Analyzing the Deployment Architecture
The main components of the circle of trust described in this chapter are the telecommunications company which acts as and Identity Provider, and a ringtone Service Provider. The following two use cases are supported by the Fedlet:
The following table provides a simple comparison of the two use cases.
Table 5–1 Comparison of Fedlet Use Cases|
Identity Provider-Initiated Single Sign-On |
Service Provider-Initiated Single Sign-On |
|---|---|
|
1. Mobile phone user authenticates with Telecommunications Company. |
1. Mobile phone user attempts to access the ringtone Service Provider portal. |
|
2. Upon authentication, mobile phone user accesses the ringtone Service Provider portal. |
2. Ringtone Service Provider detects whether or not the mobile phone user has been authenticated by the Telecommunications Company. If not, then the ringtone Service Provider redirects the mobile phone user to the Telecommunications Identity Provider. |
|
3. Telecommunications Company challenges mobile phone user's credentials. Mobile user presents credentials. |
|
|
4. Upon authentication, mobile phone user accesses the ringtone Service Provider portal. |
Identity Provider-Initiated Single Sign-On
The following illustrates the flow of communication in a federation scenario between a telecommunications company acting as the Identity Provider, and a ringtone provider company acting as the Service Provider.
Figure 5–4 Process Flow for the Fedlet in Identity Provider-initiated Single Sign-On
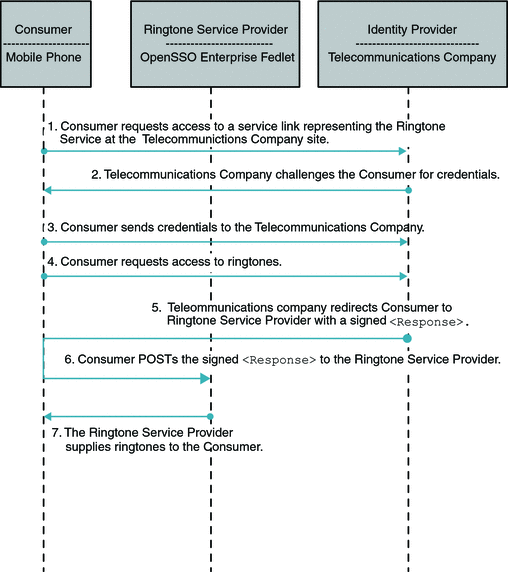
In an Identity Provider-initiated single sign-on scenario, the Identity Provider is configured with specialized links to specific Service Providers. These links actually refer to the local Identity Provider single sign-on service and pass parameters to the service identifying the remote Service Provider. So instead of directly visiting the Service Provider, the user goes to the Identity Provider site and clicks on one of the links to gain access to the remote Service Provider. This triggers the creation of a SAML assertion that is subsequently transported to the Service Provider.
Fedlet Service Provider-Initiated Single Sign-On
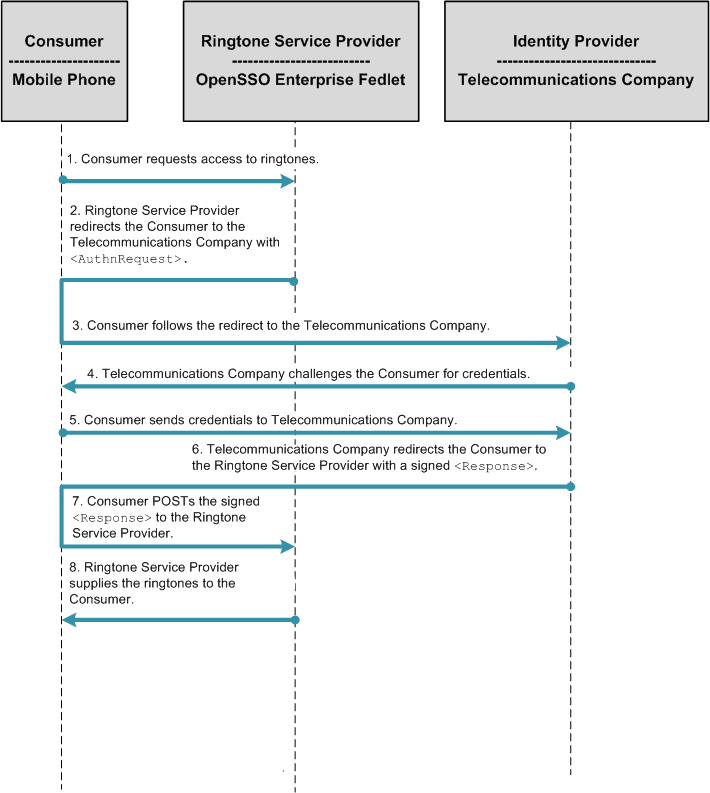
In a Service Provider-initiated single sign-on scenario, the user attempts to access a resource on the Service Provider. However the user does not have a current logon session on this site, and the user's federated identity is managed by the Identity Provider. The user is sent to the Identity Provider to log on. The Identity Provider creates a SAML assertion for the user's federated identity and sends it back to the Service Provider. The following figure illustrates the process flow.
Figure 5–5 Process Flow for Fedlet Service Provider-initiated Single Sign-On
- © 2010, Oracle Corporation and/or its affiliates
