Chapter 1 Introducing OpenSSO Enterprise
Sun OpenSSO Enterprise 8.0 (OpenSSO Enterprise) integrates authentication and authorization services, single sign-on (SSO), and open, standards-based federation protocols (including the Liberty Alliance Project specifications, WS-Federation and Security Assertion Markup Language [SAML]) to provide a comprehensive solution for protecting network resources by preventing unauthorized access to web services, applications and web content, and securing identity data. This introductory chapter contains a high-level description of OpenSSO Enterprise and what it does. It contains the following sections:
What is OpenSSO Enterprise?
OpenSSO Enterprise is a single product that combines the features of Sun Java™ System Access Manager, Sun Java System Federation Manager, and the Sun Java System SAML v2 Plug-in for Federation Services. Additionally, it is enhanced with new functionality developed specifically for this release. OpenSSO Enterprise provides access management by allowing the implementation of authentication, policy-based authorization, federation, SSO, and web services security from a single, unified framework. The core application is delivered as a simple web archive (WAR) that can be easily deployed in a supported web container.
Note –
OpenSSO Enterprise is Sun Microsystems' commercial distribution of the open source code available at OpenSSO.
To assist the core application, policy agents, the Client SDK, and (possibly) other disparate pieces must be installed remotely and be able to communicate with the OpenSSO Enterprise server. See What Does OpenSSO Enterprise Do? for a high-level picture of the deployment architecture and Chapter 2, Examining OpenSSO Enterprise for more specific information.
What Does OpenSSO Enterprise Do?
The following types of interactions occur daily in a corporate environment.
-
An employee looks up a colleague’s phone number in the corporate phone directory.
-
A manager retrieves employee salary histories to determine an individual’s merit raise.
-
An administrative assistant adds a new hire to the corporate database, triggering the company’s health insurance provider to add the new hire to its enrollment.
-
An engineer sends an internal URL for a specification document to another engineer who works for a partner company.
-
A customer logs into a company’s web site and looks for a product in their online catalog.
-
A vendor submits an invoice to the company’s accounting department.
-
A corporate human resources administrator accesses an outsourced benefits application.
For each of these transactions, the company must determine who is allowed to view the information or use the application. Some information such as product descriptions and advertising can be made available to everyone in a public online catalog. Other information such as accounting and human resources data must be restricted to employees only. And other sensitive information such as pricing models and employee insurance plans is appropriate to share only with partners, suppliers, and employees. This need for access determination is met by Sun OpenSSO Enterprise, an access management product with authentication, authorization, and single sign-on (SSO) services provided out of the box.
When a user or an external application requests access to content stored on a company’s server, a policy agent (available in a separate download and installed on the same machine as the resource you want to protect) intercepts the request and directs it to OpenSSO Enterprise which, in turn, requests credentials (such as a username and password in the case of a user) for authentication. If the credentials returned match those stored in the appropriate identity data store, OpenSSO Enterprise determines that the user is authentic. Following authentication, access to the requested content is determined by the policy agent which evaluates the policies associated with the authenticated identity. Policies are created using OpenSSO Enterprise and identify which identities are allowed to access a particular resource, specifying the conditions under which this authorization is valid. Based upon the results of the policy evaluation, the policy agent either grants or denies the user access. Figure 1–1 illustrates a high-level deployment architecture of OpenSSO Enterprise.
Figure 1–1 High-level Deployment Architecture of OpenSSO Enterprise
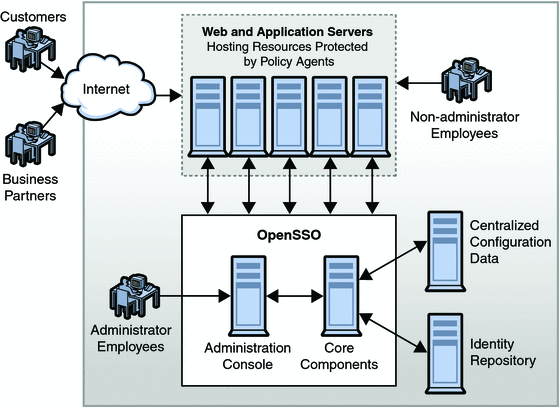
What Are the Functions of OpenSSO Enterprise?
