Chapter 6 Installing and Configuring the Distributed Authentication UI Servers
This chapter contains detailed instructions for the following tasks:
-
6.1 Installing and Deploying the Distributed Authentication UI Servers
-
6.2 Configuring the Distributed Authentication UI Servers Load Balancer
6.1 Installing and Deploying the Distributed Authentication UI Servers
Use the following as your checklist for installing and Deploying the Distributed Authentication UI servers:
-
Install a container for Distributed Authentication UI Server 1.
-
Install a container for Distributed Authentication UI Server 2.
-
Import the root CA certificate for the Access Manager load balancer into Authentication UI Server 1.
-
Verify that authentication through Authentication UI Server 1 is successful.
-
Import the root CA certificate for the Access Manager load balancer into Authentication UI Server 2.
-
Verify that authentication through Authentication UI Server 2 is successful.
Figure 6–1 Distributed Authentication
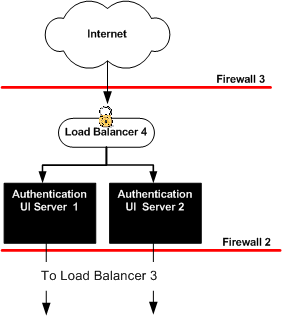
The Java ES installer must be mounted on the host AuthenticationUI-1 where you will install Web Server. See the section “To Download and Unpack the Java Enterprise System 2005Q4 Installer”3.2 Downloading and Mounting the Java Enterprise System 2005Q4 Installer in this document.
 To Install a Container for Distributed Authentication
UI Server 1
To Install a Container for Distributed Authentication
UI Server 1
-
As a root user, log in to host Authentication UI-1.
-
Start the Java Enterprise System installer with the -nodisplay option.
# /mnt/Solaris_sparc # ./installer -nodisplay
-
When prompted, provide the following information:
 To Build and Deploy Distributed Authentication
UI Server 1
To Build and Deploy Distributed Authentication
UI Server 1
-
Log in as a root user to AccessManager-1.
For this example, log into AccessManager-1.
-
Copy the Distributed Authentication UI files to another workspace on the AccessManager-1.
# cd /opt/SUNWcomm/SUNWam # cp README.distAuthUI amauthistui.war Makefile.distAuthUI /opt/SUNWam
-
Edit the Makefile.distAuthUI file and set the following properties:
JAVA_HOME=/usr/jdk/entsys-j2se/ SERVER_PROTOCOL=http SERVER_HOSTNAME=LoadBalancer-3.example.com SERVER_PORT=90 SERVER_DEPLOY_URI=amserver DISTAUTH_PROTOCOL=http DISTAUTH_HOSTNAME=AuthenticationUI-1.example.com DISTAUTH_PORT=1080 DISTAUTH_DEPLOY_URI=/distAuth APPLICATION_USERNAME=amadmin APPLICATION_PASSWORD=4m4dmin1 NOTIFICATION_URL=http://AuthenticationUI-1.example.com:1080/ distAuth/notificationservice DEBUG_LEVEL=message DEBUG_DIR=/tmp/distAuth COOKIE_ENCODE=false DISTAUTH_VERSION=7.0
-
Create the war file by issuing the following command
# /usr/sfw/bin/gmake -f Makefile.distAuthUI
This creates a war file named distAuthUI.war .
-
Rename the generated file.
# mv distAuthUI.war distAuth_AccessManager-1.war
-
Copy distAuth_AccessManager-1.war from the local host where you built the Distributed Authentication UI server (AccessManager–1) to the remote host where the Distributed Authentication UI server will be deployed (AuthenticationUI-1).
In this deployment example, the desintation directory is /tmp.
-
Log in as a root user to the Authentication UI-1 Web Server.
-
Start the Authentication UI-1 Web Server.
# cd /opt/SUNWwbserver # #cd https-AuthenticationUI-1.example.com # # ./start
-
Deploy the Distributed Authentication UI WAR file.
