Part VI Configuring Special Use Cases
Chapter 15 Use Case 1: Testing Basic SAMLv2 Protocols
The three primary SAMLv2 protocols are Persistent Federation with SSO, Single Logout, and Federation Termination. SAMLv2 protocols can be initiated from the Service Provider site or from the Identity Provider site. Multiple variations exist. For example, the SSO protocol has two profiles, the browser artifact profile and browser POST profile. The profiles are among the many mechanisms described in the SAML specification.
Use Case 1 provides instructions for constructing and accessing URLs that use these profiles. Single logout uses two versions, SOAP and HTTP direct. Federation Termination uses two variations, HTTP data rate and SOAP.
15.1 Before You Begin
A sample JSP file is provided at the end of this chapter to help you run the four groups of test cases described in this chapter. Before you can begin running these test cases, you must complete the following tasks:
The following table summarizes the SAMLv2 profiles you can test in the Federation environment described in previous chapters of this document.
Table 15–1 SAMLv2 Profiles Illustrated in Use Case 1|
Initiated by Service Provider |
Initiated by Identity Provider |
||
|---|---|---|---|
|
Use Case 1A |
1. Persistent Federation (Browser Artifact) 2. Logout (SOAP) 3. Single Sign-On (Browser Artifact) 4. Federation Termination Browser (SOAP) |
Use Case 1C |
1. Persistent Federation (Browser Artifact) 2. Logout (SOAP) 3. Single Sign-On (Browser Artifact) 4. Federation Termination Browser (SOAP) |
|
Use Case 1B |
1. Persistent Federation (Browser POST) 2. Logout (HTTP) 3. Single Sign-On (Browser POST) 4. Federation (Termination HTTP) |
Use Case 1D |
1. Persistent Federation (Browser POST) 2. Logout (HTTP) 3. Single Sign-On (POST) 4. Federation Termination (HTTP) |
 To Create an index.jsp File
To Create an index.jsp File
-
As a root user, log into the Federation Manager 1 host.
-
Create a text file named index.jsp based on the sample below.
-
Copy the index.jsp file to the following directory:
/opt/SUNWwbsver/https-FederationManager-1.siroe.com/webapps/ https-FederationManager-1.siroe.com/federation/saml2/jsp
-
As a root user, log into the Federation Manager 2 host.
-
Create a text file named index.jsp based on the sample below.
-
Copy the index.jsp file to the following directory:
/opt/SUNWwbsver/https-FederationManager-2.siroe.com/webapps/ https-FederationManager-1.siroe.com/federation/saml2/jsp
 To Create a Test User in the Identity Provider
Site
To Create a Test User in the Identity Provider
Site
-
Go to the Access Manager URL:
https://Loadbalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- User Name:
-
amadmin
- Password:
-
4m4dmin1
-
On the Realms page, click the users realm name.
-
On the users-Properties page, click the Subjects tab and then click New.
-
On the New User page, provide the following information:
- ID:
-
idp
- First Name:
-
idp
- Last Name:
-
idp
- Full Name:
-
idp
- Password:
-
idp
- Password (confirm):
-
idp
Click Save.
15.2 Testing Requests Initiated by the Service Provider Using SOAP
Use the following as your checklist for testing this use case:
Note –
Conduct the four tests using the same browser window instance. The tests must be conducted in consecutive order to satisfy Use Case 1A.
 To Test Persistent Federation Using Browser
Artifact
To Test Persistent Federation Using Browser
Artifact
-
Access the Federation Manager server using one of the following alternatives:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Persistent Federation (Browser Artifact)
-
Go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spSSOInit.jsp?metaAlias=/sp&idpEntityID= loadbalancer-3.example.com
The login request is redirected to Access Manager.
-
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The login request is redirected to Federation Manager.
-
Log in to the Federation Manager console using the following information:
- User Name:
-
spuser
- User Name:
-
spuser
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
15.2.1 To Test Logout Using SOAP
Access the Federation Manager server using one of the following alternatives:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Logout (SOAP)
-
Go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spSingleLogoutInit.jsp?metaAlias=/sp&binding= urn:oasis:names:tc:SAML:2.0:bindings: SOAP&idpEntityID=loadbalancer-3.example.com
The message “SP initiated single logout succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2 |
 To Test Single Sign-On Using Browser Artifact
To Test Single Sign-On Using Browser Artifact
-
Access the Federation Manager server using one of the following options:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Single Sign-On (Browser Artifact)
-
Go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spSSOInit.jsp?metaAlias=/sp&idpEntityID= loadbalancer-3.example.com
-
-
The login request is redirected to Access Manager.
