Granting Access to Your Account
If you need to give someone access to log into your account (as you), you can do so through Kerberos, without revealing your password, by putting a .k5login file in your home directory. A .k5login file is a list of one or more Kerberos principals corresponding to each person for whom you want to grant access. (Each principal must be on a separate line.)
Suppose that the user david keeps a .k5login file in his home directory that looks like this:
jennifer@ENG.ACME.COM joe@ACME.ORG |
This file allows the users jennifer and joe to assume david's identity, provided that they already have Kerberos tickets in their respective realms. For example, jennifer can rlogin into david's machine (boston), as him, without having to give his password:
Figure 6-1 Using the .k5login File
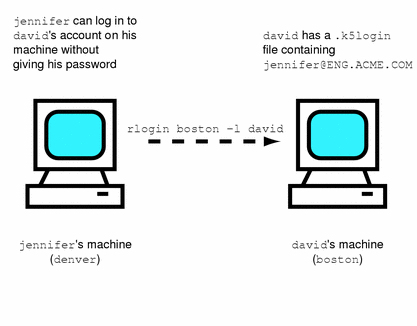
(In the case where david's home directory is NFS-mounted, using Kerberos V5 protocols, from another (third) machine, jennifer must have a forwardable ticket in order to access his home directory. See "How to Create a Ticket" for an example of using a forwardable ticket.)
If you will be logging into other machines across a network, you'll want to include your own Kerberos principal in .k5login files on those machines.
Using a .k5login file is much safer than giving out your password:
-
You can take access away any time by removing the principal(s) from your .k5login file.
-
Although users named in the .k5login file in your home directory have full access to your account on that machine (or sets of machines, if the .k5login file is shared, for example over NFS), they do not inherit your network privileges -- that is, any Kerberized services will authorize access based on that user's identity, not yours. So jennifer can log in to joe's machine and perform tasks there, but if she uses a Kerberized programs such as ftp or rlogin, she does so as herself.
-
Kerberos keeps a log of who obtains tickets, so a system administrator can find out, if necessary, who is capable of using your user identity at a particular time.
One common way to use the .k5login file is to put it in root's home directory, giving root access for that machine to the Kerberos principals listed. This allows system administrators to become root locally, or to log in remotely as root, without having to give out the root password, and without anyone having to type the root password over the network.
Example -- Using the .k5login File
Suppose jennifer decides to log in to the machine boston.acme.com as root. Since she has an entry for her principal name in the .k5login in root's home directory on boston.acme.com, she again does not have to type in her password:
% rlogin boston.acme.com -l root -x This rlogin session is using DES encryption for all data transmissions. Last login: Thu Jun 20 16:20:50 from daffodil SunOS Release 5.7 (GENERIC) #2: Tue Nov 14 18:09:31 EST 1998 boston[root]% |
- © 2010, Oracle Corporation and/or its affiliates
