Provisioning Identities from Identity Manager to OpenSSO Enterprise
Provisioning users from one data store to a second allows the individual applications (for which the user stores are being provisioned) to use their proprietary repositories to read and write attributes that are specific to them. Before you can provision a user, role, or group into OpenSSO Enterprise from Identity Manager, the SunAccessManagerRealm adapter must be configured with the information required to successfully log in to OpenSSO Enterprise and the target OpenSSO Enterprise realm.
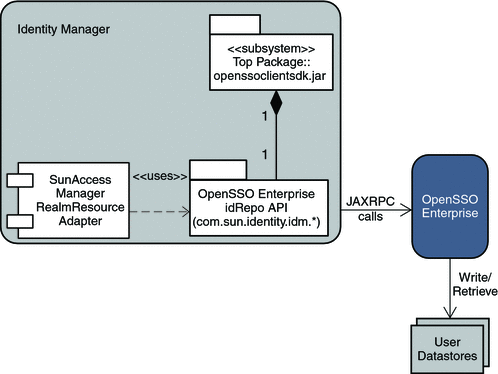
When you provision a user, role, or group from Identity Manager into OpenSSO Enterprise, you must select the Resource that you want to provision into. In this example, you will select the SunAccessManagerRealm adapter as the Resource to provision into. This adapter uses OpenSSO Enterprise APIs (OpenSSO package com.sun.identity.idm.*), to communicate with OpenSSO Enterprise. OpenSSO Enterprise receives the request to create or retrieve a user, role, or group. OpenSSO Enterprise then performs the task on its configured data stores in the relevant OpenSSO Enterprise realm. Similarly, for role or group retrieval from the OpenSSO Enterprise data store, the SunAccessManagerRealm adapter uses OpenSSO Enterprise APIs to communicate with OpenSSO Enterprise and to retrieve these objects.
In Identity Manager, Resource Objects correspond to OpenSSO Enterprise roles and groups. Resource Accounts correspond to OpenSSO Enterprise users that have been provisioned from Identity Manager. Since Resource Objects and Resource Accounts are managed differently in Identity Manager, both types of resources are viewable on separate tabs in the Identity Manager console.
The following figure illustrates how objects are provisioned and retrieved in Identity Manager.
Figure 1–2 Overview of Provisioning and Retrieving Objects in Identity Manager
To provision identities from Identity Manager to OpenSSO Enterprise, follow these steps:
-
View OpenSSO Enterprise Roles and Groups in Identity Manager
-
Provision a Test User From Identity Manager Into OpenSSO Enterprise
-
Provision a Test Role From Identity Manager Into OpenSSO Enterprise
-
Verify the Test Role Was Successfully Provisioned from Identity Manager Into OpenSSO Enterprise
-
Provision an Admin-User From Identity Manager Into OpenSSO Enterprise
-
Verify the Admin-User Was Successfully Provisioned from Identity Manager into OpenSSO Enterprise
-
Provision an Admin-Role From Identity Manager Into OpenSSO Enterprise
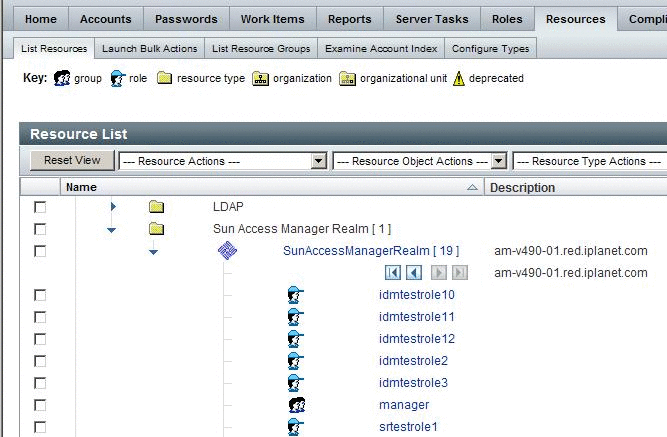
 To View OpenSSO Enterprise Roles and Groups
in Identity Manager
To View OpenSSO Enterprise Roles and Groups
in Identity Manager
-
1) Login to the Identity Manager console using the following credentials:
- User Name:
-
configurator
- Password:
-
configurator
-
Navigate to the tab Resources | List Resources.