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
 To Test Federation Termination Using SOAP
To Test Federation Termination Using SOAP
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Federation Termination (SOAP)
-
Go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spMNIRequestInit.jsp?metaAlias=/sp&idpEntityID= loadbalancer-3.example.com&requestType= Terminate&binding=urn:oasis:names:tc:SAML:2.0:bindings:SOAP
The message “ManageNameID Request succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
Access the Federation Manager server using one of the following alternatives:
15.3 Testing Requests Initiated by the Service Provider Using HTTP Redirect
Use the following as your checklist for testing:
Note –
Conduct the four tests using the same browser window instance. The tests must be conducted in consecutive order to satisfy Use Case 1B.
 To Test Persistent Federation Using Browser
POST
To Test Persistent Federation Using Browser
POST
-
Access the Federation Manager server using one of the following alternatives:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Persistent Federation (Browser POST)
-
Go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spSSOInit.jsp?metaAlias=/sp&idpEntityID= loadbalancer-3.example.com&binding=HTTP-POST
The login request is redirected to Access Manager.
-
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The login request is redirected to Federation Manager.
-
Log in to the Federation Manager console using the following information:
- User Name:
-
spuser
- User Name:
-
spuser
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
 To Test Logout Using HTTP
To Test Logout Using HTTP
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Logout (HTTP)
-
Go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spSingleLogoutInit.jsp?metaAlias=/sp&idpEntityID= loadbalancer-3.example.com
The message “SP initiated single logout succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
Access the Federation Manager server using one of the following alternatives:
 To Test Single Sign-On Using Browser POST
To Test Single Sign-On Using Browser POST
-
Access the Federation Manager using one of the following options:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Single Sign-On (Browser POST)
-
Configure and go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spSSOInit.jsp?metaAlias=/sp&idpEntityID= loadbalancer-3.example.com&binding=HTTP-POST
The login request is redirected to Access Manager.
-
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
 To Test Federation Termination Using HTTP
To Test Federation Termination Using HTTP
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Federation Termination (HTTP)
-
Go to the following URL:
https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/ spMNIRequestInit.jsp?metaAlias=/sp&idpEntityID= loadbalancer-3.example.com&requestType=Terminate
The message “ManageNameID Request succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
Access the Federation Manager server using one of the following alternatives:
15.4 Testing Requests Initiated by the Identity Provider Using SOAP
Use the following as your checklist for testing:
Note –
Conduct the four tests using the same browser window instance. The tests must be conducted in consecutive order to satisfy Use Case 1C.
 To Test Persistent Federation Using Browser
Artifact
To Test Persistent Federation Using Browser
Artifact
-
Access the Federation Manager server using one of the following alternatives:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the IDP Initiated Profiles section, click the following link:
Persistent Federation (Browser Artifact)
-
Go to the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp/ idpSSOInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com
The login request is redirected to Access Manager.
-
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The login request is redirected to Federation Manager.
-
Log in to the Federation Manager console using the following information:
- User Name:
-
spuser
- User Name:
-
spuser
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
 To Test Logout Using SOAP
To Test Logout Using SOAP
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the IDP Initiated Profiles section, click the following link:
Logout (HTTP)
-
Go to the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp/ idpSingleLogoutInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com&binding= urn:oasis:names:tc:SAML:2.0:bindings:SOAP
The message “IDP initiated single logout succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
Access the Federation Manager server using one of the following alternatives:
 To Test Single Sign-On Using Browser Artifact
To Test Single Sign-On Using Browser Artifact
-
Access the Federation Manager server using one of the following alternatives:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the IDP Initiated Profiles section, click the following link:
Single Sign-On (Browser Artifact)
-
Go to the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp/ idpSSOInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com
The login request is redirected to Access Manager.
-
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
 To Test Federation Termination Using SOAP
To Test Federation Termination Using SOAP
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the IDP Initiated Profiles section, click the following link:
Federation Termination (HTTP)
-
Go to the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp/ idpMNIRequestInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com&binding= urn:oasis:names:tc:SAML:2.0:bindings:SOAP&requestType=Terminate
The message “ManageNameID Request succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
Access the Federation Manager server using one of the following alternatives:
15.5 Testing Requests Initiated by the Identity Provider Using HTTP Redirect
Use the following as your checklist for testing:
Note –
Conduct the four tests using the same browser window instance. The tests must be conducted in consecutive order to satisfy Use Case 1D.