On the host AuthenticationUI-1, in the directory where you copied the distAuth_AuthenticationUI-1.war file, run the wdeploy command using the following form:
wdeploy deploy -u uri_path -i instance -v vs_id
[ [-V verboseLevel ]| [-q] ] [-n] [-d directory] war_file
For example, in this Deployment Example:
# cd /opt/SUNWwbsvr/bin/https/bin # ./wdeploy deploy -u /distAuth -i https-AuthenticationUI-1.example.com -v https-AuthenticationUI-1.example.com -d /opt/SUNWwbsvr/https-AuthenticationUI-1.example.com/webapps/distAuth /tmp/distAuth_AuthenticationUI-1.war
-
Restart Web Server.
# cd /opt/SUNWwbserver # cd https-AuthenticationUI-1.example.com # ./stop; ./start server has been shutdown # Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_04] from [Sun Microsystems Inc.] # info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-1.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-1.example.com] at [/search] info: HTTP3072: [LS ls1] http://AuthenticationUI-1.example.com:8080 ready to accept requests startup: server started successfully
Next Steps
The web module is loaded in the following directory:
/opt/SUNWwbsvr/https-AuthenticationUI-1.example.com/webapps/distAuth
 To Install a Container for Distributed Authentication
UI Server 2
To Install a Container for Distributed Authentication
UI Server 2
-
As a root user, log in to host AuthenticationUI-2.
-
Start the Java Enterprise System installer with the -nodisplay option.
# /mnt/Solaris_sparc # ./installer -nodisplay
-
When prompted, provide the following information:
Welcome to the Sun Java(TM) Enterprise System; serious software made simple... <Press ENTER to Continue>
Press Enter.
<Press ENTER to display the Software License Agreement>
Press Enter.
Have you read, and do you accept, all of the termsof the preceding Software License Agreement [No]
Enter y.
Please enter a comma separated list of languages you would like supported with this installation [8]
Enter 8 for “English only.”
Enter a comma separated list of products to install,or press R to refresh the list []
Enter 3 to select Web Server.
Press "Enter" to Continue or Enter a comma separated list of products to deselect... [1]
Press Enter.
Enter 1 to upgrade these shared components and 2 to cancel [1]
You are prompted to upgrade shared components only if the installer detects that an upgrade is required.
Enter 1 to upgrade shared components.
Enter the name of the target installation directory for each product: Web Server [/opt/SUNWwbsvr] :
Accept the default value.
System ready for installation Enter 1 to continue [1]
Enter 1.
1. Configure Now - Selectively override defaults or express through 2. Configure Later - Manually configure following installation Select Type of Configuration [1]
Enter 1.
Common Server Settings Enter Host Name [AuthenticationUI-2]
Accept the default value.
Enter DNS Domain Name [example.com]
Accept the default value.
Enter IP Address [xxx.xx.87.180]
Accept the default value.
Enter Server admin User ID [admin]
Enter admin.
Enter Admin User's Password (Password cannot be less than 8 characters) []
For this example, enter web4dmin.
Confirm Admin User's Password []
Enter the same password to confirm it.
Enter System User [root]
Accept the default value.
Enter System Group [root]
Accept the default value.
Enter Server Admin User ID [admin]
Enter admin.
Enter Admin User's Password []
For this example, enter web4dmin.
Enter Host Name [AuthenticationUI-2.example.com]
Accept the default value.
Enter Administration Port [8888]
Enter 1080.
Enter Administration Server User ID [root]
Accept the default value.
Enter System User ID [webservd]
Enter root.
Enter System Group [webservd]
Enter root.
Enter HTTP Port [80]
Enter 8888.
Enter content Root [/opt/SUNWwbsvr/docs]
Accept the default value.
Do you want to automatically start Web Serverwhen system re-starts.(Y/N)[N]
Accept the default value.
