Installing Portal Server and Access Manager in a High Availability Scenario with Berkeley Database
This section explains how to install Portal Server and Access Manager in a high availability scenario using Berkeley database. Berkeley database is installed when you install Access Manager. In a high availability scenario, Berkeley database is used to store session variables of the user.
In the procedures in this section, you do the following:
-
Install Directory Server, Application Server, Access Manager, and Portal Server on Node 1 and Node 2.
-
Install a Portal Server instance on Node 2. (The portal ID for Node 1 and Node 2 are the same.)
-
Install a Load Balancer on Node 3.
Figure 8–1 Portal Server With Berkely Database
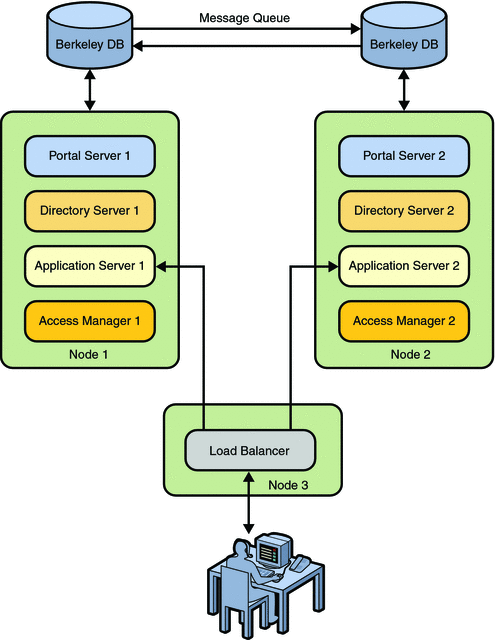
 To Install Portal Server and Access Manager in a High
Availability Scenario with Berkeley Database
To Install Portal Server and Access Manager in a High
Availability Scenario with Berkeley Database
These instructions require the following:
-
Directory Server on Node 1 is not in the multi master replication (MMR) mode. Only one instance of Directory Server exists.
-
Access Manager on Node 1 is installed in Legacy mode. The data can be stored only in Directory Server.
-
On Node 1, install Directory Server, Access Manager, and Application Server.
-
Verify whether Access Manager is installed properly by accessing amconsole.
http://node1.domain-name:8080/amconsole
-
Log in to amconsole on Node 1. In the Organization Aliases List, add the Fully Qualified Domain Name (FQDN) of Node 2.
-
Click Service Configuration and click Platform in the right panel.
-
In the Platform Server List, add the following.
http://node2.domain-name:8080|02
-
On Node 2, run the Java ES installer to install Access Manager.
On the page that asks whether Directory Server is already provisioned with data, select Yes and proceed with installing Access Manager.
Note –Ensure that the password encryption key on Node 2 is the same as the password encryption key on Node 1. The password encryption key should be the same for the LDAP internal password on both of the nodes.
-
On Node 2, start Application Server and verify whether Access Manager is installed properly by accessing amconsole.
http://node2.domain-name:8080/amconsole
-
In a text editor, open the AMConfig.properties file on Node 1 and Node 2.
The file is located in the AccessManager_base/SUNWam/config directory.
 To Install the Load Balancer on Node 3
To Install the Load Balancer on Node 3
-
Install the Load Balancer plugin on Node 3 that is provided with Application Server 8.2. Select Web Server as a component to install with the Load Balancer plugin.
-
In a text editor, open the loadbalancer.xml file on Node 3.
This file is located in the WebServer_base/SUNWwbsvr7/https-Node3/config directory.
-
Edit the file so that the Load Balancer balances the load between the two Access Manager instances.
Edit the listeners with the appropriate values.
A sample loadbalancer.xml which balances the load on Portal Server and Access Manager instances on Node 1 and Node 2 is as follows:
<!DOCTYPE loadbalancer PUBLIC "-//Sun Microsystems Inc.//DTD Sun ONE Application Server 7.1// EN" "sun-loadbalancer_1_1.dtd"> <loadbalancer> <cluster name="cluster1"> <!-- Configure the listeners as space seperated URLs like listeners="http://host:port https://host:port" For example: <instance name="instance1" enabled="true" disable-timeout-in-minutes="60" listeners="http://localhost:80 https://localhost:443"/> --> <instance name="instance1" enabled="true" disable-timeout-in-minutes="60" listeners="http://node1.domain-name:8080"/> <instance name="instance2" enabled="true" disable-timeout-in-minutes="60" listeners="http://node2.domain-name:8080"/> <web-module context-root="/portal" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <web-module context-root="/psconsole" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <web-module context-root="/amserver" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <web-module context-root="/amconsole" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <web-module context-root="/ampassword" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <web-module context-root="/amcommon" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <web-module context-root="/" enabled="true" disable-timeout-in-minutes="60" error-url="sun-http-lberror.html" /> <health-checker url="/" interval-in-seconds="10" timeout-in-seconds="30" /> </cluster> <property name="reload-poll-interval-in-seconds" value="60"/> <property name="response-timeout-in-seconds" value="30"/> <property name="https-routing" value="true"/> <property name="require-monitor-data" value="false"/> <property name="active-healthcheck-enabled" value="false"/> <property name="number-healthcheck-retries" value="3"/> <property name="rewrite-location" value="true"/> </loadbalancer>
-
Start the Web Server.
-
On Node 1 and Node 2, start Access Manager, Directory Server, and Application Server .
 To Configure Session Failover with Message Queue and
Berkeley Database
To Configure Session Failover with Message Queue and
Berkeley Database
-
Edit the Application Server domain.xml file on Node 1 and Node 2 to add locations of the jms.jar file and imq.jarfile.
<JAVA javahome="/usr/jdk/entsys-j2se" server-classpath="/usr/share/lib/imq.jar:/usr/share/lib/jms.jar: ....?