 To Test Persistent Federation Using Browser
POST
To Test Persistent Federation Using Browser
POST
-
Access the Federation Manager server using one of the following alternatives:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Persistent Federation (Browser POST)
-
Go to the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp /idpSSOInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com&binding=HTTP-POST
The login request is redirected to Access Manager.
-
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The login request is redirected to Federation Manager.
-
Log in to the Federation Manager console using the following information:
- User Name:
-
spuser
- User Name:
-
spuser
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
 To Test Logout Using HTTP
To Test Logout Using HTTP
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Logout (HTTP)
-
Go to the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp/ idpSingleLogoutInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com
The message “SP initiated single logout succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
Access the Federation Manager server using one of the following alternatives:
 To Test Single Sign-On Using Browser POST
To Test Single Sign-On Using Browser POST
-
Access the Federation Manager server using one of the following alternatives:
-
Go to the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Single Sign-On (Browser POST)
-
Configure the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp/ idpSSOInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com&binding=HTTP-POST
The login request is redirected to Access Manager.
-
-
Log in to the Access Manager console using the following information:
- User Name:
-
idp
- Password:
-
idp
The message “Single Sign-On succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
 To Test Federation Termination Using HTTP
To Test Federation Termination Using HTTP
-
Access the index.jsp URL:
https://LoadBalancer-9-siroe.com:3443/federation/saml2/jsp/index.jsp
On the SAML2 Use Cases page, in the SP Initiated Profiles section, click the following link:
Federation Termination (HTTP)
-
Go to the following URL:
https://loadbalancer-3.example.com:9443/amserver/saml2/jsp/ idpMNIRequestInit.jsp?metaAlias=/users/idp&spEntityID= loadbalancer-9.siroe.com&requestType=Terminate
The message “ManageNameID Request succeeded” is displayed. You can view the debug file to see the actual assertion that was sent over the wire.
# vi /var/opt/SUNWam/fm/federation/debug/fmSAML2
Access the Federation Manager server using one of the following alternatives:
15.6 The Sample jsp.index File
Example 15–1 Sample jsp.index File for Testing SAMLv2 Protocols
<%--
Copyright © 2004 Sun Microsystems, Inc. All rights reserved
Use is subject to license terms.
--%>
<html>
<head>
<title>SAML2 Usecases (index)</title>
<meta http-equiv="Content-Type" content="text/html; charset=iso-8859-1">
<link rel="stylesheet" href="samples/liberty/sso/css/styles.css"
type="text/css">
</head>
<body bgcolor="#FFFFFF" text="#000000" leftmargin="9" marginwidth="9"
topmargin="9" marginheight="9" >
<br>
<table width="30%" border="0" cellspacing="0" cellpadding="0" >
<tr>
<td colspan="2"> </td>
<td width="100%">
<table border="0" cellspacing="0" cellpadding="0" align=center>
<tr>
<td>
<P ALIGN=CENTER>
<FONT FACE="Arial Narrow, sans-serif">
<FONT SIZE=2 STYLE="font-size: 11pt">
<B>SAML2 Usecases</B>
</FONT>
</FONT>
</P>
</td>
</tr>
<tr><td colspan="3"> </td></tr>
<tr>
<td>
<p>
<B>SP Initiated Profiles</B>
</p>
</td>
</tr>
<tr><td colspan="3"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp
/spSSOInit.jsp?metaAlias=/sp&idpEntityID=loadbalancer-3.example.com">
Persistent Federation (Browser Artifact) </a>
</p>
</td>
</tr>
<tr><td colspan="3"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/
spSingleLogoutInit.jsp?metaAlias=/sp&binding=urn:oasis:names:tc:SAML:
2.0:bindings:SOAP&idpEntityID=loadbalancer-3.example.com">Logout(SOAP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/
spSSOInit.jsp?metaAlias=/sp&idpEntityID=loadbalancer-3.example.com">
Single Sign-On (Browser Artifact) </a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/
spMNIRequestInit.jsp?metaAlias=/sp&idpEntityID=
loadbalancer-3.example.com&requestType=Terminate&binding=
urn:oasis:names:tc:SAML:2.0:bindings:SOAP">
Federation Termination(SOAP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp
/spSSOInit.jsp?metaAlias=/sp&idpEntityID=
loadbalancer-3.example.com&binding=
HTTP-POST">Persistent Federation (Browser POST) </a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp/