Ready to Install 1. Install 2. Start Over 3. Exit Installation What would you like to do [1]
When ready to install, enter 1.
 To Build and Deploy Distributed Authentication
UI Server 2
To Build and Deploy Distributed Authentication
UI Server 2
-
Log in as a root user to an Access Manager host.
For this example, log into AccessManager-2.
-
Copy the Distributed Authentication UI files to another workspace on the same (local) host.
cd /opt/SUNWcomm/SUNWam cp README.distAuthUI amauthistui.war Makefile.distAuthUI /opt/SUNWam
-
Edit the Makefile.distAuthUI file and set the following properties:
JAVA_HOME=/usr/jdk/entsys-j2se/ SERVER_PROTOCOL=http SERVER_HOSTNAME=LoadBalancer-3.example.com SERVER_PORT=90 SERVER_DEPLOY_URI=amserver DISTAUTH_PROTOCOL=http DISTAUTH_HOSTNAME=AuthenticationUI-2.example.com DISTAUTH_PORT=1080 DISTAUTH_DEPLOY_URI=/distAuth APPLICATION_USERNAME=amadmin APPLICATION_PASSWORD=4m4dmin1 NOTIFICATION_URL=http://AuthenticationUI-2.example.com:1080/ distAuth/notificationservice DEBUG_LEVEL=message DEBUG_DIR=/tmp/distAuth COOKIE_ENCODE=false DISTAUTH_VERSION=7.0
-
Create the war file by issuing the following command
gmake -f Makefile.distAuthUI.war
This creates a war file named distAuth_deploy.war.
-
Rename the generated file.
mv distAuthUI.war distAuth_AccessManager-2.war
-
Copy distAuth_AccessManager-2.war from the local host where you built the Distributed Authentication UI (AccessManager—2) to the remote host where the Distributed Authentication UI will be deployed (AuthetnicationUI-2).
# cp distAuth_AccessManager-2.war /net/AuthenticationUI-2/ tmp/distAuth_ AuthenticationUI-2.war
-
Deploy the Distributed Authentication UI WAR file.
On the host AuthenticationUI-2, in the directory where you copied the distAuth_ AuthenticationUI-2.war file, run the wdeploy command using the following form:
wdeploy deploy -u uri_path -i instance -v vs_id
[ [-V verboseLevel ]| [-q] ] [-n] [-d directory] war_file
For example, in this Deployment Example:
# ./wdeploy deploy -u /distAuth -i https-AuthenticationUI-2.example.com -v https-AuthenticationUI-2.example.com -d /opt/SUNWwbsvr/https-AuthenticationUI-2.example.com/webapps/distAuth /tmp/distAuth_ AuthenticationUI-2.war
-
Restart Web Server.
# cd /opt/SUNWwbserver # cd https-AuthenticationUI-2.example.com # ./stop; ./start server has been shutdown # Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, Version 1.5.0_04] from [Sun Microsystems Inc.] # info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/search] info: HTTP3072: [LS ls1] http://AuthenticationUI-2.example.com:8080 ready to accept requests startup: server started successfully
Next Steps
The web module is loaded in the following directory:
/opt/SUNWwbsvr/https-AuthenticationUI-2.example.com/webapps/distAuth/distAuth
 To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 1
To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 1
In this procedure, you import a Certificate Authority (CA) certificate. The certificate enables the Authentication UI server to trust the certificate from the Access Manager load balancer (Load Balancer 3), and to establish trust with the certificate chain that is formed from the CA to the certificate.
-
Log in as root to Authentication UI Server 2.
-
Copy the root CA certificate into a directory.
After the certificate authority (CA) sends you the certificate, copy the certificate text into a file. In this example, the file is /export/software/ca.cer.
-
Import the root CA certificate into the Java certificate store.
