Discovery Service Process
This figure provides a high-level overview of the interaction between parties in a web services environment using the Discovery Service. In this scenario, the identity provider hosts the Discovery Service. The process assumes that the Discovery Service is not generating security tokens. The individual steps are written up in more detail following the figure.
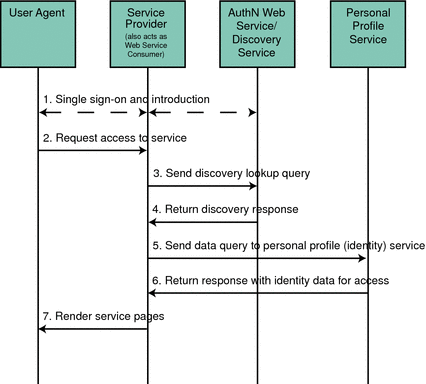
Figure 8–2 Participants in, and Process of, the Discovery Service
-
The user logs in to a Liberty-enabled identity provider, is authenticated, and completes the federation process, enabling single sign-on with other members of the authentication domain. More specifically:
-
Within a browser, the user types the URL for a Liberty-enabled service provider.
-
The service provider collects the user’s credentials and redirects the information to the identity provider for authentication.
-
If the credentials are verified, the user is authenticated.
-
Assuming the identity provider is the center of an authentication domain, that provider will notify the authenticated user of the option to federate any local identities created with member organizations. The user would then accept or decline this invitation to federate. By accepting the invitation, the user will be given the option to federate to a member organization’s web site at each login. If the user accepts this option to federate, single sign-on is enabled.
-
-
After authentication, the user now requests access to services hosted by another service provider in the authentication domain.
-
The service provider, acting as a web service consumer (WSC), sends a DiscoveryLookup query to the Discovery Service looking for a pointer to the user's identity provider.
The service provider is able to bootstrap the Discovery Service using the end point reference culled from the authentication statement.
-
The Discovery Service returns a DiscoveryLookup response to the service provider that points to the instance of the requested identity provider.
The response contains the resource offering for the user’s Personal Profile Service.
-
The service provider then sends a query (using the Data Services Template Specification) to the Personal Profile Service.
The required authentication mechanism specified in the Personal Profile Service resource offering must be followed.
-
The Personal Profile Service authenticates and validates authorization, or policy, or both for the requested user and service provider, and returns a Data Services Template response.
If user interaction is required for some attributes, the Interaction Service will be invoked to query the user for consents or attribute values. The Data Services Template would then be returned after all required data is collected.
-
The service provider processes the Personal Profile Service response and renders HTML pages based on the original request and user authorization.
A user's actual account information is not exchanged during federation. Thus, the identifier displayed on each provider site will be based on the respective local identity profile.
- © 2010, Oracle Corporation and/or its affiliates