spSingleLogoutInit.jsp?metaAlias=/sp&idpEntityID=
loadbalancer-3.example.com">
Logout(HTTP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp
/spSSOInit.jsp?metaAlias=/sp&idpEntityID=
loadbalancer-3.example.com&binding=
HTTP-POST">Single Sign-On (Browser POST) </a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-9.siroe.com:3443/federation/saml2/jsp
/spMNIRequestInit.jsp?metaAlias=/sp&idpEntityID=
loadbalancer-3.example.com&requestType=Terminate">
Federation Termination(HTTP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<B>IDP Initiated Profiles </B>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpSSOInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com">
Persistent Federation (Browser Artifact)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpSingleLogoutInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com&binding=
urn:oasis:names:tc:SAML:2.0:bindings:SOAP">Logout(SOAP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpSSOInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com">
Single Sign-On (Browser Artifact)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpMNIRequestInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com&binding= urn:oasis:names:tc:SAML:2.0:
bindings:SOAP&requestType=Terminate">Federation Termination (SOAP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpSSOInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com&binding=
HTTP-POST">Persistent Federation (Browser POST)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpSingleLogoutInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com">Logout(HTTP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpSSOInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com&binding=
HTTP-POST">Single Sign-On (Browser POST)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
<tr>
<td>
<p>
<a href="https://loadbalancer-3.example.com:9443/amserver/saml2/jsp
/idpMNIRequestInit.jsp?metaAlias=/users/idp&spEntityID=
loadbalancer-9.siroe.com&requestType=Terminate">
Federation Termination (HTTP)</a>
</p>
</td>
</tr>
<tr><td colspan="1"> </td></tr>
</table>
</td>
</tr>
</table>
</body>
</html>
|
Chapter 16 Use Case 2: User Attribute Mapping
In this use case, no user repository exists in the Service Provider site. All users in the Identity Provider site are mapped to an anonymous user. The anonymous user represents all users in the Identity Provider site when it presents itself to the Service Provider site. The anonymous user is used to map transient-based federation attributes.
This use case illustrates how you can pass user profile attributes from the Identity Provider site to the to Service Provider site, and the from Service Provider site to all of its Service Provider agent-protected applications. Communication from the Identity Provider site to the Service Provider site takes place using SAMLv2 protocols. Communication from Federation Manager site to all Service Provider agent-protected applications takes place using agent-to- LDAP attribute mapping.
16.1 Mapping User Attributes from the Identity Provider to a Single User on the Service Provider
Use the following as your checklist for mapping user attributes to a single user:
 To Modify the usersLDAP User
Attributes
To Modify the usersLDAP User
Attributes
-
Go to the Access Manager URL:
https://LoadBalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- User name:
-
amadmin
- Password:
-
4m4dmin1
-
Add the usersLDAP user attributes that will be set for the user entry.
In this example, you will add the mail and telephone number attributes.
-
On the Realms page, click the users realm name, and then click Data Stores.
-
On the users — Data Stores page, click the usersLDAP data store name.
-
On the Edit Data Store page, add givenname to the LDAP User Attributes list.
In the LDAP User Attributes field, enter givenname, and then click Add.
-
In the same manner, add mail to the LDAP User Attributes list.
-
In the same manner, add telephonenumber to the LDAP User Attributes list.
-
Click Save.
-
 To Create a New User
To Create a New User
-
Go to the Access Manager URL:
https://LoadBalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- User name:
-
amadmin
- Password:
-
4m4dmin1
-
On the Realms page, click the users realm name, and then click the Subject tab.
-
On the User tab, click New.
-
On the New User page, provide the following information:
- ID:
-
jsmith
- First Name:
-
John
- Last Name:
-
Smith
- Full Name:
-
John Smith
- Password:
-
jsmith
- Password (confirm):
-
jsmith
Click Create, and then log out of the Access Manager console.
