Liberty Use Cases
Identity data consists of all the information that companies maintain about individual customers, corporate partners, and employees. Federating sources of identity data allows for accessing, transporting, sharing, and managing the data between partnered organizations and applications without weakening existing security safeguards. There are many ways to use Access Manager and its Liberty-based implementations to federate sources of identity data. The following sections explain just a few ways.
Unified Access to Intranet Resources
Many corporations provide access to outsourced human resources services, such as health benefits and 401(k) plans. The corporate intranet offers central access to these services, but employees have to log in and authenticate themselves every time they access each service. Employees might not want to share the same profile and password with both their 401(k) provider and their health care provider. Federation of identity data can provide seamless integration of web resources across multiple security domains within the same enterprise, allowing for employee ease-of-use and control.
Integrated Partner Networks
Enterprises can construct a network of partnered services for securely exchanging customer account information, transaction data, and credentials through a set of interoperable web services. Federation among partner networks allows identities to share key pieces of their respective data without sharing control. For example, logging in to one web site that represents an authentication domain consisting of an airline, a car rental company, and a hotel chain allows an identity to make travel plans even if one of the sites does not contain an identity data store.
Sample Use Case Process
Using a cell phone, a principal is able to access a ring-tone vendor's site. Due to implementation of single sign-on, the ring-tone vendor recognizes the principal from the cell-phone provider's authentication. This allows the principal to purchase ring tones by interacting with the user's bank for payment. The following figure illustrates the process of requesting a service and being authenticated for access. It assumes the following:
-
MyWireless is a cellular service provider and an identity provider in a federation framework that contains access to the discovery service in a web services framework.
-
MyRingtones is a service provider in a federation framework that also acts as a web service consumer (WSC) in a web services framework. It sells ringtones for use with cellular phones.
-
MyBank is a web service provider (WSP) in a web services framework. Linking MyBank to My Ringtones offers the opportunity for seamless purchases.
Note –
The same web service can act as a different entity in different scenarios.
Figure 2–1 Process in a Liberty-enabled Use Case
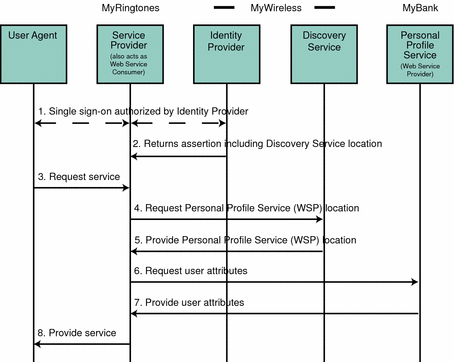
The user attempts to access MyRingtones and, after being prompted for credentials stored in MyBank, receives authorization through MyWireless. Single sign-on is accomplished in the back end. The entire process is based on implementations of the Liberty ID-FF, Liberty ID-WSF, and Liberty ID-SIS specifications.
- © 2010, Oracle Corporation and/or its affiliates