# /usr/jdk/entsys-j2se/jre/bin/keytool -import -trustcacerts -alias OpenSSLTestCA -file /export/software/ca.cer -keystore /usr/jdk/entsys-j2se/jre/lib/security/cacerts -storepass changeit Owner: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Issuer: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Serial number: 97dba0aa26db6386 Valid from: Tue Apr 18 07:66:19 PDT 2006 until: Tue Jan 13 06:55:19 PST 2009 Certificate fingerprints: MD5: 9f:57:ED:B2:F2:88:B6:E8:0F:1E:08:72:CF:70:32:06 SHA1: 31:26:46:15:C5:12:5D:29:46:2A:60:A1:E5:9E:26:64:36:80:E4:70 Trust this certificate: [no] yes Certificate was added to keystore. -
Verify that the root CA certificate was imported into the keystore.
# /usr/jdk/entsys-j2se/jre/bin/keytool -list -keystore ./cacerts -storepass changeit | grep -i open openssltestca, Nov 8, 2006, trustedCertEntry
-
Restart AuthenticationUI-1.
# cd /opt/SUNWwwbsvr/https-AuthenticationUI-1.example.com # ./stop server has been shutdown #./start Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, version 1.5.0_04 ] from [Sun Microsystems Inc.] info: WEB0100: Loading web module in virtual server https-AuthenticationUI-1.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server https-AuthenticationUI-1.example.com] at [/search] info: HTTP3072: [LS is 1] http://AuthenticationUI-1.example.com:1080 ready to accept requests startup: server started successfully
 To Verify that Authentication Through Authentication
UI Server 1 is Successful
To Verify that Authentication Through Authentication
UI Server 1 is Successful
Find a host that has direct network connectivity to both Authentication UI servers and the external facing load balancer of the Access Manager servers. One natural place is the Distributed Authentication UI server host itself.
-
Open a web browser and go to the following URL:
http://AuthenticationUI-1.example.com:1080/distAuth/UI/Login?goto= http://LoadBalancer-3.example.com:90
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
After successful authentication, you should be redirected to the index page for Access Manager's Web Server.
-
Log out of the Access Manager console.
 To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 2
To Import the Root CA Certificate for the
Access Manager Load Balancer into Authentication UI Server 2
In this procedure, you import a Certificate Authority (CA) certificate. The certificate enables the Authentication UI server to trust the certificate from the Access Manager load balancer (Load Balancer 3), and to establish trust with the certificate chain that is formed form the CA to the certificate.
-
Log in as a root user to Authentication UI Server 2.
-
Copy the root CA certificate into a directory.
After the certificate authority (CA) sends you the certificate, copy the certificate text into a file. In this example, the file is /export/software/ca.cer.
-
Import the root CA certificate into the Java certificate store.
# /usr/jdk/entsys-j2se/jre/bin/keytool -import -trustcacerts -alias OpenSSLTestCA -file /export/software/ca.cer -keystore /usr/jdk/entsys-j2se/jre/lib/security/cacerts -storepass changeit Owner: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Issuer: EMAILADDRESS=nobody@nowhere.com, CN=OpenSSLTestCA, OU=Sun, O=Sun,L=Santa Clara, ST=California C=US Serial number: 97dba0aa26db6386 Valid from: Tue Apr 18 07:66:19 PDT 2006 until: Tue Jan 13 06:55:19 PST 2009 Certificate fingerprints: MD5: 9f:57:ED:B2:F2:88:B6:E8:0F:1E:08:72:CF:70:32:06 SHA1: 31:26:46:15:C5:12:5D:29:46:2A:60:A1:E5:9E:26:64:36:80:E4:70 Trust this certificate: [no] yes Certificate was added to keystore. -
Verify that the root CA certificate was imported into the keystore.
# /usr/jdk/entsys-j2se/jre/bin/keytool -list -keystore ./cacerts -storepass changeit | grep -i open openssltestca, Nov 8, 2006, trustedCertEntry
-
Restart AuthenticationUI-2.