Note –When you create a Message Queue instance, do not use the default Message Queue instance that starts with Application Server or the guest user for Message Queue.
-
Start Message Queue on Node 1 and Node 2.
/bin/imqbrokerd -tty -name mqins -port 7777 &
where mqins is the Message Queue instance name.
-
Add a user to this message queue.
imqusermgr add -u amsvrusr -p secret12 -i mqins -g admin
where amsvrusr is the name of the new user that is used instead of guest.
-
Inactivate the guest user.
imqusermgr update -u guest -i mqins -a false
-
Create an encrypted file for the message queue on Node 1 and Node 2.
./amsfopasswd -f /AccessManager_base/SUNWam/.password -e password-file
-
Edit the amsfo.conf file on both the nodes.
A list of sample entries in amsfo.conf file is displayed as follows:
AM_HOME_DIR=/opt/SUNWam AM_SFO_RESTART=true LUSTER_LIST=node1.domain-name:7777,node2.domain-name:7777 DATABASE_DIR="/tmp/amsession/sessiondb" DELETE_DATABASE=true LOG_DIR="/tmp/amsession/logs" START_BROKER=true BROKER_INSTANCE_NAME=amsfo BROKER_PORT=7777 BROKER_VM_ARGS="-Xms256m -Xmx512m" USER_NAME=amsvrusr PASSWORDFILE=$AM_HOME_DIR/.password AMSESSIONDB_ARGS="" lbServerPort=8080 lbServerProtocol=http lbServerHost=node3.domain-name SiteID=10
-
Configure amsfo.confon Node 1.
AccessManager_base/SUNWam/bin/amsfoconfig
After running the script, the following output is displayed:
Session Failover Configuration Setup script. ========================================================= ========================================================= Checking if the required files are present... ========================================================= Running with the following Settings. ------------------------------------------------- Environment file: /etc/opt/SUNWam/config/amProfile.conf Resource file: /opt/SUNWam/lib/amsfo.conf ------------------------------------------------- Using /opt/SUNWam/bin/amadmin Validating configuration information. Done... Please enter the LDAP Admin password: (nothing will be echoed): password1 Verify: password1 Please enter the JMQ Broker User password: (nothing will be echoed): password2 Verify: password2 Retrieving Platform Server list... Validating server entries. Done... Retrieving Site list... Validating site entries. Done... Validating host: http://amhost1.example.com:7001|02 Validating host: http://amhost2.example.com:7001|01 Done... Creating Platform Server XML File... Platform Server XML File created successfully. Creating Session Configuration XML File... Session Configuration XML File created successfully. Creating Organization Alias XML File... Organization Alias XML File created successfully. Loading Session Configuration schema File... Session Configuration schema loaded successfully. Loading Platform Server List File... Platform Server List server entries loaded successfully. Loading Organization Alias List File... Organization Alias List loaded successfully. Please refer to the log file /var/tmp/amsfoconfig.log for additional information. ############################################################### Session Failover Setup Script. Execution end time 10/05/05 13:34:44 ############################################################### -
Edit the amsessiondb script with the default path and directory of the following:
JAVA_HOME=/usr/jdk/entsys-j2se/ IMQ_JAR_PATH=/usr/share/lib JMS_JAR_PATH=/usr/share/lib BDB_JAR_PATH=/usr/share/db.jar BDB_SO_PATH=/usr/lib AM_HOME=/opt/SUNWam
-
Start and stop the Message Queue instance running on port 7777.
AccessManager_base/SUNWam/bin/amsfo start
AccessManager_base/SUNWam/bin/amsfo stop
-
Restart Access Manager, Directory Server, Application Server, and Web Server on all the nodes.
-
Log in to the amconsole through Load Balancer.
http://node3.domain-name:80/amconsole
-
Stop the Application Server on Node 1.
The session is handled by Access Manager on Node 2.
 To Install Portal Server on Node 1
To Install Portal Server on Node 1
-
Invoke the Java ES installer and install Portal Server on Node 1 in the Configure Now mode.
-
Access Portal Server to verify the installation.
http://node1.domain-name:8080/portal
-
Create a Portal Server instance on Node 2.
 To Create a Portal Server Instance on Node 2
To Create a Portal Server Instance on Node 2
-
Invoke the Java ES installer, and install Portal Server in the Configure Now mode.
-
Copy example2.xml to a temporary directory to make a backup of the original file.
cp PortalServer_base/SUNWportal/samples/psconfig/example2.xml /tmp-directory
-
Edit the original example2.xml file to replace the tokens with the machine information for Node 1.
-
Configure Portal Server using the example2.xml file as the configuration XML file.
PortalServer_base/SUNWportal/bin/psconfig --config example2.xml
-
Copy the Webcontainer.properties template file to Portal Server installation bin directory.
cp PortalServer_base/SUNWportal/template/Webcontainer.properties \PortalServer_base/SUNWportal/bin
-
Modify the WebContainer.properties file as per your requirements.
vi PortalServer_base/SUNWportal/bin/WebContainer.properties
Refer to the Creating Multi-Portal for more information about changing the WebContainer.properties file.
-
Create a Portal Server instance.
PortalServer_base/SUNWportal/bin/psadmin create-instance -u amadmin -f ps_password -p portal1 -w Webcontainer.properties
-
Restart Directory Server, Application Server, Access Manager, and Portal Server on Node 1 and Node 2.
-
Restart Web Server on Node 3.
-
Access the portal through the Load Balancer.
You can verify the node to which the portal is connected by tracking the access logs of the container. After you log in to the portal, kill the Application Server on the node to which it is connected. Then, click any of the links on the desktop to maintain the session and automatically connect to Node 2.
- © 2010, Oracle Corporation and/or its affiliates