 To Edit the New User's Contact Information
To Edit the New User's Contact Information
-
Go to the Access Manager URL:
https://LoadBalancer-3.example.com:9443/amserver/UI/Login
-
Log in to the Access Manager console using the following information:
- User name:
-
amadmin
- Password:
-
4m4dmin1
-
On the Realms page, click the users realm name, and then click the Subject tab.
-
On the User tab, in the list of users, click jsmith.
-
On the Edit User page, provide the following information:
- Email Address:
-
jsmith@example.com
- Telephone Number:
-
408–555–5454
Click Save, and then log out of the Access Manager console.
 To Modify the Identity Provider Metadata
To Modify the Identity Provider Metadata
-
As a root user, log into the Access Manager 1 host.
-
In the Identity Provider extended metadata file, map the Email Address and Telephone Number attributes.
For example, in the first value-pair mapping, mail is the LDAP attribute name, and EmailAddress is the information to be sent over the wire using SAMLv2 protocols.
# cd /etc/opt/SUNWam/config # vi saml2-idp-extended-metadata.xml ... <Attribute name="attributeMap"> <Value>EmailAddress=mail</Value> <Value>Telephone=telephonenumber</Value> ...
Save the file.
-
Delete the existing metadata.
# /opt/SUNWam/saml2/bin/saml2meta delete -u amadmin -w 4m4dmin1 -r /users -e loadbalancer3.example.com Descriptor and config fore entity "loadbalancer-3.example" was deleted successfully.
-
Load the modified metadata file into the Directory Server.
#/opt/SUNWam/saml2/bin/saml2meta import -u amadmin -w 4m4dmin1 -r /users -m saml2-idp-metadata.xml -x saml2-idp-extended-metadata.xml File "saml2-idp-metadata.xml" was imported successfully. File "saml2-idp-extended-metadata.xml" was imported sucessfully.
When you map the attributes on one Access Manager server, the mapping is also made available to the second Access Manager. So you do not have to modify metadata on the Access Manager 2 server. The metadata will also be made available to the Federation Manager servers.
 To Modify the Service Provider Metadata
To Modify the Service Provider Metadata
-
As a root user, log into the Federation Manager 1 host .
-
In the Service Provider extended metadata file, map the Email Address and Telephone Number attributes.
# cd /etc/opt/SUNWam/config # vi saml2-sp-extended-metadata.xml ... <Attribute name="attributeMap"> <Value>EmailAddress=EmailAddress</Value> <Value>Telephone=Telephone</Value> ...
Notice that the value mail in the EmailAddress attribute—value pair does not have to be identical to the value EmailAddress specified in the Identity Provider metadata.
-
Add anonymous to the transient user list.
<Attribute name="transientUser"> <Value>anonymous</Value>
Save the file.
-
Delete the existing metadata.
# /opt/SUNWam/saml2/bin/saml2meta -i /var/opt/SUNWam/fm/war_staging delete -u amadmin -w 11111111 -e loadbalancer-9.siroe.com
-
Load the modified metadata file into the Directory Server.
#/opt/SUNWam/saml2/bin/saml2meta -i /var/opt/SUNWam/fn/war_staging import -u amadmin -w 11111111 -m saml2-sp-metadata.xml -x saml2-sp-extended-metadata.xml File "saml2-sp-metadata.xml" was imported successfully. File "saml2-sp-extended-metadata.xml" was imported sucessfully.
Save the file.
-
Restart Federation Manager 1.
# cd /opt/SUNWwbsvr/https-FederationManager-1.siroe.com # ./stop; ./start
-
Restart Federation Manager 2.
# cd /opt/SUNWwbsvr/https-FederationManager-2.siroe.com # ./stop; ./start
 To Modify the Agents Properties
To Modify the Agents Properties
-
Modify the Web Policy Agents properties.
-
As a root user, log into the Protected Resource 3 host.
-
Add the transient attribute to the property com.sun.am.policy.am.login.url.
# cd /etc/opt/SUNWam/agents/es6/config/ _opt_SUNWwbsvr_https-ProtectedResource-3.siroe.com # vi AMAgent.properties com.sun.am.policy.am.login.url = https://LoadBalancer-9.siroe.com:3443/federation/ saml2/jsp/spSSOInit.jsp?metaAlias=sp&idpEntityID= loadbalancer-3.example.com&NameIDFormat=transient
-
Modify the following properties:
com.sun.am.policy.agents.config.session.attribute.fetch.mode=HTTP_HEADER com.sun.am.policy.agents.config.session.attribute.map= EmailAddress|EmailAddress,Telephone|Telephone
Save the file.