-
Expand the branch for the SunAccessManagerRealm adapter instance.
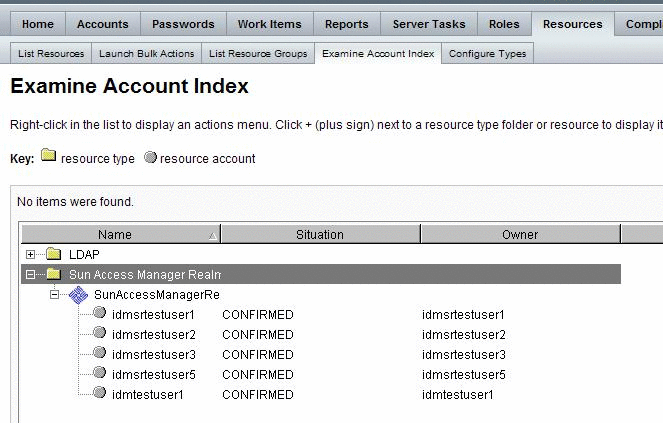
 To View OpenSSO Enterprise User Accounts in
Identity Manager
To View OpenSSO Enterprise User Accounts in
Identity Manager
-
Log in to the Identity Manager console using the following credentials:
- User Name:
-
configurator
- Password:
-
configurator
-
Navigate to the tab Resources | Examine Account Index.
-
Expand the branch for the SunAccessManagerRealm adapter instance.
You can also view the provisioned OpenSSO Enterprise user accounts in the Identity Manager console by navigating to the tab Accounts | List Accounts. However, that page will show you all Identity Manager accounts in the Identity Manager server, including those provisioned into OpenSSO Enterprise and any other resource or system, that has been configured in Identity Manager. For example, if Identity Manager were configured for SAP and OpenSSO Enterprise Resources, you would see a listing of users that have been provisioned into both systems. You can also use this page to create or provision users as described in sections below.
To view the accounts created per Resource Type, navigate to the tab Resources | Examine Account Index. This page is for viewing only, and you cannot use this page to create or provision a user.
 To Provision a Test User From Identity Manager
Into OpenSSO Enterprise
To Provision a Test User From Identity Manager
Into OpenSSO Enterprise
Follow these steps to test the Access Manager Realm Resource that was configured in Identity Manager.
-
Log in to the Identity Manager console using the following credentials:
- User Name:
-
configurator
- Password:
-
configurator
-
Navigate to the tab Accounts | List Accounts.
-
Select the option New Actions | New User.
-
In the Create User page, enter these values:
- AccountID:
-
idmuser
- First Name
-
Identity Manager
- Last Name:
-
User
- Password:
-
password
- Confirm Password password:
-
password
-
In the Create User page, click the Resources tab.
Select the SunAccessManagerRealmResourceAdapter resource as the Current Resource.
-
Click Save at the bottom of the screen.
-
In the next screen, you should see a success message "Account idmuser created." Click OK.
The User List page is displayed and contains a list with the newly-created user idmuser.
-
Log out from the Identity Manager console.
 To Verify that Identities Were Successfully
Provisioned
To Verify that Identities Were Successfully
Provisioned
-
In the Identity Manager console, return to the Accounts tab | List Accounts tab. .
You should see the idmuser user entry in the listing
-
Log in to the OpenSSO Enterprise console and verify that the user account is visible from the Subjects tab of your realm.
If the end-user entry is visible in both Identity Manager and OpenSSO Enterprise, then the end-user has successfully been provisioned.
-
Log in to Identity Manager and verify that you are logged into the Identity Manager User Page.