# cd /opt/SUNWwwbsvr/https-AuthenticationUI-2.example.com # ./stop server has been shutdown #./start Sun ONE Web Server 6.1SP5 B06/23/2005 18:00 info: CORE3016: daemon is running as super-user info: CORE5076: Using [Java HotSpot(TM) Server VM, version 1.5.0_04 ] from [Sun Microsystems Inc.] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/distAuth] info: WEB0100: Loading web module in virtual server [https-AuthenticationUI-2.example.com] at [/search] info: HTTP3072: [LS is 1] http://AuthenticationUI-2.example.com:1080 ready to accept requests startup: server started successfully
 To Verify that Authentication Through Authentication
UI Server 2 is Successful
To Verify that Authentication Through Authentication
UI Server 2 is Successful
Find a host that has direct network connectivity to both Authentication UI servers and the external facing load balancer of the Access Manager servers. One natural place is the Distributed Authentication UI server host itself.
-
Open a web browser and go to the following URL:
http://AuthenticationUI-2.example.com:1080/distAuth/UI/Login?goto= http://LoadBalancer-3.example.com:90
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
After successful authentication, you should be redirected to the index page for Access Manager's Web Server.
6.2 Configuring the Distributed Authentication UI Servers Load Balancer
-
Configure the Distributed Authentication UI servers load balancer.
-
Configure Distributed Authentication UI servers to authenticate to Access Manager as a custom user.
-
Configure the load balancer cookies for the Distributed Authentication UI servers.
-
Request an SSL certificate for the Distributed Authentication UI load balancer.
-
Install a root CA certificate on the Distributed Authentication UI load balancer.
-
Install an SSL certificate on the Distributed Authentication UI load balancer.
-
Configure SSL termination on the Distributed Authentication UI load balancer.
 To Configure the Distributed Authentication
UI Servers Load Balancer
To Configure the Distributed Authentication
UI Servers Load Balancer
Before You Begin
Contact your network administrator to obtain an available virtual IP address.
Note –
The load balancer hardware and software used in the lab facility for this deployment is BIG-IP® manufactured by F5 Networks. If you are using different load balancer software, see the documentation that comes with that product for detailed settings information.
-
Create a Pool.
A pool contains all the backend server instances.
-
Go to URL for the Big IP load balancer and log in.
-
Open the Configuration Utility.
Click “Configure your BIG-IP (R) using the Configuration Utility.”
-
In the left pane, click Pools.
-
On the Pools tab, click the Add button.
-
In the Add Pool dialog, provide the following information:
- Pool Name
-
Example: AuthenticationUI-Pool
- Load Balancing Method
-
Round Robin
- Resources
-
Add IP addresses for the Distributed Authentication UI server hosts. For this example, add AuthenticationUI-1:1080 and AuthenticationUI-2:1080.
-
Click the Done button.
-
-
Configure the load balancer for persistence.
-
Add a Virtual Server.
-
In the left frame, Click Virtual Servers.
-
On the Virtual Servers tab, click the Add button.
-
In the Add Virtual Server wizard, enter the virtual server IP address and port number.
In this example, enter the IP address for Load Balancer 4, and enter the port number 90.
-
Continue to click Next until you reach the Pool Selection dialog box.
-
In the Pool Selection dialog box, assign the AuthenticationUI-Pool that you have just created.
-
Click the Done button.
-
-
Add monitors.
Monitors are necessary for the load balancer to detect any backend server failures that may occur.
-
Verify that the Distributed Authentication UI server load balancer is configured properly.
Start a new browser and go to the Distributed Authentication UI load balancer URL. Example:
http://LoadBalancer-4.example.com:90/.
If the browser successfully renders the default Sun Web Server default document root page, close the browser.
 To Configure Distributed Authentication UI
Servers to Authenticate to Access Manager as a Custom User
To Configure Distributed Authentication UI
Servers to Authenticate to Access Manager as a Custom User
-
Set up a custom user.