-
Restart the Protected Resource 3 host.
# cd /opt/SUNWwbsvr/https-ProtectedResource-3.siroe.com # ./stop; ./start
-
As a root user, log into the Protected Resource 4 host.
-
Add the transient NameID format to the property com.sun.am.policy.am.login.url.
# cd /etc/opt/SUNWam/agents/e6/config/ _opt_SUNWwbsvr_https-ProtectedResource-4.siroe.com # vi AMAgent.properties com.sun.am.policy.am.login.url = https://LoadBalancer-9.siroe.com:3443/federation/ saml2/jsp/spSSOInit.jsp?metaAlias=sp&idpEntityID= loadbalancer-4.example.com&NameIDFormat=transient
-
Modify the following properties:
com.sun.am.policy.agents.config.session.attribute.fetch.mode=HTTP_HEADER com.sun.am.policy.agents.config.session.attribute.map= EmailAddress|EmailAddress,Telephone|Telephone
Save the file.
-
Restart the Protected Resource 4 host.
# cd /opt/SUNWwbsvr/https-ProtectedResource-4.siroe.com # ./stop; ./start
 To Verify that Attribute Mapping is Working
Properly
To Verify that Attribute Mapping is Working
Properly
The file snoop.jsp is provided at the end of this chapter for you to use with this deployment example. The snoop.jsp file reads each of the HTTP headers and reads a number of query parameters in the SAMLv2 metadata. In this use case, the JSP determines which headers are being passed from the Service Provider to the agent. When you will initiate SAMLv2 for Federation, the user attribute mapping from the Identity Provider to the Service Provider takes place using the SAMLv2 protocol. The mapping from the Service Provider to the Identity Provider takes places using LDAP attribute mapping from Federation Manager to the Web Policy Agent.
-
As a root user, log into the Protected Resource 3 host.
-
Copy the snoop.jsp file to the following directory on both the Protected Resource 3 host and the Protected Resource 4 host:
/opt/SUNWwbsvr/docs
-
Access snoop.jsp through the Web Policy Agents URL:
https://LoadBalancer-11.siroe.com:6443/snoop.jsp
The Web Policy Agent redirects the request, and the Access Manager login page is displayed.
-
Log in to the Access Manager console using the following information:
- User Name:
-
jsmith
- Password:
-
jsmith
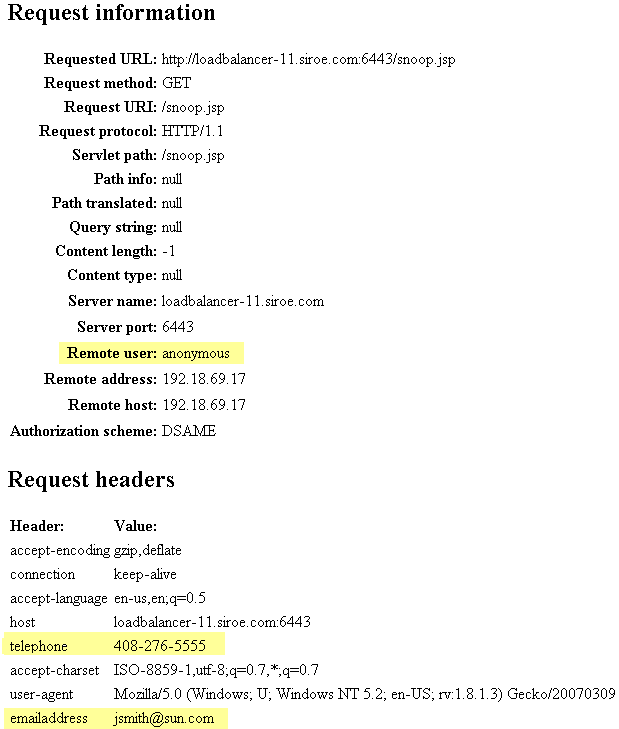
The JSP Snoop Page is displayed. John Smith's telephone number and email address are included in the request headers section of the file. Also notice that the Remote user is anonymous. This is the user that serves as confirmation of the transientUser you configured in the saml2-sp-extended-metadata.xmlfile on the Service Provider.