In this example, go to the following URL:
http://ApplicationServerHost:Port/idm/user
Log in using the following credentials:
- User Name:
-
idmuser
- Password:
-
password
-
Log in to OpenSSO Enterprise.
In this example, go to the following URL:
http://host1.example.com:48080/amserver/UI/Login?realm=idm
Log in using the following credentials:
- User Name:
-
idmuser
- Password:
-
password
-
Verify that you are logged into OpenSSO Enterprise and that you can see the user profile page.
-
Log out from the Identity Manager administrator interface and OpenSSO Enterprise console.
Next Steps
If you are not able to log in as the user, do the following:
-
Verify that you can see the user entry in the sub-realm in the OpenSSO Enterprise console.
-
Troubleshoot the issue using the OpenSSO Enterprise debug logs and the debug logs written by the Identity Manager's Access Manager Resource
 To Provision a Test Role From Identity Manager
Into OpenSSO Enterprise
To Provision a Test Role From Identity Manager
Into OpenSSO Enterprise
Before You Begin
In the OpenSSO Enterprise console, in the data store configuration page for the realm or sub-realm into which you will be provisioning the role, for the property LDAP Roles Attributes, add cn to the list of values.
The cn attribute is not defined as an attribute for the IdType.ROLE in the Data Store configuration by default. This attribute is set, when the role is provisioned to OpenSSO Enterprise. If the cn attribute is not already defined, Identity Manager shows the following error on the Identity Manager administrator interface:
com.waveset.util.WavesetException: Error creating object 'idmsrtestrole5'. com.waveset.util.WavesetException: Error setting attributes for 'idmsrtestrole5' com.sun.identity.idm.IdRepoException: Illegal arguments: One or more required arguments is null or empty |
-
Log in to the Identity Manager administrator interface using the following credentials:
- User Name:
-
configurator
- Password:
-
password
-
Navigate to the tab Resources | List Resources.
-
Expand the branch for the Sun Access Manager Realm entry.
-
Mark the checkbox in front of the SunAccessManagerRealm entry.
-
Choose the option Resource Actions | Create Resource Object.
-
In the New Resource Object page, select Role from the dropdown box, and click New.
In the next page:
-
Click Save.
-
In the Create Role Results page, click OK.
The Resource List page is displayed, and contains a list with the role idm_users created when you expand the SunAccessManagerRealm branch.
-
Log out from the Identity Manager administrator interface.
 To Verify the Test User Role Was Successfully
Provisioned from Identity Manager Into OpenSSO Enterprise
To Verify the Test User Role Was Successfully
Provisioned from Identity Manager Into OpenSSO Enterprise
-
Log in to OpenSSO Enterprise.
In this example, go to the following URL:
http://host1.example.com:48080/opensso
Log in using the following credentials:
- User Name:
-
amadmin
- Password:
-
password
-
Navigate to the sub-realm idm and tab Subjects | User.
The user Identity Manager User should be listed as one of the users.
-
Navigate to the tab Subjects | Role.
The role idm_users should be listed as one of the roles.
-
In the role profile page, click the idm_admins_role role entry.
-
Click on the User tab.
The user Identity Manager User should be selected into the role.
-
Log out of the OpenSSO Enterprise console.
Next Steps
If you are not able to see the role entry or the user assigned to the role troubleshoot the issue using the OpenSSO Enterprise debug logs and the debug logs written by the Identity Manager's Access Manager Resource.
 To Provision an Admin-User From Identity
Manager Into OpenSSO Enterprise
To Provision an Admin-User From Identity
Manager Into OpenSSO Enterprise
At this point, the Identity Manager is not yet protected by the policy agent. Follow these steps to create a user that will have administrative privileges on Identity Manager.
-
Login to the Identity Manager administrator interface using the following credentials:
- User Name:
-
configurator
- Password:
-
configurator
-
Navigate to the tab Accounts | List Accounts.
-
Choose the option New Actions | New User.
