Appendix B Identity Manager and Identity Synchronization for Windows Cohabitation
This appendix describes how Sun Java System Identity Synchronization for Windows 6.0 and Identity Manager 5.0 SP2 co-exist in a customer deployment as part of a larger user provisioning strategy, to facilitate native password changes on Directory Server and Active Directory.
This appendix augments Chapter 3, Case Study: Deploying in a High-Availability Environment Over a Wide Area Network Using SSL integration of Identity Synchronization for Windows with Identity Manager, and the changes required in Identity Manager, for coexistence.
This appendix assumes knowledge of the concepts and deployment experience of Identity Manager. For details, see http://docs.sun.com.
This appendix includes:
-
Identity Manager and Identity Synchronization for Windows Functionality
-
Password Changes and Provisions Originating from Identity Manager Console
-
Configuring Identity Manager and Identity Synchronization for Windows
Overview
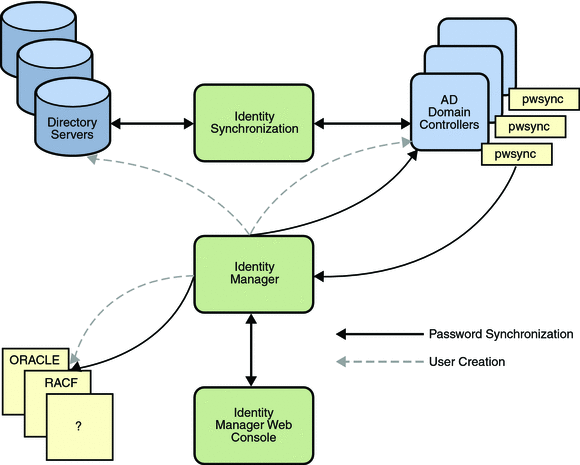
Overview illustrates the following three important components of the Identity Manager and Identity Synchronization for Windows cohabitation deployment:
-
Active Directory Domains
-
Separate Directory Server deployment
-
Any other Identity Manager-managed resource, which does not include the previous two, for example, Oracle RDBMS
The Identity Manager Console handles resource administration such as system-wide password changes and users creation. All password changes between Directory Servers and Active Directory Domains are synchronized using Identity Synchronization for Windows. Password changes that occur within an Active Directory Domain are synchronized to Directory Server using Identity Synchronization for Windows, and synchronized to all other Identity Manager resources using pwsync (an Identity Manager DLL installed on the Primary Domain Controllers of Windows systems). All password changes originating from the Identity Manager Administrator Console are subsequently propagated to all Identity Manager resources, except the Sun Java System Directory Server. All user creations originating from the Identity Manager Console are reflected to all resources, including Directory Servers. For details, seeConfiguring pwsync to Not Propagate Passwords to Directory Server
Figure B–1 Password Synchronization and User Creation in an Identity Manager-Identity Synchronization for Windows Environment
Identity Manager and Identity Synchronization for Windows Functionality
The effective functionality of Identity Manager and Identity Synchronization for Windows results only when both the systems deployed and configured to function as a single system.
The Identity Synchronization for Windows functionality comprises:
-
Detection of all the password changes on Active Directory, and synchronization with Directory Server using On Demand Synchronization.
-
Detection of all password changes on Directory Server, and synchronization with Active Directory.
Identity Synchronization for Windows does not synchronize:
-
User creations
-
User deletions
-
Non-password attributes
The Identity Manager functionality, in cohabitation with Identity Synchronization for Windows, comprises:
-
Detection of all password changes on Active Directory using the pwsync component and synchronization of the changes to all other Identity Manager-managed resources, except Directory Server resources.
-
Use of Identity Manager Administrator Console to propagate user password changes to Active Directory and all other Identity Manager-managed resources, except Directory Server.
-
Use of Identity Manager Administrator Console to propagate new users across all Identity Manager-managed resources (including Directory Server).
Password Changes on Active Directory
Passwords modified on Active Directory are propagated through the Identity Manager-Identity Synchronization for Windows deployment as described below (See Overview for illustration):
-
The user resets the password on Active Directory by using the Change Password option in the Task Manager dialog of Windows.
-
Identity Synchronization for Windows detects the change and sets a password invalid flag on the corresponding user entry in the Identity Synchronization for Windows-managed Directory Server.
-
The user connects to Directory Server for the password change to be complete (see On Demand Synchronization in the Sun Java System Directory Server Enterprise Edition 6.3 Installation Guide.)
-
Identity Manager’s pwsync command also detects the password change and propagates it to all other Identity Manager-managed resources, except Directory Servers.
Password Changes on Directory Server
Passwords modified on Directory Servers are propagated through the Identity Manager-Identity Synchronization for Windows deployment as described below:
-
The password change is detected by Identity Synchronization for Windows and propagated to Active Directory.
-
Identity Manager’s pwsync command also detects the password change and propagates it to all other Identity Manager-managed resources, except Directory Servers.
Password Changes and Provisions Originating from Identity Manager Console
Password changes that occur through the Identity Manager Administration Console are propagated to all Identity Manager-managed resources, except Directory Server. Once a password change is detected on Active Directory, Identity Synchronization for Windows synchronizes it with Directory Server.
User creation originating from the Identity Manager Administration Console is propagated to all Identity Manager-managed resources, including both Directory Server and Active Directory Domains. New users will have to be linked by Identity Synchronization for Windows. For details, see Configuring pwsync to Not Propagate Passwords to Directory Server and Handling Identity Manager-Provisioned Users
Configuring Identity Manager and Identity Synchronization for Windows
Configuring Identity Manager and Identity Synchronization for Windows involves the following tasks:
Setting Up Identity Manager 5.0 SP2 and Later
Identity Manager 5.0 SP2 introduced a new form property that prevents the Directory Server resource from being shown as a resource where passwords can be changed. Identity Manager 5.0 SP2 also introduced a new system configuration property that can be used to prevent pwsync from reflecting password changes to the Directory Server resource.