-
Open a browser and go to the Access Manager login URL.
https://LoadBalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
-
On the Access Control tab, click the top-level realm example.com.
-
Click the Subjects tab.
-
Click the Agents tab.
-
On the Agents tab, click the New button.
-
In the New Agent page, provide the following information, and then click Create.
- ID
-
authuiadmin
- Password
-
4uthu14dmin
-
On the Agent tab, in the list of Agent names, click on authuiadmin.
-
Log out of the console.
-
-
Define authuiadmin as a special user in Access Manager 1.
-
As a root user, log in to host AccessManager–1.
-
Locate the /etc/opt/SUNWam/config/AMConfig.properties file.
Make a backup of this file before you modify it.
-
In the file, locate the following property:
com.sun.identity.authentication.special.users
-
At end of the list of values, add the UniversalID that you obtained and saved from the Agents list:
|uid=authuiadmin,ou=agents,o=example.com
This step authorizes the user to authenticate remote applications to the Access Manager server using the Access Manager Client SDK.
-
-
Define authuiadmin as a special user in Access Manager 2.
-
As a root user, log into host AccessManager–2.
-
Locate the /etc/opt/SUNWam/config/AMConfig.properties file.
Make a backup of this file before you modify it.
-
In the file, locate the following property:
com.sun.identity.authentication.special.users
-
At end of the list of values, add the UniversalID that you obtained and saved from the Agents list:
|uid=authuiadmin,ou=agents,o=example.com
This step authorizes the user to authenticate remote applications to the Access Manager server using the Access Manager Client SDK.
-
-
Restart both Access Manager 1 server and Access Manager 2 server.
-
Log out of Access Manager 1 and log out of Access Manager 2.
-
Define the custom user as a special user on the Authentication UI 1 server.
-
As a root user log into host AuthenticationUI— 1.
-
Locate the following file:
opt/SUNWwbsvr/https-AuthenticationUI-1.example.com/ webapps/distAuth/WEB-INF/classes/AMConfig.properties
Make a backup of this file before you modify it.
-
In the file, set the following properties:
com.sun.identity.agents.app.username=authuiadmin
com.iplanet.am.service.password=4uthu14dmin
-
-
Define the custom user as a special user on the Authentication UI 2 server.
-
As a root user, log into host AuthenticationUI–2.
-
Locate the following file:
opt/SUNWwbsvr/https-AuthenticationUI-2.example.com/ webapps/distAuth/WEB-INF/classes
Make a backup of this file before you modify it.
-
In the file, set the following properies:
com.sun.identity.agents.app.username=authuiadmin
com.iplanet.am.service.password=4uthu14dmin
-
-
Restart Authentication UI 1 server and Authentication UI 2 server.
# cd /opt/SUNWwbsvr/https-AuthenticationUI-1.example.com
# ./stop ; ./start
# cd /opt/SUNWwbsvr/https-AuthenticationUI-2.example.com
# ./stop ; ./start
-
Log out of Authentication UI 1 server and log out of Authentication UI 2 server.
-
Verify that everything works.
-
On Directory Server 1 and Directory Server 2, go to logs directory and run the tail command.
# cd /var/opt/mps/serverroot/slapd-am-config/logs
# tail -f access | grep authuiadmin
-
In a browser, go to following URL to open the Access Manager login page.
https://LoadBalancer-4.example.com:9443/distAuth/UI/Login?goto=https://LoadBalancer-3.example.com:9443/amserver/UI/Login
Using this URL, you will be able to view entries for the Authentication UI server binding to the Directory Server as the special user authuiadmin.
-
In the logs, look for entries similar to this:
[12/Jul/2006:21:08:33 -0700] conn=43430 op=0 msgId=1059 - BIND dn="uid=authuiadmin,ou=agents,o=example.com" method=128 version=3 [12/Jul/2006:21:08:33 -0700] conn=43430 op=0 msgId=1059 - RESULT err=0 tag=97 nentries=0 etime=0 dn="uid=authuiadmin,ou=agents,o=example.com"
When you see err=0 in either log, you know that the Authentication UI server successfully logged into the Access Manager server. If the err value is anything other an 0, you must troubleshoot the configuration.