Figure 16–1 Output from snoop.jsp
Example 16–1 snoop.jsp
sr1-usca-43 7 > view snoop.jsp
"snoop.jsp" [Read only] 171 lines, 3825 characters
<HTML>
<HEAD>
<TITLE>JSP snoop page</TITLE>
<%@ page import="javax.servlet.http.
HttpUtils,java.util.Enumeration" %>
</HEAD>
<BODY>
<H1>JSP Snoop page</H1>
<H2>Request information</H2>
<TABLE>
<TR>
<TH align=right>Requested URL:</TH>
<TD><%= HttpUtils.getRequestURL(request) %></TD>
</TR>
<TR>
<TH align=right>Request method:</TH>
<TD><%= request.getMethod() %></TD>
</TR>
<TR>
<TH align=right>Request URI:</TH>
<TD><%= request.getRequestURI() %></TD>
</TR>
<TR>
<TH align=right>Request protocol:</TH>
<TD><%= request.getProtocol() %></TD>
</TR>
<TR>
<TH align=right>Servlet path:</TH>
<TD><%= request.getServletPath() %></TD>
</TR>
<TR>
<TH align=right>Path info:</TH>
<TD><%= request.getPathInfo() %></TD>
</TR>
<TR>
<TH align=right>Path translated:</TH>
<TD><%= request.getPathTranslated() %></TD>
</TR>
<TR>
<TH align=right>Query string:</TH>
<TD><%= request.getQueryString() %></TD>
</TR>
<TR>
<TH align=right>Content length:</TH>
<TD><%= request.getContentLength() %></TD>
</TR>
<TR>
<TH align=right>Content type:</TH>
<TD><%= request.getContentType() %></TD>
<TR>
<TR>
<TH align=right>Server name:</TH>
<TD><%= request.getServerName() %></TD>
<TR>
<TR>
<TH align=right>Server port:</TH>
<TD><%= request.getServerPort() %></TD>
<TR>
<TR>
<TH align=right>Remote user:</TH>
<TD><%= request.getRemoteUser() %></TD>
<TR>
<TR>
<TH align=right>Remote address:</TH>
<TD><%= request.getRemoteAddr() %></TD>
<TR>
<TR>
<TH align=right>Remote host:</TH>
<TD><%= request.getRemoteHost() %></TD>
<TR>
<TR>
<TH align=right>Authorization scheme:</TH>
<TD><%= request.getAuthType() %></TD>
<TR>
</TABLE>
<%
Enumeration e = request.getHeaderNames();
if(e != null && e.hasMoreElements()) {
%>
<H2>Request headers</H2>
<TABLE>
<TR>
<TH align=left>Header:</TH>
<TH align=left>Value:</TH>
</TR>
<%
while(e.hasMoreElements()) {
String k = (String) e.nextElement();
%>
<TR>
<TD><%= k %></TD>
<TD><%= request.getHeader(k) %></TD>
</TR>
<%
}
%>
</TABLE>
<%
}
%>
<%
e = request.getParameterNames();
if(e != null && e.hasMoreElements()) {
%>
<H2>Request parameters</H2>
<TABLE>
<TR valign=top>
<TH align=left>Parameter:</TH>
<TH align=left>Value:</TH>
<TH align=left>Multiple values:</TH>
</TR>
<%
while(e.hasMoreElements()) {
String k = (String) e.nextElement();
String val = request.getParameter(k);
String vals[] = request.getParameterValues(k);
%>
<TR valign=top>
<TD><%= k %></TD>
<TD><%= val %></TD>
<TD><%
for(int i = 0; i < vals.length; i++) {
if(i > 0)
out.print("<BR>");
out.print(vals[i]);
}
%></TD>
</TR>
<%
}
%>
</TABLE>
<%
}
%>
<%
e = getServletConfig().getInitParameterNames();
if(e != null && e.hasMoreElements()) {
%>
<H2>Init parameters</H2>
<TABLE>
<TR valign=top>
<TH align=left>Parameter:</TH>
<TH align=left>Value:</TH>
</TR>
<%
while(e.hasMoreElements()) {
String k = (String) e.nextElement();
String val = getServletConfig().getInitParameter(k);
%>
<TR valign=top>
<TD><%= k %></TD>
<TD><%= val %></TD>
</TR>
<%
}
%>
</TABLE>
<%
}
%>
</BODY>
</HTML>
|
- © 2010, Oracle Corporation and/or its affiliates