The following sections contain an overview of the functions of OpenSSO Enterprise.
Access Control
OpenSSO Enterprise manages authorized access to network services and resources. By implementing authentication and authorization, OpenSSO Enterprise (along with an installed policy agent) ensures that access to protected resources is restricted to authorized users. In a nutshell, a policy agent intercepts a request for access to a resource and communicates with OpenSSO Enterprise to authenticate the requestor. If the user is successfully authenticated, the policy agent then evaluates the policies associated with the requested resource and the user to determine if the authenticated user is authorized to access the resource. If the user is authorized, the policy agent allows access to the resource, also providing identity data to the resource to personalize the interaction. For more information on access control, see Core Services and Part II, Access Control Using OpenSSO Enterprise.
Federation Management
With the introduction of federation protocols into the process of access management, identity information and entitlements can be communicated across security domains, spanning multiple trusted partners. By configuring a circle of trust and defining applications and services as providers in the circle (either identity providers or service providers), users can opt to associate, connect or bind the various identities they have configured locally for these providers. The linked local identities are federated and allow the user to log in to one identity provider site and click through to an affiliated service provider site without having to reauthenticate; in effect, single sign-on (SSO). OpenSSO Enterprise supports several open federation technologies including the Security Access Markup Language (SAML) versions 1 and 2, WS-Federation, and the Liberty Alliance Project Identity Federation Framework (Liberty ID-FF), therefore encouraging an interoperable infrastructure among providers. For more information on federation management, see Core Services and Part III, Federation Management Using OpenSSO Enterprise.
Web Services Security
A web service is a component service or application that exposes some type of business or infrastructure functionality through a language-neutral and platform-independent, network interface; enterprises might use this web service to build larger service-oriented architectures. In particular, the service defines its interface (for example, the format of the message being exchanged) using the Web Services Description Language (WSDL), and communicates using SOAP and eXtensible Markup Language (XML) messages. The web service client (WSC) communicates with the web service provider (WSP) through an intermediary — usually a firewall or load balancer.
Although web services enable open, flexible, and adaptive interfaces, their openness creates security risks. Without proper security protections, a web service can expose vulnerabilities that might have dire consequences. Hence, ensuring the integrity, confidentiality and security of web services through the application of a comprehensive security model is critical for both enterprises and consumers. A successful security model associates identity data with the web services and creates secure service-to-service interactions. The security model adopted by OpenSSO Enterprise identifies the user and preserves that identity through multiple interactions, maintains privacy and data integrity, uses existing technologies, and logs the interactions. In OpenSSO Enterprise, the following web service security standards are implemented:
-
Liberty Alliance Project Identity Web Services Framework (Liberty ID-WSF)
-
WS-I Basic Security Profile
-
WS-Trust (from which the Security Token Service was developed)
The web services security framework uses the Security Token Service and separately installed security agents. For more information on OpenSSO Enterprise web services and web services security, see Core Services and Part IV, The Web Services Stack, Identity Services, and Web Services Security.
Identity Web Services
For some time, OpenSSO Enterprise has provided client interfaces for access to core features and functionality. These interfaces are used by policy agents and custom applications developed by customers. With this release, OpenSSO Enterprise now exposes certain functions as simple identity web services allowing developers to easily invoke them when developing their applications using one of the supported integrated development environment (IDE) products. (The IDE generates the stub code that wraps a call to the web service.) Identity Web Services are available using:
-
SOAP and Web Services Description Language (WSDL)
-
Representational State Transfer (REST)
They do not require the deployment of an agent or a proxy and include the following capabilities:
-
Authentication to validate user credentials.
-
Authorization to permit access to protected resources.
-
Provisioning for user attribute management and self registration.
-
Logging to keep track of it all.
For more information on identity services, see Identity Web Services and Part IV, The Web Services Stack, Identity Services, and Web Services Security.
What Else Does OpenSSO Enterprise Offer?