-
Log in to the Access Manager console using the following information:
- Username
-
amadmin
- Password
-
4m4dmin1
If you can successfully log in, you know that authentication worked successfully
-
-
Log out of the console.
 To Configure the Load Balancer Cookies for
the Distributed Authentication UI Servers
To Configure the Load Balancer Cookies for
the Distributed Authentication UI Servers
-
Log in as a root user to Authentication UI 1 host.
-
Go to the following directory:
# cd /webapps/distAuth/WEB-INF/classes
-
Modify the AMconfig.properties file.
Make a backup of this file.
At the end of the file, uncomment the last two lines and set the following values:
com.iplanet.am.lbcookie.name=AuthenticationUILBCookie com.iplanet.am.lbcookie.value=AuthenticationUI-1
-
Restart the Authentication UI 1 host.
-
As a root user log into host AuthenticationUI–2 .
-
Go to the following directory:
# cd /webapps/distAuth/WEB-INF/classes
-
Modify the AMconfig.properties file.
Make a backup of this file.
At the end of the file, uncomment the last two lines and set the following values:
com.iplanet.am.lbcookie.name=AuthenticationUILBCookie com.iplanet.am.lbcookie.value=AuthenticationUI-2
-
Restart the Distributed Authentication UI 1 server.
 To Request an SSL Certificate for the Distributed
Authentication UI Load Balancer
To Request an SSL Certificate for the Distributed
Authentication UI Load Balancer
-
Open a browser, go to the BIG-IP URL:
https://is-F5.example.com
-
Log in to the BIG-IP console using the following information:
- User Name:
-
username
- Password:
-
password
-
Click “Configure your BIG-IP (R) using the Configuration Utility.”
-
In the left pane, click Proxies.
-
Click the Cert-Admin tab.
-
On the SSL Certificate Administration page, click the button named “Generate New Key Pair/Certificate Request.”
-
In the Create Certificate Request page, provide the following information:
- Key Identifier:
-
LoadBalancer-4.example.com
- Organizational Unit Name:
-
Deployment
- Domain Name:
-
LoadBalancer-4.example.com
- Challenge Password:
-
password
- Retype Password:
-
password
-
Click the button “Generate Key Pair/Certificate Request.”
On the SSL Certificate Request page, the request is generated in the Certificate Request field.
-
Copy all the text contained in the Certificate Request field.
Save the text in a text file to keep it handy for later use.
-
Send the text of the certificate request to a Certificate Authority of your choice.
A Certificate Authority is an entity that issues certified digital certificates. VersiSign, Thawte , Entrust, and GoDaddy are just a few examples of Certificate Authority companies. In this deployment example, CA certificates were obtained from OpenSSL. Follow the instructions provided by the Certificate Authority for submitting a certificate request.
 To Install a Root CA Certificate on the Distributed
Authentication UI Load Balancer
To Install a Root CA Certificate on the Distributed
Authentication UI Load Balancer
The root Certificate Authority certificate proves that a Certificate Authority such as VeriSign or Entrus actually issued the digital server certificate you received. You install the root certificate on Load Balancer 3 to ensure that the link between the Load Balancer 3 SSL certificate can be maintained with the issuing company.
-
In the BIG-IP load balancer console, click Proxies.
-
Click the Cert-Admin tab.
-
Click the Import link.
-
In the Import Type field, choose Certificate, and then click Continue.
-
In the Install SSL Certificate page, in the Certificate File field, click Browse.
-
In the Choose File dialog, choose Browser.
Navigate to the file that includes the root CA Certificate, and click Open.
-
In the Certificate Identifier field, enter OpenSSL_CA_cert.
-
Click Install Certificate.
