Overview
In order for authentication to occur, Access Manager must be able to send HTTP or HTTPS packets with the authentication interface directly to the web browser. This deployment architecture requires opening holes in any firewalls between the end user and Access Manager.
In order to do this securely, Access Manager 7 supports a distributed authentication user interface web application. With distributed authentication, an additional server provides the authentication UI web application. The authentication UI servers exist solely for the purpose of serving up the authentication interface to web browsers. They let users eliminate the need for opening holes in firewalls between the end user and Access Manager. The following figure outlines the components and runtime flow of a basic distributed authentication deployment scenario.
Figure 1 Distributed Authentication Overview
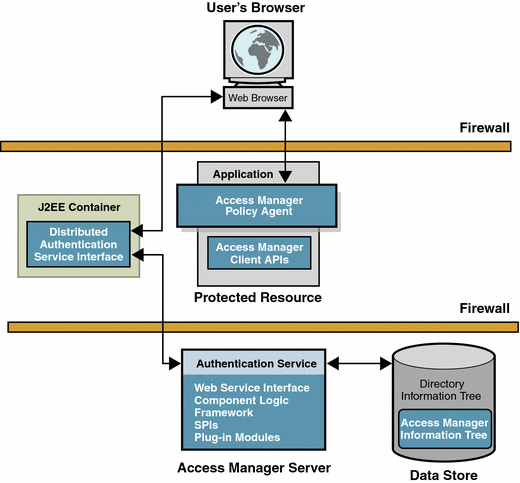
The Distributed Authentication UI service has the following dependencies:
-
The SUNWamclnt (Access Manager Client SDK package) is installed.
-
The SUNWjato (JATO package) is installed.
-
Access Manager Server is available (remotely).
-
The Client SDK will be able to communicate with Access Manager Server using http(s).
The Certificate, HTTP Basic, and MSISDN authentication modules are not supported through the distributed authentication interface.
The following service flow outlines how distributed authentication works in a typical scenario:
-
The web browser makes a request to the resource protected by a policy agent.
-
If there is no cookie containing an SSO token, the policy agent issues a redirect to its authentication URL. With the distributed authentication interface, the authentication URL is the URL of the distributed authentication service.
-
The browser follows the redirect and makes a request
-
The distributed authentication service recognizes the inbound request. Using the parameters in the request, it communicates with the authentication server (Access Manager) on the back end to determine the appropriate authentication instance, and gets the necessary callbacks to use in the presentation framework/layer. It also determines which presentation to use.
-
The distributed authentication service, using the information from the server, returns a presentation extraction page back to the web browser with the appropriate callbacks info from the server.
-
The browser replies with the credentials in a POST operation.
-
The distributed authentication service gets the credentials and passes them to Access Manager.
-
Access Manager authenticates using the appropriate authentication instance. If successful, it passes back the SSOToken, or it passes back the appropriate error information.
-
If successful, the distributed authentication service, replies with a 302 redirect back to the originally requested resource, which includes the SSOToken in a set-cookie header.
- © 2010, Oracle Corporation and/or its affiliates