OpenSSO Enterprise allows for:
-
Ease of Deployment: OpenSSO Enterprise is delivered as a web archive (WAR) that can be easily deployed as a Java EE application in different web containers. Most configuration files and required libraries are inside the WAR to avoid the manipulation of the classpath in the web container's configuration file. The OpenSSO Enterprise WAR is supported on:
-
Sun Java System Web Server 7.0 — Update 3 and above
-
Sun Java System Application Server 9.1 EE Update 2 and above (and Glassfish v2 update 2 and above)
-
BEA WebLogic Application Server 9.2 mp2
-
IBM WebSphere Application Server 6.1
-
Oracle Application Server 10g
-
JBoss 4.2.x
-
Tomcat 5.5.x & 6.x
Note –Tomcat 5.5.26 and 6.15 are not supported.
-
Geronimo (supported on the Sun SolarisTM 10 Operating Environment for SPARC, x86 & x64 and the Sun Solaris 9 Operating Environment for SPARC & x86 systems only)
Note –Geronimo can install Tomcat and Jetty web containers; OpenSSO Enterprise supports only Tomcat.
See the Sun OpenSSO Enterprise 8.0 Release Notes for updates to this list.
-
-
Portability: OpenSSO Enterprise is supported on the following operating systems:
-
Sun Solaris 10 Operating Environment for SPARC, x86 & x64 systems
-
Sun Solaris 9 Operating Environment for SPARC & x86 systems
-
Windows Server 2003 and Windows XP (development only) operating systems
-
Red Hat Enterprise Linux 4 Server (Base)
-
Red Hat Enterprise Linux 4 Advanced Platform
-
Red Hat Enterprise Linux 5 Server (Base)
-
Red Hat Enterprise Linux 5 Advanced Platform
-
Windows 2003 Standard Server
-
Windows 2003 Enterprise Server
-
Windows 2003 Datacenter Server
-
Windows Vista
-
IBM AIX 5.3 (supported with the IBM WebSphere Application Server 6.1 container only)
See the Sun OpenSSO Enterprise 8.0 Release Notes for updates to this list.
-
-
Open Standards: OpenSSO Enterprise is built using open standards and specifications as far as possible. For example, features designed for federation management and web services security are based on the Security Assertion Markup Language (SAML), the Liberty Alliance Project specifications, and the WS-Security standards.
-
Ease of Administration: OpenSSO Enterprise contains a web-based, graphical administration console as well as command line interfaces for configuration tasks and administrative operations. Additionally, an embedded, centralized data store allows for one place to store server and agent configuration data.
-
Security:
-
Runtime security enables an enterprise's resources to be protected as configured and OpenSSO Enterprise services to be accessed by authorized entities only.
-
Administration security ensures only authorized updates are made to the OpenSSO Enterprise configuration data.
-
Deployment security implements best practices for installing OpenSSO Enterprise on different operating systems, web containers, and so forth.
Additionally, all security actions are logged.
-
-
Configuration Data Store: OpenSSO Enterprise can write server configuration data to a centralized configuration data store. You can also point to instances of Sun Java System Directory Server 5.2 or Directory Server Enterprise Edition 6.x during configuration of OpenSSO Enterprise for use as a configuration data store. See Data and Data Stores for more information.
-
User Data Store Independence: OpenSSO Enterprise allows you to view and retrieve user information without making changes to an existing user database. Supported directory servers include Directory Server 5.1, 5.2 & 6.2, IBM Tivoli Directory 6.1, and Microsoft Active Directory 2003. See Data and Data Stores for more information.
 Caution –
Caution – The configuration data store embedded with OpenSSO Enterprise should only be used as a user data store for proof of concepts and deployments in development.
-
Web and Non-Web-Based Resources: The core design of OpenSSO Enterprise caters to SSO for both web and non-web applications.
-
Performance, Scalability and Availability: OpenSSO Enterprise can be scaled horizontally and vertically to handle increased workloads, and as security needs change over time. There is no single point of failure.
-
Distributed Architecture Server and client components can be deployed across the enterprise or across domain boundaries as all application programming interfaces (API) provide remote access to OpenSSO Enterprise based on a service-oriented architecture.
-
Flexibility and Extensibility: Many OpenSSO Enterprise services expose a service provider interface (SPI) allowing expansion of the framework to provide for specific deployment needs.
-
Internationalization OpenSSO Enterprise contains a framework for multiple language support. Customer facing messages, API, command line interfaces, and user interfaces are localized in the supported languages.
- © 2010, Oracle Corporation and/or its affiliates