Configuring the Form Property
To ensure that Identity Manager does not propagate user password changes to Directory Server but instead only propagates them to Active Directory, and then relies on Identity Synchronization for Windows to propagate them to Directory Server, the following form property can be added to any form used for changing a user's password. This will prevent a resource from being displayed in the table of resources where password changes occur.
<Properties\>
<Property name='Exclude'\>
<list\>
/<new class='com.waveset.object.AttributeCondition'\>
<s\>id</s\>
<s\>equals</s\>
<s\>#ID#50D9481DC6C43026:3BB34:FFB73A9286:-7FC0</s\>
</new\>/
</list\>
</Property\>
</Properties\>
|
The resource can be excluded by id as shown in the form above, name (a string), or by type (also a string). The forms to which this property must be included are:
-
Change My Password Form
-
Change Password Form
-
Expired Login Form
-
Tabbed User Form
Note –
Some of the forms above already include the form property. In such scenarios, only the new attribute condition needs to be added from the XML fragment above.
In multiple attribute condition scenarios, the forms are and'ed together (they cannot be or'ed). For example, if the Change My Password form and Change Password form already include an attribute condition to exclude disabled resources, and the condition above is added, a resource will only be excluded if it meets both conditions, that is, it is disabled and has the ID you entered.
If a form does not already include the Exclude property, it can be added by copying the full XML fragment above, or by adding the <Property name=Exclude\>, if a <Properties\> block already exists.
Configuring pwsync to Not Propagate Passwords to Directory Server
The passwordSyncExcludeList System Configuration attribute lists resources that should not be updated when the Active Directory pwsync Plugin detects a password change. In an Identity Manager-Identity Synchronization for Windows environment, this attribute should include Directory Servers that are being synchronized, to prevent unwanted interaction between Identity Manager and Identity Synchronization for Windows. This attribute can be added to the system configuration object by going to the /debug page (for example, http://applicationserverhost:port/idm/debug), listing objects of type Configuration, and editing the System Configuration to include the following
<Attribute name='passwordSyncExcludeList' value='Directory Server Resource'/\>
where Directory Server Resource is the name of the resource to be excluded during a pwsync password change. (If there is more than one resource to exclude, use a comma-separated list.)
Setting Up Identity Manager 5.0 SP1 and Earlier
Identity Manager installations prior to 5.0 SP2 require a modification to the workflow for coexistence with Identity Synchronization for Windows. These changes facilitate propagation of updates from other Identity Manager resources to Directory Servers (provisioning) and to Active Directory (passwords and provisioning). Administrators must install the Identity Manager component pwsync on all domain controllers where password synchronization is desired with all other Identity Manager-managed resources (except Directory Server).
This workflow change will result in an error during the end-user password change. However, the change is propagated to Directory Server.
To modify the workflow:
-
Install pwsync on all Active Directory domain controllers.
-
Modify the Identity Manager task definition for Change User Password, which can be done from the /debug page or the Configuration Editor.
-
Add a new activity to remove the Directory Server resources that should not have the password reset.
-
Replace the string NAME DS RESOURCE with the names of these Directory Server resource. This can be done by adding the following activity:
<Activity id='1' name='RemoveLDAP'\> <Variable name='userObject'/\> # checkout user # <Action id='0' application='com.waveset.session.WorkflowServices'\> <Argument name='op' value='checkoutObject'/\> <Argument name='type' value='User'/\> <Argument name='name' value='$(accountId)'/\> <Argument name='authorized' value='true'/\> <Return from='object' to='userObject'/\> </Action\> <Action id='1'\> <expression\> <block\> # Get pending changes for Directory Server resource # <defvar name='resourceInfo'\> <invoke name='getResourceInfo'\> <ref\>userObject</ref\> <s\>NAME DS RESOURCE</s\> </invoke\> </defvar\>
# Clears pending password change # <invoke name='setPassword'\> <ref\>resourceInfo</ref\> <null/\> </invoke\> # Get other pending resource changes # <defvar name='resourceInfoAttributes'\> <invoke name='getAttributes'\> <ref\>resourceInfo</ref\> </invoke\> </defvar\> # removes expire password flag # <invoke name='remove'\> <ref\>resourceInfoAttributes</ref\> <s\>expirePassword</s\> </invoke\> # Set cleared attributes for check in # <invoke name='setAttributes'\> <ref\>resourceInfo</ref\> <ref\>resourceInfoAttributes</ref\> </invoke\> </block\> </expression\> </Action\> # Check in user # <Action id='2' application='com.waveset.session.WorkflowServices'\> <Argument name='op' value='checkinObject'/\> <Argument name='object' value='$(userObject)'/\> </Action\> <Transition to='Reprovision'/\> </Activity\>
-
Configuring Identity Synchronization for Windows
Identity Synchronization for Windows should be configured as described in Chapter 3, Case Study: Deploying in a High-Availability Environment Over a Wide Area Network Using SSL and not be configured for user creations or any other attribute synchronization.
Handling Identity Manager-Provisioned Users
User creation is not the responsibility of Identity Synchronization for Windows in this deployment. Therefore, new users that are added to Directory Server using Identity Manager will not be linked to the corresponding entries in Active Directory Domains, and visa-versa. To establish this link for new users, administrators must periodically execute idsync resync so that password changes for the new entries are synchronized. The frequency with which this operation is executed is the administrator’s decision. Periodic automated execution is feasible using a scheduled UNIX cron job. For details, see Periodic idsync resync Operation for Primary Installation
- © 2010, Oracle Corporation and/or its affiliates