-
In the Create User page, enter these values:
- AccountID:
-
idmadmin
- First Name
-
Identity Manager
- Last Name:
-
Admin
- Password:
-
password
- Confirm Password :
-
password
-
In the Create User page, click the Resources tab.
For the Individual Resource Assignment, choose the SunAccessManagerRealm as the Current Resource.
-
In the Create User page, click the Security tab.
-
Click Save at the bottom of the screen.
-
In the next screen, you should see a success message, “Account idmadmin created.”
Click OK.
The User List page is displayed and contains a list with the new user idadmin.
-
Log out from the Identity Manager administrator interface.
 To Verify the Admin-User Was Successfully
Provisioned from Identity Manager into OpenSSO Enterprise
To Verify the Admin-User Was Successfully
Provisioned from Identity Manager into OpenSSO Enterprise
-
In the Identity Manager administrator interface, return to the Accounts tab | List Accounts tab
You should see the admin-user entry in the listing.
-
Log in to the OpenSSO Enterprise console.
Verify that the admin-user account is visible from the Subjects tab of your realm. If the admin-user entry is visible in both Identity Manager and OpenSSO Enterprise, then the admin-user has successfully been provisioned.
-
Log in to Identity Manager.
In this example, go to the following URL:
http://host1.example.com:2080/idm
Log in using the following credentials:
- User Name:
-
idmadmin
- Password:
-
password
Verify that you are logged into the Identity Manager administrator interface.
-
Log in to OpenSSO Enterprise.
In this example, go to the following URL:
http://host1.example.com:48080/opensso/UI/Login?realm=idm
Log in using the following credentials:
- User Name:
-
idmadmin
- Password:
-
password
Verify that you are logged into OpenSSO Enterprise and can see the user profile page.
 To Provision an Admin-Role From Identity Manager
Into OpenSSO Enterprise
To Provision an Admin-Role From Identity Manager
Into OpenSSO Enterprise
At this point, the Identity Manager is not yet protected by the policy agent. The role that will be created here will not have any special privileges assigned to it. It will only be used to group the administrative users, and this role will be used later in a policy in OpenSSO Enterprise.
-
Log in to the Identity Manager administrator interface as using the following credentials:
- User Name:
-
configurator
- Password:
-
configurator
-
Navigate to tab Resources | List Resources.
-
Expand the branch for the Sun Access Manager Realm entry.
-
Mark the checkbox in front of the SunAccessManagerRealm entry.
-
Choose the option Resource Actions | Create Resource Object.
-
In the New Resource Object page, select Role from the dropdown box, and click New.
-
In the next page, enter the name of the role as idm_admins, and assign the user idmadmin to this role.
Click Save.
-
In the Create Role Results screen, click OK.
When you expand the SunAccessManagerRealm branch, the Resource List page is displayed and contains a list with the new role idm_admins.
-
Log out of the Identity Manager administrator interface.
 To Verify the Test Admin Role Was Successfully
Provisioned from Identity Manager Into OpenSSO Enterprise
To Verify the Test Admin Role Was Successfully
Provisioned from Identity Manager Into OpenSSO Enterprise
-
Log in to OpenSSO Enterprise.
In this example, go to the following URL:
http://host1.example.com:48080/opensso
Log in using the following credentials:
- User Name:
-
idm_admins
- Password:
-
password
-
Navigate to the sub-realm idm and tab Subjects | User.
The user Identity Manager Admin should be listed as one of the users.
-
Navigate to the tab Subjects | Role.
The role idm_admins should be listed as one of the roles.
-
In the role profile page, click the idm_admins role entry.
-
Click on the User tab.
The user Identity Manager Admin should be selected into the role.
-
Log out of the OpenSSO Enterprise console.
Next Steps
If you are not able to see the role entry or the user assigned to the role, troubleshoot the issue using the OpenSSO Enterprise debug logs and the debug logs written by the Identity Manager Access Manager Resource.
- © 2010, Oracle Corporation and/or its affiliates
