were obtained from OpenSSL. Follow the instructions provided by your Certificate Authority to submit a certificate request.
 To Import a CA Root Certificate on the Distributed Authentication User Interface Load
Balancer
To Import a CA Root Certificate on the Distributed Authentication User Interface Load
Balancer
The CA root certificate proves that the particular CA (such as VeriSign or Entrust) did, in fact, issue a particular SSL certificate. You install the root certificate on Load Balancer 4 to ensure that a link between the Load Balancer 4 SSL certificate can be maintained with the issuing company. CA root certificates are publicly available.
Before You Begin
You should have a CA root certificate.
-
Access https://is-f5.example.com, the Big IP load balancer login page, from a web browser.
-
Log in using the following information:
- User name:
-
username
- Password:
-
password
-
In the BIG-IP load balancer console, click Proxies.
-
Click the Cert-Admin tab.
-
Click Import.
-
In the Import Type field, choose Certificate, and click Continue.
-
Click Browse in the Certificate File field on the Install SSL Certificate page.
-
In the Choose File dialog, choose Browser.
-
Navigate to the file that includes the root CA Certificate and click Open.
-
In the Certificate Identifier field, enter OpenSSL_CA_cert.
-
Click Install Certificate.
-
On the Certificate OpenSSL_CA_Cert page, click Return to Certificate Administration.
The root certificate OpenSSL_CA_Cert is now included in the Certificate ID list.
 To Install an SSL Certificate on the Distributed Authentication User Interface Load
Balancer
To Install an SSL Certificate on the Distributed Authentication User Interface Load
Balancer
Before You Begin
This procedure assumes you have received an SSL certificate from a CA and just completed To Import a CA Root Certificate on the Distributed Authentication User Interface Load Balancer.
-
In the BIG-IP load balancer console, click Proxies.
-
Click the Cert-Admin tab.
The key LoadBalancer-4.example.com is in the Key List. This was generated in To Request a Secure Sockets Layer Certificate for the Distributed Authentication User Interface Load Balancer.
-
In the Certificate ID column, click the Install button for LoadBalancer-4.example.com.
-
In the Certificate File field, click Browse.
-
In the Choose File dialog, navigate to the file that contains the certificate text sent to you by the CA and click Open.
-
Click Install Certificate.
-
On the Certificate LoadBalancer-4.example.com page, click Return to Certificate Administration Information.
Verify that the Certificate ID indicates LoadBalancer-4.example.com on the SSL Certificate Administration page.
-
Log out of the load balancer console.
 To Configure SSL Termination on the Distributed Authentication User Interface Load
Balancer
To Configure SSL Termination on the Distributed Authentication User Interface Load
Balancer
Secure Socket Layer (SSL) termination at Load Balancer 4 increases performance on the Access Manager level, and simplifies SSL certificate management. For example, because Load Balancer 4 sends unencrypted data internally neither the Access Manager server nor the Distributed Authentication User Interface has to perform decryption, and the burden on its processor is relieved. Clients send SSL-encrypted data to Load Balancer 4 which, in turn, decrypts the data and sends the unencrypted data to the appropriate Distributed Authentication User Interface. Load Balancer 4 also encrypts responses from the Distributed Authentication User Interface, and sends these encrypted responses back to the client. Towards this end, you create an SSL proxy, the gateway for decrypting HTTP requests and encrypting the reply.
Note –
Load Balancer 4 can intelligently load-balance a request based on unencrypted cookies. This would not be possible with SSL-encrypted cookies because Load Balancer 4 cannot read SSL-encrypted cookies.
Before You Begin
Before creating the SSL proxy, you should have a certificate issued by a recognized CA.
-
Access https://is-f5.example.com, the BIG-IP load balancer login page, in a web browser.
-
Log in using the following information:
- Username
-
username
- Password
-
password
-
Click Configure your BIG-IP using the Configuration Utility.
-
In the left pane, click Proxies.
-
On the Proxies tab, click Add.
-
In the Add Proxy dialog, provide the following information:
- Proxy Type:
-
Check the SSL checkbox.
- Proxy Address:
-
The IP address of Load Balancer 4, the Distributed Authentication User Interface load balancer.
- Proxy Service:
-
9443
The secure port number
- Destination Address:
-
The IP address of Load Balancer 4, the Distributed Authentication User Interface load balancer.
- Destination Service:
-
90
The non-secure port number
- Destination Target:
-
Choose Local Virtual Server.
- SSL Certificate:
-
Choose LoadBalancer-4.example.com.
- SSL Key:
-
Choose LoadBalancer-4.example.com.
- Enable ARP:
-
Check this checkbox.
-
Click Next.
-
In the Rewrite Redirects field, choose All.
-
Click Done.
The new proxy server is now added to the Proxy Server list.
-
Log out of the load balancer console.
-
Access https://LoadBalancer-4.example.com:9443/distAuth/UI/Login?goto= https://LoadBalancer-3.example.com:9443 from a web browser.
Tip –A message may be displayed indicating that the browser doesn't recognize the certificate issuer. If this happens, install the CA root certificate in the browser so that the browser recognizes the certificate issuer. See your browser's online help system for information on installing a root CA certificate.
-
Log in to the Access Manager console as the administrator.
- Username
-
amadmin
- Password
-
4m4dmin1
If you can successfully log in to Access Manager, the SSL certificate is installed and the proxy service is configured properly.
-
Log out of Access Manager, and close the browser.
- © 2010, Oracle Corporation and/or its affiliates
