Federated Single Sign-On Use Case in the Service Provider Environment
In this use case, the company uses SiteMinder in the Service Provider environment to protect legacy applications. OpenSSO Enterprise is installed to invoke Federation protocols. The OpenSSO Enterprise server includes a customized authentication module for handling SiteMinder sessions. A SiteMinder Web Agent is installed on the same OpenSSO Enterprise instance to protect OpenSSO Enterprise.
Figure 2–6 SiteMinder Federation in a Service Provider Environment
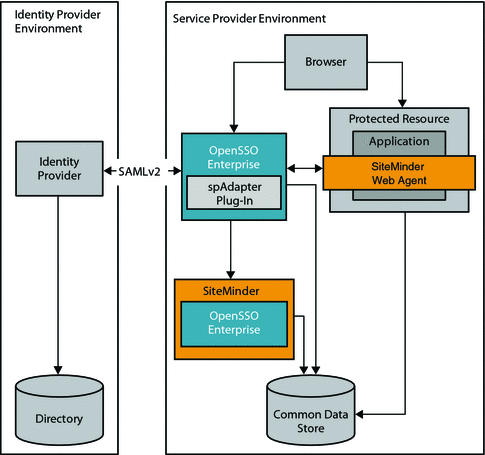
This use case includes two additional, lightweight components:
- Custom Authentication Module (spAdapter)
-
This is an OpenSSO Enterprise SAMLv2 plug-in that processes operations after federated single sign-on login is completed and before the target URL is displayed. After the OpenSSO Enterprise session is established, the spAdapter plug-in uses the OpenSSO Enterprise session to communicate with the SiteMinder Custom Authentication Scheme.
- Custom Authentication Scheme
-
This is a SiteMinder SAMLv2 plug-in. It uses the OpenSSO Enterprise configuration defined in the SAMLv2 metadata and the SAMLv2 session to generate a SiteMinder session.
When an access request comes from a partner application, the SiteMinder login page is displayed. If the user has already been authenticated, the OpenSSO Enterprise custom authentication module creates a session for the user. The custom authentication module consumes the SiteMinder session, and then generates a SAML assertion. The following two figures illustrate the steps in the single sign-on flow:
Figure 2–7 Process Flow for SiteMinder Federation in the Service Provider Environment
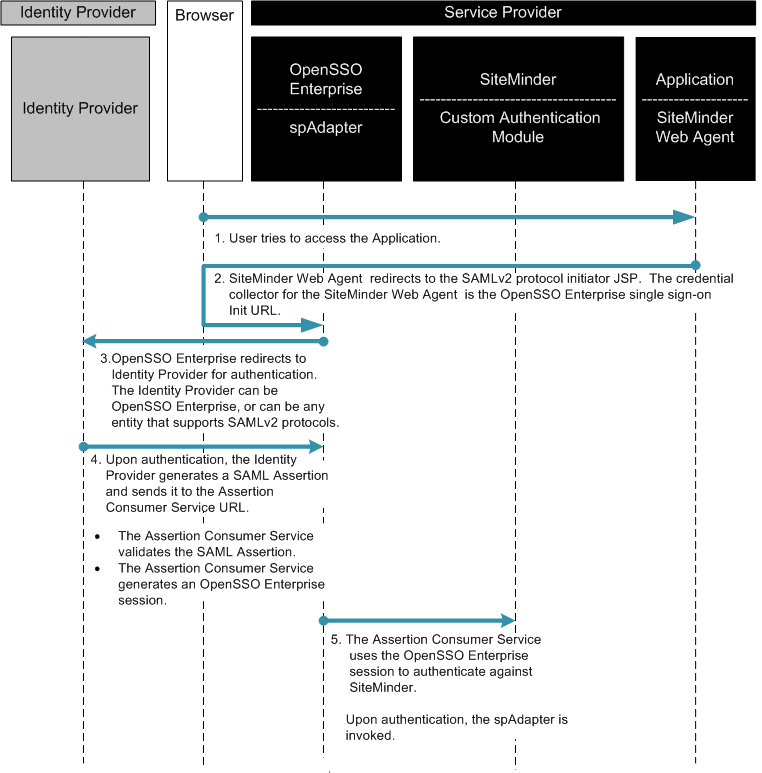
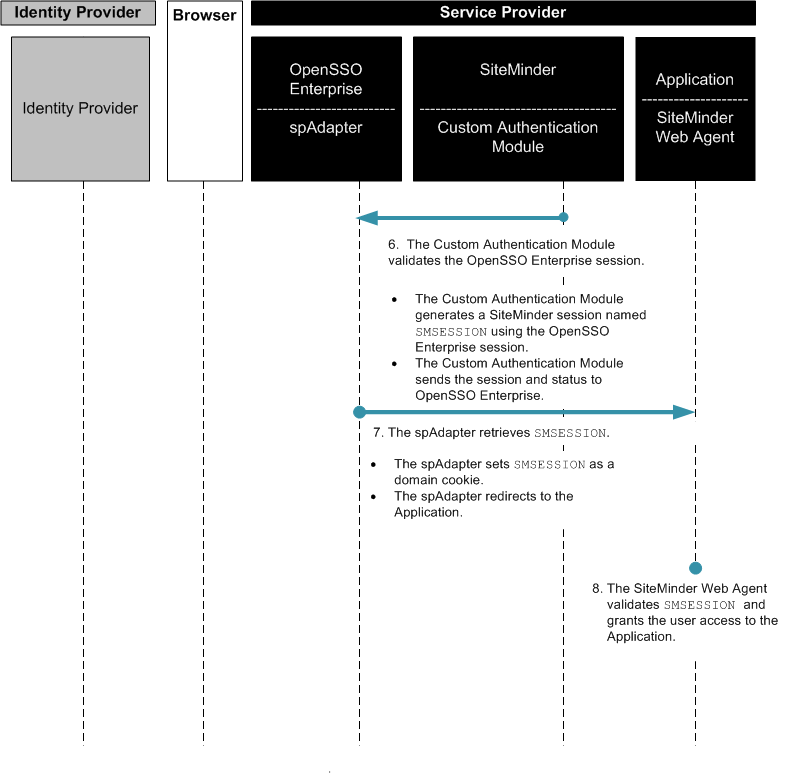
Figure 2–8 Process Flow for SiteMinder Federation in the Service Provider Environment (continued)
- © 2010, Oracle Corporation and/or its affiliates