-
In the Certificate OpenSSL_CA_Cert page, click Return to Certificate Administration.
The new certificate OpenSSL_CA_Cert is now included in the Certificate ID list.
 To Install an SSL Certificate on the Distributed
Authentication UI Load Balancer
To Install an SSL Certificate on the Distributed
Authentication UI Load Balancer
-
Once you've received the SSL certificate from a Certificate Authority, in the BIG-IP load balancer console, click Proxies.
-
Click the Cert-Admin tab.
The key LoadBalancer-4.example.com is in the Key List. This was generated in a previous step when you generated a key pair and a certificate request.
-
In the Certificate ID column, click the Install button for LoadBalancer-4.example.com.
-
In the Certificate File field, click Browse.
In the Choose File dialog, navigate to the text file in which you saved the certificate text sent to you by the certificate issuer, and then click Open.
-
Click Install Certificate.
-
In the Certificate LoadBalancer-3.example.com page, click Return to Certificate Information link.
In the SSL Certificate Administration page, verify that the Certificate ID indicates LoadBalancer-4.example.com.
 To Configure SSL Termination on the Distributed
Authentication UI Load Balancer
To Configure SSL Termination on the Distributed
Authentication UI Load Balancer
In this deployment example, Secure Socket Layer (SSL) termination at Load Balancer 4 increases the performance at the server level, and simplifies SSL certificate management. Clients will access Load Balancer 4 using SSL-encrypted data. Load Balancer 4 decrypts the data and then sends the unencrypted data on to the Access Manager server. The Access Manager server or Authentication UI server does not have to perform decryption, and the burden on its processor is relieved. Load Balancer 3 then load-balances the decrypted traffic to the appropriate Access Manager server. Finally, Load Balancer 34encrypts the responses from server, and sends encrypted responses to the client.
In this deployment example, an SSL certificate is required only at the Load Balancer 4, and not required for each Access Manager server. This simplifies SSL certificate management. Load Balancer 4 can intelligently load-balance a request based on unencrypted cookies. This would not be possible with SSL-encrypted cookies because Load Balancer 4 cannot read SSL-encrypted cookies.
In this deployment example, you set up a proxy server using BIG-IPTM hardware and software.
-
Configure the new proxy service.
-
Log in to the BIG-IP load balancer using the following information:
- Username
-
username
- Password
-
password
-
Click the link “Configure your BIG-IP using the Configuration Utility.”
-
In the load balancer console, in the left pane, click Proxies.
-
On the Proxies tab, click Add.
-
In the Add Proxy dialog, provide the following information:
- Proxy Type:
-
Check the SSL checkbox.
- Proxy Address:
-
xxx.xx.69.14 (The IP address of Load Balancer 3, the Access Manager server load balancer.)
- Proxy Service:
-
9443 (The port number of the new proxy you are setting up.)
- Destination Address:
-
xxx.xx.69.14
- Destination Service:
-
90
- Destination Target:
-
Choose Local Virtual Server.
- SSL Certificate:
-
Choose LoadBalancer-4.example.com.
- SSL Key:
-
Choose LoadBalancer-4.example.com.
- Enable ARP:
-
Check this checkbox.
-
Click Next.
-
In the Rewrite Redirects field, choose All.
-
Click Done.
The new proxy server is now added to the Proxy Server list.
-
-
Verify that you can access the Access Manager server using the new proxy server port number.
-
Open a browser, and go to the following URL:
https://LoadBalancer-4.example.com:9443/distAuth/UI/Login?goto= https://LoadBalancer-3.example.com:9443/amserver/UI/Login
Tip –You may see a message indicating that the Access Manager server doesn't recognize the certificate issuer. When this happens, install the root Certificate Authority certificate in the browser so that the browser recognizes the certificate issuer. See your browser's online help system for information on installing a root CA certificate.
-
Log out of Access Manager, and close the browser.
-
- © 2010, Oracle Corporation and/or its affiliates
